Assessing the Escalating Jihadi Terrorism Threat in West Africa: Implications for Ghana’s Security Strategies
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Feature The Rising Jihadi Terrorism Threat Across West Africa A Case For The Re-Examination Of Ghanas Response Strategies
1. BLUF (Bottom Line Up Front)
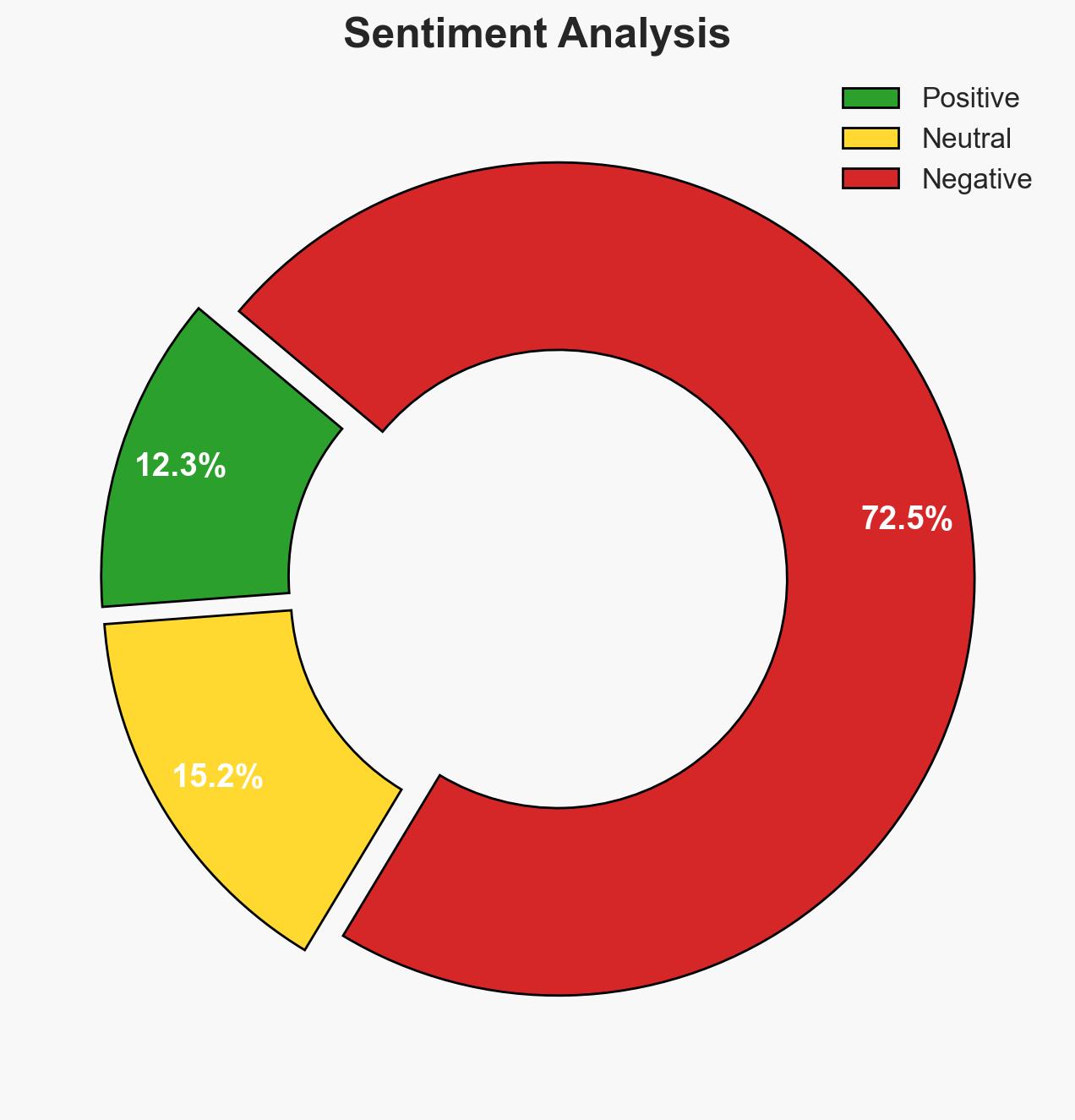
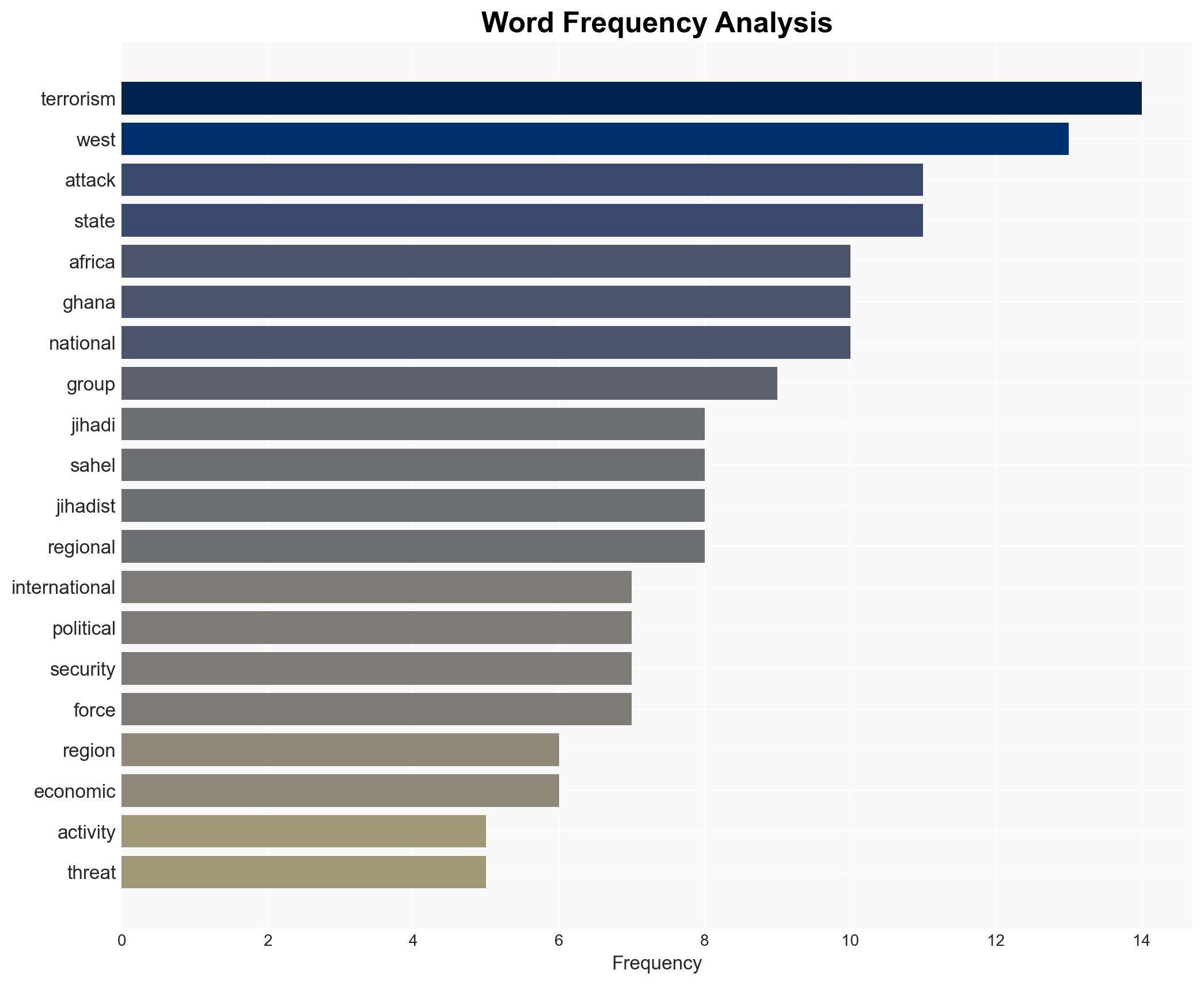
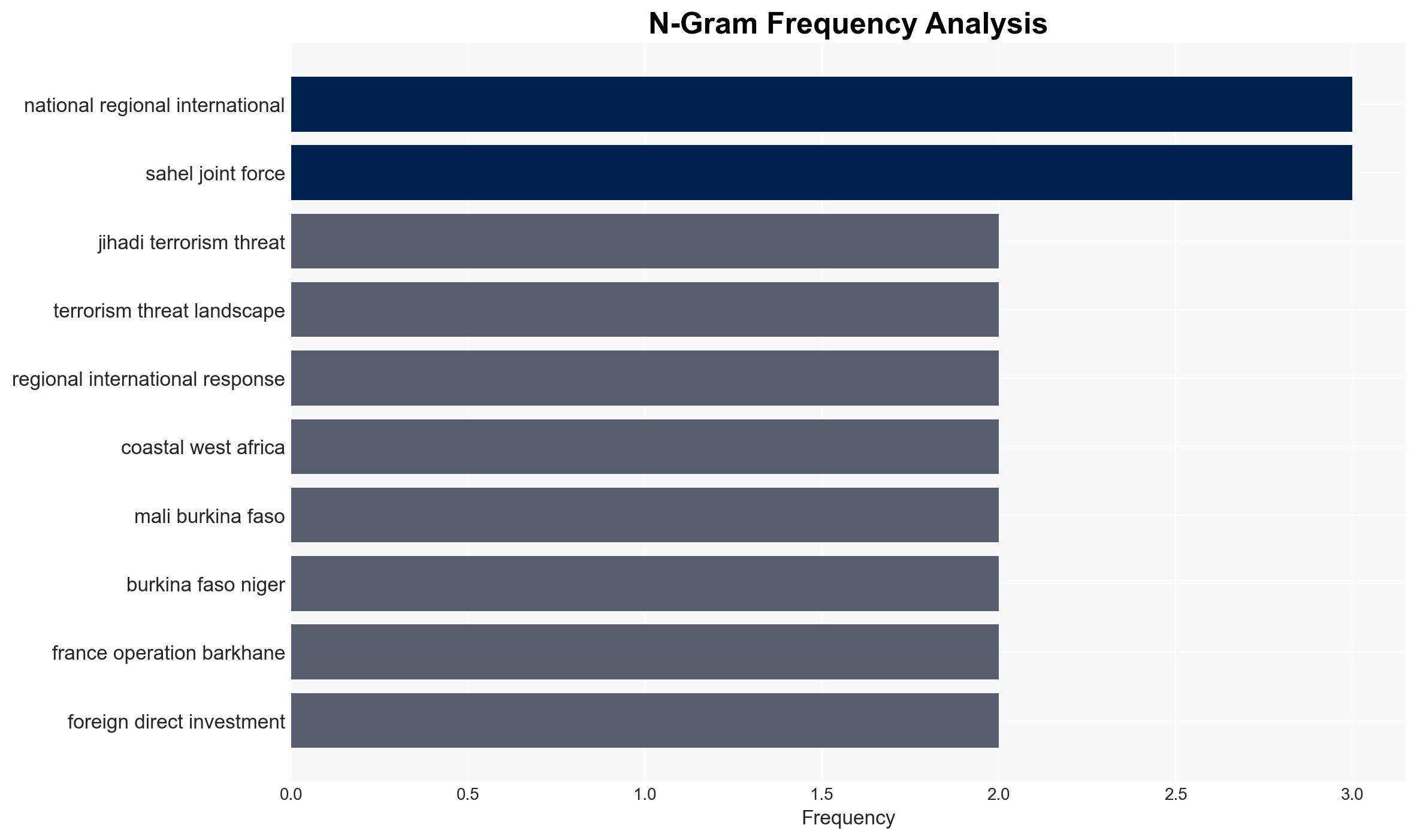
The increasing incidence of jihadi terrorism in West Africa, particularly by groups such as Boko Haram and JNIM, poses a significant threat to regional stability and security. Ghana, while not yet directly affected, must reassess its counter-terrorism strategies to address potential spillover effects. This assessment is made with moderate confidence, considering the current trends and reported data.
2. Competing Hypotheses
- Hypothesis A: Jihadi terrorist groups will continue to expand their operations into coastal West African states, including Ghana, due to their strategic objectives and current trajectory. Supporting evidence includes the increase in attacks in neighboring countries and the strategic importance of coastal regions. Key uncertainties include the capacity of these groups to sustain operations in new territories.
- Hypothesis B: The current containment efforts by regional and international actors will prevent significant expansion of jihadi activities into Ghana. This is supported by the lack of attacks in Ghana to date and ongoing regional security cooperation. Contradicting evidence includes the persistent rise in attacks in other coastal states.
- Assessment: Hypothesis A is currently better supported due to the documented increase in regional attacks and the strategic motivations of jihadi groups. Indicators that could shift this judgment include successful regional military interventions or significant internal disruptions within these terrorist organizations.
3. Key Assumptions and Red Flags
- Assumptions: Jihadi groups are motivated by strategic control over coastal regions; regional security cooperation remains constant; Ghana’s current security posture is insufficient against potential threats.
- Information Gaps: Detailed intelligence on the operational capabilities and intentions of jihadi groups specifically targeting Ghana.
- Bias & Deception Risks: Potential over-reliance on regional security reports which may understate threats to maintain political stability; possible misinformation campaigns by jihadi groups to mislead security assessments.
4. Implications and Strategic Risks
The evolving jihadi threat in West Africa could destabilize the region, affecting political stability, security, and economic development.
- Political / Geopolitical: Increased pressure on regional governments to enhance security cooperation and address root causes of extremism.
- Security / Counter-Terrorism: Potential for increased military engagement and resource allocation to counter-terrorism efforts.
- Cyber / Information Space: Possible increase in cyber operations by jihadi groups to disrupt communications and spread propaganda.
- Economic / Social: Potential negative impact on foreign investment and tourism, exacerbating economic challenges and social unrest.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence-sharing mechanisms with regional partners and increase surveillance of border regions.
- Medium-Term Posture (1–12 months): Develop comprehensive counter-terrorism strategies that include community engagement and deradicalization programs.
- Scenario Outlook:
- Best: Effective regional cooperation contains the threat, and Ghana remains unaffected.
- Worst: Jihadi groups establish a foothold in Ghana, leading to increased attacks and instability.
- Most-Likely: Sporadic incidents occur, prompting a reassessment of national security strategies.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Counter-Terrorism, West Africa, jihadi terrorism, regional security, Ghana, Boko Haram, JNIM
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us