Security Gaps in Syria’s Transition Enable Islamic State to Launch Targeted Attacks on US Forces
Published on: 2025-12-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Syrias incomplete security Transition has left gaps for Islamic State to Exploit
1. BLUF (Bottom Line Up Front)
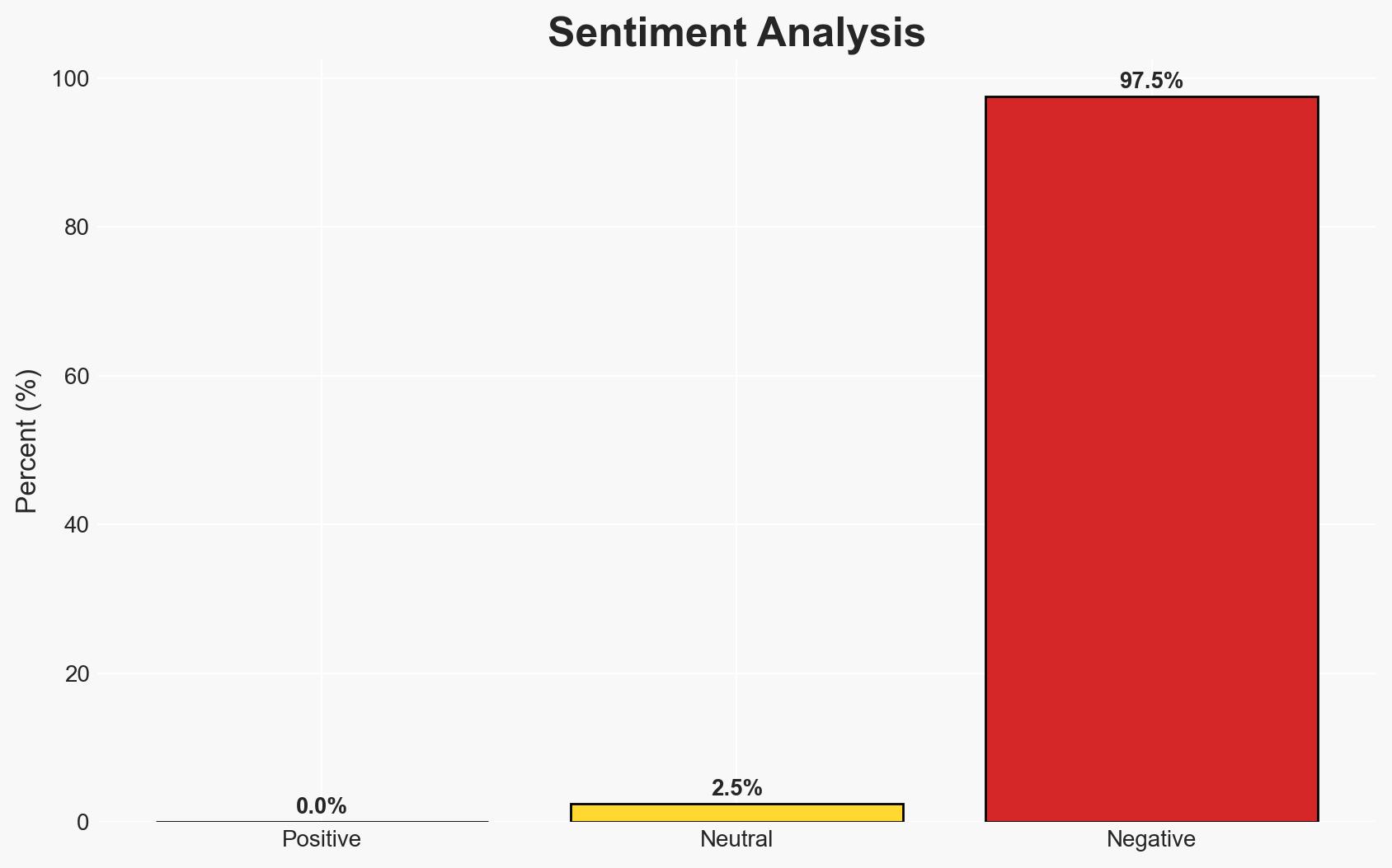
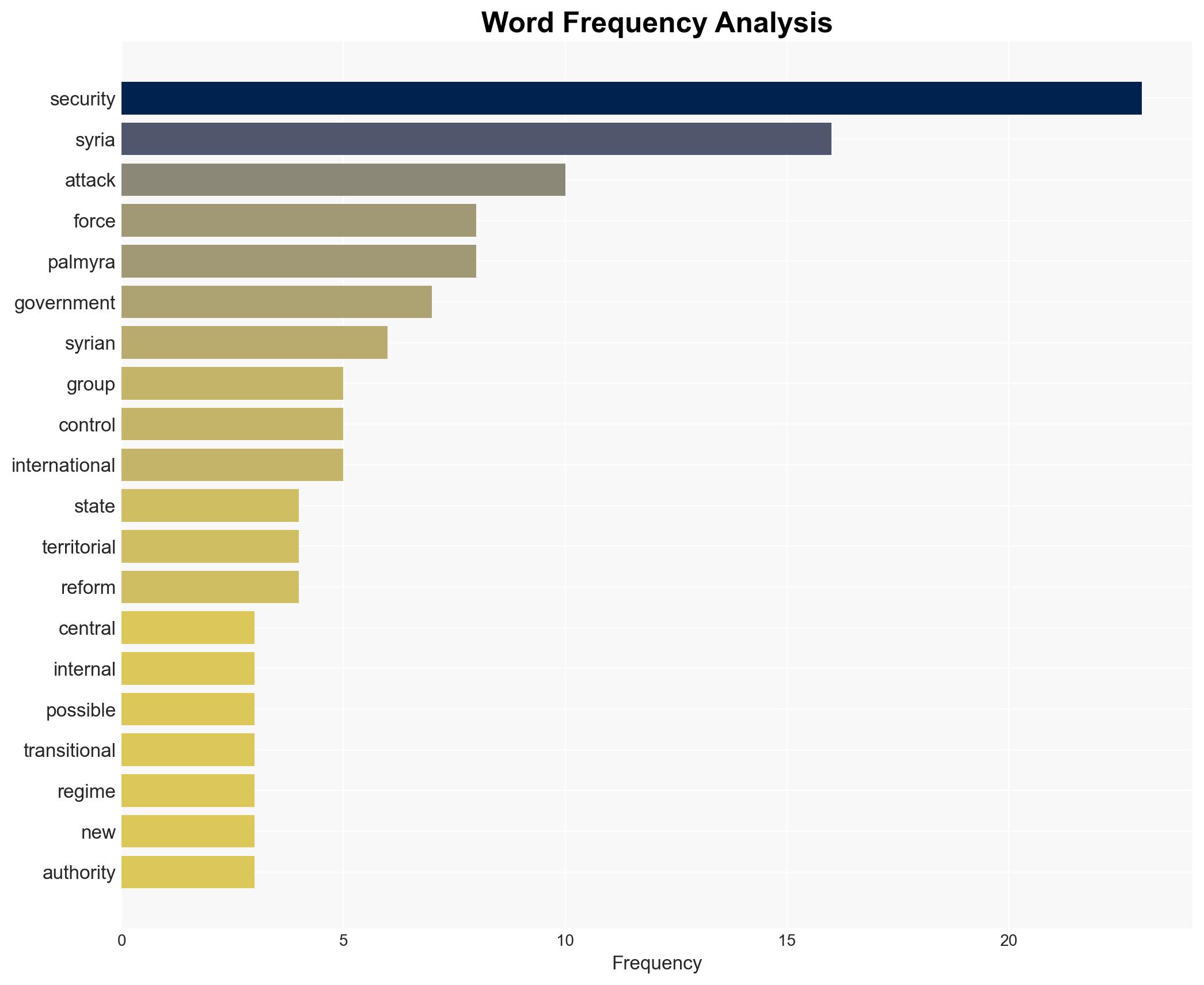
The Syrian transitional government’s rapid security sector assembly has left critical vulnerabilities, enabling Islamic State (IS) to exploit these gaps through insurgent tactics. The attack near Palmyra highlights the fragmented security landscape and the challenges in vetting recruits. This situation poses a significant threat to regional stability and counter-terrorism efforts. Overall confidence in this assessment is moderate, given the incomplete data on IS infiltration levels and the transitional government’s capacity to respond effectively.
2. Competing Hypotheses
- Hypothesis A: The attack was a result of insufficient vetting and rapid integration of diverse factions into Syria’s security forces. Supporting evidence includes the attacker’s recent enlistment and prior suspicion of extremist sympathies. Key uncertainties involve the extent of IS infiltration and the effectiveness of current vetting processes.
- Hypothesis B: The attack was an isolated incident, not indicative of broader systemic failures within the Syrian security apparatus. This hypothesis is contradicted by the fragmented security environment and ongoing IS insurgency tactics, which suggest systemic vulnerabilities.
- Assessment: Hypothesis A is currently better supported, as the attack aligns with known IS strategies to exploit institutional weaknesses. Indicators such as further attacks or increased infiltration reports could reinforce this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The transitional government lacks comprehensive vetting processes; IS continues to target weak institutional structures; the security landscape remains fragmented.
- Information Gaps: Detailed data on the extent of IS infiltration within Syrian security forces; effectiveness of current counter-insurgency measures.
- Bias & Deception Risks: Potential over-reliance on reports from local security forces, which may be biased or incomplete; IS propaganda efforts could distort perceptions of their capabilities.
4. Implications and Strategic Risks
The current security vulnerabilities in Syria could lead to increased IS activity, further destabilizing the region and complicating international counter-terrorism efforts.
- Political / Geopolitical: Potential for increased foreign intervention or support to stabilize the region, risking geopolitical tensions.
- Security / Counter-Terrorism: Heightened threat of IS attacks, requiring enhanced counter-terrorism operations and international cooperation.
- Cyber / Information Space: IS may exploit digital platforms for recruitment and propaganda, necessitating robust cyber defenses.
- Economic / Social: Prolonged instability could hinder economic recovery and exacerbate social tensions within Syria.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance vetting processes for security recruits; increase intelligence-sharing with international partners; monitor IS communications for threat indicators.
- Medium-Term Posture (1–12 months): Develop comprehensive security sector reforms; strengthen alliances with regional counter-terrorism entities; invest in community-based de-radicalization programs.
- Scenario Outlook:
- Best: Successful reform and international support stabilize the security environment.
- Worst: IS escalates attacks, leading to widespread instability and humanitarian crises.
- Most-Likely: Continued sporadic IS activity with gradual improvements in security sector capabilities.
6. Key Individuals and Entities
- Ahmed al-Sharaa (Syrian President)
- Islamic State (IS)
- Syrian internal security forces
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
national security threats, counter-terrorism, security sector reform, insurgency, geopolitical stability, intelligence-sharing, IS infiltration, Syrian transitional government
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us