Phishing Campaign Linked to Operation ForumTroll Targets Russian Academics with Fake eLibrary Communications
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
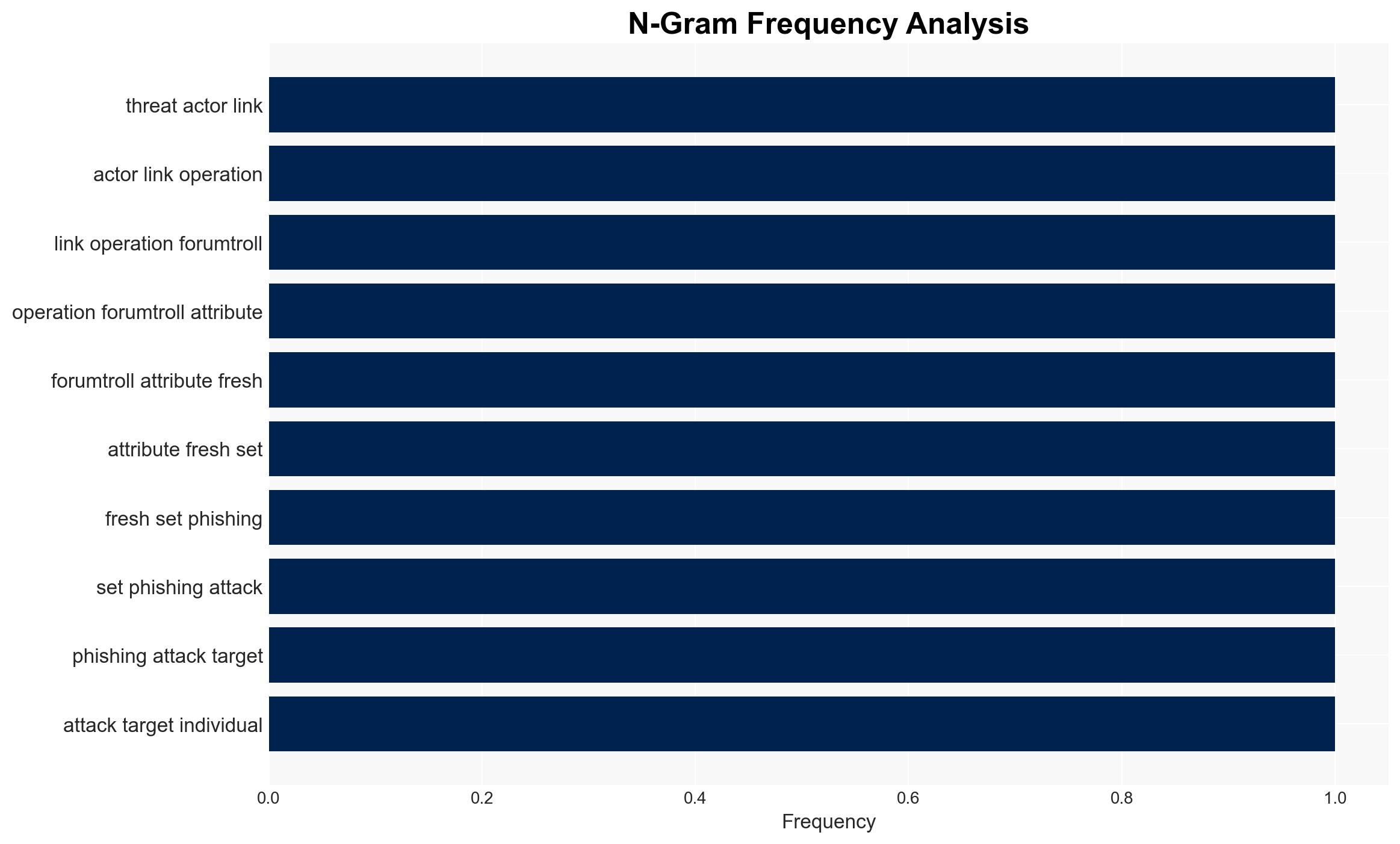
Intelligence Report: New ForumTroll Phishing Attacks Target Russian Scholars Using Fake eLibrary Emails
1. BLUF (Bottom Line Up Front)
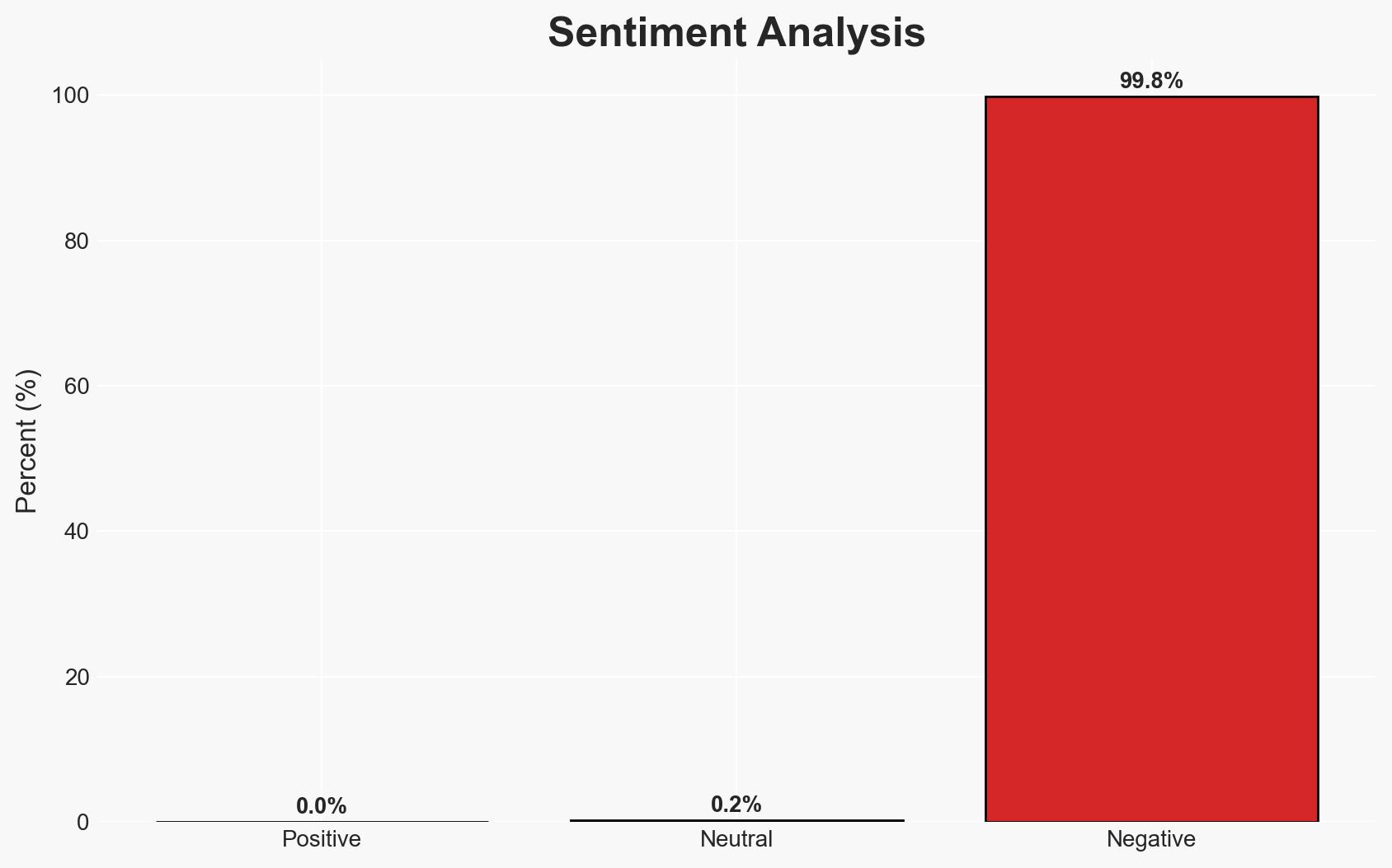
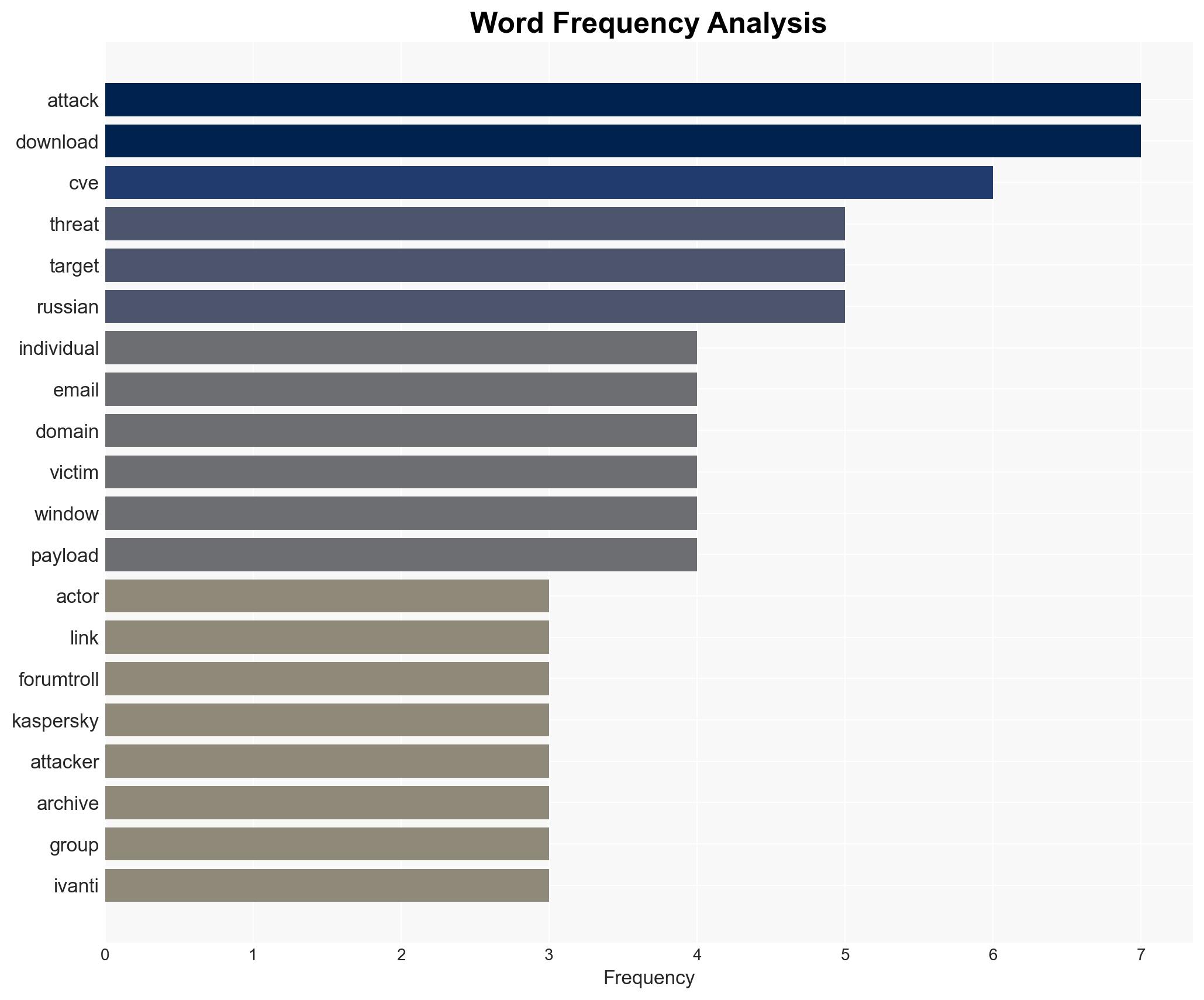
The ForumTroll phishing campaign is targeting Russian scholars with sophisticated techniques, leveraging fake eLibrary emails to deliver malware. The operation appears to be well-planned, indicating a strategic intent to compromise individuals in sensitive academic fields. The origins of the threat actor remain unknown. Overall confidence in this assessment is moderate due to the lack of information on the actor’s identity and motives.
2. Competing Hypotheses
- Hypothesis A: The ForumTroll campaign is conducted by a state-sponsored actor aiming to gather intelligence on Russian academia, particularly in fields relevant to national security and foreign policy. This is supported by the targeting of scholars in political science, international relations, and global economics. However, the lack of direct attribution to a specific nation-state actor leaves this hypothesis uncertain.
- Hypothesis B: The campaign is orchestrated by a financially motivated cybercriminal group seeking to exploit academic credentials for monetary gain or to sell access to third parties. The sophistication of the attack and the strategic domain aging could contradict this hypothesis, suggesting a higher level of resource allocation than typical for financially motivated actors.
- Assessment: Hypothesis A is currently better supported due to the targeted nature of the attacks on scholars in sensitive fields and the sophisticated methods employed. Indicators such as the use of a zero-day vulnerability and personalized phishing emails suggest a level of sophistication consistent with state-sponsored operations. Confirmation of the actor’s identity or further evidence of financial motives could shift this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The threat actor has significant resources and technical capabilities; the targeted individuals possess information of strategic value; the operation is part of a broader intelligence-gathering effort.
- Information Gaps: The identity and ultimate objectives of the threat actor; the extent of the compromise among targeted individuals; potential links to other known cyber operations.
- Bias & Deception Risks: Potential bias in attributing the attack to state-sponsored actors without concrete evidence; deception by the threat actor to mislead attribution efforts.
4. Implications and Strategic Risks
This development could lead to increased cyber espionage activities targeting academic institutions, potentially affecting international academic collaboration and research integrity.
- Political / Geopolitical: Potential escalation in cyber tensions between Russia and perceived adversaries if attribution points to a foreign state actor.
- Security / Counter-Terrorism: Increased vulnerability of academic institutions to cyber threats, necessitating enhanced security measures.
- Cyber / Information Space: Potential for further exploitation of academic networks to access sensitive research data or disrupt operations.
- Economic / Social: Possible impact on academic funding and partnerships if institutions are perceived as insecure or compromised.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of academic networks for similar phishing attempts; conduct awareness campaigns for potential targets; collaborate with cybersecurity firms for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures for academic institutions, including improved cybersecurity protocols and incident response capabilities; foster international partnerships for collaborative defense efforts.
- Scenario Outlook:
- Best: Successful attribution and neutralization of the threat actor, leading to enhanced security measures across academia.
- Worst: Widespread compromise of academic networks, resulting in significant data breaches and loss of research integrity.
- Most-Likely: Continued targeting of academic institutions with incremental improvements in cybersecurity defenses.
6. Key Individuals and Entities
- Georgy Kucherin, Security Researcher at Kaspersky
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, phishing attacks, academic security, state-sponsored threats, cyber defense, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us