Mustang Panda Deploys TONESHELL Backdoor via Undocumented Kernel-Mode Rootkit in Recent Cyber Attack
Published on: 2025-12-30
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Mustang Panda Uses Signed Kernel-Mode Rootkit to Load TONESHELL Backdoor
1. BLUF (Bottom Line Up Front)
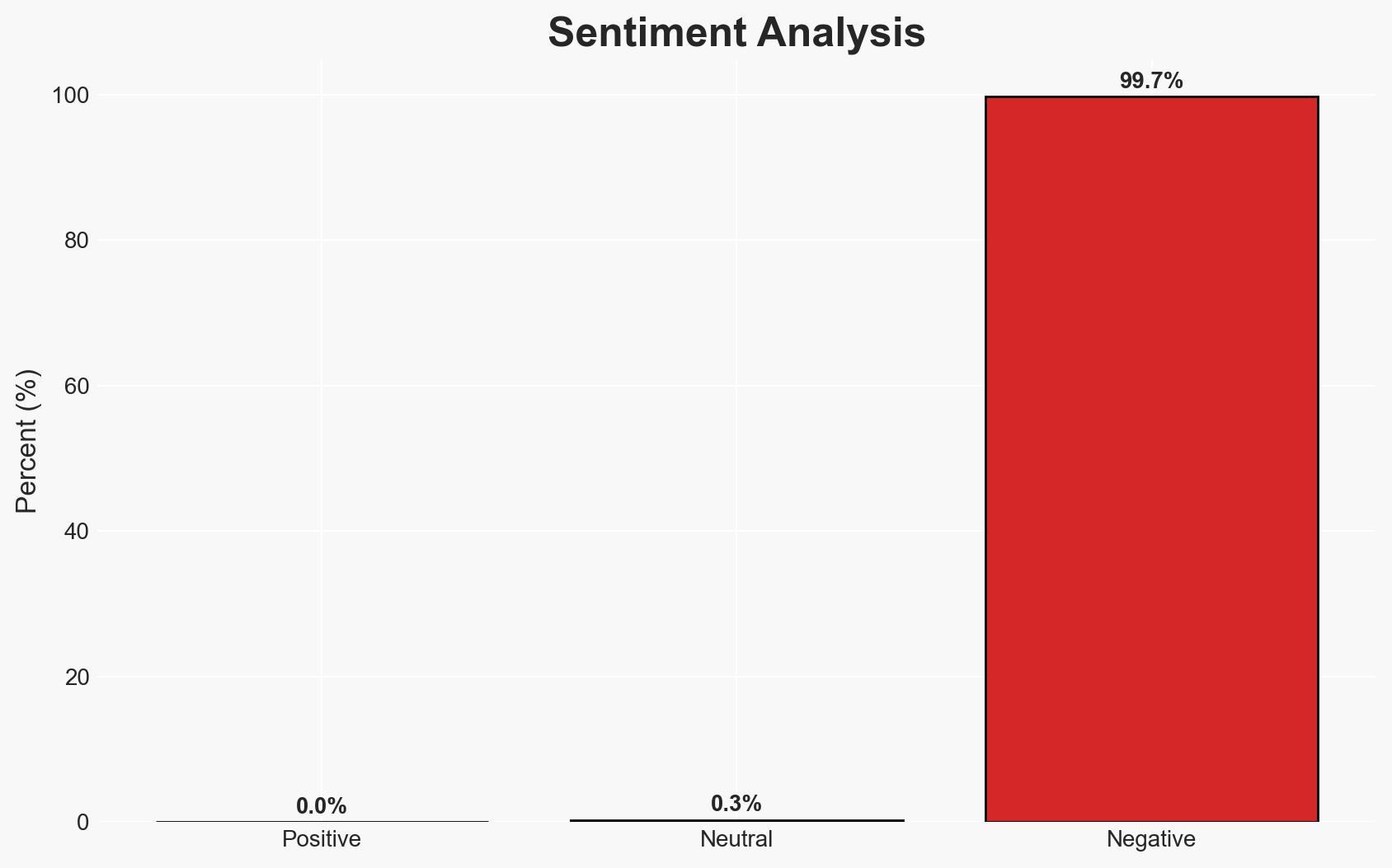
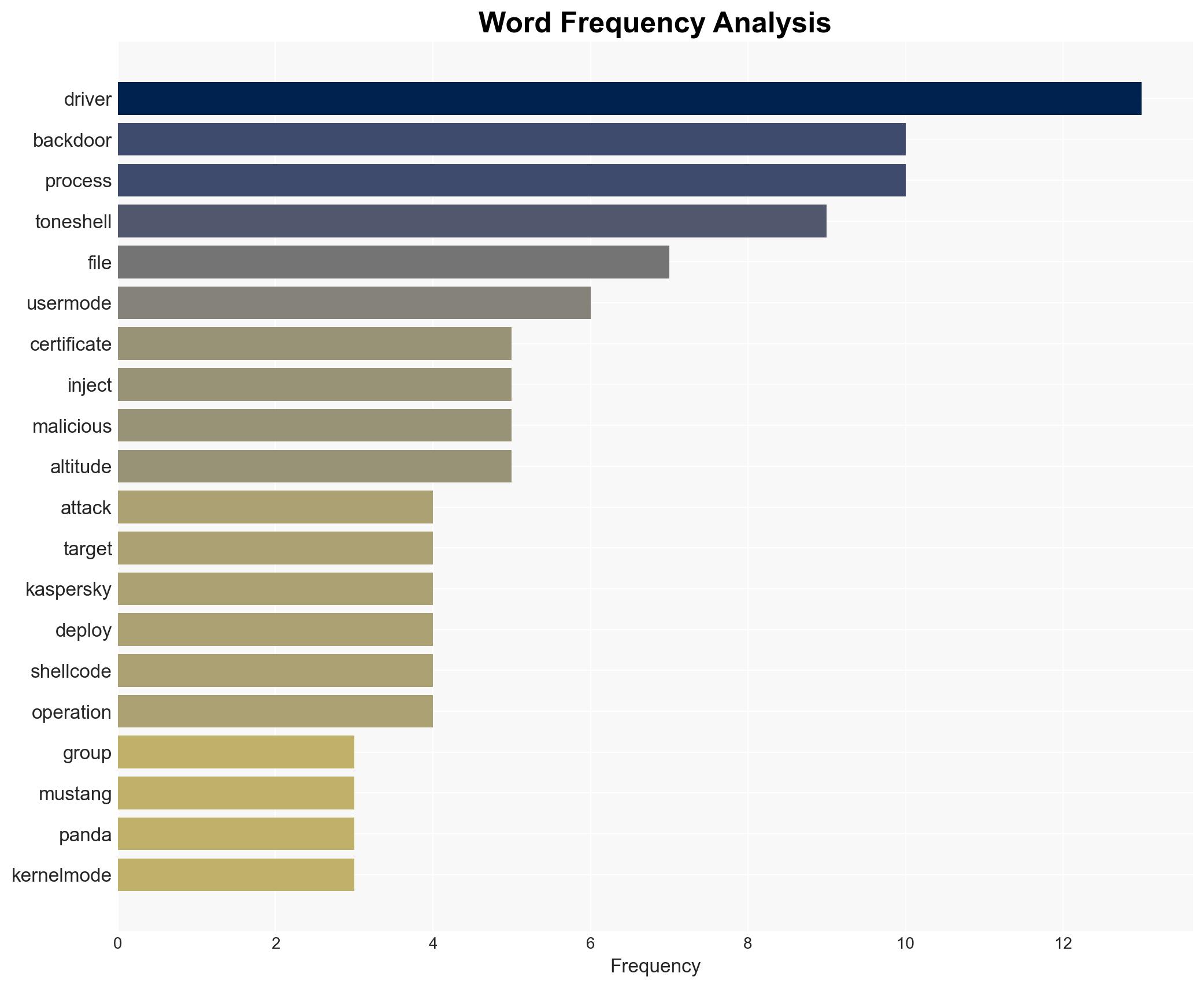
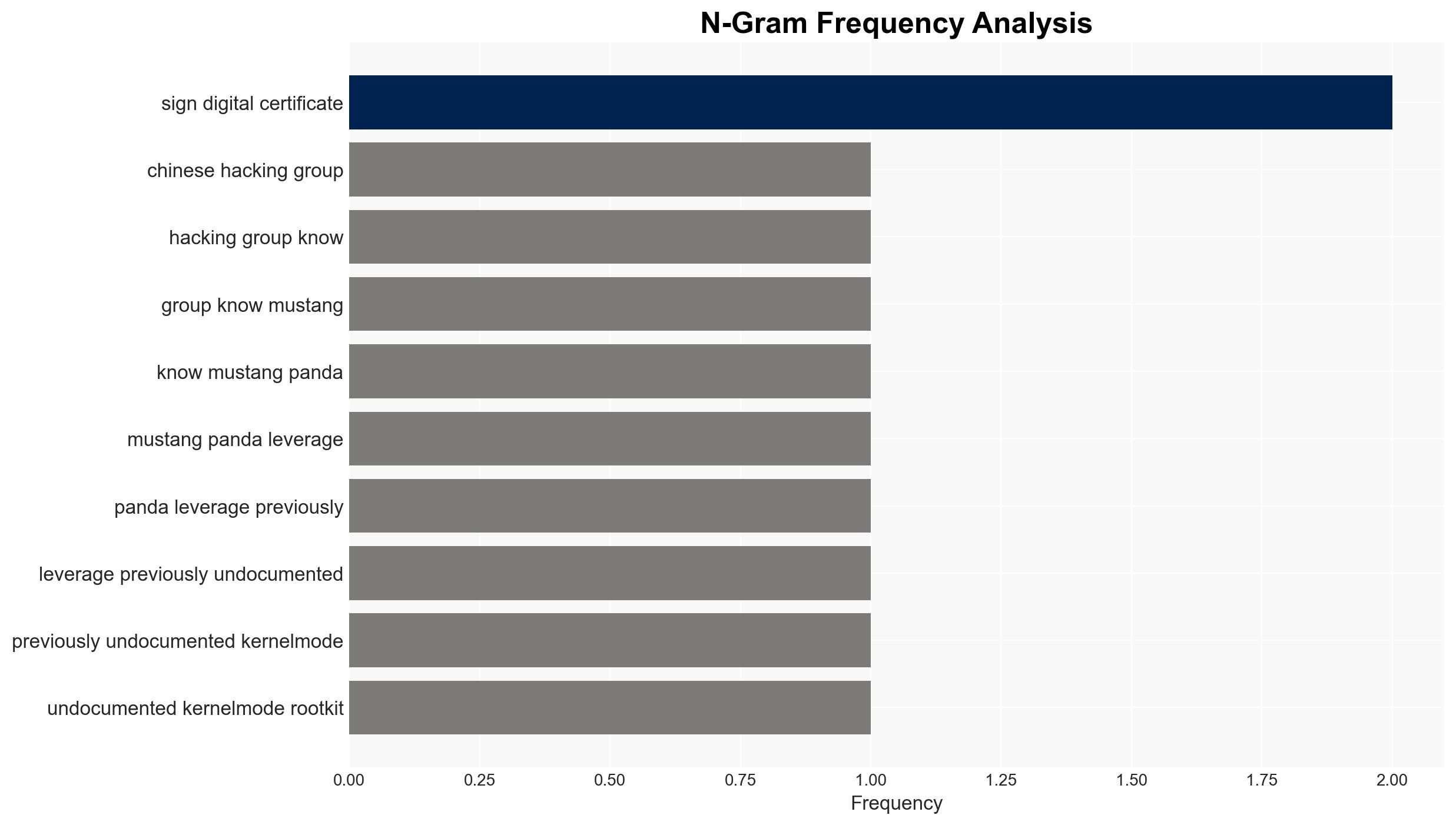
Mustang Panda, a Chinese hacking group, has deployed a sophisticated cyber-espionage campaign using a signed kernel-mode rootkit to deliver the TONESHELL backdoor, primarily targeting government entities in Southeast and East Asia. The use of a stolen digital certificate indicates a high level of operational security and capability. This development poses a significant threat to regional cybersecurity with moderate confidence in the assessment due to incomplete information on the initial access vector.
2. Competing Hypotheses
- Hypothesis A: Mustang Panda is using a stolen digital certificate to conduct targeted cyber-espionage operations against Southeast Asian governments. This is supported by the use of a known certificate and previous targeting patterns, but the initial access vector remains unclear.
- Hypothesis B: The campaign is a false flag operation by another actor aiming to implicate Mustang Panda, leveraging their known tactics and tools. This is less supported due to the consistent use of Mustang Panda’s known infrastructure and tools.
- Assessment: Hypothesis A is currently better supported due to the alignment with Mustang Panda’s historical activities and the use of their established tools and infrastructure. Confirmation of the initial access vector could further solidify this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The digital certificate was stolen or leaked; Mustang Panda is the sole actor behind the campaign; the targets are primarily government entities in Southeast Asia.
- Information Gaps: The exact method of initial access; the full scope of targeted entities; potential involvement of other threat actors.
- Bias & Deception Risks: Potential confirmation bias due to historical attribution to Mustang Panda; risk of misattribution if the campaign is a false flag operation.
4. Implications and Strategic Risks
This development could exacerbate regional tensions and lead to increased cybersecurity measures among Southeast Asian nations. The use of sophisticated cyber tools may prompt a reevaluation of existing security protocols.
- Political / Geopolitical: Potential for diplomatic tensions between China and affected Southeast Asian countries.
- Security / Counter-Terrorism: Increased vigilance and potential retaliatory cyber operations by affected states.
- Cyber / Information Space: Heightened cybersecurity awareness and potential for increased cyber defense collaboration in the region.
- Economic / Social: Possible economic impacts due to disrupted governmental operations and increased cybersecurity spending.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of government networks in Southeast Asia; share threat intelligence with regional partners; verify the integrity of digital certificates.
- Medium-Term Posture (1–12 months): Develop regional cybersecurity partnerships; invest in advanced threat detection and response capabilities; conduct joint cybersecurity exercises.
- Scenario Outlook:
- Best: Successful attribution and mitigation lead to strengthened regional cybersecurity.
- Worst: Escalation of cyber-attacks results in significant political and economic instability.
- Most-Likely: Continued low-level cyber-espionage with incremental improvements in regional cybersecurity defenses.
6. Key Individuals and Entities
- Mustang Panda (Chinese hacking group)
- Guangzhou Kingteller Technology Co., Ltd (Chinese company)
- Kaspersky (Russian cybersecurity company)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, Southeast Asia, digital certificates, Mustang Panda, regional security, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us