RansomHouse ransomware attack compromises over 700,000 records at Japanese e-commerce firm Askul
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Askul data breach exposed over 700000 records after ransomware attack
1. BLUF (Bottom Line Up Front)
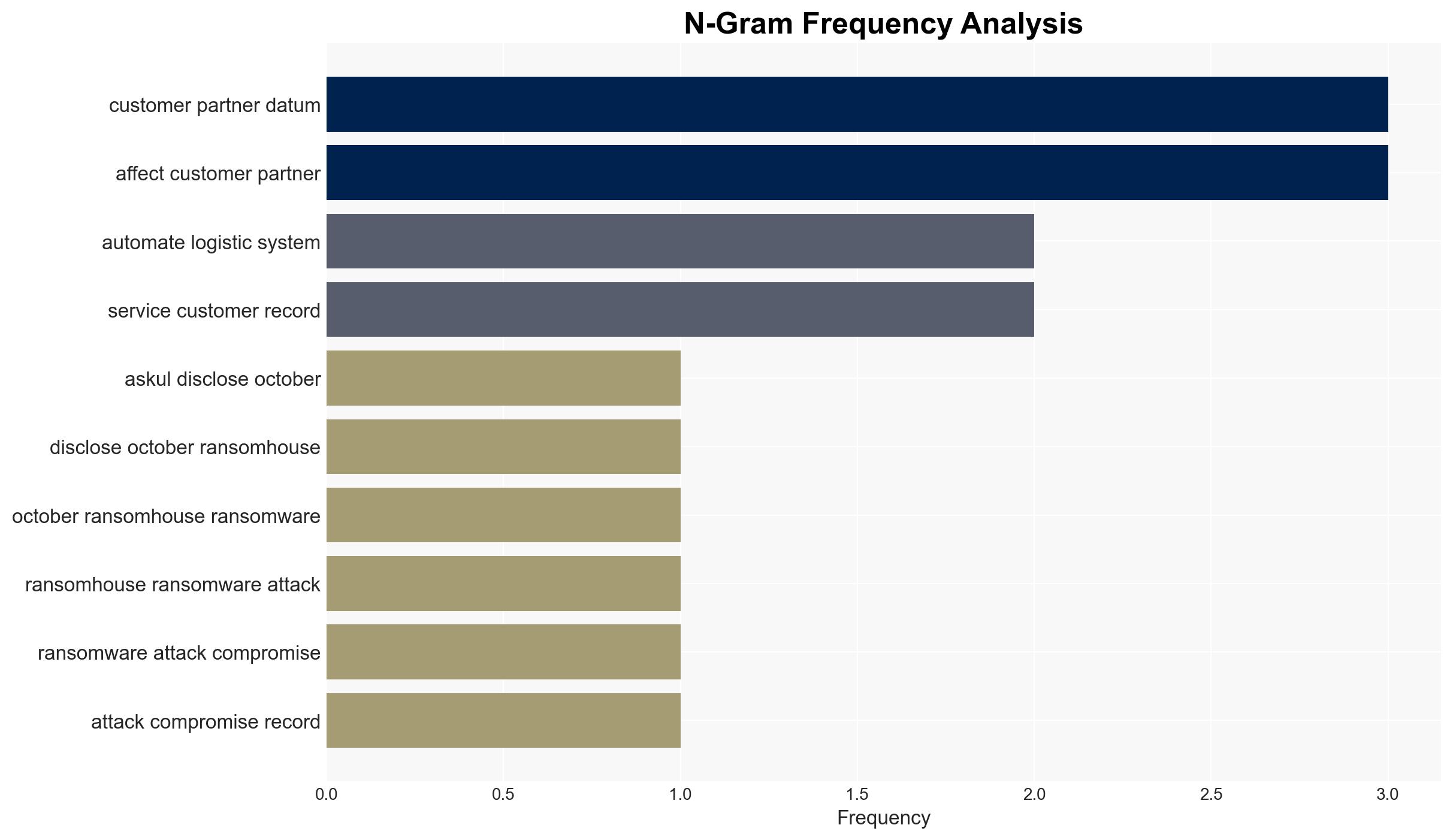
The ransomware attack on Askul, a major Japanese e-commerce and logistics firm, resulted in the compromise of over 700,000 records, affecting customers, partners, and employees. The attack, attributed to the RansomHouse group, highlights vulnerabilities in Askul’s cybersecurity infrastructure. The incident has significant implications for the company’s operations and reputation. Overall confidence in this assessment is moderate, given the available information.
2. Competing Hypotheses
- Hypothesis A: The attack was primarily financially motivated, with RansomHouse seeking ransom payments. This is supported by the group’s history and the release of data following failed negotiations. However, the specific financial demands and negotiation details remain unclear.
- Hypothesis B: The attack may have been part of a broader campaign to disrupt Japanese economic entities, potentially involving state-sponsored actors. This is less supported due to the lack of direct evidence linking the attack to geopolitical motives.
- Assessment: Hypothesis A is currently better supported due to the typical modus operandi of ransomware groups focusing on financial gain. Indicators such as further data releases or communications from RansomHouse could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attack was initiated using stolen credentials; RansomHouse is primarily financially motivated; Askul’s cybersecurity measures were inadequate.
- Information Gaps: Details of the negotiation process with RansomHouse; specific vulnerabilities exploited; full scope of data compromised.
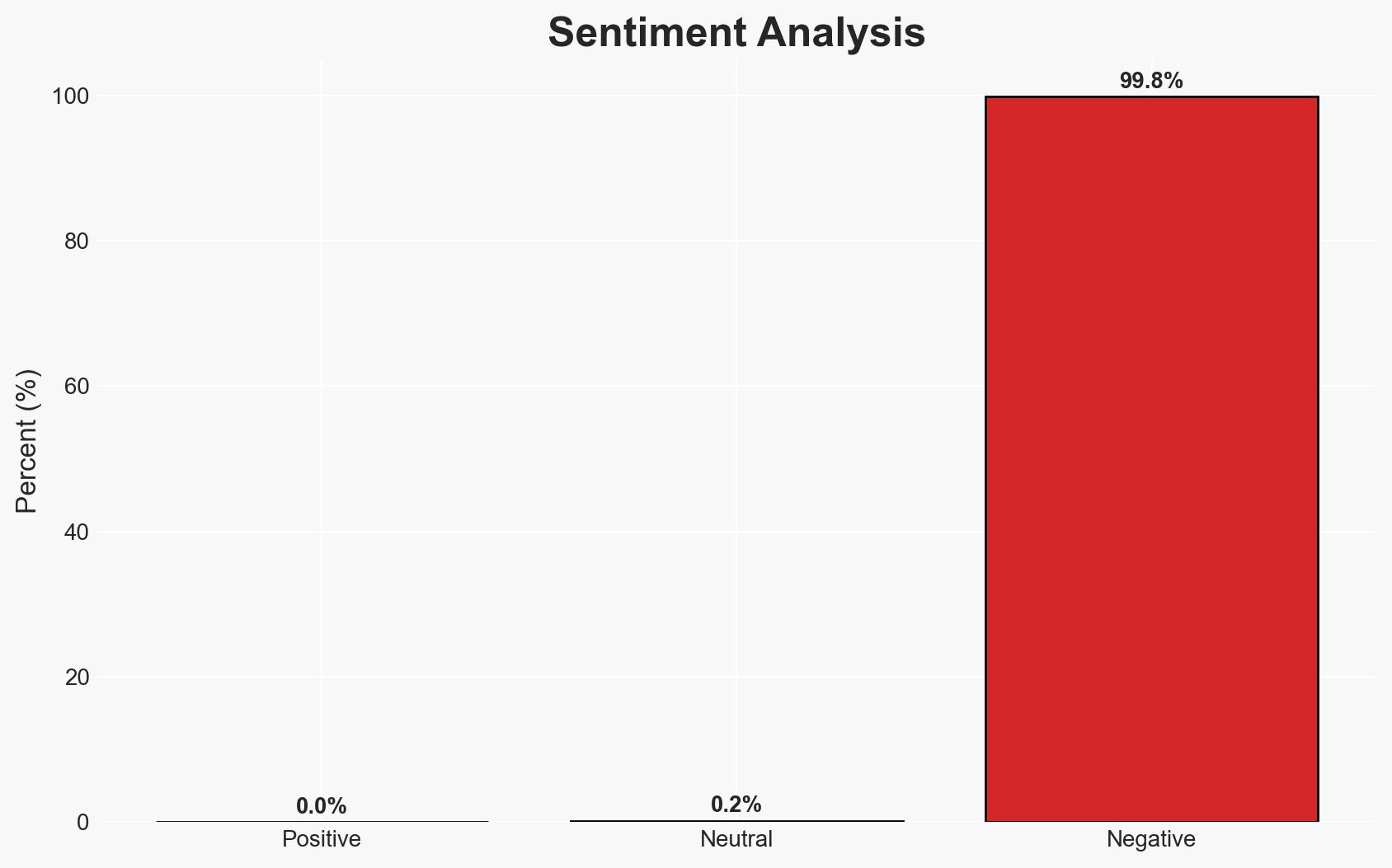
- Bias & Deception Risks: Potential bias in company disclosures to minimize reputational damage; possible manipulation by RansomHouse in their public claims.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on cybersecurity practices within Japanese firms and potential regulatory changes. The incident may also embolden other cybercriminal groups to target similar companies.
- Political / Geopolitical: Potential for increased tensions if state-sponsored involvement is suspected, impacting Japan’s international relations.
- Security / Counter-Terrorism: Heightened threat environment for Japanese corporations, requiring enhanced security measures.
- Cyber / Information Space: Increased risk of copycat attacks and further data breaches, necessitating improved cybersecurity protocols.
- Economic / Social: Possible loss of consumer trust in Askul, affecting its market position and financial performance.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive cybersecurity audit; enhance monitoring of Askul’s network for further breaches; engage with law enforcement and cybersecurity experts.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; implement robust incident response plans; invest in employee cybersecurity training.
- Scenario Outlook:
- Best: Rapid recovery and strengthening of cybersecurity measures restore confidence.
- Worst: Continued data leaks and regulatory penalties severely damage Askul’s reputation and financial standing.
- Most-Likely: Gradual recovery with ongoing challenges in restoring full customer trust and operational efficiency.
6. Key Individuals and Entities
- Askul Corporation
- RansomHouse (ransomware group)
- LOHACO/Yahoo Japan ecosystem
- Personal Information Protection Commission (Japan)
7. Thematic Tags
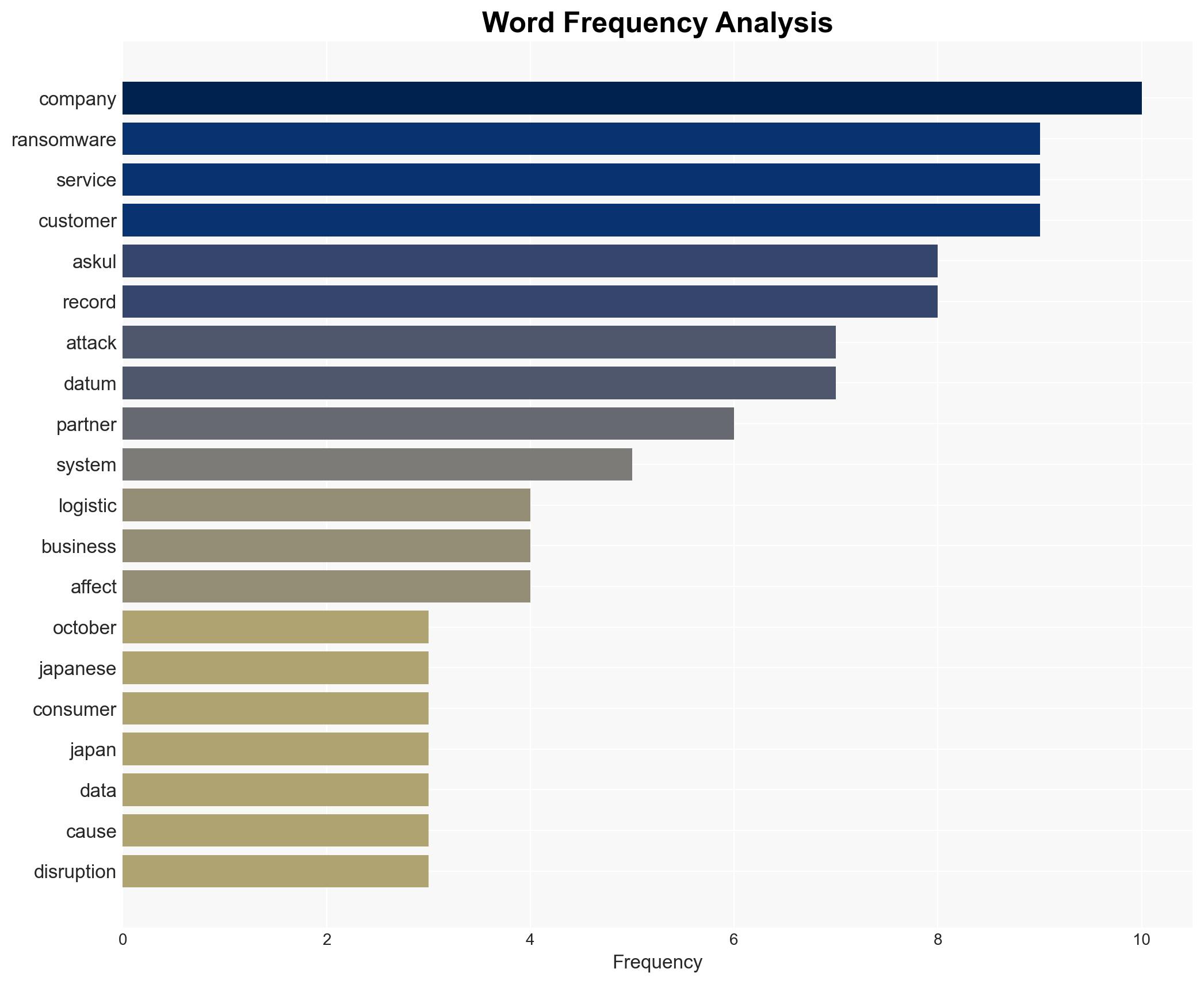
cybersecurity, ransomware, data breach, e-commerce, Japan, information security, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us