Princeton University faces lawsuits over cybersecurity breach affecting student and alumni data security
Published on: 2025-12-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Princeton faces multiple lawsuits after disclosing cybersecurity breach involving student and alumni data
1. BLUF (Bottom Line Up Front)
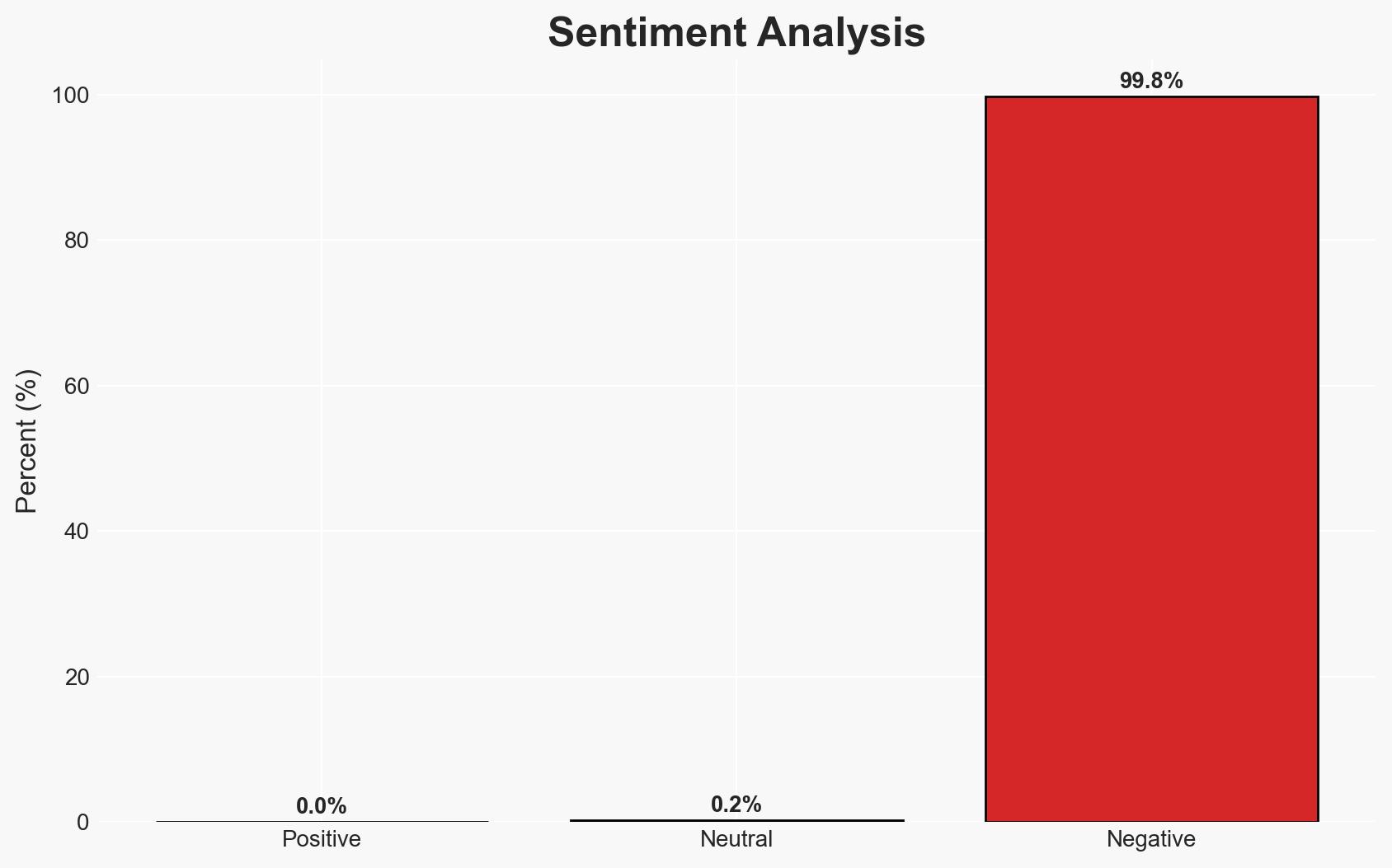
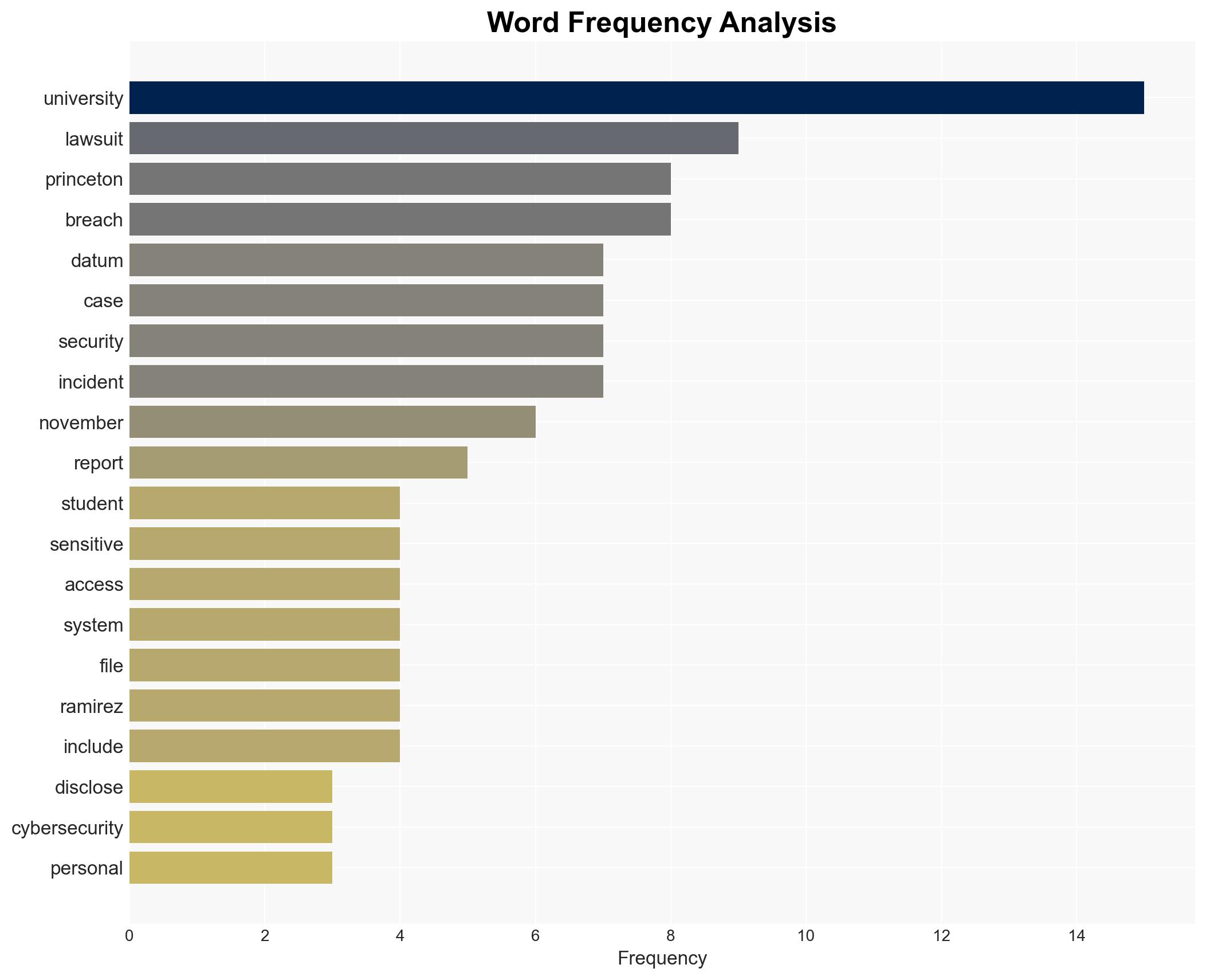
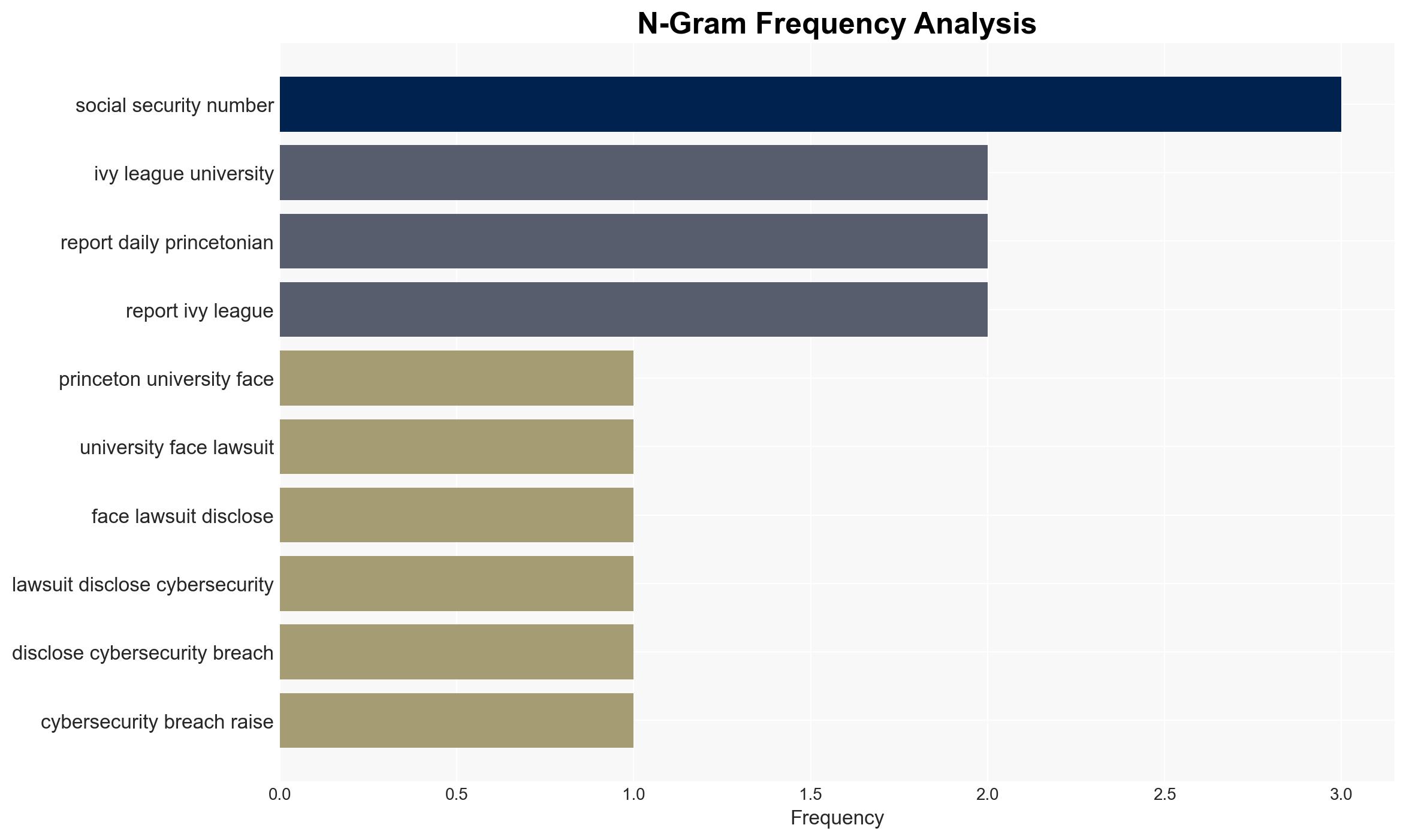
Princeton University is embroiled in a consolidated lawsuit following a cybersecurity breach that exposed sensitive data of students, faculty, alumni, and donors. The breach, part of a broader pattern affecting Ivy League institutions, has raised significant concerns about data protection in higher education. The most likely hypothesis is that the breach resulted from inadequate security measures, with moderate confidence due to limited available evidence.
2. Competing Hypotheses
- Hypothesis A: The breach was due to inadequate security measures at Princeton University. Supporting evidence includes the lawsuit’s claims of negligence and the lack of evidence of highly sensitive data exposure. However, the specific security failures remain unidentified, creating uncertainty.
- Hypothesis B: The breach was part of a coordinated cyberattack targeting multiple Ivy League universities. This is supported by similar incidents reported across other institutions, but Princeton’s statement that the breach is unrelated to others contradicts this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the lawsuit’s focus on Princeton’s security practices and the University’s own admissions. Future revelations about the breach’s technical details or connections to other incidents could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Princeton’s cybersecurity measures were insufficient; the breach was isolated to the University Advancement database; no highly sensitive data was exposed.
- Information Gaps: Specific vulnerabilities exploited in the breach; full scope of data accessed; potential connections to other cyber incidents.
- Bias & Deception Risks: Potential bias in University statements minimizing the breach’s impact; legal motivations may influence plaintiffs’ claims.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of data protection practices in higher education, influencing regulatory and policy environments. It may also prompt similar legal actions against other institutions.
- Political / Geopolitical: Potential for regulatory changes impacting higher education data protection standards.
- Security / Counter-Terrorism: Increased focus on cybersecurity measures within educational institutions to prevent future breaches.
- Cyber / Information Space: Heightened awareness and potential for further cyberattacks targeting perceived vulnerabilities in academia.
- Economic / Social: Financial implications for Princeton due to legal costs and potential settlements; reputational damage affecting stakeholder trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Princeton’s cybersecurity posture; engage with stakeholders to assess data protection measures; prepare for potential regulatory inquiries.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for enhanced protection; invest in staff training and awareness programs; review and update data protection policies.
- Scenario Outlook:
- Best: Princeton resolves the lawsuit with minimal financial and reputational damage, leading to improved security measures.
- Worst: Further breaches occur, leading to severe financial penalties and regulatory action.
- Most-Likely: The lawsuit proceeds with moderate impact, prompting incremental improvements in cybersecurity practices.
6. Key Individuals and Entities
- David Ramirez (Plaintiff)
- Henggao Cai (Plaintiff)
- Gary Penna (Plaintiff)
- Jennifer Morrill (Princeton Spokesperson)
- Judge Robert Kirsch (Presiding Judge)
7. Thematic Tags
cybersecurity, data protection, higher education, legal action, Ivy League, information security, breach response
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us