ESET Cybersecurity: Essential Protection Against Ransomware and Data Theft
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Protect data from ransomware and more with ESET Cybersecurity
1. BLUF (Bottom Line Up Front)
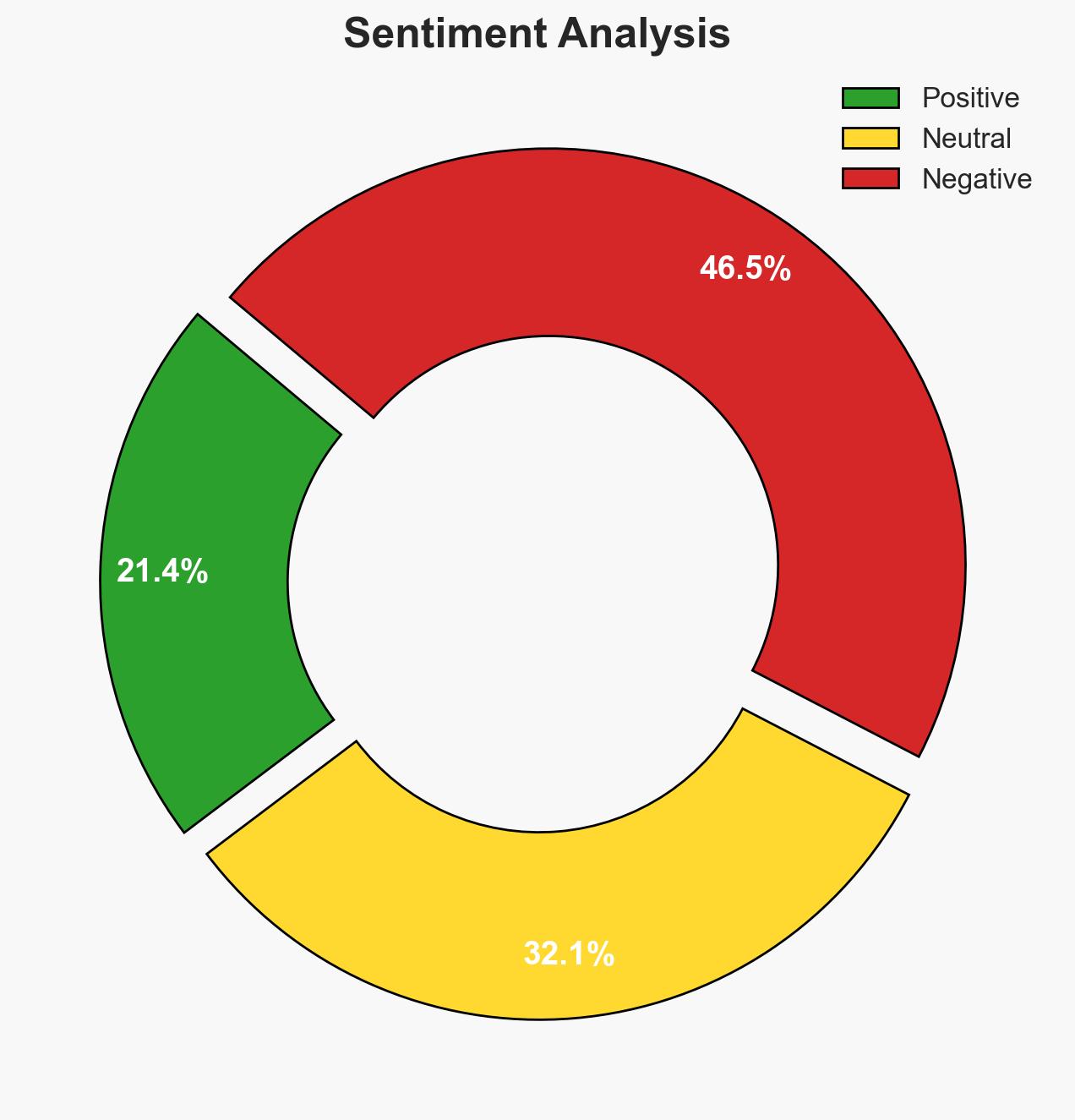
Ransomware and other cyber threats pose significant risks to data security, affecting individuals and organizations alike. ESET Cybersecurity offers a comprehensive solution with high detection rates and minimal false positives, providing effective protection against these threats. The most likely hypothesis is that ESET’s solutions can significantly reduce the risk of data breaches for individual users. Overall confidence in this assessment is moderate due to potential information gaps regarding real-world efficacy.
2. Competing Hypotheses
- Hypothesis A: ESET Cybersecurity significantly reduces the risk of ransomware and other cyber threats for individual users. This is supported by reported high detection rates and additional features like Ransomware Shield and VPN services. However, the real-world efficacy of these features in diverse threat environments remains uncertain.
- Hypothesis B: ESET Cybersecurity offers limited additional protection compared to other solutions, and users remain vulnerable to sophisticated attacks. This hypothesis is less supported given the reported advantages of ESET’s detection rates and unique features, though it highlights the potential for over-reliance on software without user education and other security measures.
- Assessment: Hypothesis A is currently better supported due to the reported technical capabilities and features of ESET Cybersecurity. Key indicators that could shift this judgment include independent evaluations of ESET’s performance in real-world scenarios and user feedback on its effectiveness.
3. Key Assumptions and Red Flags
- Assumptions: ESET’s detection rates and features perform as advertised; users will properly configure and utilize the software; cyber threats will continue to evolve but remain within the scope of ESET’s capabilities.
- Information Gaps: Lack of independent, large-scale studies on ESET’s effectiveness; user feedback on long-term use; specific threat vectors ESET may not cover.
- Bias & Deception Risks: Potential marketing bias in the source material; lack of third-party validation could indicate overstatement of capabilities.
4. Implications and Strategic Risks
The adoption of ESET Cybersecurity could influence user behavior and perceptions of data security. If effective, it may reduce the frequency and impact of ransomware attacks on individuals, but over-reliance without broader security measures could lead to complacency.
- Political / Geopolitical: Limited direct implications, though widespread adoption could reduce the impact of ransomware on critical sectors.
- Security / Counter-Terrorism: Enhanced individual security could reduce the success rate of cybercriminal operations, potentially shifting their focus to less protected targets.
- Cyber / Information Space: Increased use of ESET may drive competitors to enhance their offerings, potentially raising overall cybersecurity standards.
- Economic / Social: Reduced ransomware incidents could lower economic losses for individuals and small businesses, enhancing social trust in digital transactions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct independent assessments of ESET’s effectiveness; promote user education on comprehensive cybersecurity practices.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for enhanced threat intelligence sharing; invest in user training programs.
- Scenario Outlook: Best: ESET significantly reduces ransomware incidents; Worst: Over-reliance leads to increased vulnerability; Most-Likely: ESET provides moderate protection, necessitating complementary measures.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, data protection, ESET, cyber threats, information security, digital resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us