US Launches Operation Hawkeye Strike, Deploying A-10s in Retaliation Against ISIS in Syria
Published on: 2025-12-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: A-10s Spearhead US Retaliation Strikes Against ISIS Targets in Syria
1. BLUF (Bottom Line Up Front)
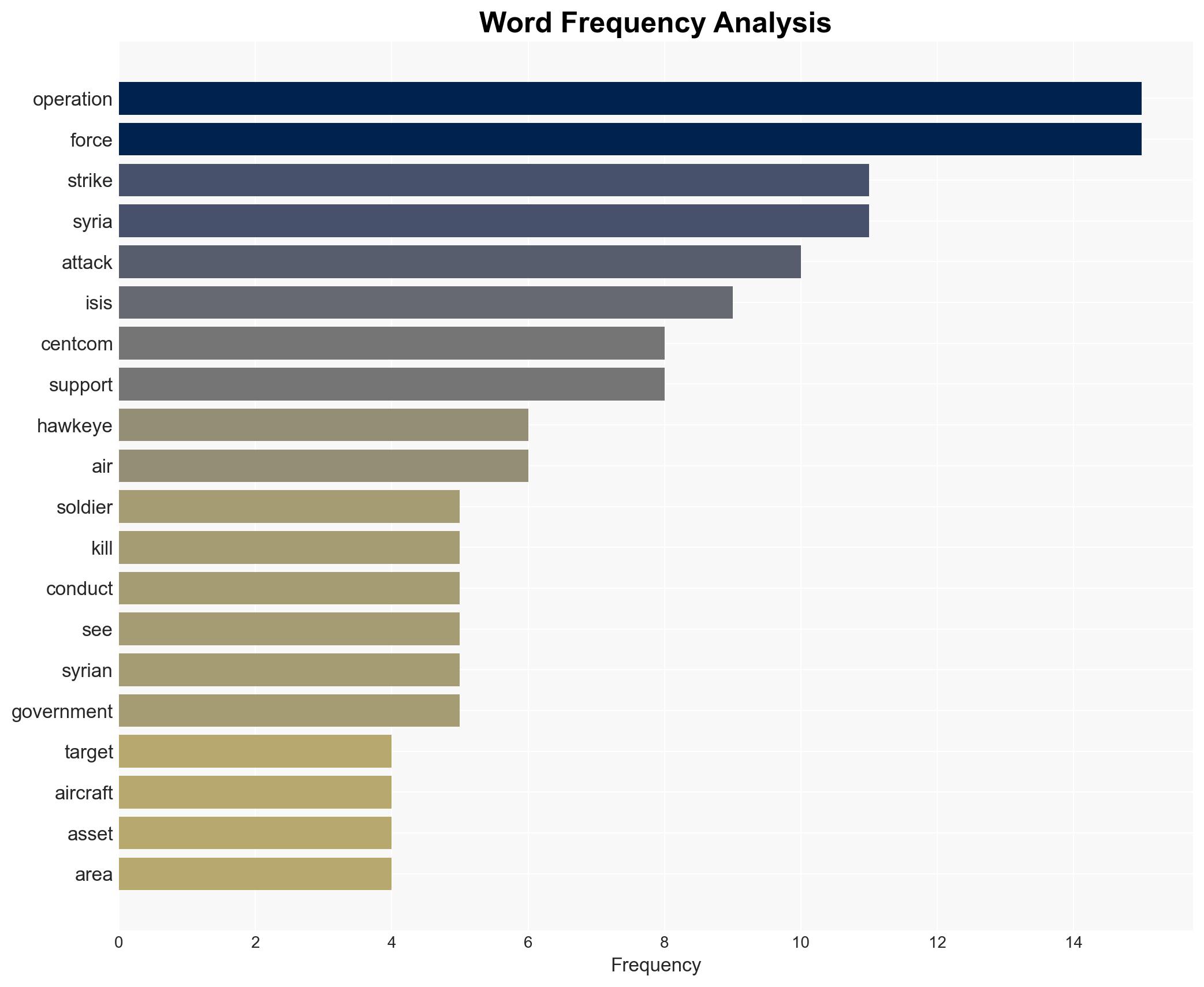
The U.S. military has conducted a large-scale retaliatory strike against ISIS targets in Syria following the death of two U.S. soldiers and an interpreter. This operation, spearheaded by A-10 aircraft, signifies a robust military response and aims to deter future ISIS activities. The most likely hypothesis is that this action will temporarily disrupt ISIS operations but may not significantly degrade their long-term capabilities. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The U.S. retaliation will significantly degrade ISIS’s operational capabilities in Syria. Supporting evidence includes the scale of the strike and the use of precision munitions. However, the resilience and adaptability of ISIS, along with potential underestimation of their resources, contradict this hypothesis.
- Hypothesis B: The strikes will temporarily disrupt ISIS activities but will not lead to a long-term degradation of their capabilities. This is supported by historical resilience of ISIS and the limited scope of a single operation. Contradicting evidence could include any significant intelligence indicating a critical blow to ISIS infrastructure.
- Assessment: Hypothesis B is currently better supported due to the historical resilience of ISIS and the limited impact of isolated military operations. Key indicators that could shift this judgment include credible intelligence of significant ISIS leadership losses or infrastructure destruction.
3. Key Assumptions and Red Flags
- Assumptions: The operation was accurately reported; ISIS retains significant operational capabilities; U.S. military objectives were primarily tactical.
- Information Gaps: Detailed intelligence on the current strength and disposition of ISIS forces in Syria; potential regional reactions to the U.S. strikes.
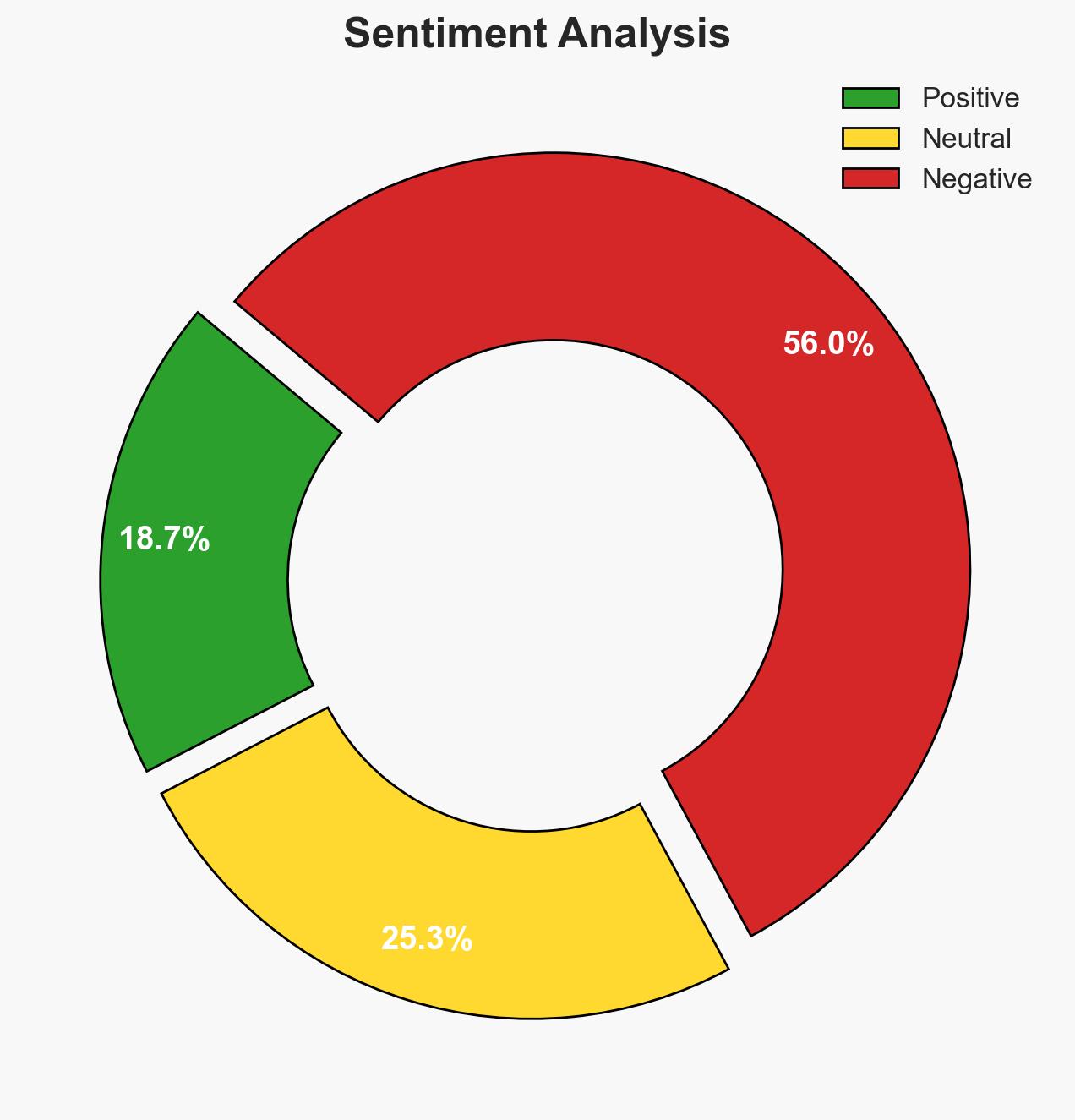
- Bias & Deception Risks: Potential bias in U.S. military reporting; ISIS propaganda may overstate their resilience or understate losses.
4. Implications and Strategic Risks
This development could lead to a temporary reduction in ISIS activities but may also provoke retaliatory actions or inspire further recruitment. The operation’s impact on regional stability and U.S. relations with local allies remains uncertain.
- Political / Geopolitical: Potential strain on U.S.-Syria relations; increased tensions with regional actors sympathetic to ISIS.
- Security / Counter-Terrorism: Short-term disruption of ISIS operations; potential for retaliatory attacks against U.S. interests.
- Cyber / Information Space: Possible increase in ISIS propaganda efforts; risk of cyber retaliation targeting U.S. infrastructure.
- Economic / Social: Limited immediate economic impact; potential for increased refugee flows if conflict escalates.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence collection on ISIS movements; increase security measures for U.S. personnel in the region.
- Medium-Term Posture (1–12 months): Strengthen partnerships with regional allies; develop contingency plans for potential ISIS resurgence.
- Scenario Outlook:
- Best: ISIS significantly weakened, leading to reduced threat levels.
- Worst: ISIS retaliates, escalating regional conflict.
- Most-Likely: Temporary disruption with eventual ISIS adaptation and continuation of operations.
6. Key Individuals and Entities
- U.S. President Donald Trump
- Secretary of Defense Pete Hegseth
- Adm. Brad Cooper, commander of CENTCOM
- ISIS (Islamic State of Iraq and Syria)
- Iowa Army National Guard
- Jordanian Air Force
7. Thematic Tags
Counter-Terrorism, military operations, ISIS, U.S. military strategy, Middle East security, airstrikes, geopolitical tensions
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us