APT28 Launches Extended Phishing Campaign Against Users of Ukrainian Webmail Service UKR.net
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: APT28 Targets Ukrainian UKR-net Users in Long-Running Credential Phishing Campaign
1. BLUF (Bottom Line Up Front)
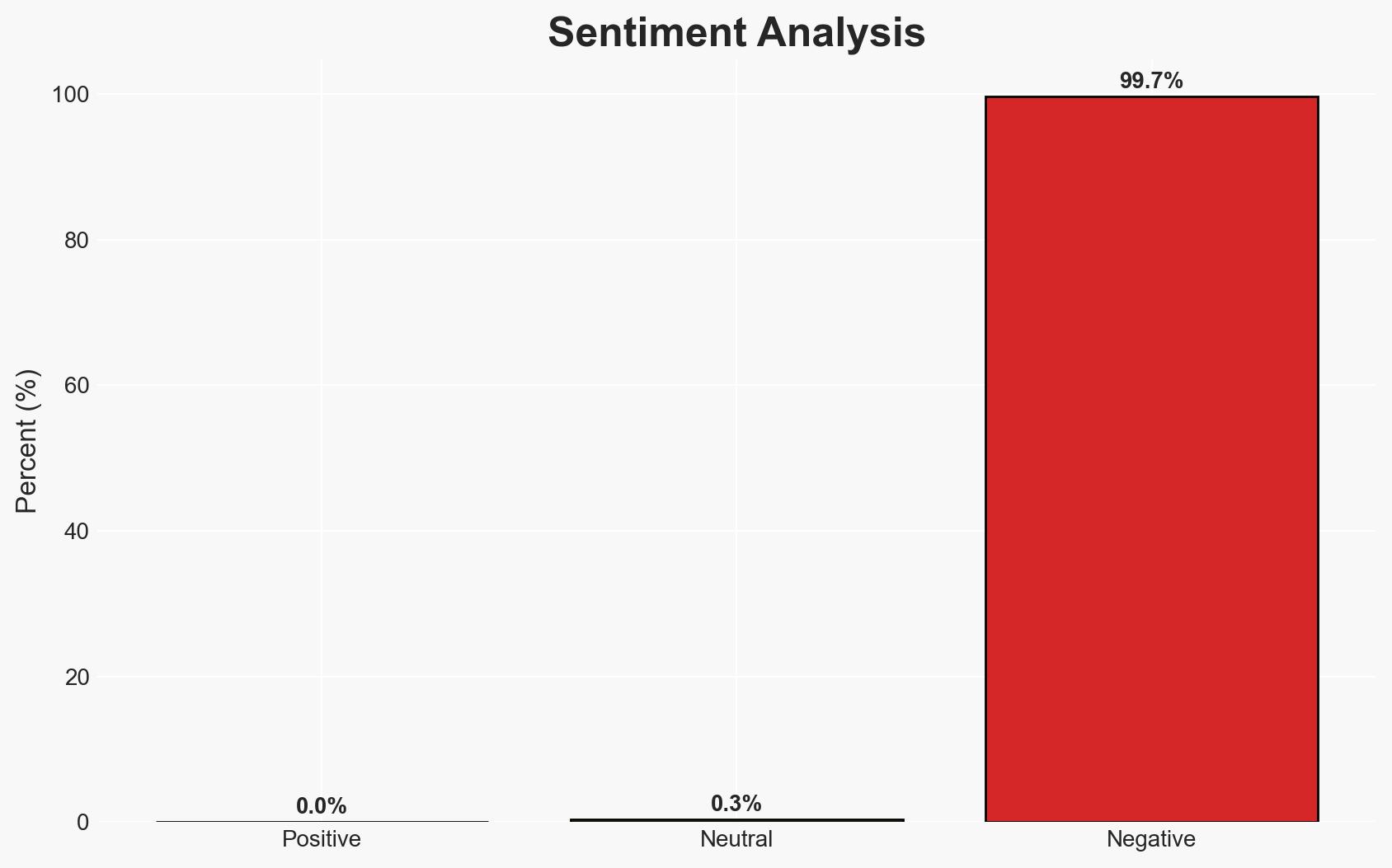
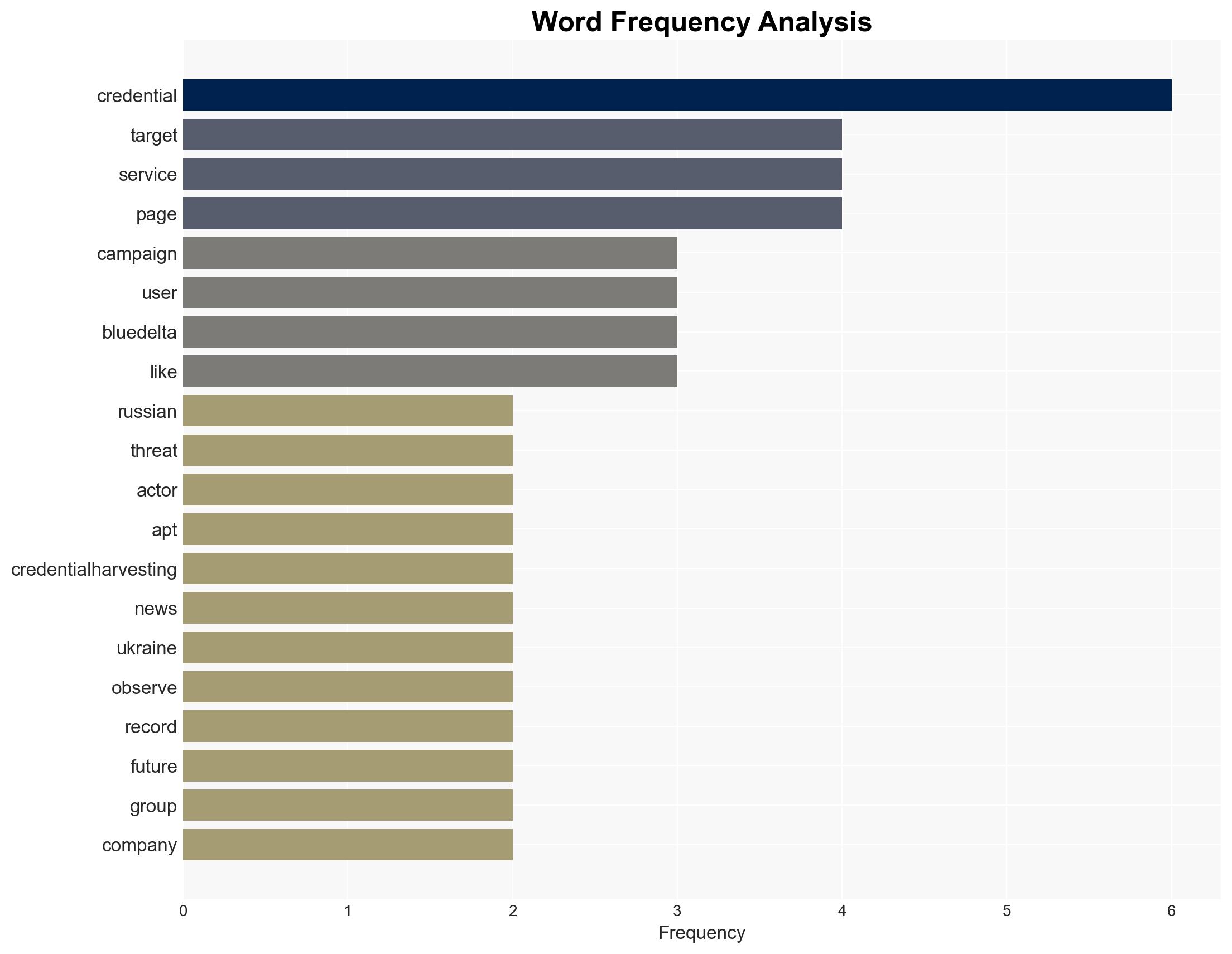
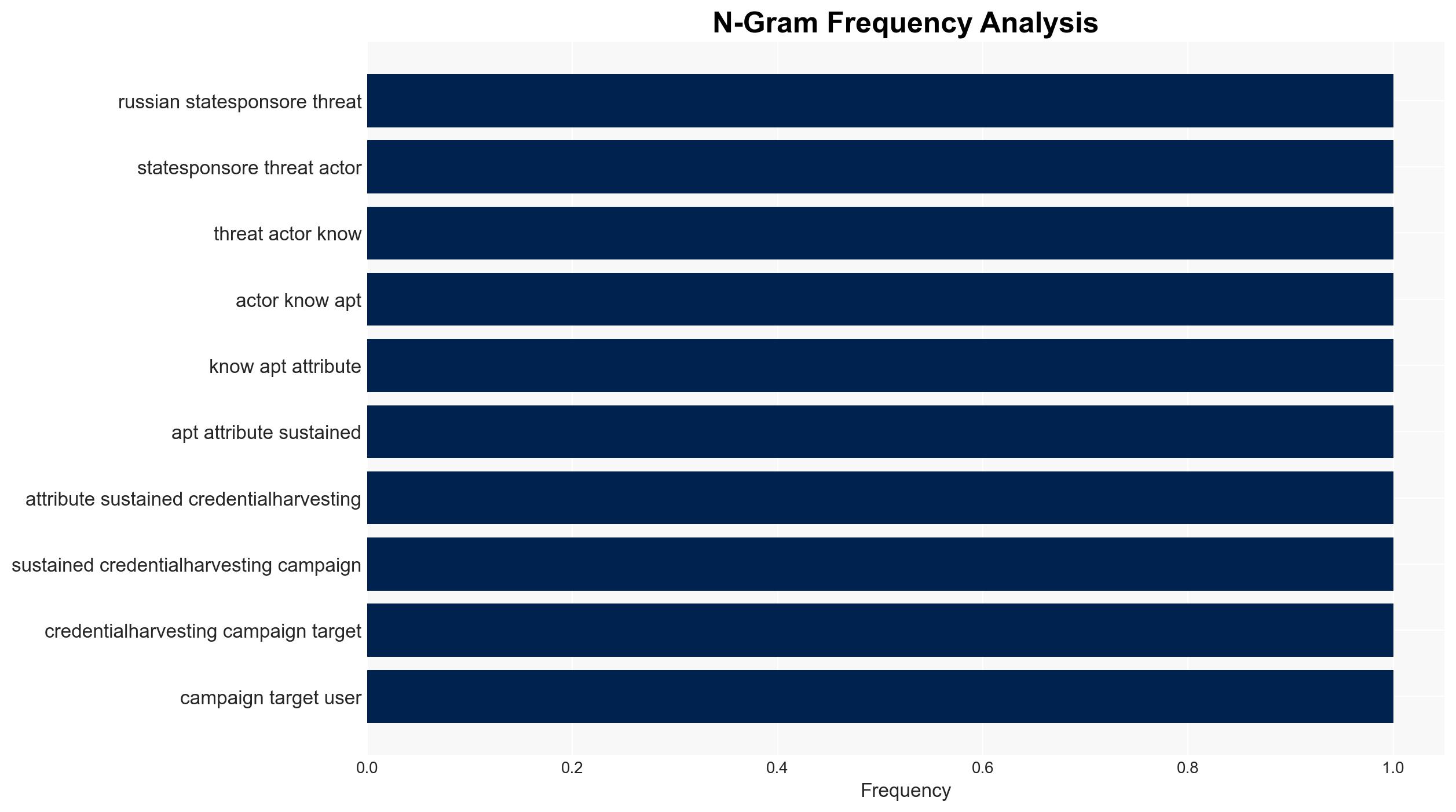
The Russian state-sponsored group APT28 is conducting a sustained credential phishing campaign targeting Ukrainian UKR-net users, likely to support GRU intelligence objectives amid the ongoing conflict in Ukraine. The campaign’s use of adaptive tactics, such as anonymized tunneling, indicates a high level of sophistication. This assessment is made with moderate confidence due to the consistent historical pattern of APT28’s activities and the current geopolitical context.
2. Competing Hypotheses
- Hypothesis A: APT28 is targeting UKR-net users to collect intelligence in support of Russian military operations in Ukraine. This is supported by the group’s historical focus on intelligence collection and the ongoing conflict. However, specific targets within Ukraine remain unidentified, creating uncertainty.
- Hypothesis B: The campaign is a broader effort to disrupt Ukrainian communications and sow confusion, rather than solely intelligence gathering. While this aligns with broader Russian cyber strategies, the lack of direct evidence of disruption efforts contradicts this hypothesis.
- Assessment: Hypothesis A is currently better supported due to APT28’s known association with GRU intelligence operations and the strategic importance of Ukrainian intelligence. Indicators such as increased targeting of non-governmental entities could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: APT28 operates under GRU directives; the campaign’s primary goal is intelligence collection; the use of anonymized tunneling is a response to infrastructure takedowns.
- Information Gaps: Specific identities of targeted individuals or entities; full scope of data compromised; potential collaboration with other threat actors.
- Bias & Deception Risks: Potential bias in attributing all activities to APT28; deception through false flag operations or misattribution by adversaries.
4. Implications and Strategic Risks
This development could exacerbate tensions between Russia and Ukraine, with potential spillover effects on NATO and EU cybersecurity postures. The campaign highlights the persistent threat of state-sponsored cyber operations and the need for robust defensive measures.
- Political / Geopolitical: Escalation in cyber conflict could lead to increased sanctions or diplomatic actions against Russia.
- Security / Counter-Terrorism: Heightened alertness in cybersecurity defenses across Ukrainian and allied networks.
- Cyber / Information Space: Potential for increased cyber espionage activities targeting critical infrastructure and governmental communications.
- Economic / Social: Potential destabilization of Ukrainian digital infrastructure, impacting economic activities and public trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of phishing activities; deploy updated security protocols for UKR-net users; engage in public awareness campaigns.
- Medium-Term Posture (1–12 months): Strengthen international cybersecurity partnerships; invest in advanced threat detection capabilities; review and update incident response plans.
- Scenario Outlook:
- Best: Successful mitigation of phishing campaigns, leading to decreased effectiveness of APT28 operations.
- Worst: Escalation of cyber activities leading to significant breaches of critical infrastructure.
- Most-Likely: Continued low-level phishing activities with periodic spikes in intensity, requiring ongoing vigilance.
6. Key Individuals and Entities
- APT28 (Fancy Bear, BlueDelta, etc.)
- GRU (Main Directorate of the General Staff of the Russian Federation’s Armed Forces)
- Recorded Future’s Insikt Group
- Mastercard-owned cybersecurity company
- UKR-net
7. Thematic Tags
cybersecurity, cyber-espionage, phishing, Russian cyber operations, GRU, Ukraine conflict, credential theft
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us