Nissan confirms data breach at Red Hat exposes information of 21,000 customers in Fukuoka, Japan
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Nissan says thousands of customers exposed in Red Hat breach
1. BLUF (Bottom Line Up Front)
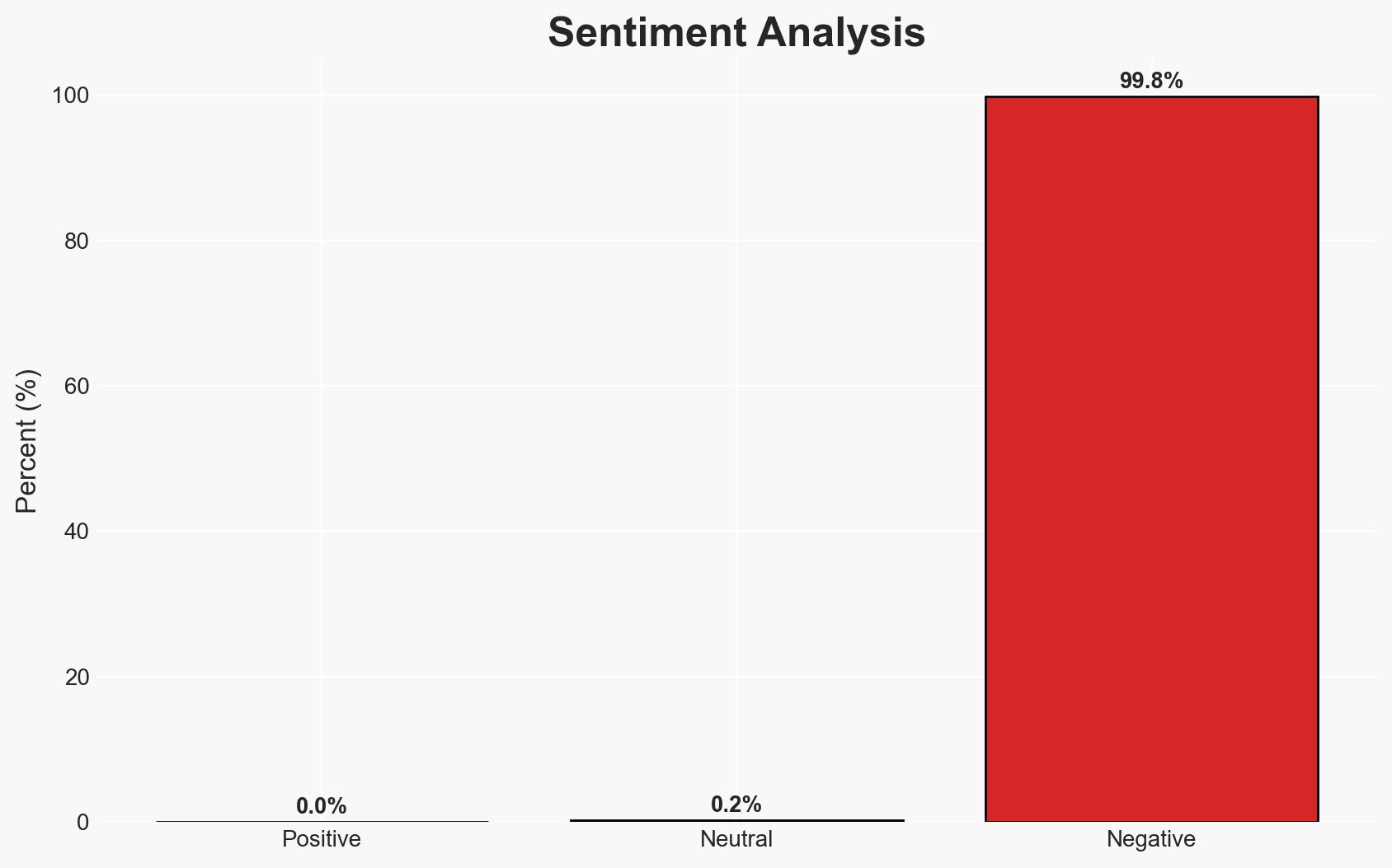
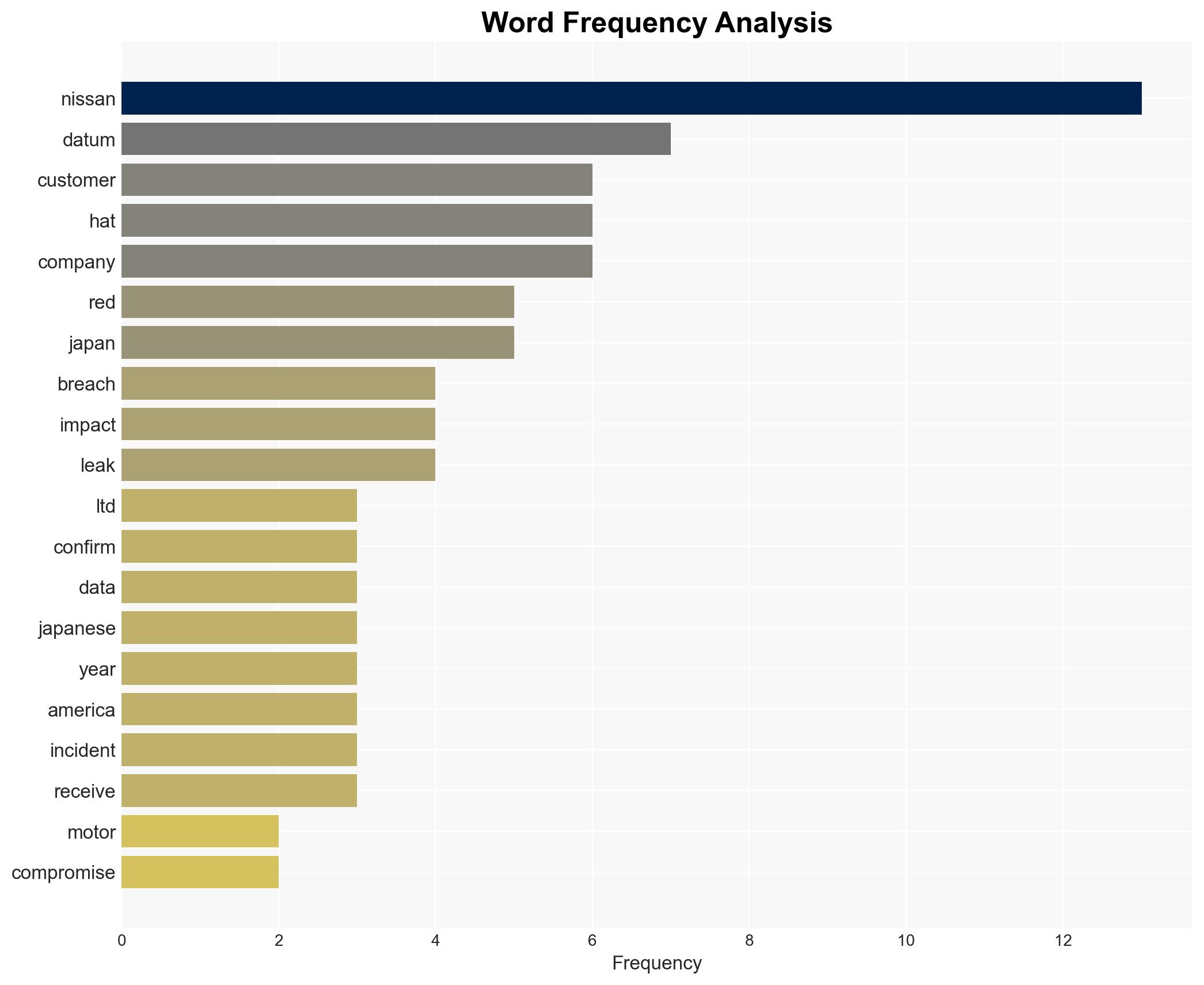
The recent data breach at Red Hat has compromised personal information of approximately 21,000 Nissan customers in Fukuoka, Japan. The breach, attributed to the Crimson Collective and ShinyHunters, highlights vulnerabilities in Nissan’s third-party data management systems. While no financial data was exposed, the incident underscores potential risks to customer trust and operational security. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The breach was primarily a result of vulnerabilities in Red Hat’s data security protocols, exploited by external threat actors. Supporting evidence includes the involvement of known cybercriminal groups and the scale of data accessed. However, the specific vulnerabilities exploited remain unidentified, creating uncertainty.
- Hypothesis B: The breach may have been facilitated by internal negligence or insider threat within Red Hat, potentially exacerbated by inadequate security oversight by Nissan. While no direct evidence supports this, the lack of immediate detection suggests possible internal lapses.
- Assessment: Hypothesis A is currently better supported due to the known involvement of external cybercriminal groups and the absence of evidence pointing to internal complicity. Key indicators that could shift this judgment include discovery of insider involvement or evidence of systemic security failures within Red Hat.
3. Key Assumptions and Red Flags
- Assumptions: Red Hat’s security protocols were insufficient to prevent unauthorized access; Nissan’s customer data was adequately protected except for this incident; external threat actors were primarily responsible for the breach.
- Information Gaps: Specific vulnerabilities exploited in Red Hat’s systems; full extent of data accessed or potentially misused; internal security measures at Red Hat and Nissan.
- Bias & Deception Risks: Potential bias in attributing the breach solely to external actors without considering internal factors; reliance on Nissan’s and Red Hat’s disclosures, which may understate the breach’s impact.
4. Implications and Strategic Risks
This breach could lead to increased scrutiny of Nissan’s data management practices and impact customer trust. It may also prompt regulatory actions and influence cybersecurity policies in the automotive sector.
- Political / Geopolitical: Potential diplomatic discussions on cybersecurity standards between Japan and the U.S., where Red Hat is based.
- Security / Counter-Terrorism: Increased risk of targeted cyberattacks on Nissan and its partners, necessitating enhanced security measures.
- Cyber / Information Space: Likely escalation in cyber threats targeting automotive industry supply chains; potential for further data leaks.
- Economic / Social: Possible financial impact on Nissan due to reputational damage and customer attrition; broader implications for consumer confidence in data security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of third-party vendors; enhance monitoring of data access logs; communicate transparently with affected customers.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms; invest in advanced threat detection technologies; develop a robust incident response plan.
- Scenario Outlook:
- Best: No further data misuse detected, leading to restored customer trust.
- Worst: Additional breaches occur, severely damaging Nissan’s reputation and financial standing.
- Most-Likely: Incremental improvements in cybersecurity posture with gradual recovery of customer confidence.
6. Key Individuals and Entities
- Nissan Motor Co. Ltd.
- Red Hat
- Crimson Collective
- ShinyHunters
- Nissan Fukuoka Sales Co., Ltd.
7. Thematic Tags
cybersecurity, data breach, automotive industry, third-party risk, threat actors, customer data, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us