Senate recess leaves CISA without confirmed director as Plankey’s nomination stalls amid bipartisan objections
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Senate adjourns without confirming CISA director
1. BLUF (Bottom Line Up Front)
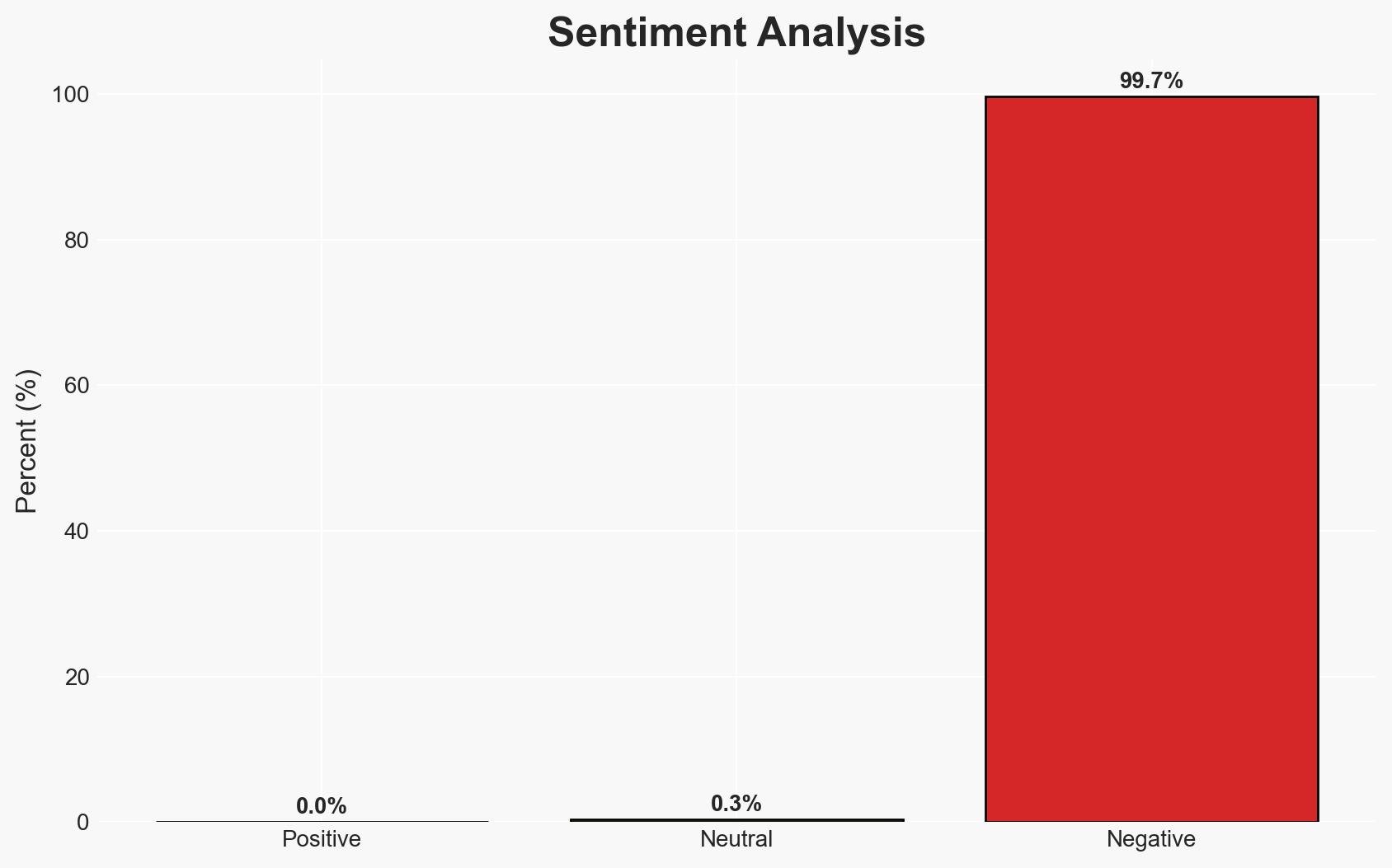
The Senate’s adjournment without confirming Sean Plankey as the CISA director extends the leadership vacuum at a critical time for U.S. cyber defense, particularly in a midterm election year. This situation exacerbates existing workforce and operational challenges within CISA, potentially undermining its ability to protect critical infrastructure. The overall confidence level in this assessment is moderate due to procedural uncertainties and political dynamics.
2. Competing Hypotheses
- Hypothesis A: The delay in confirming the CISA director is primarily due to procedural hurdles and political disputes unrelated to cybersecurity policy. Supporting evidence includes bipartisan objections and broader political disputes. Key uncertainties involve the specific political motivations behind the objections.
- Hypothesis B: The delay is strategically motivated to weaken CISA’s operational capabilities, potentially benefiting adversaries. Contradicting evidence includes the lack of direct indications of such a strategy and procedural nature of the delays.
- Assessment: Hypothesis A is currently better supported due to the procedural nature of the objections and lack of direct evidence for strategic weakening. Indicators that could shift this judgment include new evidence of targeted political maneuvers against CISA.
3. Key Assumptions and Red Flags
- Assumptions: The leadership vacuum will persist into the new year; political disputes are not directly linked to cybersecurity policy; CISA’s operational capabilities are currently compromised.
- Information Gaps: Specific details on the political objections and their direct impact on CISA’s operations; the White House’s plans for renomination.
- Bias & Deception Risks: Potential bias in attributing delays solely to procedural issues without considering strategic motivations; risk of underestimating adversarial exploitation of CISA’s weakened state.
4. Implications and Strategic Risks
The continued leadership vacuum at CISA could exacerbate existing operational challenges, impacting the agency’s ability to safeguard critical infrastructure during a politically sensitive period. This development may interact with broader geopolitical tensions, particularly with adversaries like China.
- Political / Geopolitical: Potential erosion of confidence in U.S. cyber defense capabilities; exploitation by foreign adversaries.
- Security / Counter-Terrorism: Increased vulnerability to cyber threats and misinformation campaigns, especially during elections.
- Cyber / Information Space: Potential for increased cyber-attacks on critical infrastructure and federal networks.
- Economic / Social: Possible destabilization of public trust in electoral processes and government cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Expedite the renomination process; enhance interim leadership capabilities; increase monitoring of critical infrastructure vulnerabilities.
- Medium-Term Posture (1–12 months): Strengthen inter-agency collaboration; invest in workforce development; enhance public-private partnerships for cyber defense.
- Scenario Outlook:
- Best: Quick confirmation of a new director stabilizes CISA operations.
- Worst: Prolonged leadership vacuum leads to significant cyber incidents.
- Most-Likely: Interim measures mitigate immediate risks, but long-term challenges persist.
6. Key Individuals and Entities
- Sean Plankey, CISA
- Department of Homeland Security
- U.S. Senate
- White House
7. Thematic Tags
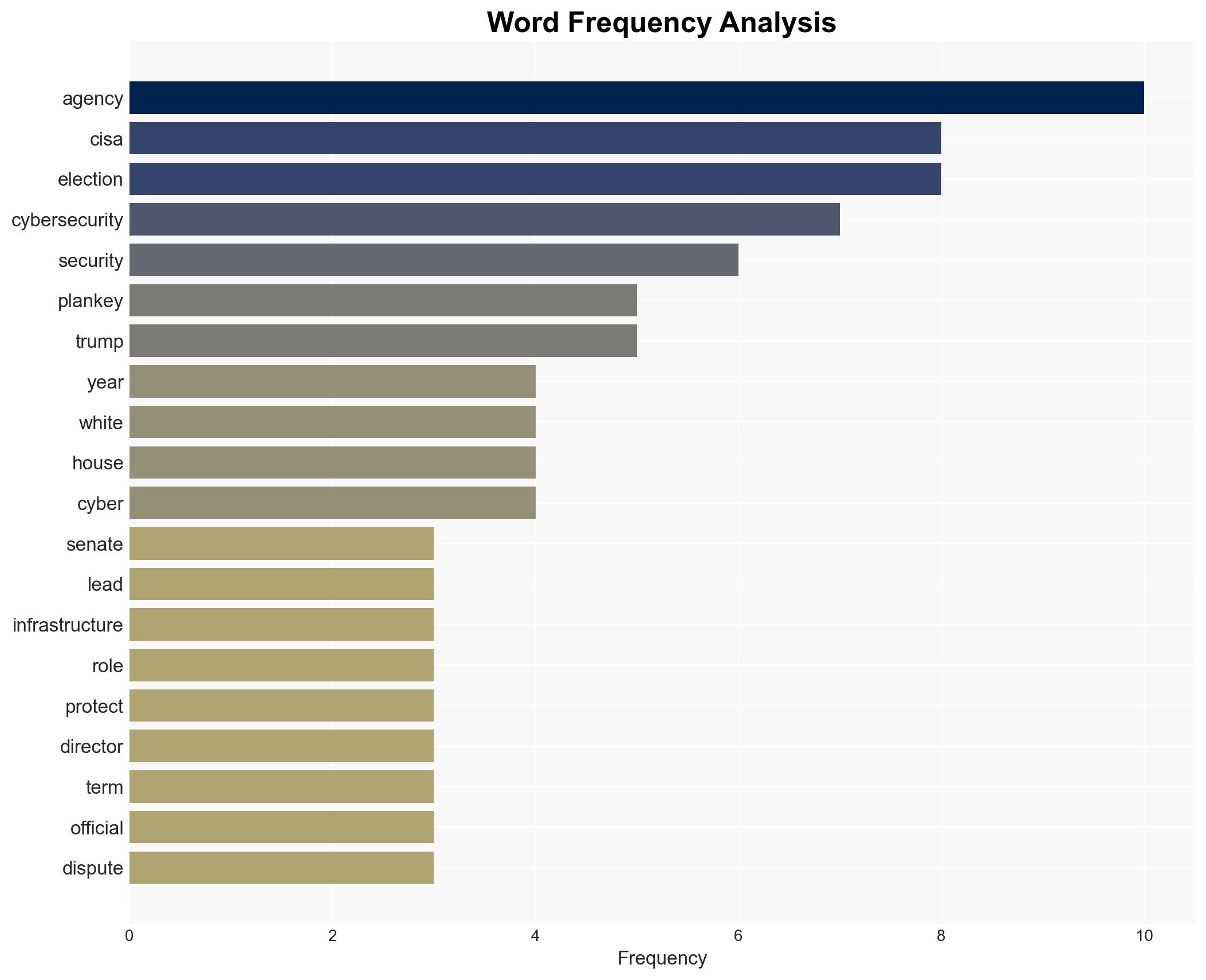
cybersecurity, CISA, U.S. Senate, leadership vacuum, critical infrastructure, political dynamics, cyber threats
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us