Third-Party Access: A Critical Vulnerability in Supply Chain Security Management
Published on: 2025-12-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Why Third-Party Access Remains the Weak Link in Supply Chain Security
1. BLUF (Bottom Line Up Front)
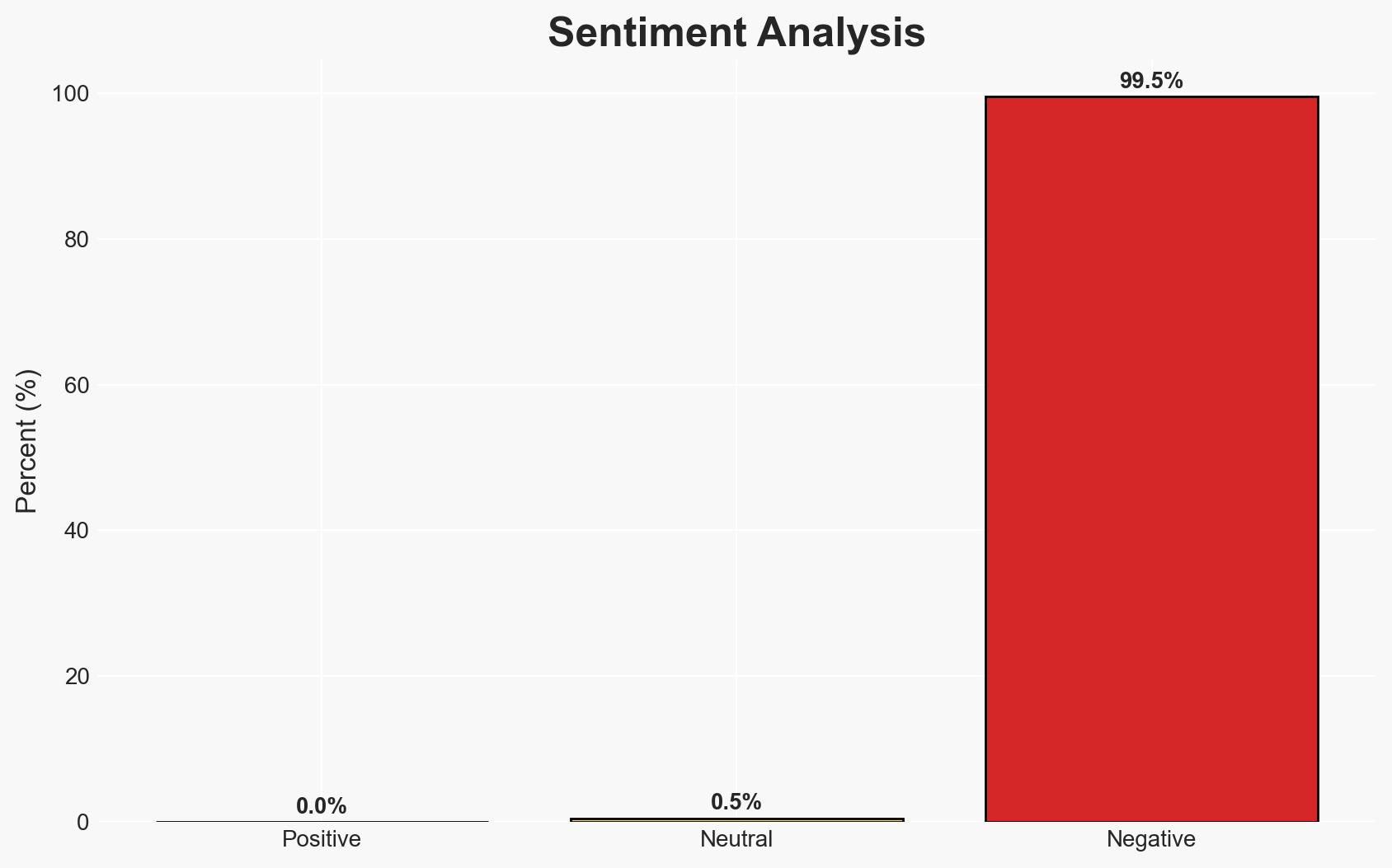
The exploitation of third-party access remains a critical vulnerability in supply chain security, with attackers leveraging weak access controls to infiltrate systems. This issue affects organizations across sectors, increasing their exposure to cyber threats. The most likely hypothesis is that inadequate identity and access management practices are the primary enablers of these vulnerabilities. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The primary cause of supply chain security breaches is weak identity and access management controls, as evidenced by the retention of access by third parties long after it is needed. This hypothesis is supported by the Thales Digital Trust Index report, which highlights poor access management practices. Key uncertainties include the extent of awareness and capability to implement stronger controls.
- Hypothesis B: Breaches are primarily due to sophisticated attacker techniques that exploit inherent vulnerabilities in web protocols and authentication methods. While attackers do exploit known weaknesses, this hypothesis is less supported by the evidence, which emphasizes poor implementation and management practices.
- Assessment: Hypothesis A is currently better supported due to the direct correlation between poor access management practices and increased vulnerability. Indicators that could shift this judgment include new evidence of advanced persistent threats exploiting novel vulnerabilities.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have the capability to improve access management; attackers will continue to exploit weak controls; third-party access is necessary for business operations; current practices are insufficient to mitigate risks.
- Information Gaps: Specific details on the types of organizations most affected; quantitative data on the impact of breaches; effectiveness of current mitigation strategies.
- Bias & Deception Risks: Potential bias in survey data from the Thales report; over-reliance on reported practices without independent verification; possible underreporting of breaches due to reputational concerns.
4. Implications and Strategic Risks
This development could lead to increased regulatory scrutiny and demand for improved cybersecurity standards. Organizations may face heightened risk of data breaches and operational disruptions.
- Political / Geopolitical: Potential for increased international regulatory cooperation on cybersecurity standards.
- Security / Counter-Terrorism: Expanded attack surface could be exploited by state and non-state actors, increasing the threat landscape.
- Cyber / Information Space: Greater emphasis on developing robust identity and access management solutions; potential rise in cyber insurance costs.
- Economic / Social: Potential financial losses and reputational damage for affected organizations; increased demand for cybersecurity professionals.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct comprehensive audits of third-party access; implement stricter access controls and monitoring; initiate awareness campaigns on access management.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; invest in advanced identity and access management technologies; enhance training programs for staff.
- Scenario Outlook: Best: Organizations strengthen access controls, reducing breach incidents. Worst: Continued neglect leads to significant breaches and regulatory penalties. Most-Likely: Incremental improvements in access management with ongoing breaches due to lagging implementation.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
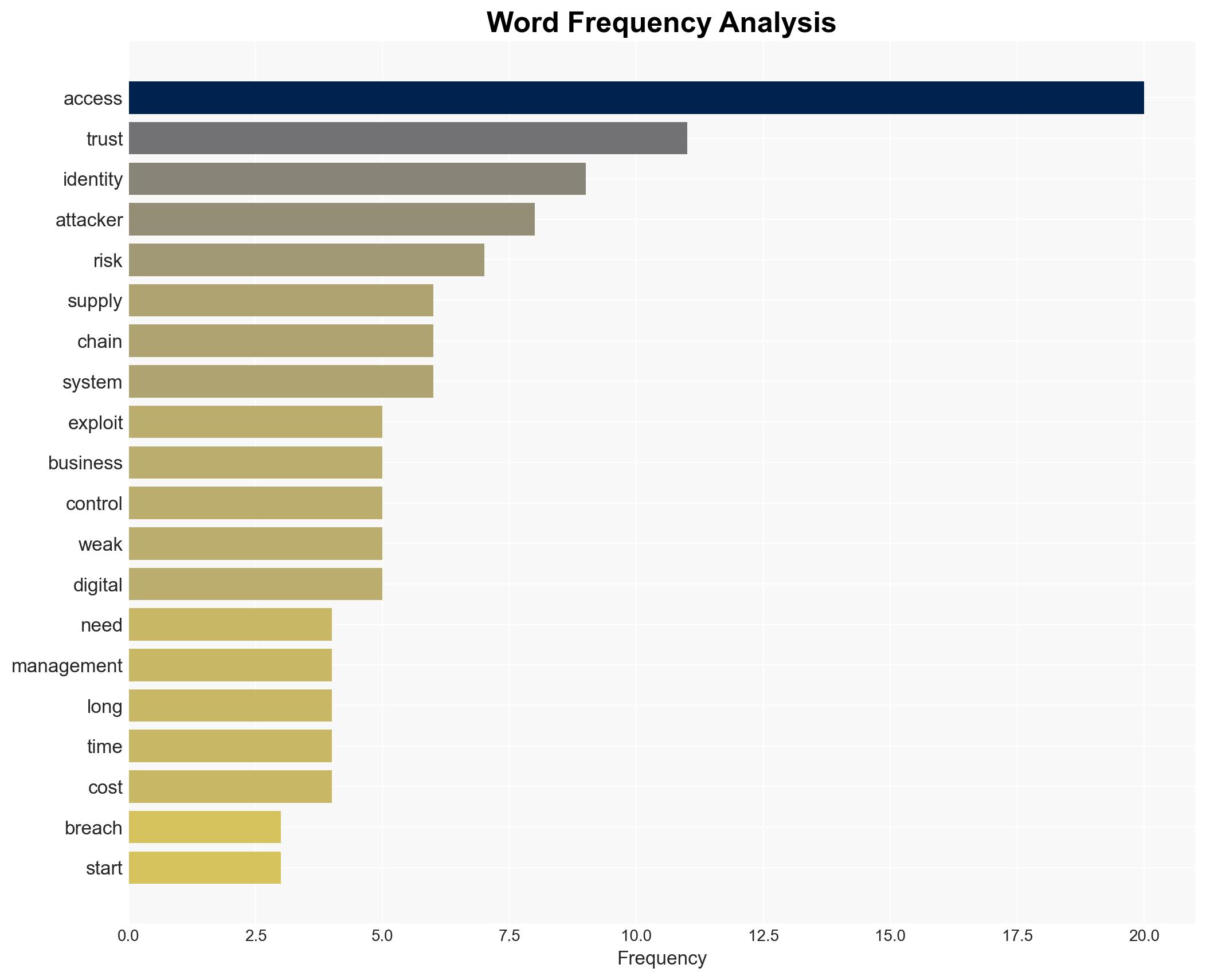
cybersecurity, supply chain security, identity management, cyber vulnerabilities, access control, third-party risk, cybersecurity strategy, digital trust
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us