Recent attacks linked to Islamic State indicate the group’s enduring influence despite territorial losses.
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Recent attacks have been ‘inspired’ by Islamic State What does that mean
1. BLUF (Bottom Line Up Front)
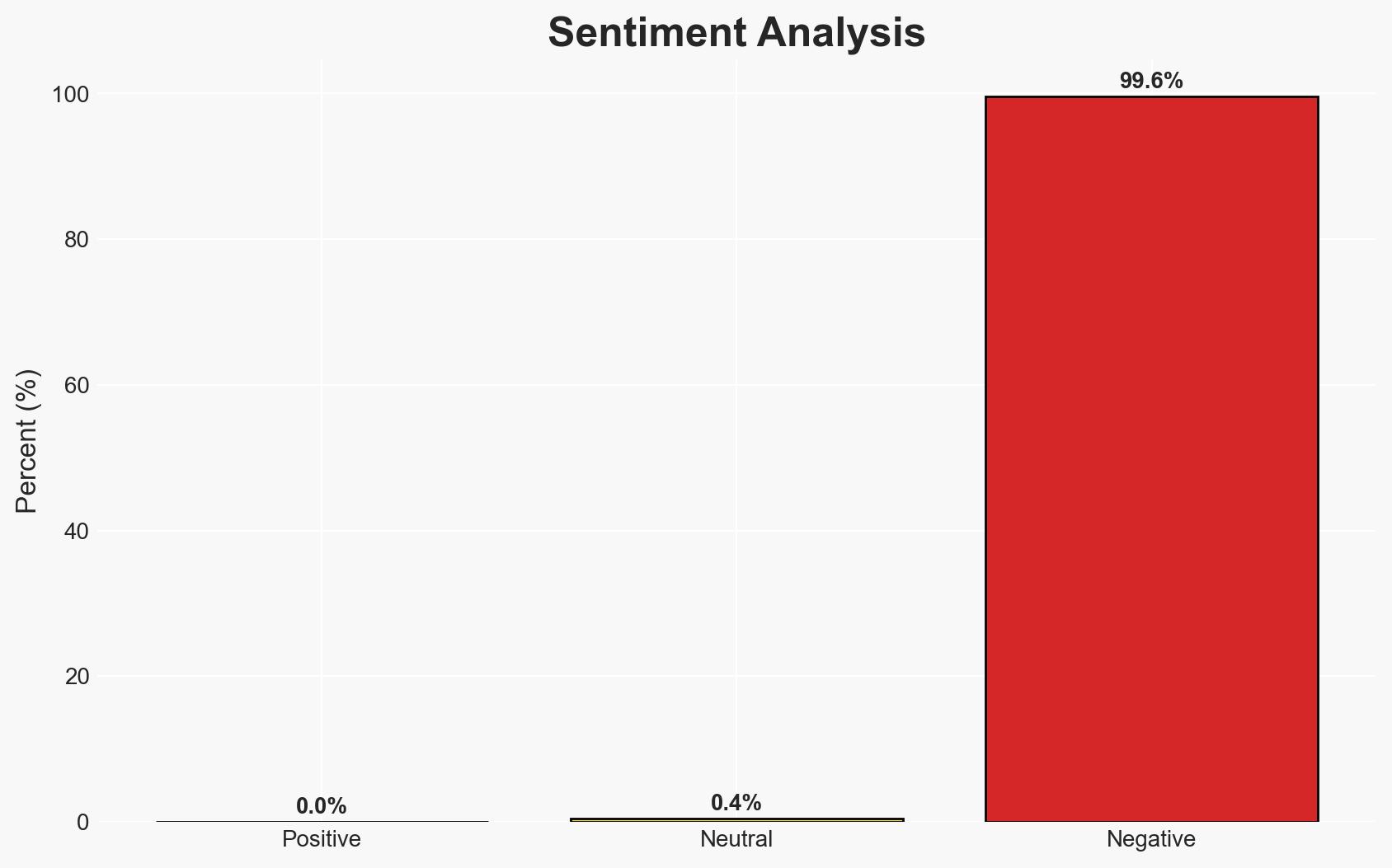
Recent attacks attributed to inspiration from the Islamic State (ISIS) suggest the group remains a persistent ideological threat despite its territorial defeat. The most likely hypothesis is that ISIS continues to inspire decentralized attacks globally, leveraging its ideological influence. This affects national security and counter-terrorism efforts, with moderate confidence in this assessment due to limited direct evidence of centralized coordination.
2. Competing Hypotheses
- Hypothesis A: ISIS is actively coordinating recent attacks through a dispersed network. Supporting evidence includes the historical presence of ISIS fighters and recent attacks attributed to the group. Contradicting evidence is the lack of direct claims of responsibility and the group’s degraded operational capacity.
- Hypothesis B: Recent attacks are independently conducted by individuals or small groups inspired by ISIS ideology without direct coordination. This is supported by the decentralized nature of recent attacks and the ideological persistence of jihadist-Salafism. However, the presence of former fighters and sympathizers poses a risk of reorganization.
- Assessment: Hypothesis B is currently better supported due to the lack of direct claims and evidence of centralized coordination. Indicators such as increased communication from known ISIS operatives or coordinated multi-location attacks could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: ISIS lacks the capacity for centralized coordination; attacks are ideologically motivated rather than operationally directed; regional instability continues to provide fertile ground for extremist ideologies.
- Information Gaps: Details on communication between attackers and any ISIS operatives; intelligence on the current structure and leadership of ISIS.
- Bias & Deception Risks: Confirmation bias in attributing attacks to ISIS; potential misinformation from local sources or groups seeking to exaggerate ISIS influence.
4. Implications and Strategic Risks
The persistence of ISIS-inspired attacks could lead to increased security measures and strain on counter-terrorism resources. This development could exacerbate regional instability and complicate international relations.
- Political / Geopolitical: Potential for increased military engagement in regions with ISIS activity; strain on international alliances focused on counter-terrorism.
- Security / Counter-Terrorism: Need for enhanced intelligence-sharing and monitoring of extremist networks; potential for increased lone-wolf attacks.
- Cyber / Information Space: Risk of ISIS exploiting digital platforms for propaganda and recruitment; need for robust counter-narrative strategies.
- Economic / Social: Potential impact on tourism and foreign investment in affected regions; increased societal tensions and polarization.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of extremist communications; increase security presence at potential targets; engage in public awareness campaigns to counter extremist narratives.
- Medium-Term Posture (1–12 months): Strengthen international counter-terrorism partnerships; invest in community resilience programs; develop capabilities for rapid response to emerging threats.
- Scenario Outlook:
- Best: Successful disruption of extremist networks reduces attack frequency.
- Worst: Coordinated attacks increase, leading to significant casualties and geopolitical tensions.
- Most-Likely: Continued sporadic attacks inspired by ISIS, requiring ongoing vigilance and adaptive counter-terrorism strategies.
6. Key Individuals and Entities
- Islamic State (ISIS)
- Krissy Barrett, Australia’s federal police commissioner
- U.S. Central Command (CENTCOM)
- Philippines Bureau of Immigration
- Not clearly identifiable from open sources in this snippet for specific attackers
7. Thematic Tags
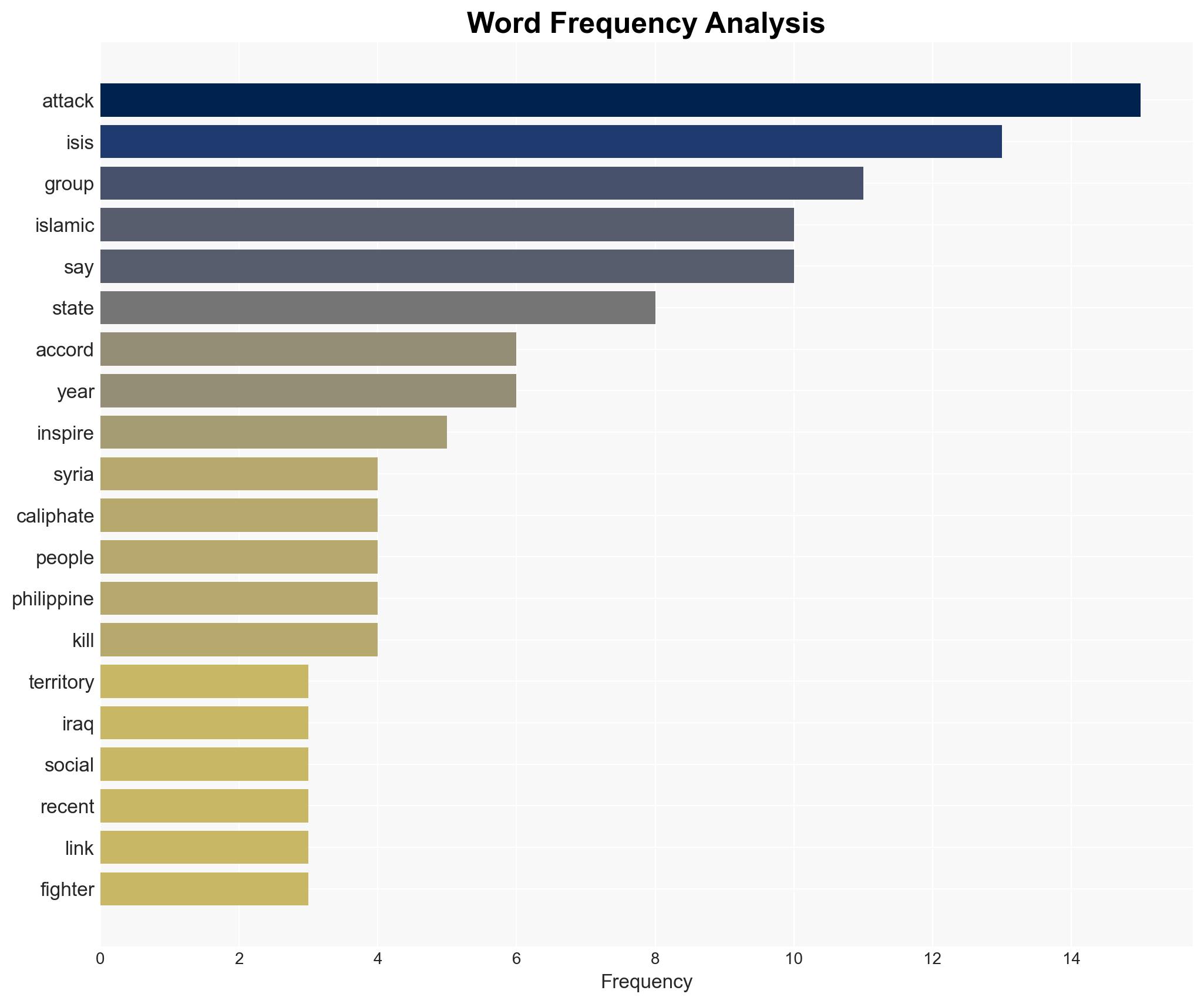
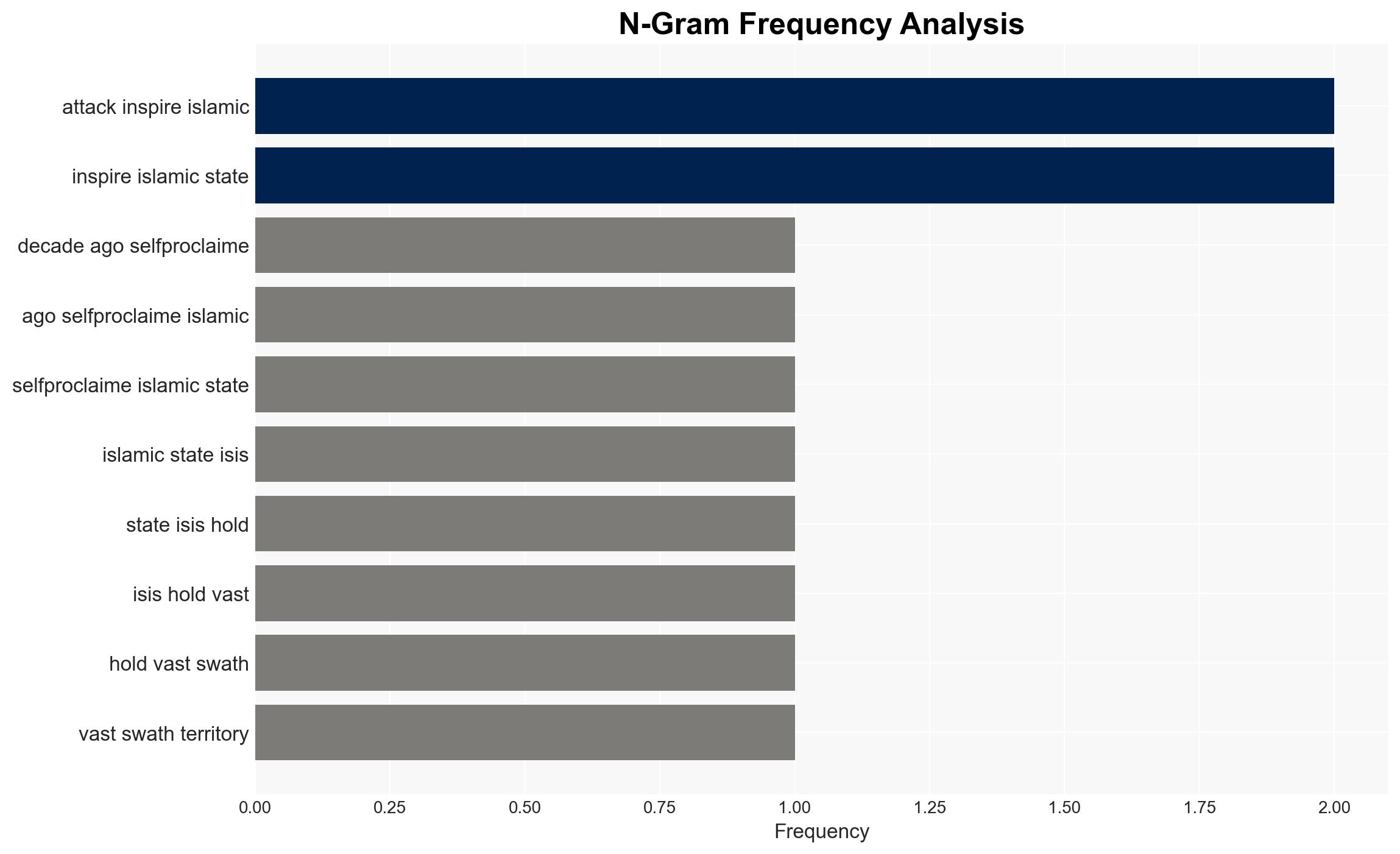
Counter-Terrorism, ISIS, ideological extremism, geopolitical stability, intelligence analysis, security operations, regional instability
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us