Smuggled North Korean smartphone reveals extensive state surveillance and control over citizens’ digital lives
Published on: 2025-12-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Smuggled North Korean phone exposes disturbing details of how Kim Jong Uns regime spies on citizens
1. BLUF (Bottom Line Up Front)
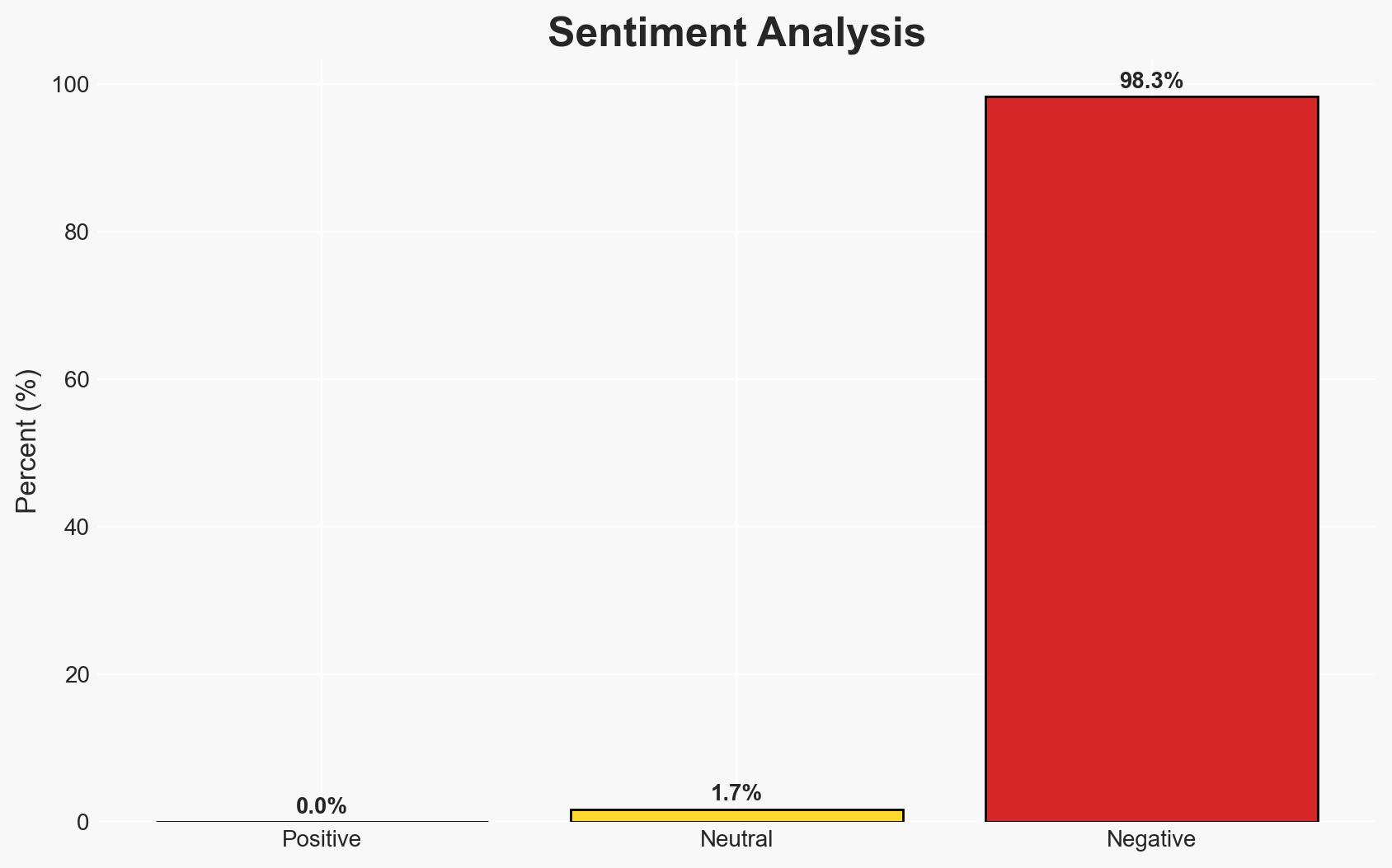
The smuggled North Korean smartphone reveals extensive state surveillance and ideological control embedded in consumer technology, highlighting the regime’s efforts to control information and behavior. This development affects North Korean citizens and has implications for regional stability. Overall, there is moderate confidence in the assessment due to the limited scope of the evidence and potential biases in source reporting.
2. Competing Hypotheses
- Hypothesis A: The North Korean regime uses consumer technology to enforce ideological conformity and monitor citizens. This is supported by the evidence of language modification and surveillance features on the smuggled phone. However, the extent of these practices across all devices remains uncertain.
- Hypothesis B: The phone’s features are exaggerated or selectively highlighted by defectors and external analysts to emphasize North Korean oppression. Contradicting evidence is limited, but potential bias in source selection and reporting could skew perceptions.
- Assessment: Hypothesis A is currently better supported due to the direct evidence from the phone’s features. Key indicators that could shift this judgment include broader corroboration from additional devices or insider testimonies.
3. Key Assumptions and Red Flags
- Assumptions: The phone is representative of typical North Korean consumer technology; the regime prioritizes ideological control over technological advancement; external analysts accurately interpret device features.
- Information Gaps: The prevalence of such devices across North Korea, the regime’s technical capabilities for mass data analysis, and the potential for international collaboration in technology development.
- Bias & Deception Risks: Potential cognitive bias in interpreting evidence through a Western lens; source bias from defectors with anti-regime agendas; possible manipulation by North Korean authorities to mislead external observers.
4. Implications and Strategic Risks
This development could exacerbate regional tensions and influence international perceptions of North Korea. It may also impact internal stability if citizens increasingly resist state control.
- Political / Geopolitical: Increased scrutiny and potential diplomatic pressure on North Korea; possible escalation in information warfare between North and South Korea.
- Security / Counter-Terrorism: Heightened risk of internal dissent and potential for crackdowns on perceived subversion.
- Cyber / Information Space: Reinforcement of North Korea’s closed information ecosystem; potential for cyber operations targeting defectors or foreign analysts.
- Economic / Social: Continued isolation could hinder economic development; social cohesion may be strained by growing awareness of external realities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of North Korean technology exports; engage with defectors for additional insights; prepare briefings for policymakers on potential regional impacts.
- Medium-Term Posture (1–12 months): Develop partnerships with regional allies to counter North Korean information operations; invest in capabilities to detect and analyze similar technologies.
- Scenario Outlook:
- Best: Increased international pressure leads to limited reforms in North Korea.
- Worst: Escalation of regional tensions and internal crackdowns.
- Most-Likely: Continued status quo with incremental technological advancements in surveillance.
6. Key Individuals and Entities
- Kim Jong Un, North Korean regime
- Jean Mackenzie, BBC Seoul correspondent
- Martyn Williams, North Korean technology expert
- Not clearly identifiable from open sources in this snippet
7. Thematic Tags
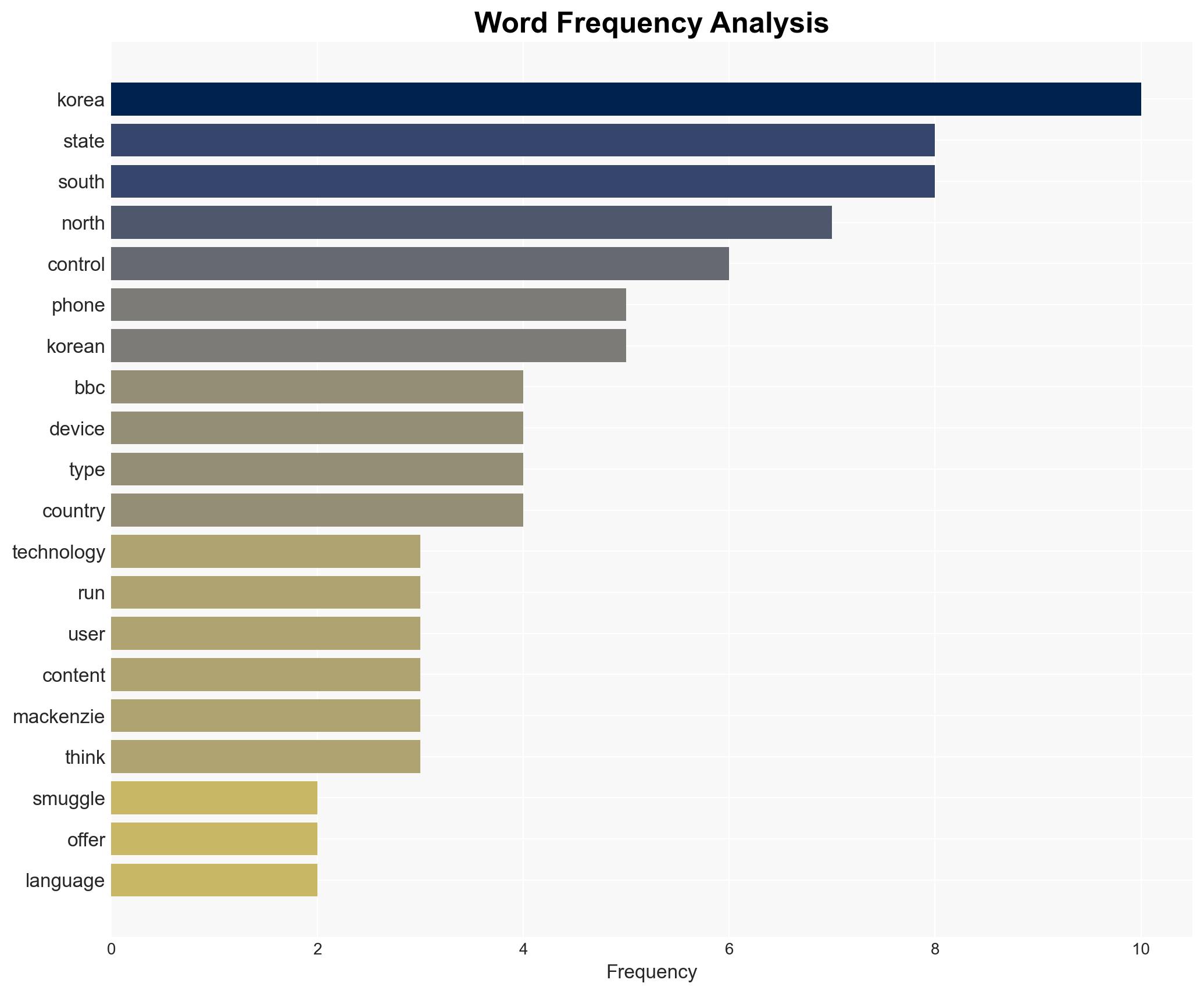
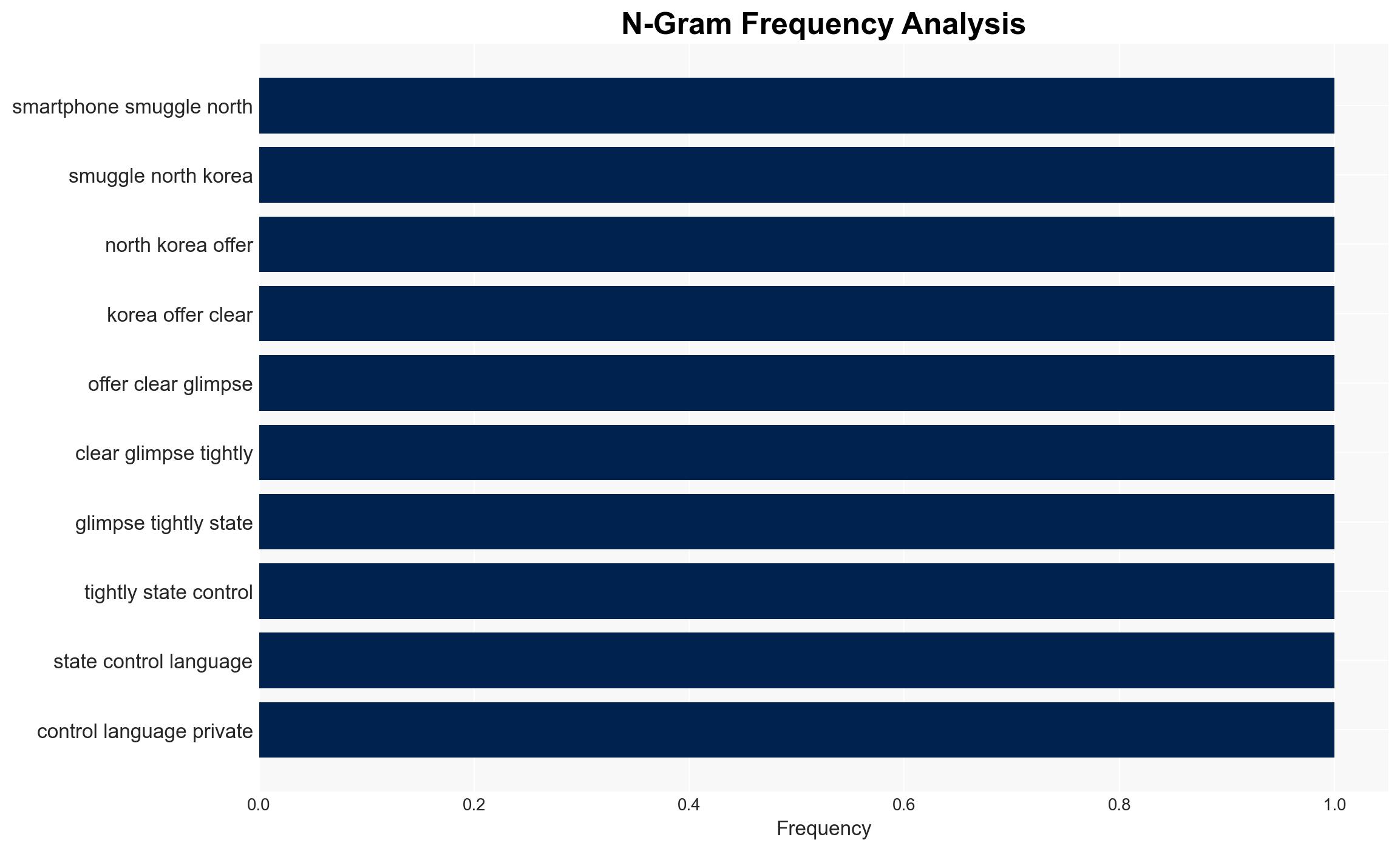
national security threats, surveillance, North Korea, information control, cyber security, ideological enforcement, regional stability
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us