Urban VPN Proxy Exposed for Stealing User Data; Users Urged to Choose Secure VPN Alternatives
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Urban VPN Proxy is the latest free VPN spying on users here’s how to stay safe
1. BLUF (Bottom Line Up Front)
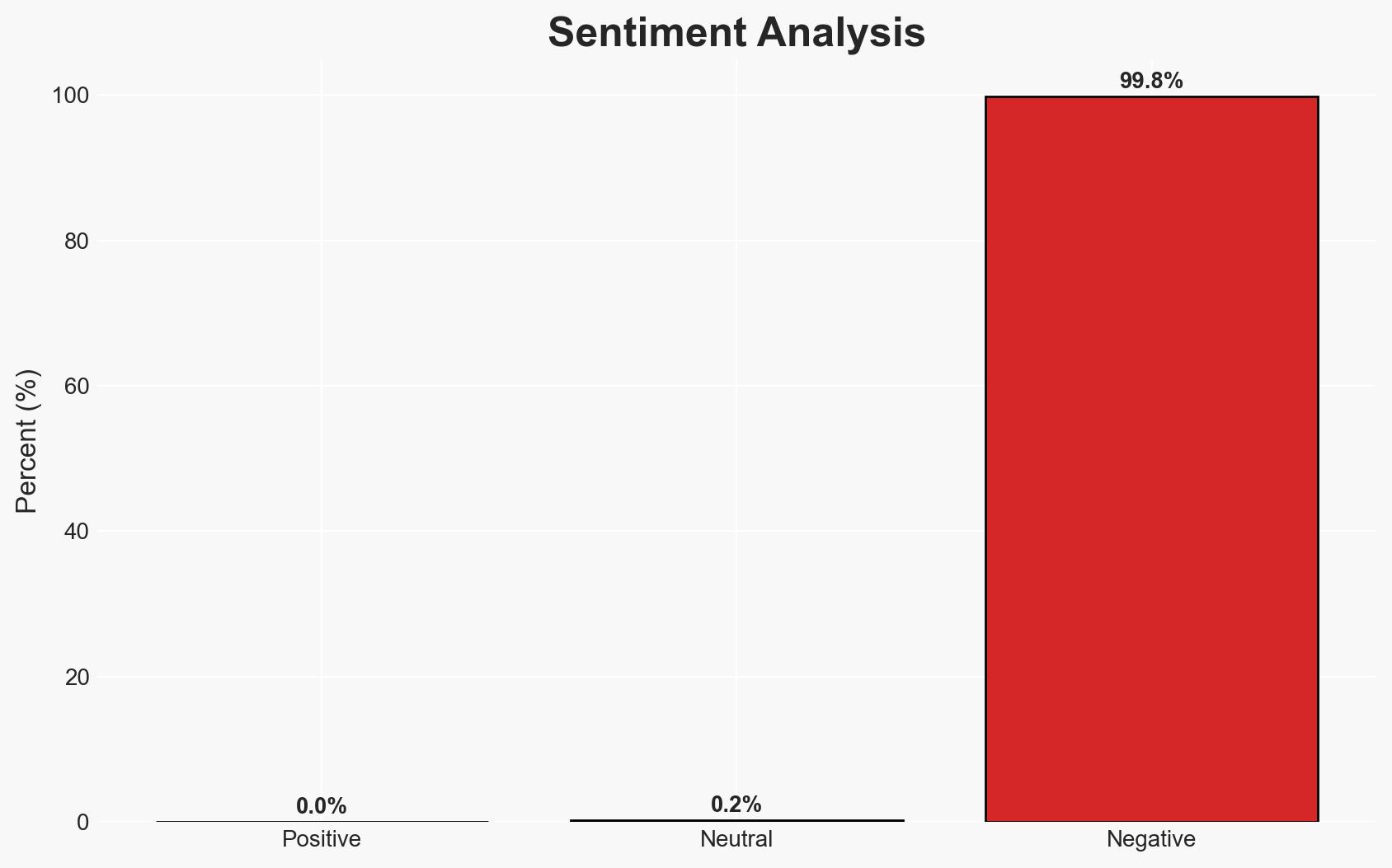
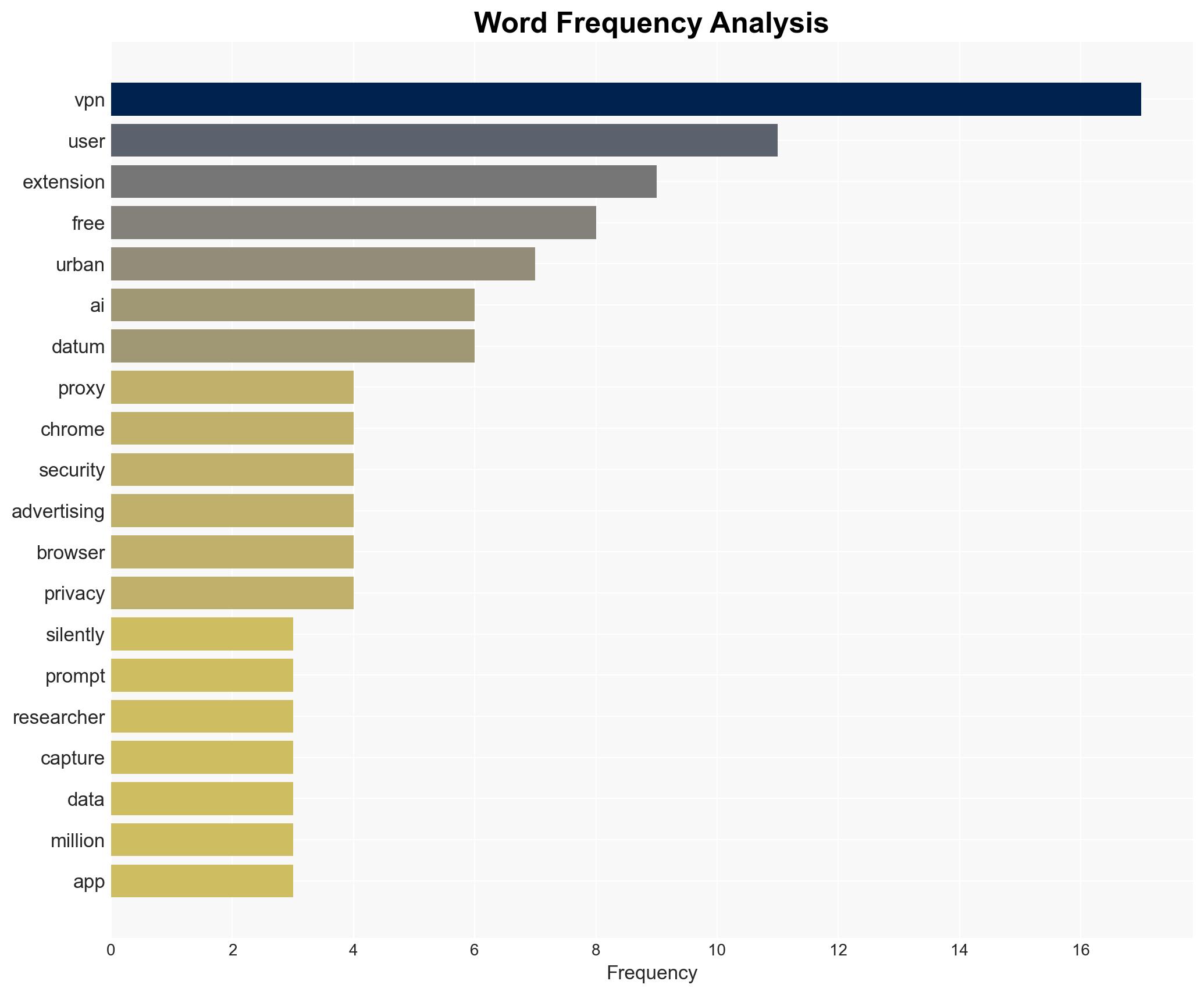
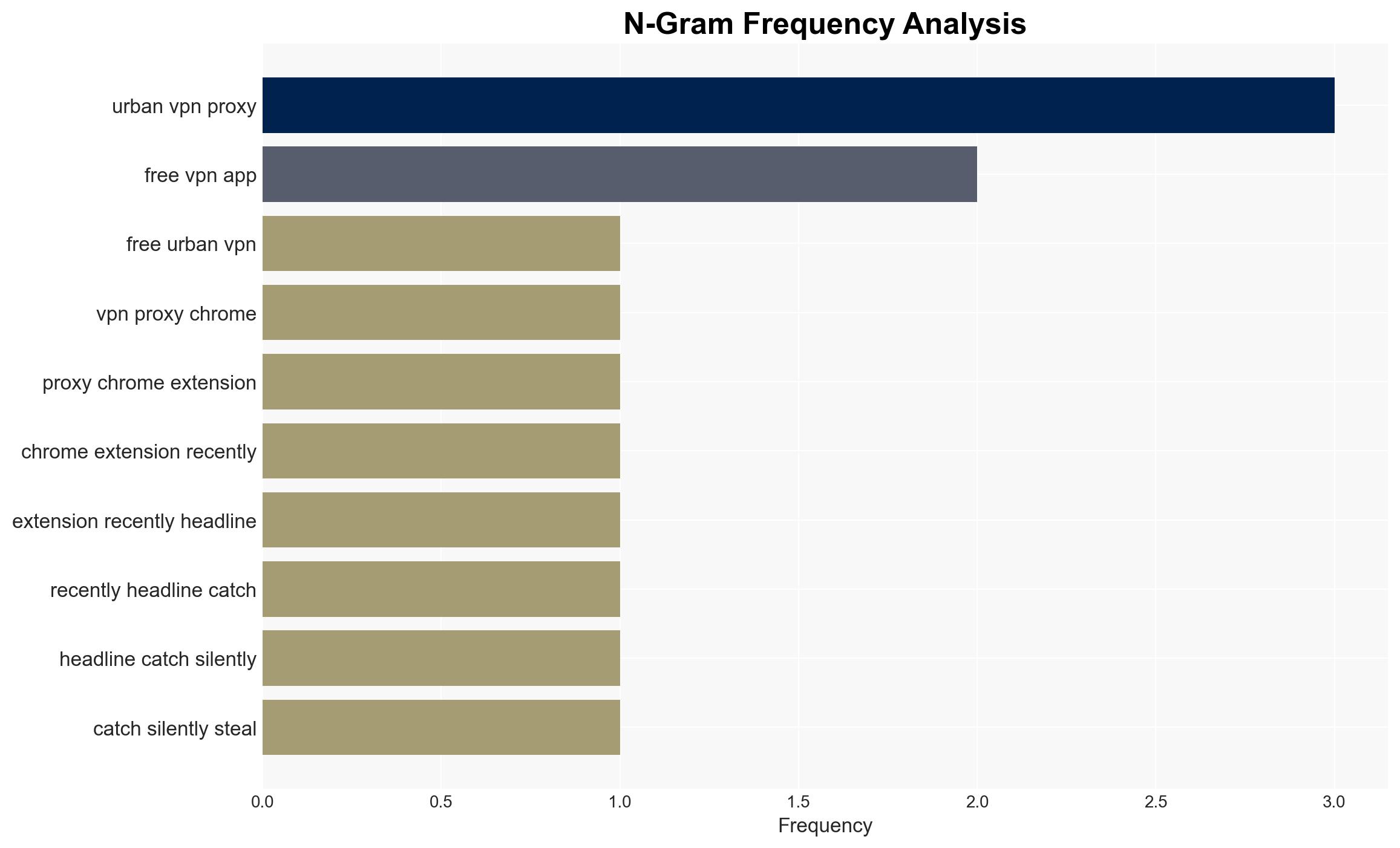
The Urban VPN Proxy extension has been identified as covertly capturing and selling user data, impacting an estimated eight million users. This incident highlights the broader risk of free VPN services being used for data exploitation. The most likely hypothesis is that Urban VPN is intentionally engaging in data harvesting for profit. Overall confidence in this judgment is moderate due to the lack of direct evidence of intent beyond the technical findings.
2. Competing Hypotheses
- Hypothesis A: Urban VPN Proxy intentionally incorporated data harvesting scripts to monetize user data. This is supported by the presence of concealed scripts and the sale of data to brokers. However, the company’s intent and internal decision-making processes remain unclear.
- Hypothesis B: The data harvesting was an unauthorized action by a rogue developer or a third-party compromise. This hypothesis lacks direct evidence but cannot be ruled out without further investigation into the company’s internal controls and security practices.
- Assessment: Hypothesis A is currently better supported due to the structured nature of the data collection and transmission to known analytics endpoints. Key indicators that could shift this judgment include internal communications from Urban VPN or evidence of external compromise.
3. Key Assumptions and Red Flags
- Assumptions: Urban VPN has control over its codebase; the data harvesting was financially motivated; users were unaware of the data collection.
- Information Gaps: Details on Urban VPN’s internal decision-making processes and security practices; potential involvement of external actors.
- Bias & Deception Risks: Confirmation bias in interpreting technical findings as intentional; potential source bias from security researchers with vested interests.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of VPN services and regulatory actions, affecting the broader digital privacy landscape.
- Political / Geopolitical: Potential for international regulatory responses and increased tensions over data privacy standards.
- Security / Counter-Terrorism: Increased risk of data breaches and exploitation by malicious actors leveraging harvested data.
- Cyber / Information Space: Heightened awareness and skepticism towards free digital privacy tools; potential for increased cyber hygiene practices.
- Economic / Social: Erosion of trust in digital privacy solutions could impact market dynamics and user behavior.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough security audit of Urban VPN and similar services; issue public advisories on the risks of free VPNs.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to enhance monitoring of VPN services; advocate for stronger regulatory frameworks.
- Scenario Outlook:
- Best: Urban VPN ceases data harvesting and enhances transparency, restoring user trust.
- Worst: Continued exploitation leads to significant data breaches and regulatory crackdowns.
- Most-Likely: Increased scrutiny results in improved industry standards and user awareness.
6. Key Individuals and Entities
- Urban VPN
- Koi Security
- BiScience
- AdClarity
- Clickstream OS
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data privacy, VPN exploitation, digital surveillance, user data monetization, regulatory response, cyber hygiene
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us