Condé Nast suffers significant data breach with 2.3M Wired user records leaked and 40M more at risk
Published on: 2025-12-28
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cond Nast faces major data breach 23M WIRED records leaked 40M more at risk
1. BLUF (Bottom Line Up Front)
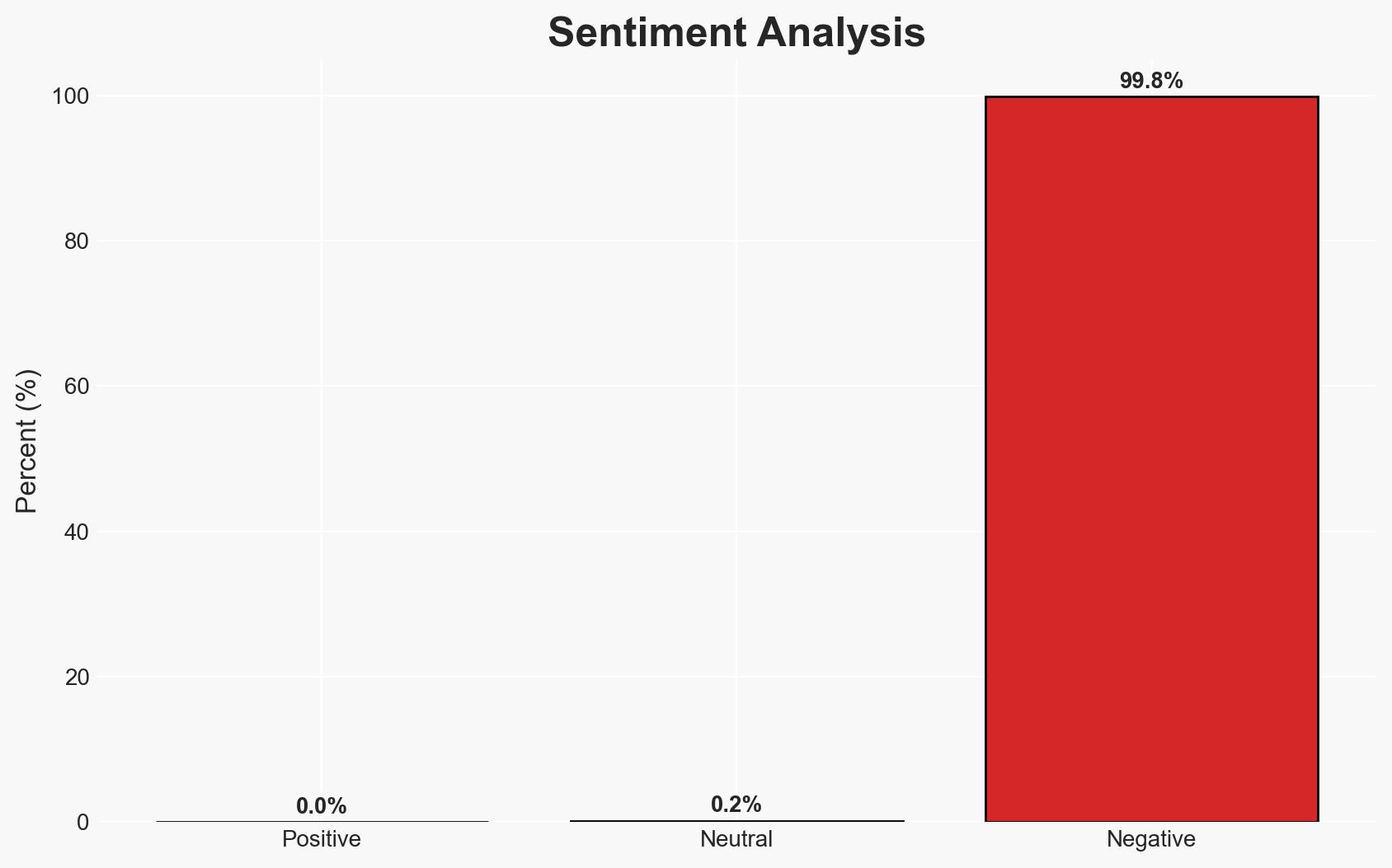
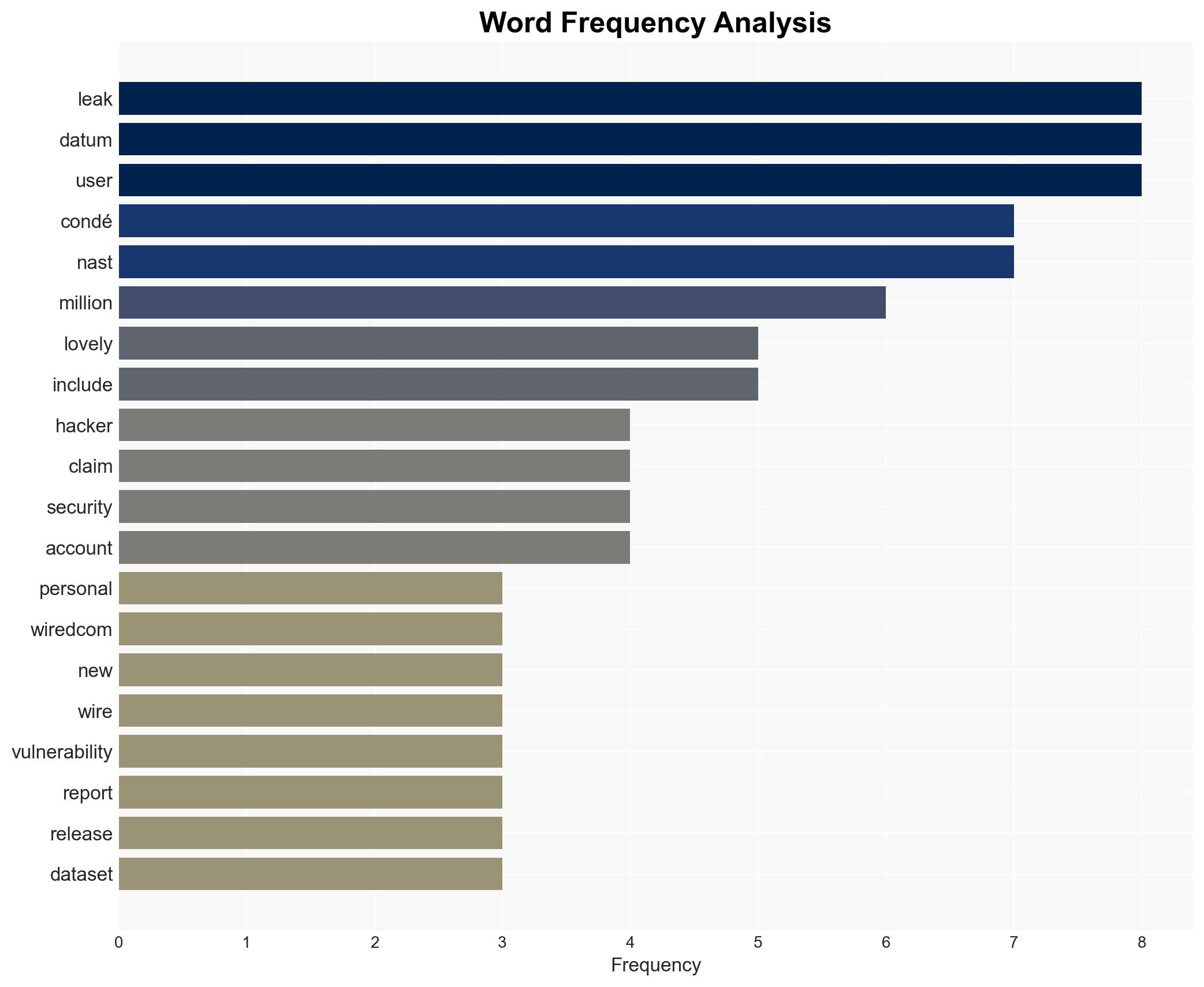
A significant data breach has compromised over 2.3 million Wired.com user records, with a potential risk to 40 million more across Condé Nast’s brands. The breach highlights systemic vulnerabilities in Condé Nast’s security infrastructure. The most likely hypothesis is that the hacker, “Lovely,” exploited these vulnerabilities after failed attempts at responsible disclosure. This situation poses substantial risks for user privacy and brand reputation. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The hacker “Lovely” exploited known vulnerabilities after Condé Nast failed to address security warnings. Supporting evidence includes Lovely’s claims of ignored warnings and the hacker’s initial approach as a security researcher. However, the hacker’s motivations and potential exaggeration of claims remain uncertain.
- Hypothesis B: The breach resulted from an insider threat or a coordinated attack by multiple actors. This hypothesis is less supported, as there is no current evidence of insider involvement or coordinated efforts beyond Lovely’s actions.
- Assessment: Hypothesis A is currently better supported due to the hacker’s detailed claims and the corroboration of the breach by external entities like Hudson Rock. Indicators that could shift this judgment include evidence of insider involvement or additional actors.
3. Key Assumptions and Red Flags
- Assumptions: Condé Nast’s centralized account system has systemic vulnerabilities; Lovely’s claims are partially accurate; external validation of the breach is reliable.
- Information Gaps: Specific details on how the vulnerabilities were exploited; confirmation of the hacker’s identity and motivations; extent of Condé Nast’s internal security measures.
- Bias & Deception Risks: Potential bias in Lovely’s narrative to exaggerate Condé Nast’s negligence; risk of deception in hacker forums where Lovely operates.
4. Implications and Strategic Risks
The breach could lead to increased scrutiny of Condé Nast’s cybersecurity practices and potential legal consequences. It may also embolden other hackers to target similar vulnerabilities in media companies.
- Political / Geopolitical: Limited direct geopolitical impact, but potential for regulatory actions in jurisdictions with strict data protection laws.
- Security / Counter-Terrorism: Increased risk of doxing, swatting, and spear-phishing targeting Condé Nast users.
- Cyber / Information Space: Potential for further cyber-attacks exploiting similar vulnerabilities in other companies.
- Economic / Social: Damage to Condé Nast’s brand reputation and potential financial liabilities from user lawsuits.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of Condé Nast’s systems; engage with cybersecurity firms for incident response; communicate transparently with affected users.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity experts; implement robust vulnerability management programs; enhance user data protection measures.
- Scenario Outlook:
- Best Case: Vulnerabilities are swiftly addressed, and user trust is restored.
- Worst Case: Additional breaches occur, leading to severe reputational and financial damage.
- Most Likely: Condé Nast improves security posture, but faces ongoing scrutiny and potential legal challenges.
6. Key Individuals and Entities
- Lovely (Hacker)
- Condé Nast (Parent Company)
- Hudson Rock (Cybersecurity Firm)
- Alon Gal (Hudson Rock Co-founder)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, media industry, user privacy, hacker threats, brand reputation, vulnerability management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us