Trojan NPM Package lotusbail Discovered, Compromising WhatsApp Chats and User Data
Published on: 2025-12-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Popular NPM Package lotusbail Exposed as Trojan Stealing WhatsApp Chats
1. BLUF (Bottom Line Up Front)
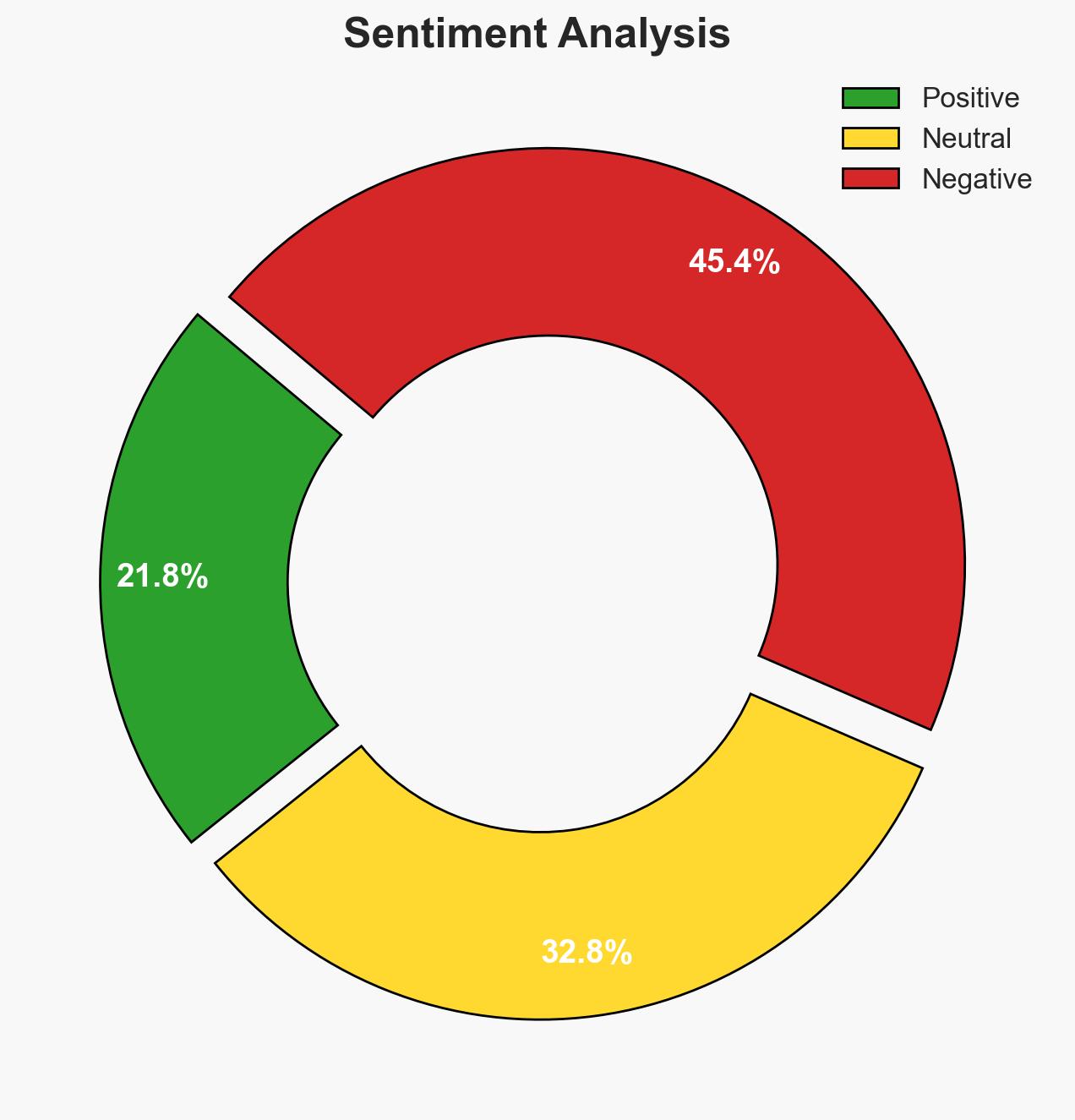
The NPM package lotusbail has been identified as a Trojan horse targeting WhatsApp users by hijacking accounts and stealing private data. This threat affects developers and end-users relying on applications that connect to WhatsApp. The most likely hypothesis is that the malware was deliberately designed for espionage or data theft. Overall confidence in this assessment is moderate, given the technical sophistication observed.
2. Competing Hypotheses
- Hypothesis A: The lotusbail package was intentionally developed as a Trojan for espionage or data theft. This is supported by the sophisticated methods used to intercept data and maintain persistent access. The use of encryption and traps indicates a high level of planning and technical capability. However, the identity and motives of the developers remain unclear.
- Hypothesis B: The lotusbail package was inadvertently compromised by a third party who inserted malicious code. This hypothesis is less supported due to the deliberate and complex nature of the malware’s functions, which suggest intentional design rather than accidental compromise.
- Assessment: Hypothesis A is currently better supported due to the deliberate and sophisticated nature of the malware’s design. Key indicators that could shift this judgment include evidence of external compromise or identification of the developers with benign intentions.
3. Key Assumptions and Red Flags
- Assumptions: The malware’s primary purpose is data theft; the developers had the technical capability to create such a Trojan; the encryption and traps were intentionally designed to evade detection.
- Information Gaps: The identity and motives of the developers; the full extent of data compromised; potential connections to larger cyber-espionage campaigns.
- Bias & Deception Risks: Potential bias in attributing intent without direct evidence; reliance on technical analysis that may overlook alternative explanations; possible deception by the developers to mislead investigators.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of open-source packages and heightened security measures among developers. It may also prompt further investigations into similar threats.
- Political / Geopolitical: Potential diplomatic tensions if state-sponsored involvement is suspected.
- Security / Counter-Terrorism: Increased risk of data breaches and espionage activities targeting communication platforms.
- Cyber / Information Space: Heightened awareness and potential regulatory actions on software supply chain security.
- Economic / Social: Trust erosion in open-source software and potential economic impacts on companies relying on compromised packages.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct audits of applications using the lotusbail package; inform affected users to check and secure their WhatsApp accounts; enhance monitoring for similar threats.
- Medium-Term Posture (1–12 months): Develop partnerships for improved threat intelligence sharing; invest in secure software development practices; enhance capabilities to detect and respond to similar threats.
- Scenario Outlook: Best: Rapid identification and mitigation of affected systems. Worst: Widespread data breaches and loss of sensitive information. Most-Likely: Gradual containment with increased awareness and security measures.
6. Key Individuals and Entities
- Tuval Admoni, Koi Security researcher
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, malware, data theft, open-source security, espionage, software supply chain, encryption
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us