Over 115,000 WatchGuard Firebox devices at risk from critical RCE vulnerability under active exploitation
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Critical RCE flaw impacts over 115000 WatchGuard firewalls
1. BLUF (Bottom Line Up Front)
The critical remote code execution (RCE) vulnerability CVE-2025-14733 affects over 115,000 WatchGuard Firebox firewalls, posing a significant cybersecurity risk, particularly to U.S. federal agencies. The vulnerability is actively exploited, with a moderate confidence level that immediate patching and mitigation efforts are essential to prevent potential breaches.
2. Competing Hypotheses
- Hypothesis A: The vulnerability is primarily being exploited by opportunistic cybercriminals targeting exposed devices for financial gain. This is supported by the widespread nature of the vulnerability and the low complexity required for exploitation. However, specific attribution to criminal groups is uncertain.
- Hypothesis B: Nation-state actors are exploiting the vulnerability to gain strategic access to sensitive networks, particularly within U.S. federal agencies. The inclusion of the vulnerability in CISA’s Known Exploited Vulnerabilities Catalog and the directive for immediate patching suggest a high-risk perception by national security entities.
- Assessment: Hypothesis B is currently better supported due to the rapid response by CISA and the potential strategic value of the compromised devices. Indicators that could shift this judgment include evidence of financial motives in attacks or attribution to specific nation-state actors.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is actively exploited in the wild; patching is effective in mitigating the risk; the majority of affected devices are within critical infrastructure.
- Information Gaps: Specific attribution of the attackers; detailed impact assessments on compromised networks; the effectiveness of mitigation measures over time.
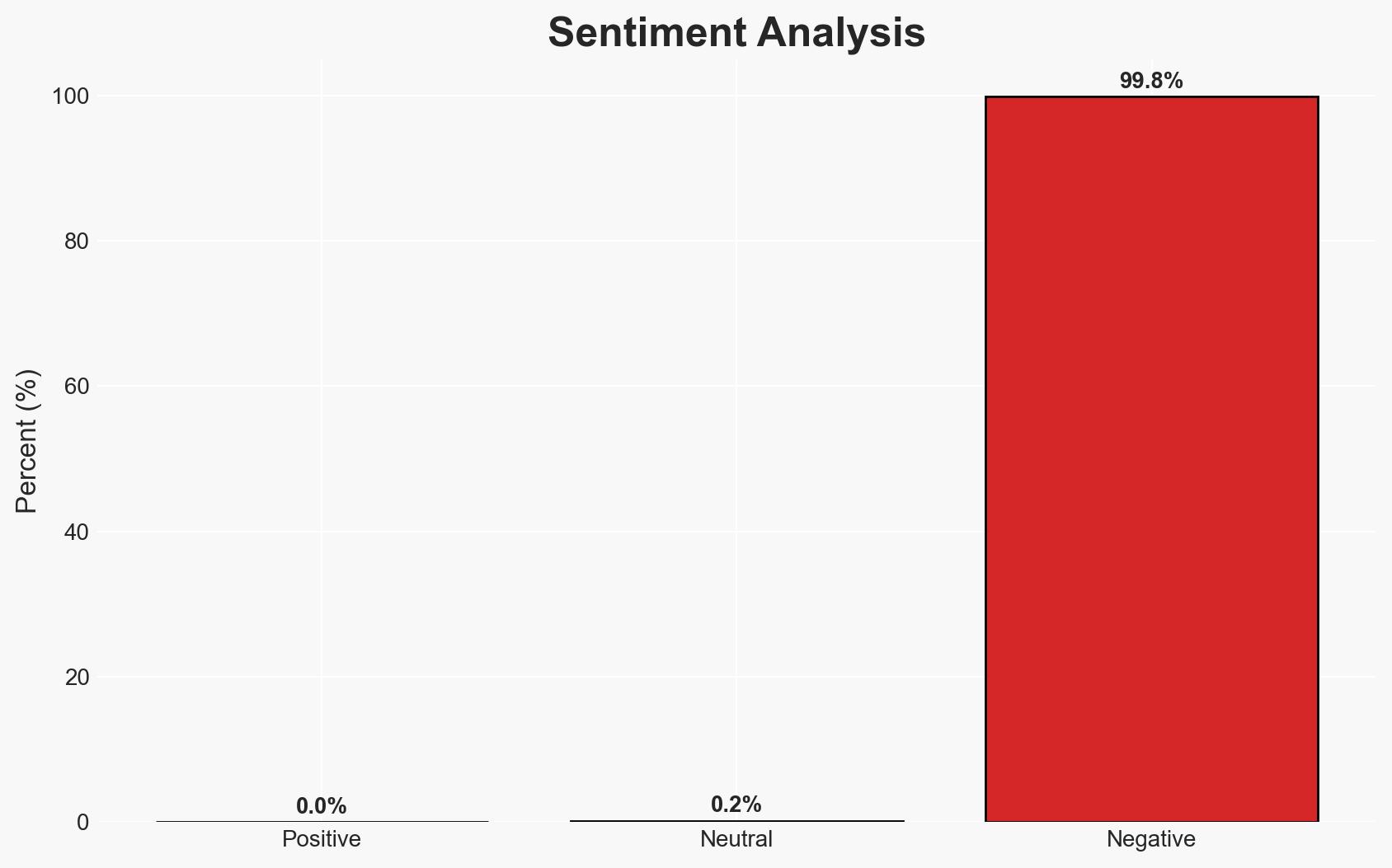
- Bias & Deception Risks: Potential bias in threat perception due to recent high-profile cyber incidents; reliance on vendor and agency reports without independent verification.
4. Implications and Strategic Risks
This vulnerability could lead to significant disruptions if exploited at scale, particularly within critical infrastructure and federal networks. The situation may evolve with increased geopolitical tensions or if new vulnerabilities are discovered.
- Political / Geopolitical: Potential escalation in cyber tensions between nation-states, particularly if attributed to a state actor.
- Security / Counter-Terrorism: Increased risk of cyber intrusions into sensitive networks, potentially affecting national security operations.
- Cyber / Information Space: Heightened alertness in the cybersecurity community and potential for increased cyber defense collaboration.
- Economic / Social: Potential economic impact from disrupted services and increased costs for cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch vulnerable devices; monitor for indicators of compromise; enhance network monitoring and incident response capabilities.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing; invest in cybersecurity training and awareness; review and update security policies and procedures.
- Scenario Outlook:
- Best: Rapid patching mitigates the threat with minimal impact.
- Worst: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Mixed outcomes with some successful mitigations and isolated incidents of exploitation.
6. Key Individuals and Entities
- WatchGuard Technologies
- Cybersecurity and Infrastructure Security Agency (CISA)
- Shadowserver Foundation
- Federal Civilian Executive Branch (FCEB) agencies
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, remote code execution, federal agencies, vulnerability management, nation-state actors, critical infrastructure, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us