Cybercriminals Upload 14 Malicious NuGet Packages to Steal Crypto Wallets and Advertising Data
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: 14 Malicious NuGet Packages Found Stealing Crypto Wallets and Ad Data
1. BLUF (Bottom Line Up Front)
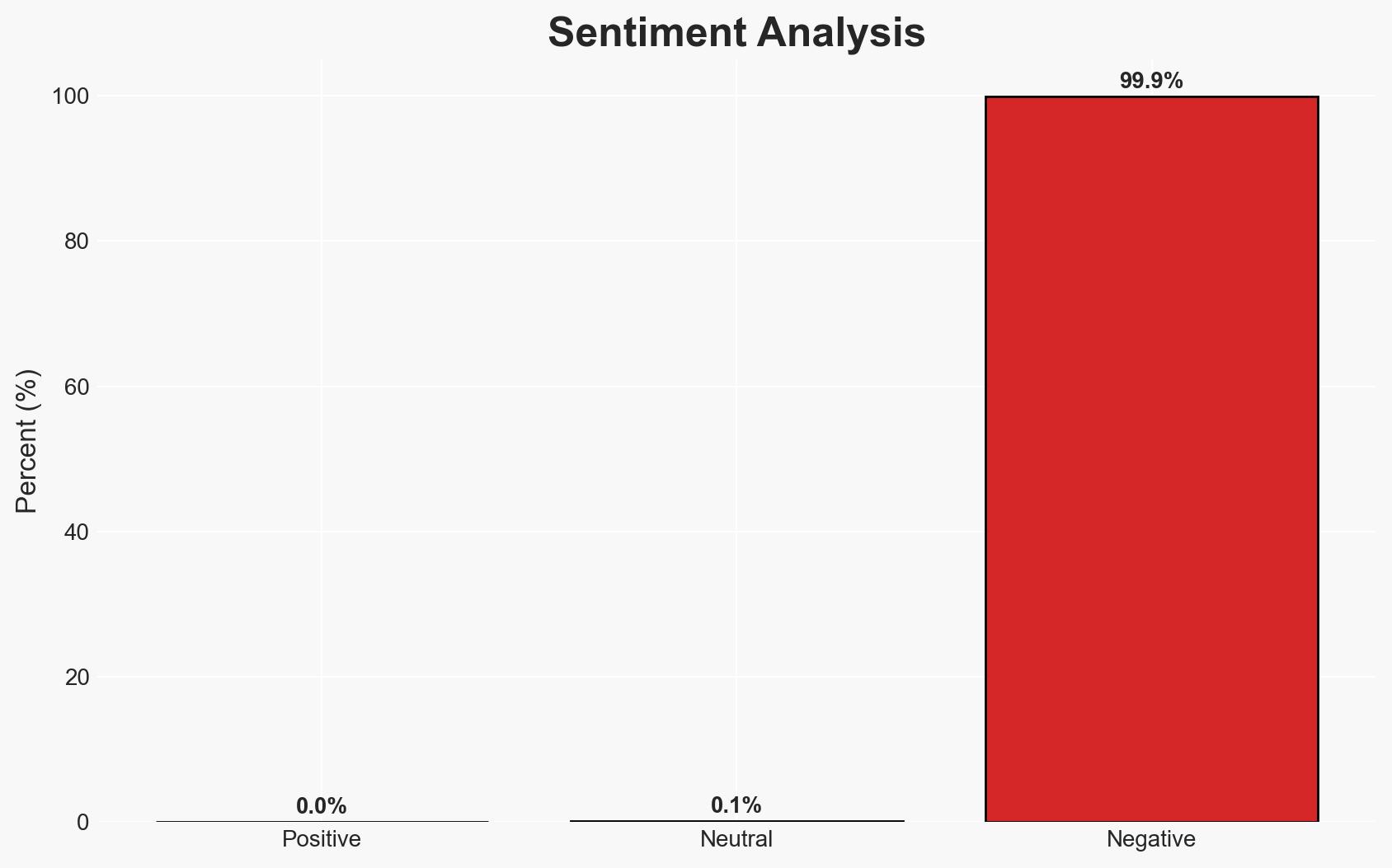
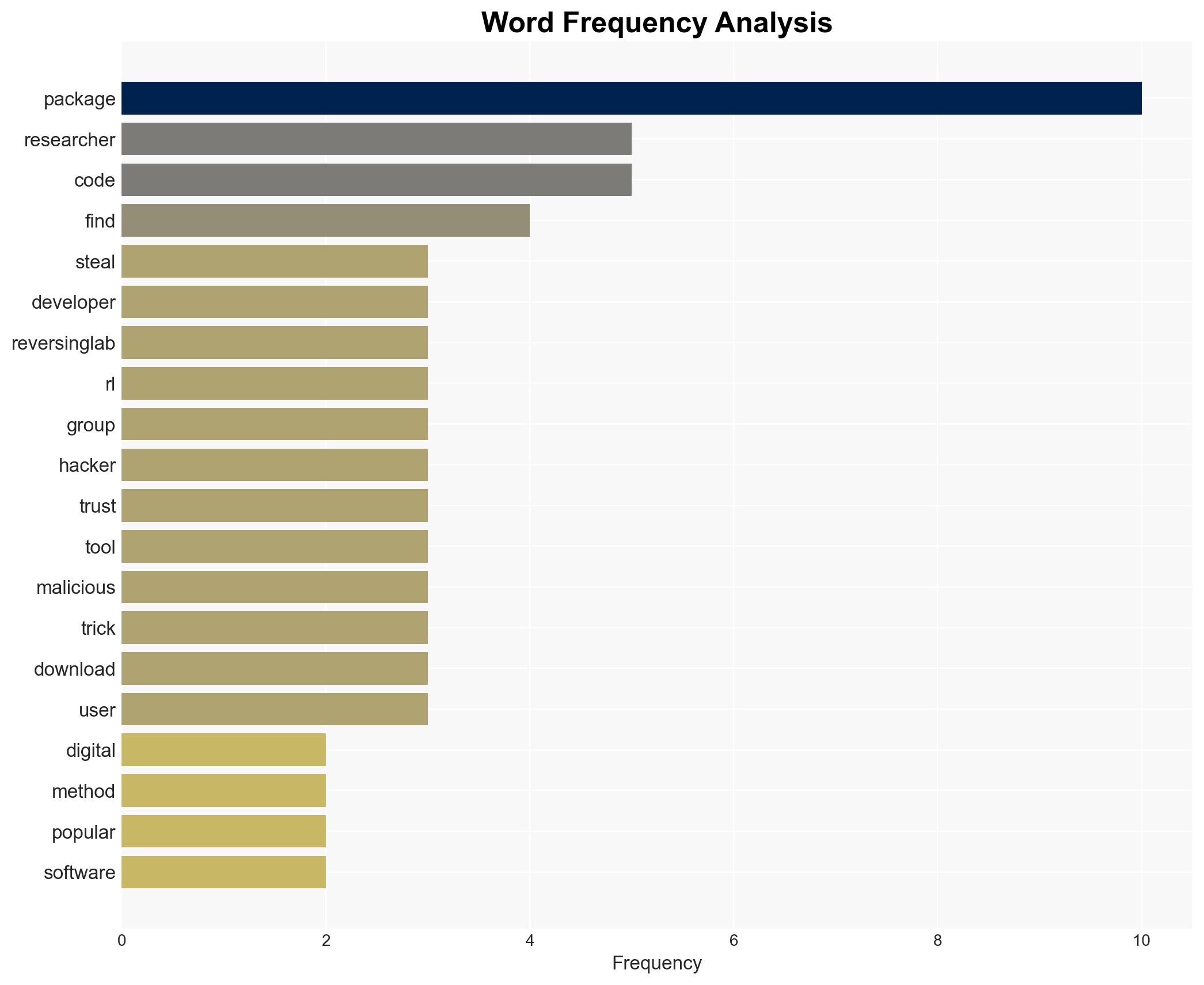
The discovery of 14 malicious packages on the NuGet platform represents a significant cybersecurity threat, primarily targeting cryptocurrency wallets and advertising data. The attack leverages sophisticated techniques such as homoglyphs and version bumping to deceive developers. This campaign has the potential to affect a wide range of users indirectly through downstream infections. Overall confidence in this assessment is moderate, given the identified patterns and methods.
2. Competing Hypotheses
- Hypothesis A: The malicious packages are part of a coordinated effort by a single group to exploit cryptocurrency and advertising platforms. This is supported by the consistent use of homoglyphs and version bumping across packages, and the repeated involvement of the author “DamienMcdougal.” However, the deletion of the SolnetAll package before full analysis introduces uncertainty.
- Hypothesis B: Multiple independent actors are using similar techniques to exploit the NuGet platform, possibly inspired by previous successful attacks. This hypothesis is less supported due to the observed patterns and the reuse of tactics by the same author.
- Assessment: Hypothesis A is currently better supported due to the consistent methods and recurring author involvement. Indicators such as new package uploads or changes in tactics could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The homoglyph and version bumping techniques are effective in deceiving developers; the author “DamienMcdougal” is a key figure in the campaign; the artificially inflated download counts are a deliberate deception tactic.
- Information Gaps: The identity and motives of “DamienMcdougal”; the full scope of affected users and downstream impacts; technical details of the deleted SolnetAll package.
- Bias & Deception Risks: Potential over-reliance on the analysis by ReversingLabs; risk of misattribution due to common cyber tactics; possibility of deliberate misinformation by the attackers.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of software repositories and heightened security measures by developers. The sophistication of the attack methods may inspire similar campaigns, potentially escalating the threat landscape.
- Political / Geopolitical: Increased tension between nations over cybersecurity responsibilities and regulatory measures.
- Security / Counter-Terrorism: Potential for similar tactics to be used in more politically motivated cyber operations.
- Cyber / Information Space: Heightened awareness and potential policy changes regarding software supply chain security.
- Economic / Social: Financial losses for individuals and companies; erosion of trust in digital platforms and tools.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor NuGet and similar platforms for new suspicious packages; enhance developer awareness and training on identifying deceptive tactics.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for early threat detection; invest in advanced threat intelligence capabilities.
- Scenario Outlook:
- Best: Effective countermeasures lead to a decline in similar attacks.
- Worst: Attackers adapt and increase the sophistication of their methods, leading to widespread financial and reputational damage.
- Most-Likely: Continued sporadic attacks with gradual improvements in detection and prevention.
6. Key Individuals and Entities
- DamienMcdougal (author of malicious packages)
- ReversingLabs (security firm that discovered the threat)
- NuGet (platform targeted by the attack)
7. Thematic Tags
cybersecurity, cryptocurrency, software supply chain, cyber deception, threat intelligence, digital trust, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us