CISA Identifies Critical Exploit in ASUS Live Update Amid Ongoing Active Attacks
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA Flags Critical ASUS Live Update Flaw After Evidence of Active Exploitation
1. BLUF (Bottom Line Up Front)
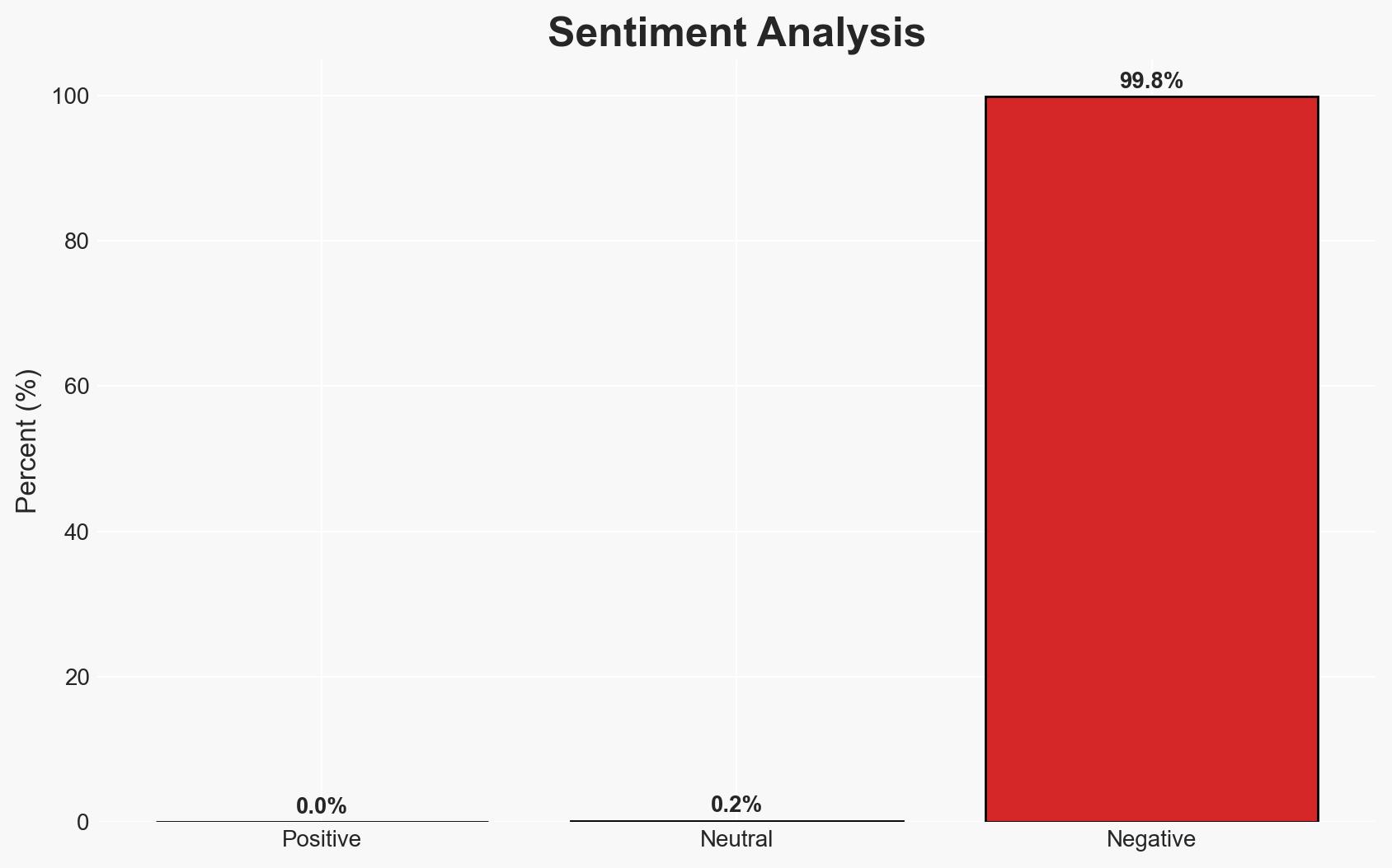
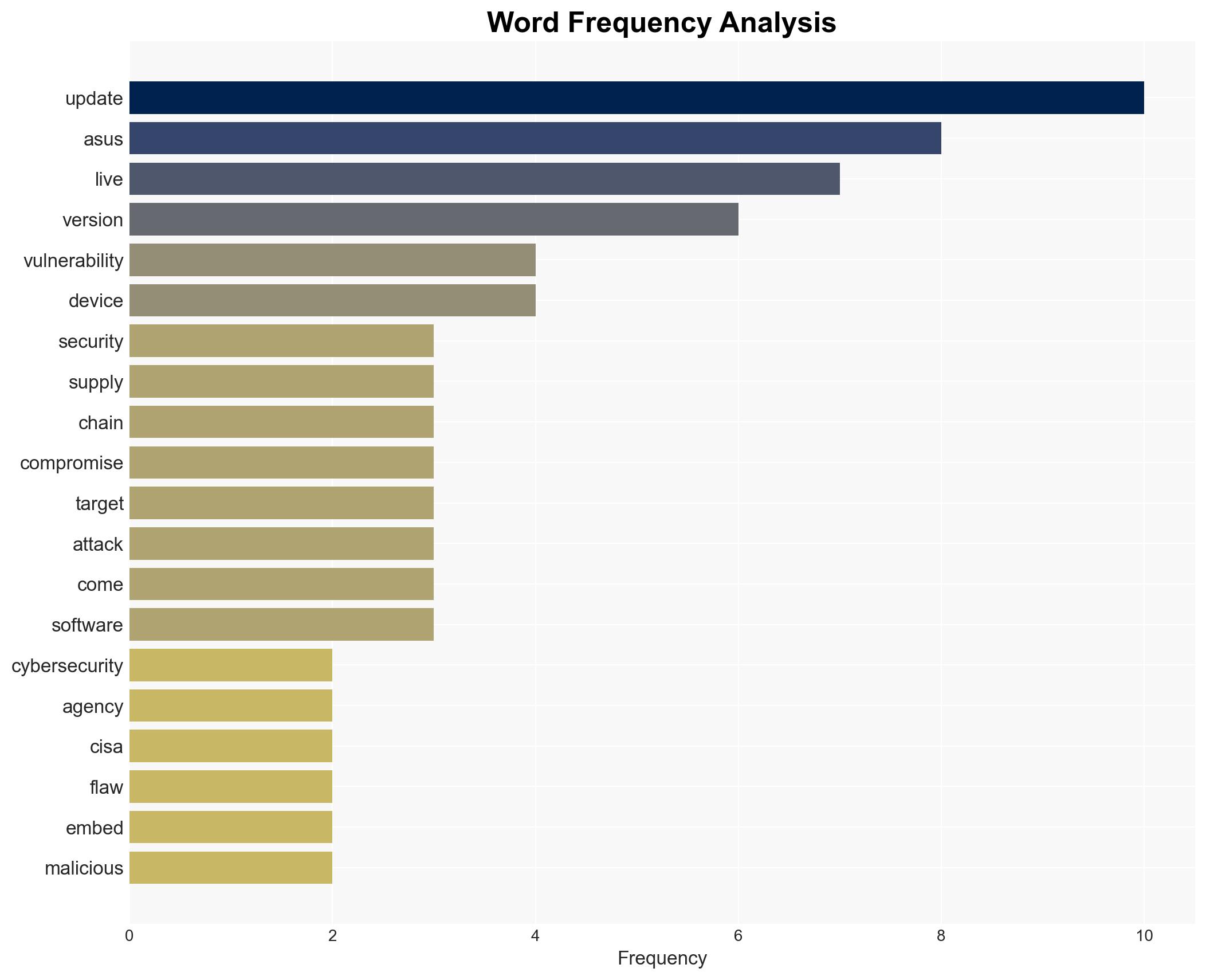
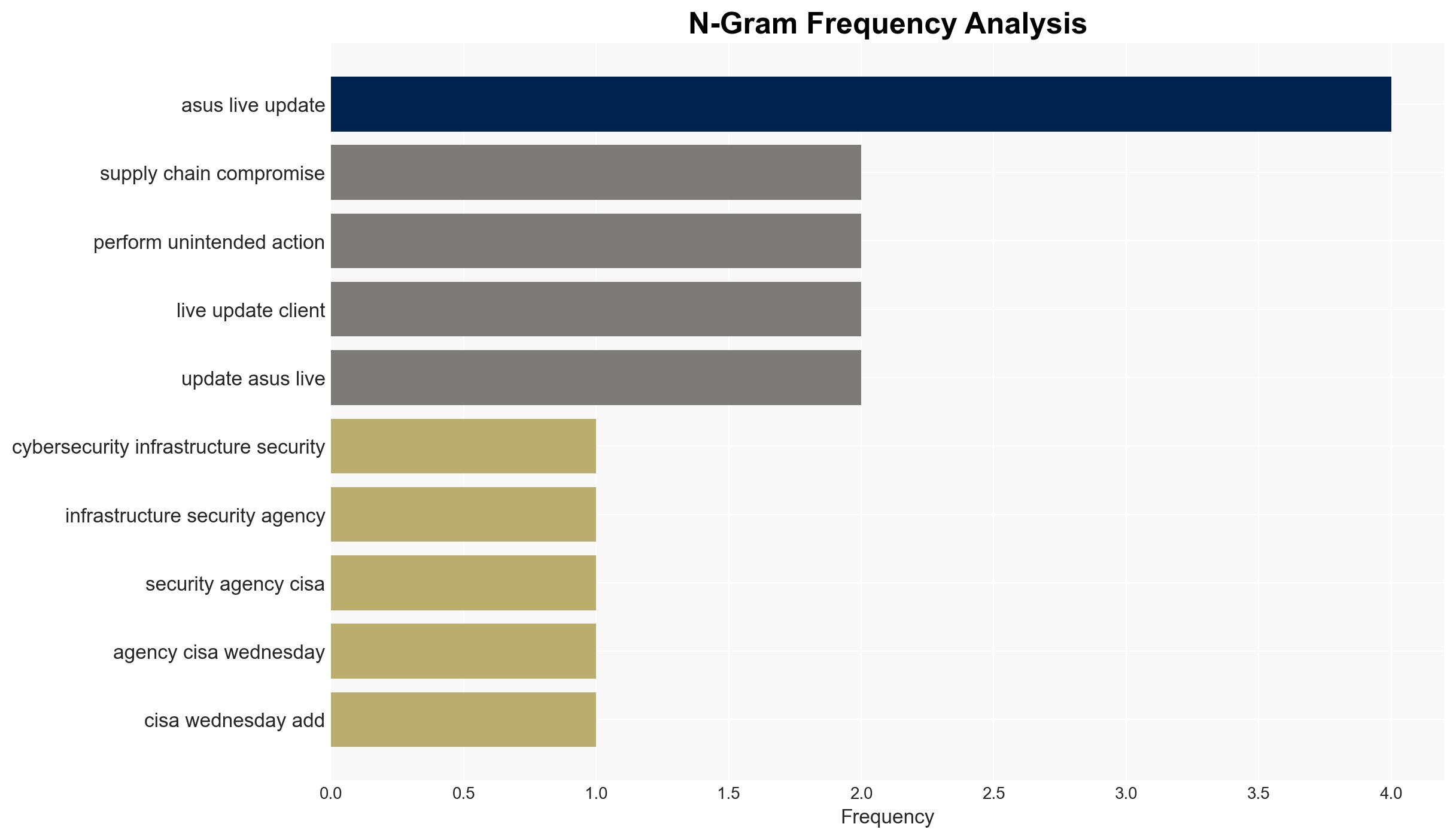
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has identified a critical vulnerability in the ASUS Live Update software, resulting from a supply chain compromise, which is actively being exploited. This flaw, linked to a past APT campaign, poses significant risks to affected systems. The most likely hypothesis is that the exploitation is targeted and limited in scope, affecting specific users identified by MAC addresses. Overall confidence in this judgment is moderate.
2. Competing Hypotheses
- Hypothesis A: The exploitation is a continuation of the 2018 APT campaign targeting specific users based on MAC addresses. This is supported by the historical context of Operation ShadowHammer and the specificity of the targeting. However, uncertainties remain about the current scale and actors involved.
- Hypothesis B: The exploitation is part of a new, broader campaign leveraging the same vulnerability but targeting a wider range of users. This hypothesis is less supported due to the lack of evidence indicating a shift in targeting strategy.
- Assessment: Hypothesis A is currently better supported due to the specificity of the targeting and historical precedent. Indicators that could shift this judgment include evidence of broader targeting or new actor involvement.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is only exploitable on devices with specific MAC addresses; the exploitation is limited to the versions identified in the 2018 campaign; ASUS’s mitigation measures are effective.
- Information Gaps: Current actor identities and motivations; the extent of current exploitation beyond the known targets; effectiveness of ASUS’s mitigation efforts.
- Bias & Deception Risks: Potential bias in relying on historical data from 2018; risk of deception if adversaries are masking broader intentions.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on supply chain vulnerabilities and software update mechanisms. The situation may evolve with further exploitation attempts or new vulnerabilities being discovered.
- Political / Geopolitical: Potential strain on U.S.-China relations if linked to state-sponsored actors; increased international focus on supply chain security.
- Security / Counter-Terrorism: Heightened alert for similar supply chain attacks; potential for copycat operations.
- Cyber / Information Space: Increased emphasis on securing software update channels; potential for misinformation campaigns exploiting the vulnerability.
- Economic / Social: Potential economic impact on ASUS and affected users; erosion of trust in software update mechanisms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Agencies should discontinue use of affected ASUS Live Update versions; increase monitoring for signs of exploitation; engage with ASUS for updates on mitigation efforts.
- Medium-Term Posture (1–12 months): Develop resilience measures for supply chain security; foster partnerships for information sharing on vulnerabilities; enhance capability development in software security.
- Scenario Outlook:
- Best: No further exploitation occurs, and ASUS’s mitigation is effective.
- Worst: New actors exploit the vulnerability, leading to widespread impact.
- Most-Likely: Limited exploitation continues, focused on specific targets.
6. Key Individuals and Entities
- ASUS
- CISA
- Kaspersky
- Advanced Persistent Threat (APT) group (specific identity not clearly identifiable from open sources in this snippet)
7. Thematic Tags
cybersecurity, supply chain security, cyber-espionage, software vulnerabilities, APT, cybersecurity policy, information security, software updates
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us