Washington’s Support Fuels Syrian Islamist Threat, Highlighted by Palmyra Executions of U.S. Soldiers
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: The Palmyra Betrayal Why Washington must stop subsidizing Syrias Islamist infiltration
1. BLUF (Bottom Line Up Front)
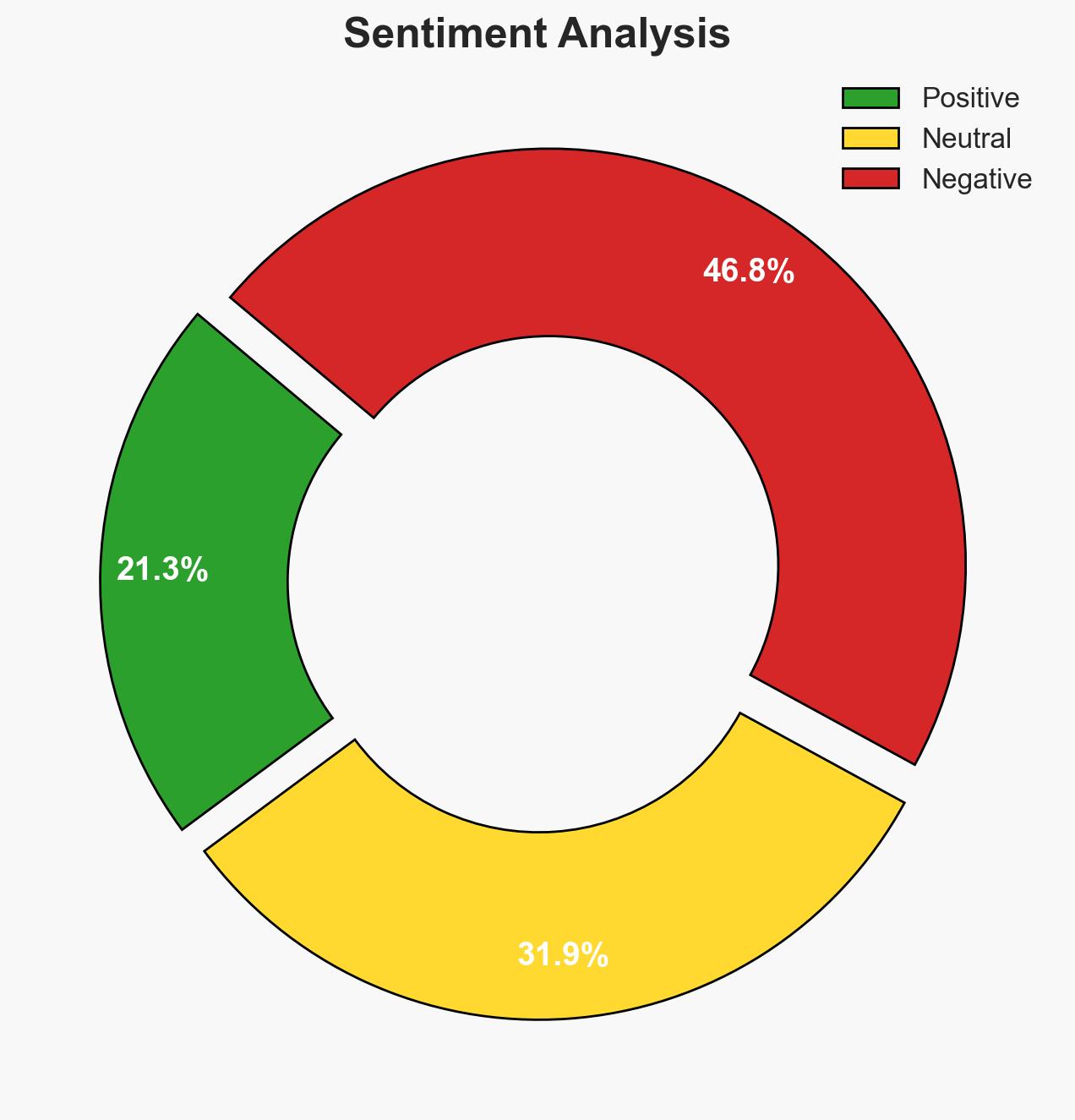
The execution of two American soldiers by a member of the Syrian internal security forces highlights a severe infiltration of extremist elements within Syrian state institutions. This incident underscores a critical failure in vetting processes and poses a significant threat to U.S. interests in the region. The most likely hypothesis is that Islamist sympathizers have systematically infiltrated Syrian security forces, with a moderate confidence level in this assessment.
2. Competing Hypotheses
- Hypothesis A: The Syrian security forces have been systematically infiltrated by Islamist sympathizers, leading to the execution of U.S. personnel. This is supported by the presence of a known radical within the ranks and the failure to act on extremist flags. Key uncertainties include the extent of infiltration and the level of awareness within the Syrian government.
- Hypothesis B: The incident was an isolated act of extremism by a rogue individual, not indicative of broader systemic issues. This is contradicted by the systemic failure to remove flagged individuals from sensitive positions.
- Assessment: Hypothesis A is currently better supported due to the systemic nature of the failures in vetting and the strategic objectives of extremist groups to degrade trust in U.S. partnerships. Indicators such as further insider attacks or increased extremist rhetoric within the Syrian forces could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The Syrian government lacks effective control over its security forces; extremist infiltration is a deliberate strategy by Islamist groups; U.S. policy is reliant on Syrian stability.
- Information Gaps: The full extent of extremist infiltration within Syrian security forces; the effectiveness of current U.S. vetting and oversight mechanisms.
- Bias & Deception Risks: Potential cognitive bias towards viewing Syrian government actions as monolithic; risk of Syrian government misinformation to downplay infiltration issues.
4. Implications and Strategic Risks
This development could exacerbate regional instability and undermine U.S. strategic objectives in the Middle East. The infiltration of extremist elements into Syrian security forces poses a direct threat to U.S. personnel and interests.
- Political / Geopolitical: Potential deterioration of U.S.-Syrian relations; increased influence of extremist groups within Syrian governance structures.
- Security / Counter-Terrorism: Heightened risk of insider attacks against U.S. and allied forces; challenges in coalition operations.
- Cyber / Information Space: Potential for extremist groups to exploit cyber vulnerabilities within Syrian security infrastructure.
- Economic / Social: Destabilization could deter international investment and aid, exacerbating economic challenges in Syria.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase vetting and oversight of Syrian security forces; enhance intelligence sharing with allies; review U.S. personnel security protocols.
- Medium-Term Posture (1–12 months): Develop resilience measures to counter extremist infiltration; strengthen partnerships with regional allies to monitor and mitigate threats.
- Scenario Outlook:
- Best: Successful reform of Syrian security forces and reduction of extremist influence.
- Worst: Escalation of insider attacks leading to broader conflict and U.S. withdrawal.
- Most-Likely: Continued challenges in vetting, with sporadic insider threats persisting.
6. Key Individuals and Entities
- President Ahmed al-Sharaa
- Syrian Internal Security Forces
- Islamic State (ISIS)
- U.S. Department of Defense
7. Thematic Tags
Counter-Terrorism, Middle East policy, security infiltration, extremist ideology, U.S. foreign policy, insider threats, Syrian stability
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us