Phishing Campaign Targets Russian Academics with Fake eLibrary Emails Linked to Operation ForumTroll
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: New ForumTroll Phishing Attacks Target Russian Scholars Using Fake eLibrary Emails
1. BLUF (Bottom Line Up Front)
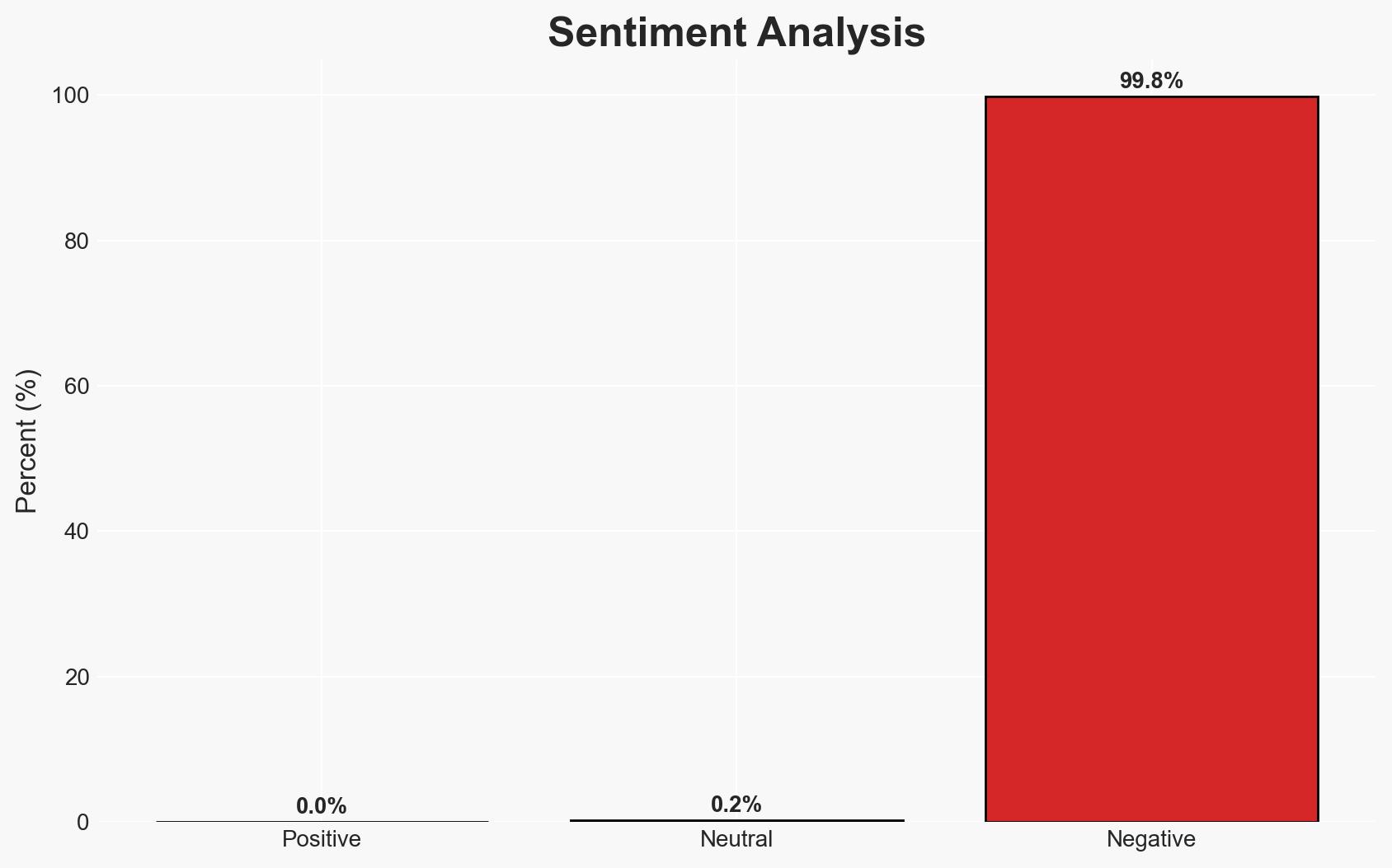
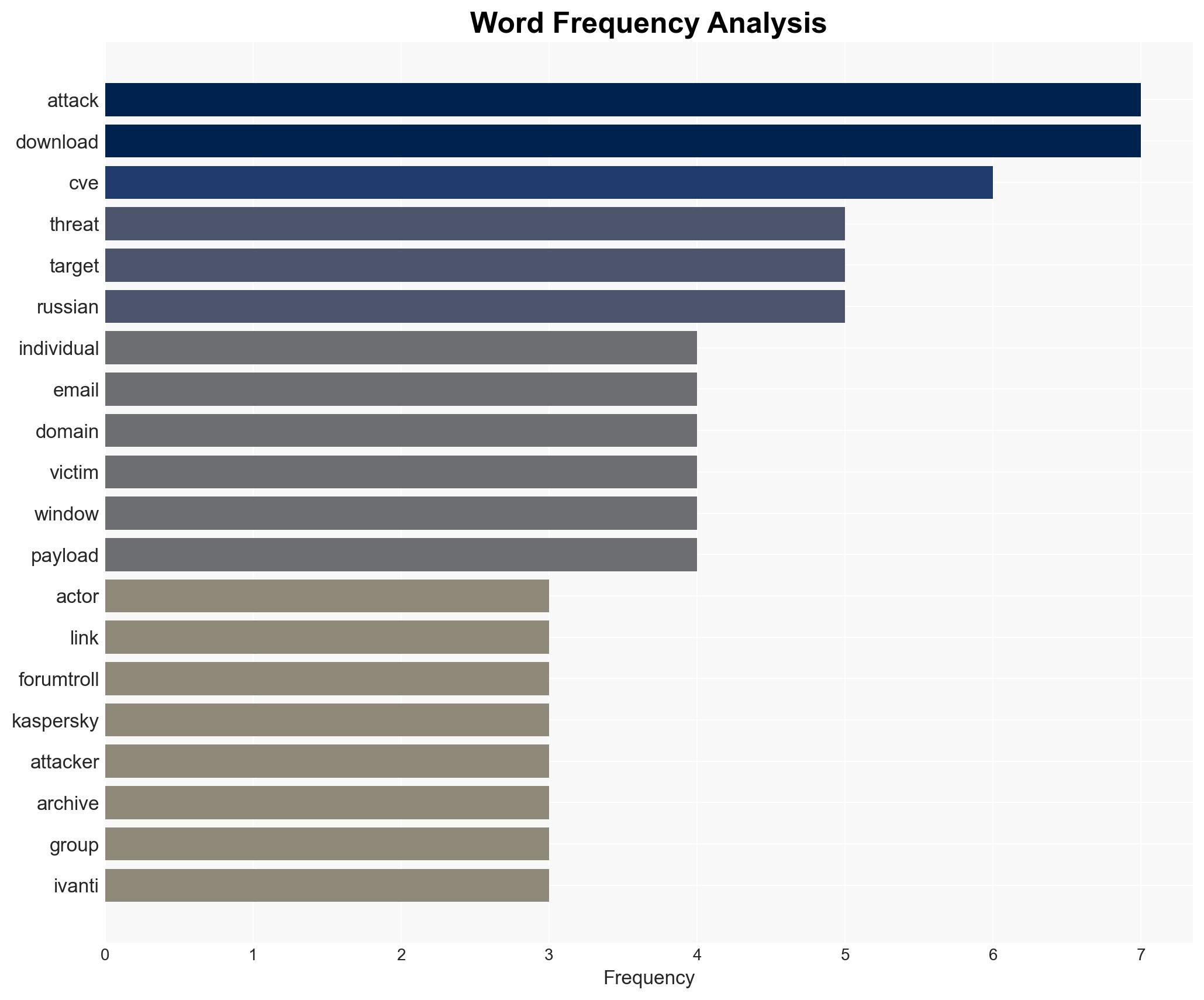
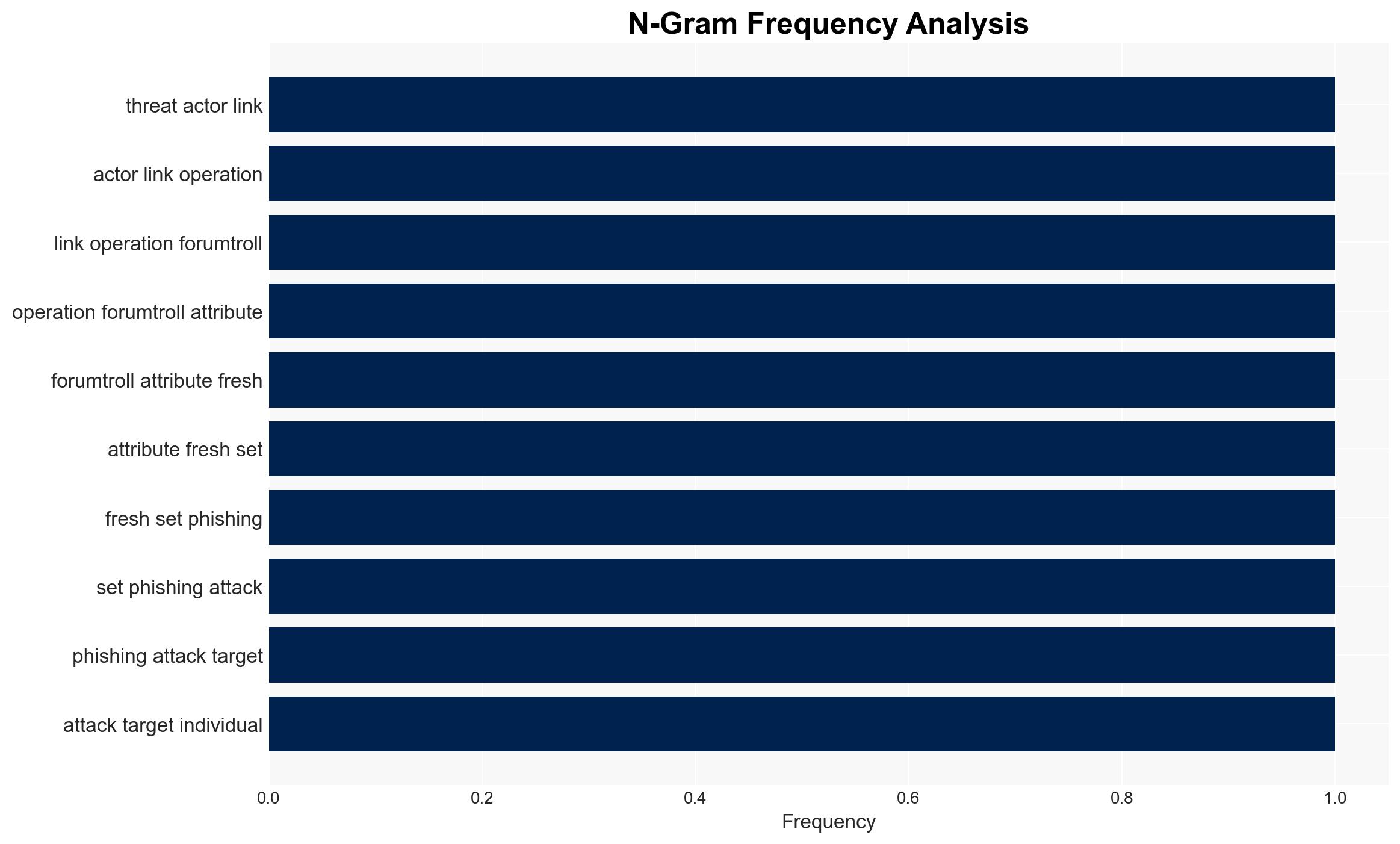
The ForumTroll threat actor has launched a new phishing campaign targeting Russian scholars in political science, international relations, and global economics. This operation uses sophisticated tactics, including domain aging and personalized emails, to exploit a zero-day vulnerability in Google Chrome. The primary objective appears to be intelligence collection. We assess with moderate confidence that the campaign is state-sponsored, given the strategic targeting and advanced methods employed.
2. Competing Hypotheses
- Hypothesis A: The ForumTroll campaign is a state-sponsored operation aimed at gathering intelligence on Russian academic circles. This is supported by the sophisticated nature of the attack, the strategic selection of targets, and the use of advanced cyber tools. However, the lack of direct attribution to a specific state actor remains a key uncertainty.
- Hypothesis B: The campaign is conducted by a non-state actor, possibly for financial gain or corporate espionage. While the targeting of scholars could suggest motives beyond financial, the absence of clear state attribution and potential for economic motivations cannot be ruled out.
- Assessment: Hypothesis A is currently better supported due to the complexity and precision of the attack, which aligns with state-sponsored capabilities. Indicators such as the use of a zero-day vulnerability and strategic domain aging suggest a high level of planning and resources typical of state actors. Confirmation of state involvement would shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The threat actor has access to advanced cyber capabilities; the campaign’s primary goal is intelligence collection; Russian scholars are the intended targets.
- Information Gaps: The identity of the threat actor; the specific objectives of the campaign; potential links to state entities.
- Bias & Deception Risks: Potential bias in attributing state sponsorship due to the sophistication of the attack; deception risk from the threat actor’s use of legitimate-looking domains and personalized emails.
4. Implications and Strategic Risks
This development could exacerbate tensions between Russia and potential adversaries, especially if state sponsorship is confirmed. It may also lead to increased scrutiny and defensive measures within Russian academic institutions.
- Political / Geopolitical: Potential for diplomatic fallout if state involvement is confirmed; increased cyber defense posturing by Russia.
- Security / Counter-Terrorism: Heightened threat environment for Russian academic institutions; potential for broader targeting of intellectual assets.
- Cyber / Information Space: Escalation in cyber espionage activities; increased focus on protecting academic and research data.
- Economic / Social: Potential disruption to academic collaboration and research activities; erosion of trust in digital communications.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of phishing activities targeting academic institutions; disseminate threat intelligence to potential targets; conduct awareness training for scholars.
- Medium-Term Posture (1–12 months): Strengthen cyber defenses in academic institutions; foster international partnerships for intelligence sharing; develop capabilities to attribute and respond to state-sponsored cyber threats.
- Scenario Outlook:
- Best: Attribution leads to diplomatic resolution and enhanced cyber cooperation.
- Worst: Escalation of cyber activities leading to broader geopolitical tensions.
- Most-Likely: Continued low-level cyber espionage with periodic escalations.
6. Key Individuals and Entities
- Georgy Kucherin (Security Researcher, Kaspersky)
- Kaspersky (Russian Cybersecurity Vendor)
- Not clearly identifiable from open sources in this snippet (Threat Actor)
7. Thematic Tags
cybersecurity, cyber-espionage, phishing attacks, state-sponsored threats, Russian academia, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us