Ontinue alerts on Nezha tool misuse as a covert remote access trojan for persistent system infiltration
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ontinue warns attackers are abusing Nezha monitoring tool as stealthy remote access trojan
1. BLUF (Bottom Line Up Front)
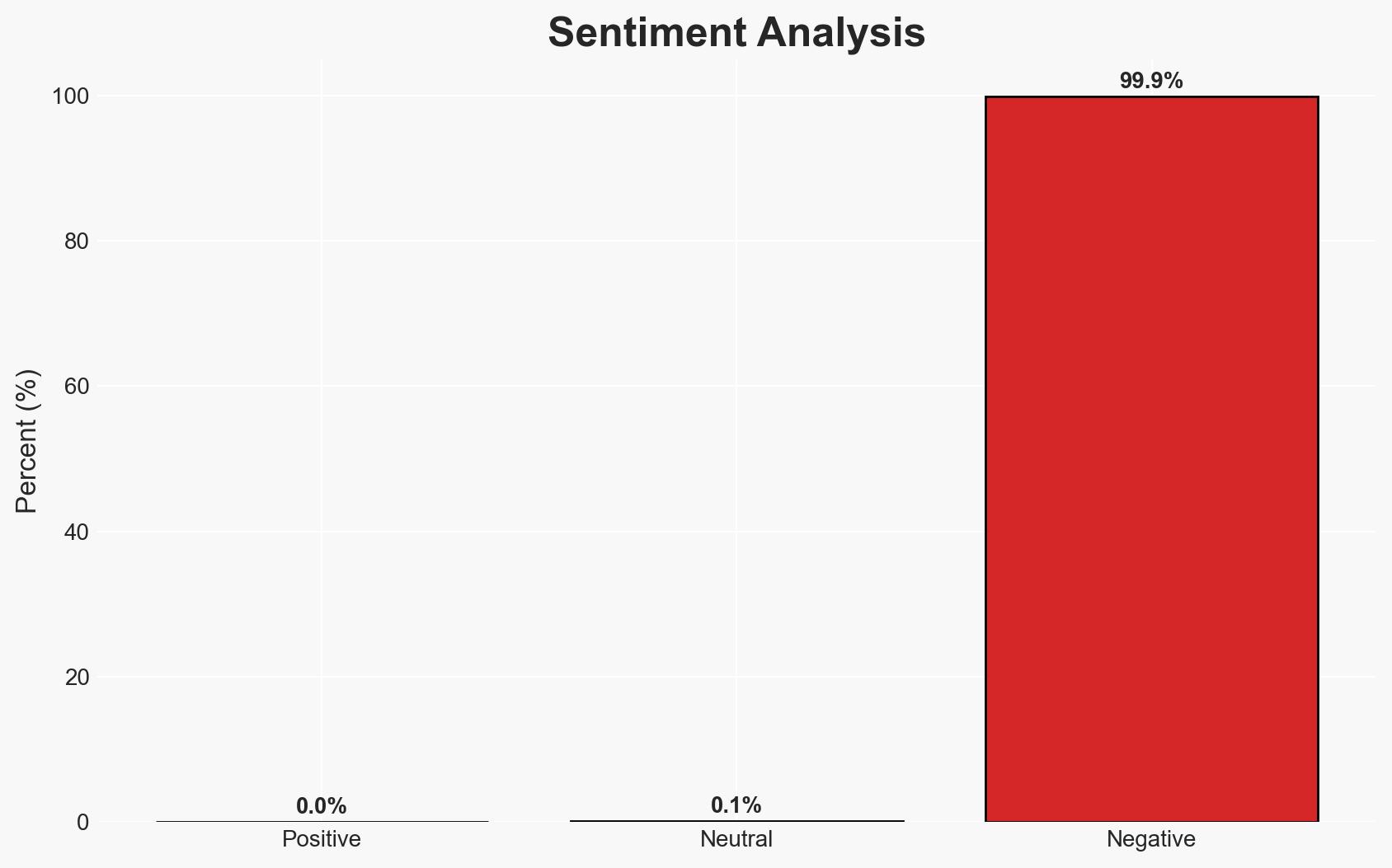
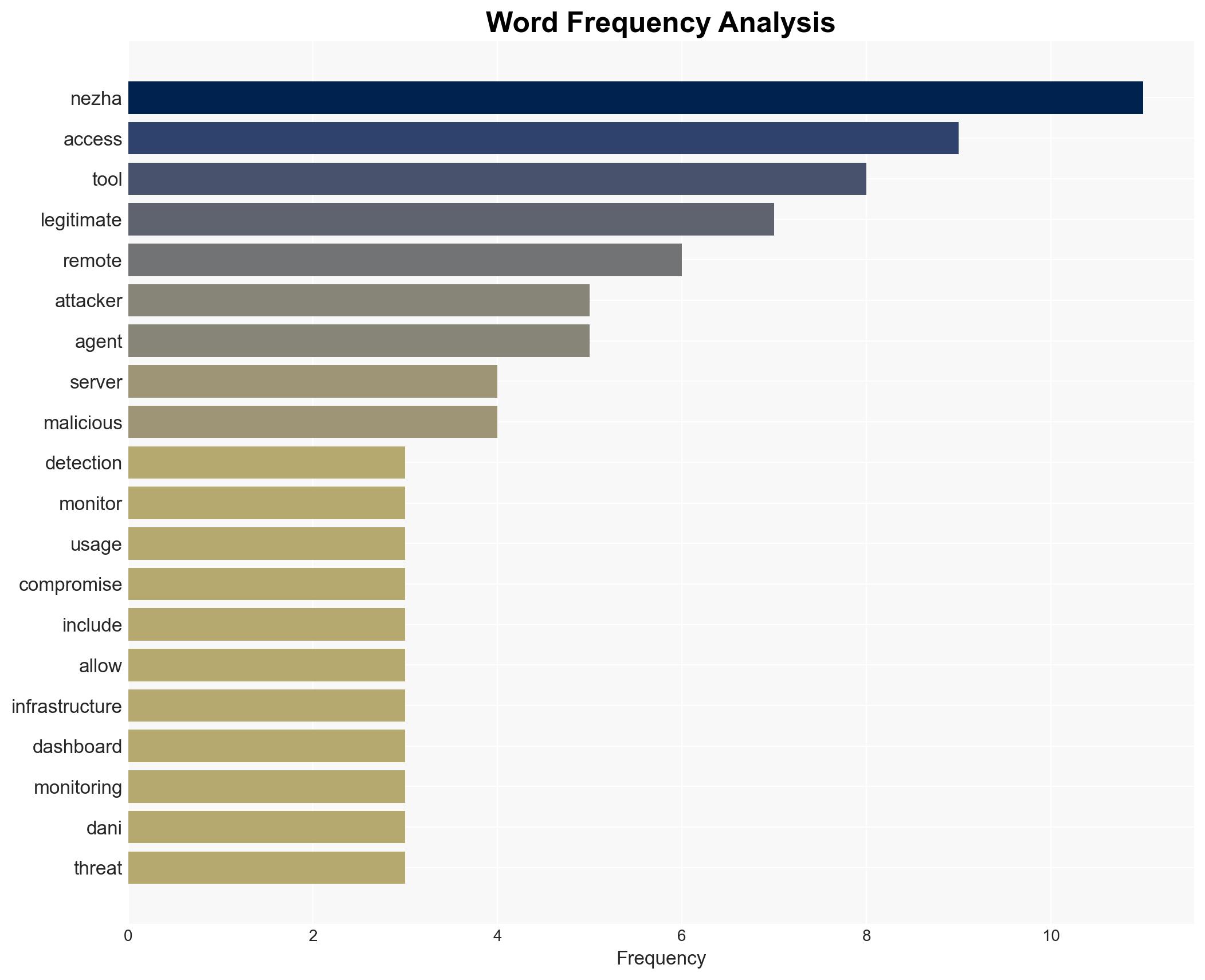
Attackers are exploiting the Nezha monitoring tool, originally designed for legitimate server management, as a stealthy remote access trojan to gain persistent, high-privilege access to compromised systems. This abuse poses a significant threat to organizations using Nezha, as it evades detection by major antivirus engines. The most likely hypothesis is that this exploitation is part of a broader trend of abusing legitimate software for cyber intrusions. Overall confidence in this assessment is moderate due to limited information on the attackers’ identities and motives.
2. Competing Hypotheses
- Hypothesis A: The abuse of Nezha is a targeted campaign by a sophisticated threat actor leveraging legitimate tools to evade detection. This is supported by the tool’s ability to bypass antivirus detection and the use of cloud infrastructure to blend in with legitimate operations. However, the specific threat actor remains unidentified, creating uncertainty.
- Hypothesis B: The exploitation of Nezha is opportunistic, carried out by multiple actors who have independently discovered its potential for stealthy access. This is suggested by the widespread compromise of endpoints and the use of a GitHub proxy service, which could indicate a lack of coordination among attackers.
- Assessment: Hypothesis A is currently better supported due to the sophistication of the deployment and the strategic use of cloud infrastructure, which suggests a coordinated effort rather than random opportunism. Key indicators that could shift this judgment include the identification of specific threat actors or evidence of disparate, uncoordinated attacks.
3. Key Assumptions and Red Flags
- Assumptions: The attackers have advanced technical capabilities; Nezha’s legitimate use will continue to mask malicious activities; the exploitation is part of a broader trend of abusing legitimate software.
- Information Gaps: Identity of the attackers; specific objectives of the campaign; the full scope of compromised entities.
- Bias & Deception Risks: Potential bias in attributing the attack to sophisticated actors without conclusive evidence; risk of deception by attackers using false flags to mislead attribution efforts.
4. Implications and Strategic Risks
The exploitation of Nezha could lead to increased adoption of similar tactics by other threat actors, complicating detection efforts and increasing the risk of widespread cyber intrusions.
- Political / Geopolitical: Potential for increased tensions if state-sponsored actors are implicated, leading to diplomatic strains.
- Security / Counter-Terrorism: Heightened threat environment as attackers gain persistent access to critical systems, potentially facilitating further cyber operations.
- Cyber / Information Space: Escalation in the use of legitimate tools for malicious purposes, challenging current cybersecurity defenses and detection methodologies.
- Economic / Social: Possible economic impacts due to compromised business operations and increased costs for cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring for Nezha-related activity; update security protocols to detect anomalies in legitimate software use; engage with cloud service providers to identify and mitigate malicious infrastructure.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for intelligence sharing; invest in advanced detection capabilities; conduct regular security audits of software tools in use.
- Scenario Outlook:
- Best: Rapid identification and neutralization of threat actors, minimizing impact.
- Worst: Proliferation of similar tactics leading to widespread cyber disruptions.
- Most-Likely: Continued exploitation of Nezha with gradual improvements in detection and response capabilities.
6. Key Individuals and Entities
- Ontinue AG
- Mayuresh Dani, Security Research Manager at Qualys Threat Research Unit
- Alibaba Cloud
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, remote access trojan, legitimate software abuse, threat detection, cloud infrastructure
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us