Data Breach Exposes Millions of PornHub Users to Extortion Threats
Published on: 2025-12-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers Stole Millions of PornHub Users Data for Extortion
1. BLUF (Bottom Line Up Front)
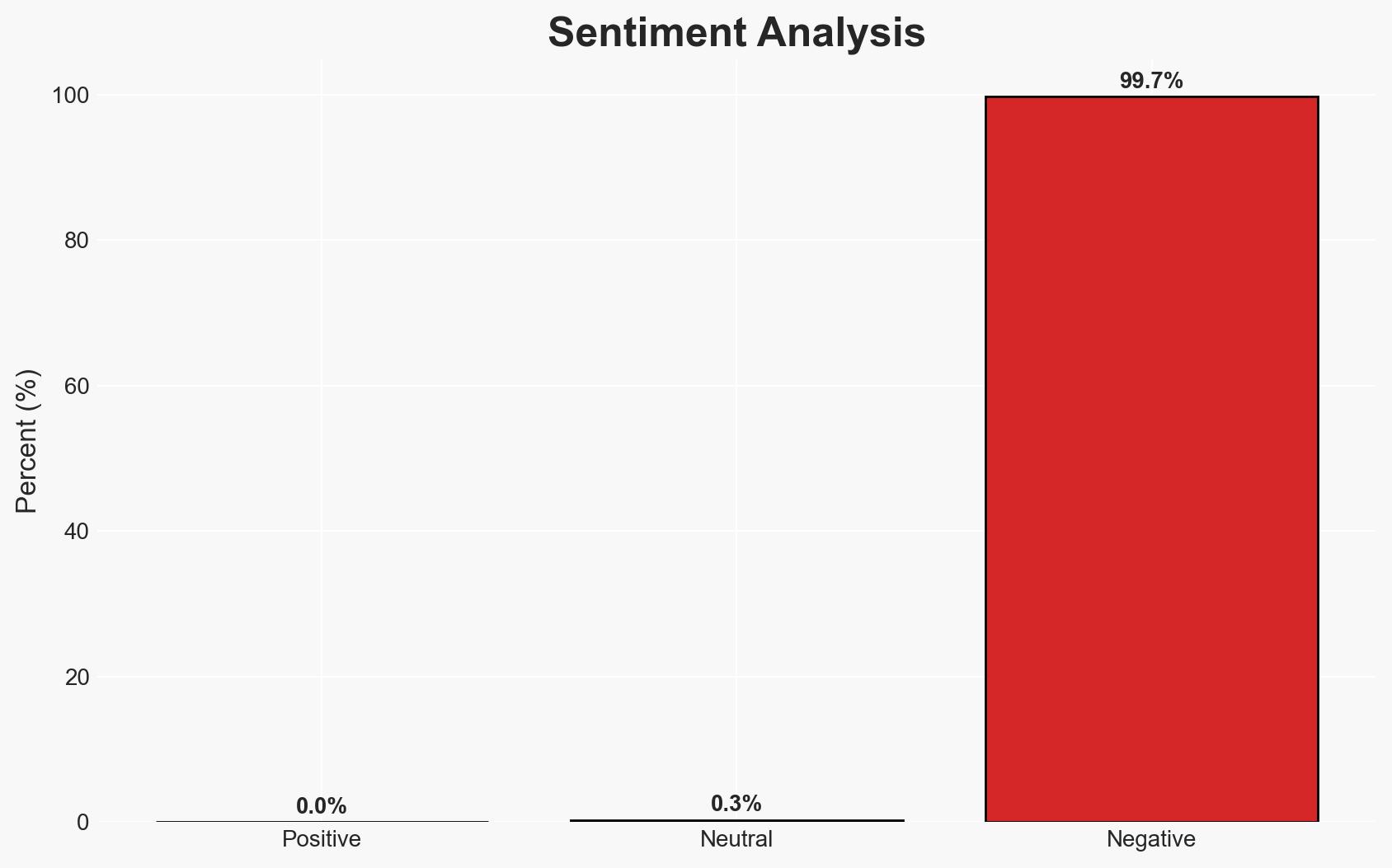
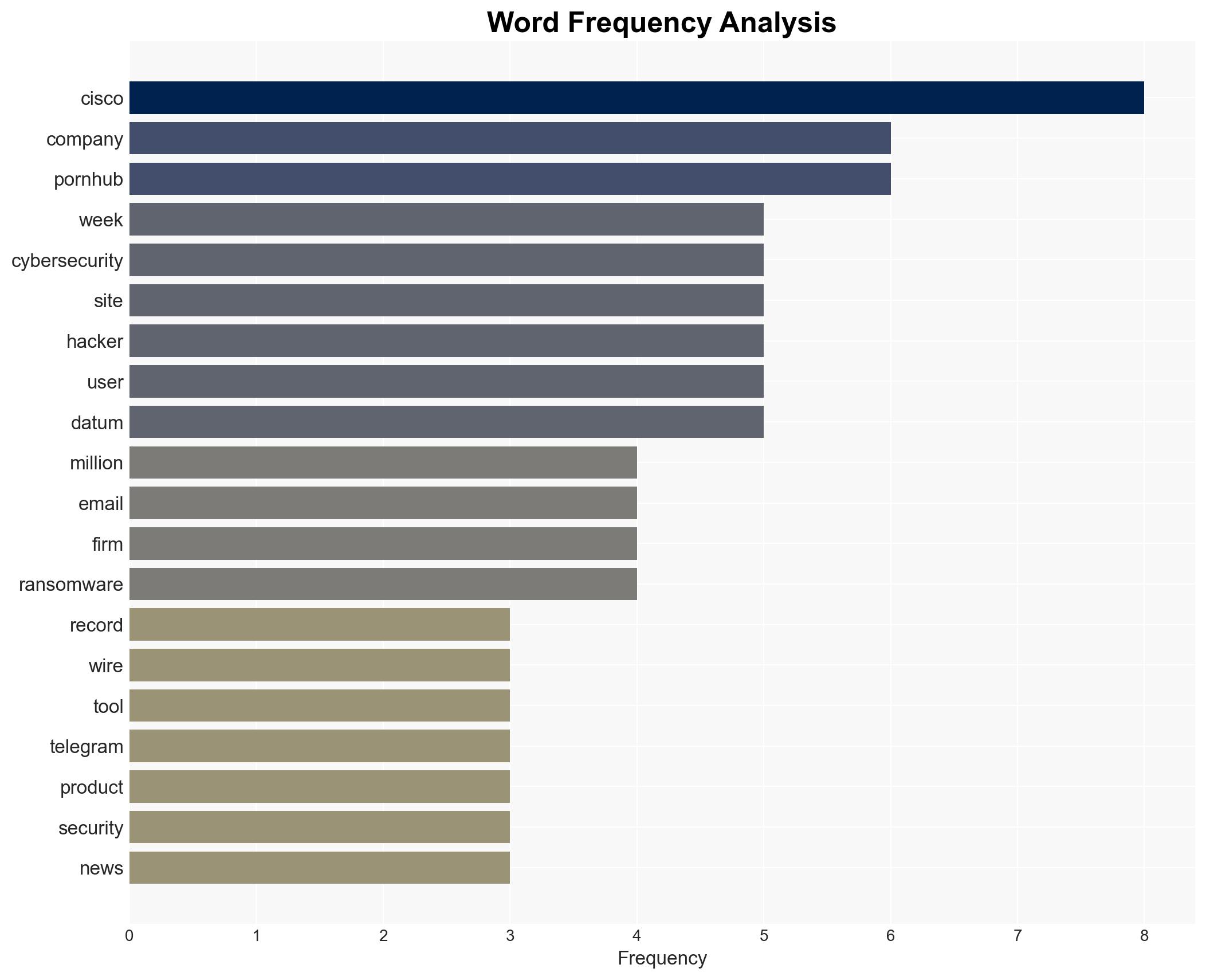
The ShinyHunters hacker group has reportedly stolen over 200 million user records from PornHub, leveraging this data for extortion. This breach poses significant privacy risks to users and potential reputational damage to PornHub. The most likely hypothesis is that the breach was facilitated through a third-party analytics firm, MixPanel. Overall confidence in this assessment is moderate due to limited direct evidence of the breach’s specifics.
2. Competing Hypotheses
- Hypothesis A: The breach was executed through vulnerabilities in MixPanel’s systems, which PornHub used until 2021. This is supported by the age of the data and the hackers’ focus on extortion, but lacks direct evidence of the vulnerability exploitation.
- Hypothesis B: The breach was a result of a direct compromise of PornHub’s current systems. This is less supported due to the age of the data and the lack of current system vulnerabilities being reported.
- Assessment: Hypothesis A is currently better supported due to the age of the data aligning with MixPanel’s usage period. Confirmation of MixPanel’s security posture during the relevant period could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The data is genuine and sourced from the stated period; ShinyHunters are acting independently without state sponsorship; MixPanel’s security was compromised during the relevant period.
- Information Gaps: Specific vulnerabilities exploited; confirmation of the exact timeline and method of data breach; current security measures in place at PornHub and MixPanel.
- Bias & Deception Risks: Potential bias in reporting due to reliance on hacker claims; risk of deception by hackers overstating the breach’s impact to increase extortion leverage.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on data protection practices in the adult entertainment industry and broader implications for third-party data management.
- Political / Geopolitical: Potential diplomatic tensions if state actors are suspected of involvement.
- Security / Counter-Terrorism: Increased risk of personal data being used for blackmail or identity theft.
- Cyber / Information Space: Highlights vulnerabilities in third-party data analytics services and potential for increased cyber extortion activities.
- Economic / Social: Possible financial losses for PornHub due to reputational damage and user trust erosion.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of PornHub and MixPanel; engage with cybersecurity firms to monitor for further extortion attempts.
- Medium-Term Posture (1–12 months): Develop resilience measures including enhanced data protection protocols and user privacy safeguards; establish partnerships with cybersecurity entities for ongoing threat intelligence sharing.
- Scenario Outlook:
- Best: Breach impact is contained with minimal user data exposure.
- Worst: Data is widely disseminated, causing significant privacy violations and financial losses.
- Most-Likely: Limited data exposure leads to moderate reputational damage and increased regulatory scrutiny.
6. Key Individuals and Entities
- ShinyHunters (hacker group)
- PornHub (affected entity)
- MixPanel (third-party data analytics firm)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, extortion, privacy, third-party risk, hacker groups
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us