Romania’s Oltenia Energy Complex suffers ransomware attack, disrupting IT systems and operations
Published on: 2025-12-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Romanian energy provider hit by Gentlemen ransomware attack
1. BLUF (Bottom Line Up Front)
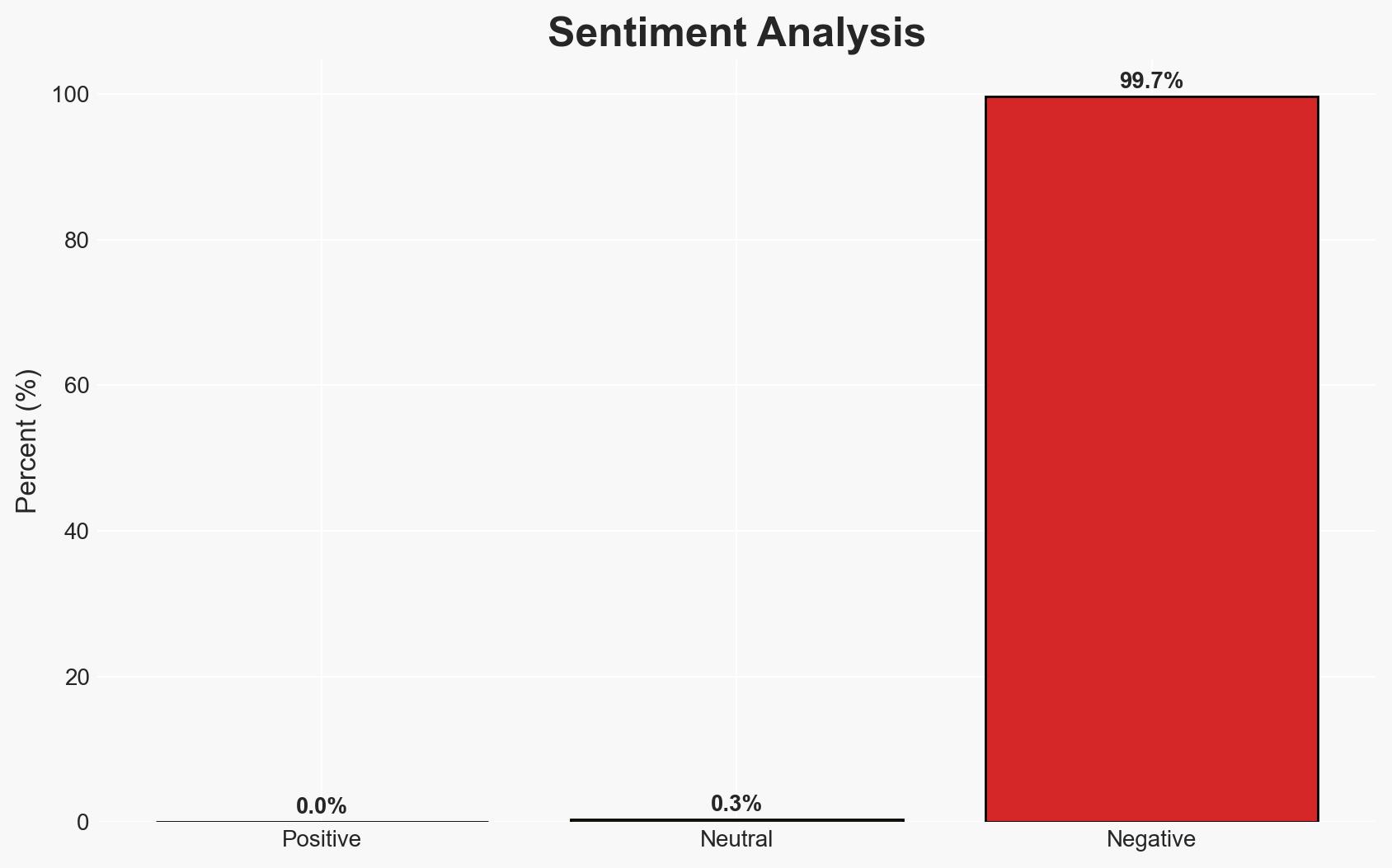
The Oltenia Energy Complex, a major Romanian energy provider, was targeted by the Gentlemen ransomware group, impacting its IT infrastructure but not the national energy system. The attack highlights vulnerabilities in critical infrastructure. The most likely hypothesis is that the attack was financially motivated, with moderate confidence in this assessment.
2. Competing Hypotheses
- Hypothesis A: The ransomware attack was financially motivated, aiming to extract a ransom from Oltenia Energy Complex. This is supported by the ransomware group’s known tactics of encrypting files and negotiating ransoms. Key uncertainties include whether data was exfiltrated before encryption.
- Hypothesis B: The attack was part of a coordinated effort to disrupt Romania’s critical infrastructure, potentially by a state-sponsored actor. This is contradicted by the lack of evidence of broader strategic disruption and the group’s history of financially motivated attacks.
- Assessment: Hypothesis A is currently better supported due to the Gentlemen group’s established pattern of financially motivated attacks. Indicators that could shift this judgment include evidence of data exfiltration for strategic purposes or links to state-sponsored actors.
3. Key Assumptions and Red Flags
- Assumptions: The ransomware group operates independently and is primarily financially motivated; Oltenia Energy Complex’s backups are intact and will enable full recovery; Romanian authorities have the capacity to investigate and respond effectively.
- Information Gaps: The extent of data exfiltration, if any; the specific vulnerabilities exploited for initial access; the current status of ransom negotiations.
- Bias & Deception Risks: Potential bias in underestimating the strategic intent of the attackers; reliance on open-source reporting which may omit classified insights.
4. Implications and Strategic Risks
This incident underscores the vulnerability of critical infrastructure to cyber threats and may embolden other threat actors. It could lead to increased scrutiny and regulatory pressure on energy providers to enhance cybersecurity measures.
- Political / Geopolitical: Potential for increased tensions if linked to state-sponsored actors; could prompt international cooperation on cybersecurity.
- Security / Counter-Terrorism: Highlights the need for enhanced protective measures for critical infrastructure; could influence threat assessments and resource allocation.
- Cyber / Information Space: May lead to increased cyber defense initiatives and information sharing among energy sector stakeholders.
- Economic / Social: Short-term operational disruptions could affect economic stability; public confidence in infrastructure security may be shaken.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Oltenia Energy Complex’s networks; support ongoing investigations; engage with international cyber defense partners.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular cybersecurity audits and incident response exercises; foster public-private partnerships for threat intelligence sharing.
- Scenario Outlook:
- Best: Full recovery with no data exfiltration; improved cybersecurity posture.
- Worst: Data exfiltration leads to further attacks or strategic exploitation.
- Most-Likely: Recovery with minor data loss; increased cybersecurity measures implemented.
6. Key Individuals and Entities
- Oltenia Energy Complex
- Gentlemen ransomware group
- National Cyber Security Directorate
- Directorate for Investigating Organized Crime and Terrorism (DIICOT)
- Ministry of Energy
7. Thematic Tags
cybersecurity, ransomware, critical infrastructure, energy sector, Romania, cybercrime, incident response
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us