UK Foreign Office confirms cyber breach; investigation reveals limited details and no immediate threat to ind…
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ministers confirm breach at UK Foreign Office but details remain murky
1. BLUF (Bottom Line Up Front)
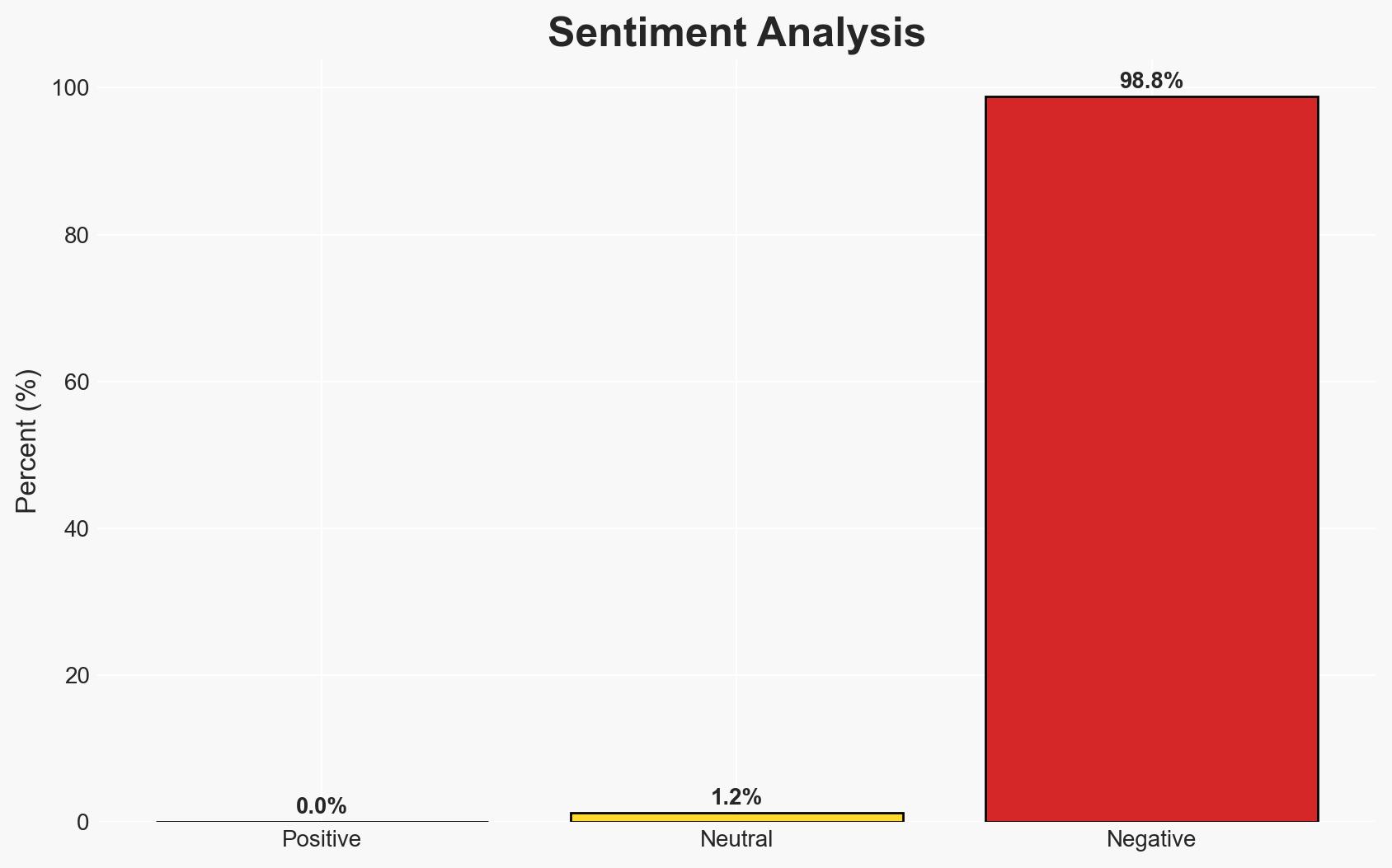
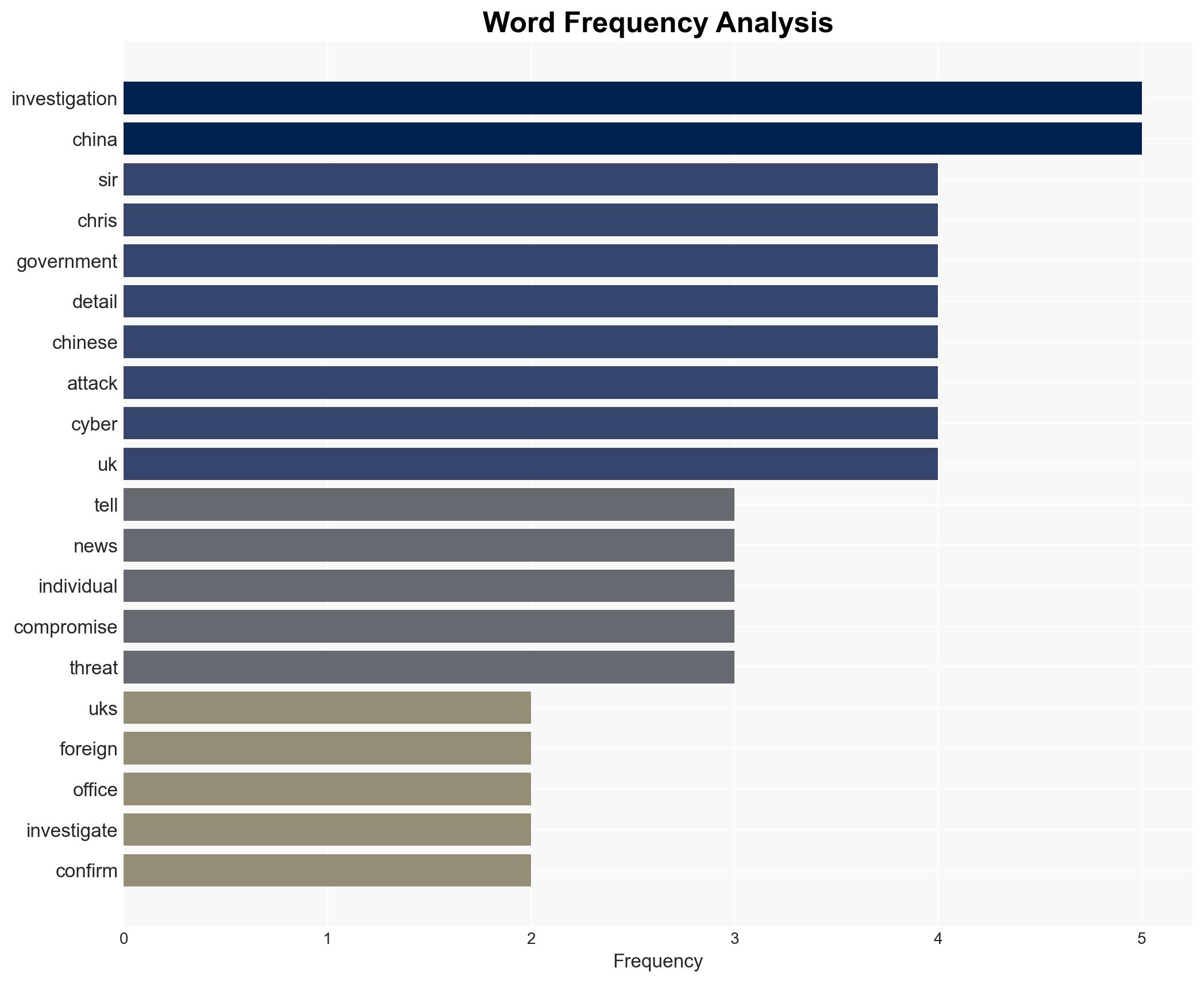
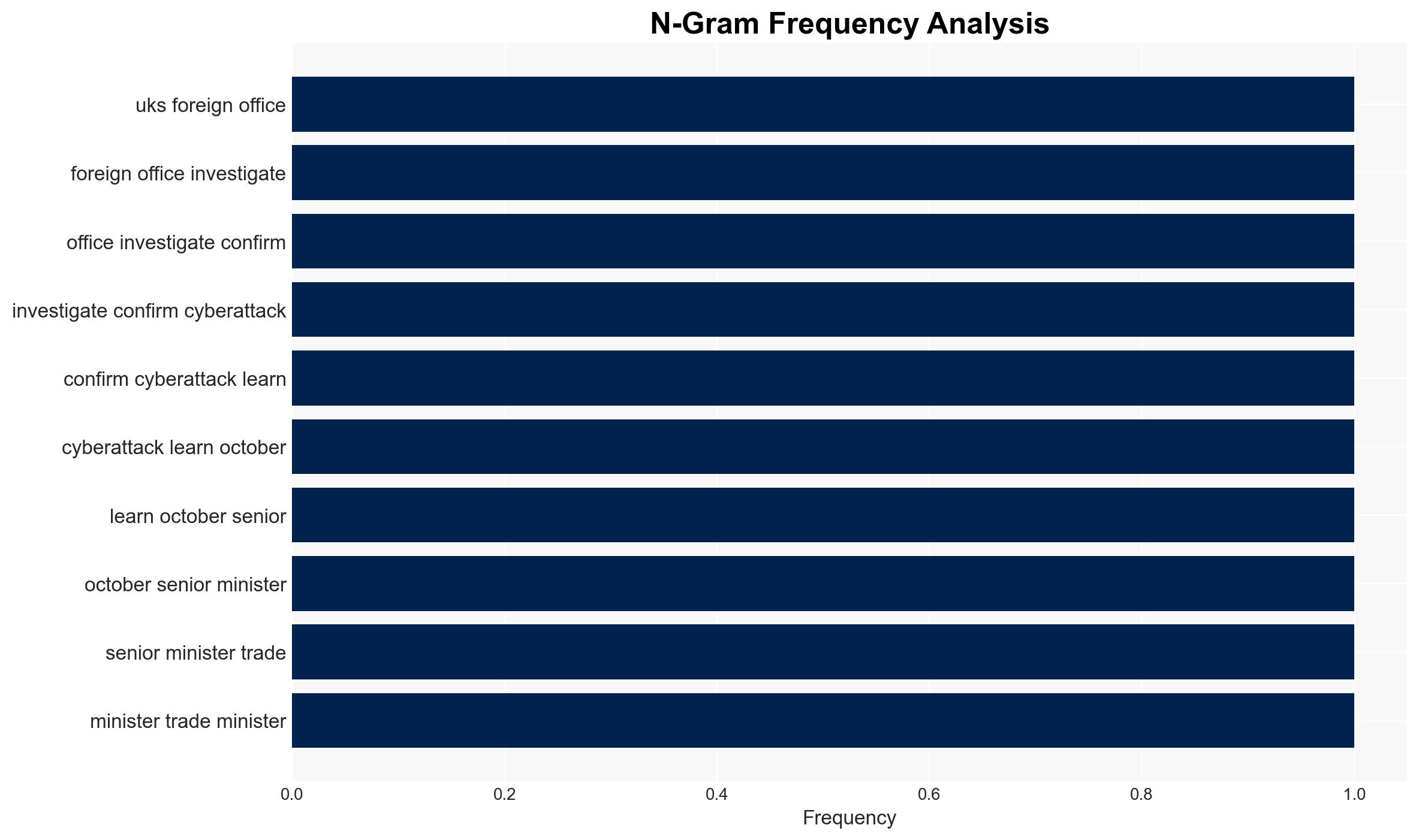
The UK Foreign Office experienced a confirmed cyberattack, with initial reports suggesting Chinese state-sponsored involvement. However, details remain speculative and under investigation. The breach potentially targeted visa application data, but no individual harm has been confirmed. Current assessment leans towards a state-sponsored espionage motive with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: The cyberattack on the UK Foreign Office was conducted by Chinese state-sponsored actors aiming to gather intelligence on visa applications. This is supported by recent reports of Chinese cyber-espionage activities targeting European entities. However, official confirmation and technical details are lacking, creating uncertainty.
- Hypothesis B: The attack was perpetrated by non-state actors or another state actor, with the Chinese attribution being speculative or a misdirection. The lack of concrete evidence linking the breach directly to China supports this alternative explanation.
- Assessment: Hypothesis A is currently better supported due to the context of ongoing Chinese cyber activities in Europe and the UK’s identification of China as a significant cyber threat. Key indicators that could shift this judgment include technical forensic evidence and official attribution from the investigation.
3. Key Assumptions and Red Flags
- Assumptions: The breach targeted sensitive data; the attackers had advanced capabilities; the UK government will disclose full findings; current public statements are accurate.
- Information Gaps: Specific technical details of the breach, confirmed attribution, and the exact data compromised.
- Bias & Deception Risks: Potential bias in media reporting; speculative attribution to China without concrete evidence; possible misinformation from involved parties.
4. Implications and Strategic Risks
The breach could exacerbate tensions between the UK and China, influencing diplomatic and cybersecurity policies. It may also prompt increased scrutiny of cyber defenses across UK government entities.
- Political / Geopolitical: Potential diplomatic strain with China; increased international focus on cyber norms and state-sponsored activities.
- Security / Counter-Terrorism: Heightened alert for further cyber intrusions; potential reevaluation of cyber defense strategies.
- Cyber / Information Space: Increased emphasis on cybersecurity measures; potential for retaliatory cyber operations.
- Economic / Social: Minimal immediate economic impact, but potential long-term effects on UK-China trade relations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of government networks; conduct thorough forensic analysis; engage with international partners for intelligence sharing.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity infrastructure; develop public-private partnerships for cyber resilience; review and update cyber defense policies.
- Scenario Outlook:
- Best: Attribution clarifies non-state actor involvement, reducing geopolitical tensions.
- Worst: Confirmed state-sponsored attack leads to significant diplomatic fallout and retaliatory measures.
- Most-Likely: Continued investigation reveals partial attribution, prompting moderate policy adjustments.
6. Key Individuals and Entities
- Sir Chris Bryant, UK Trade Minister
- Foreign, Commonwealth, and Development Office (FCDO)
- Check Point Software
- GCHQ
- Anne Keast-Butler, GCHQ Director
7. Thematic Tags
cybersecurity, cyber-espionage, UK-China relations, state-sponsored attacks, intelligence gathering, diplomatic tensions, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us