Severe Vulnerability Discovered in 70,000 XSpeeder Devices as Manufacturer Fails to Respond to Warning
Published on: 2025-12-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Critical 0day flaw Exposes 70k XSpeeder Devices as Vendor Ignores Alert
1. BLUF (Bottom Line Up Front)
A critical zero-day vulnerability in XSpeeder devices exposes 70,000 systems to potential exploitation, with the vendor unresponsive to remediation efforts. This situation poses significant risks to industrial and branch environments, with moderate confidence in the assessment that the vulnerability will remain unpatched in the near term, increasing the likelihood of exploitation.
2. Competing Hypotheses
- Hypothesis A: XSpeeder’s lack of response is due to internal resource constraints or prioritization issues. Supporting evidence includes the absence of a patch despite prolonged outreach. Contradicting evidence could be a sudden release of a patch or advisory.
- Hypothesis B: XSpeeder’s inaction is a deliberate strategy, possibly influenced by external pressures or a calculated risk assessment. Supporting evidence includes the complete lack of response over seven months. Contradicting evidence might include any future engagement or communication from XSpeeder.
- Assessment: Hypothesis A is currently better supported, as resource constraints or prioritization issues are common in vendor responses to vulnerabilities. Key indicators that could shift this judgment include any communication from XSpeeder or evidence of external influence.
3. Key Assumptions and Red Flags
- Assumptions: XSpeeder is aware of the vulnerability; the vulnerability remains unpatched; external actors have not yet widely exploited the vulnerability.
- Information Gaps: XSpeeder’s internal decision-making processes; potential communications between XSpeeder and external actors; the current extent of exploitation.
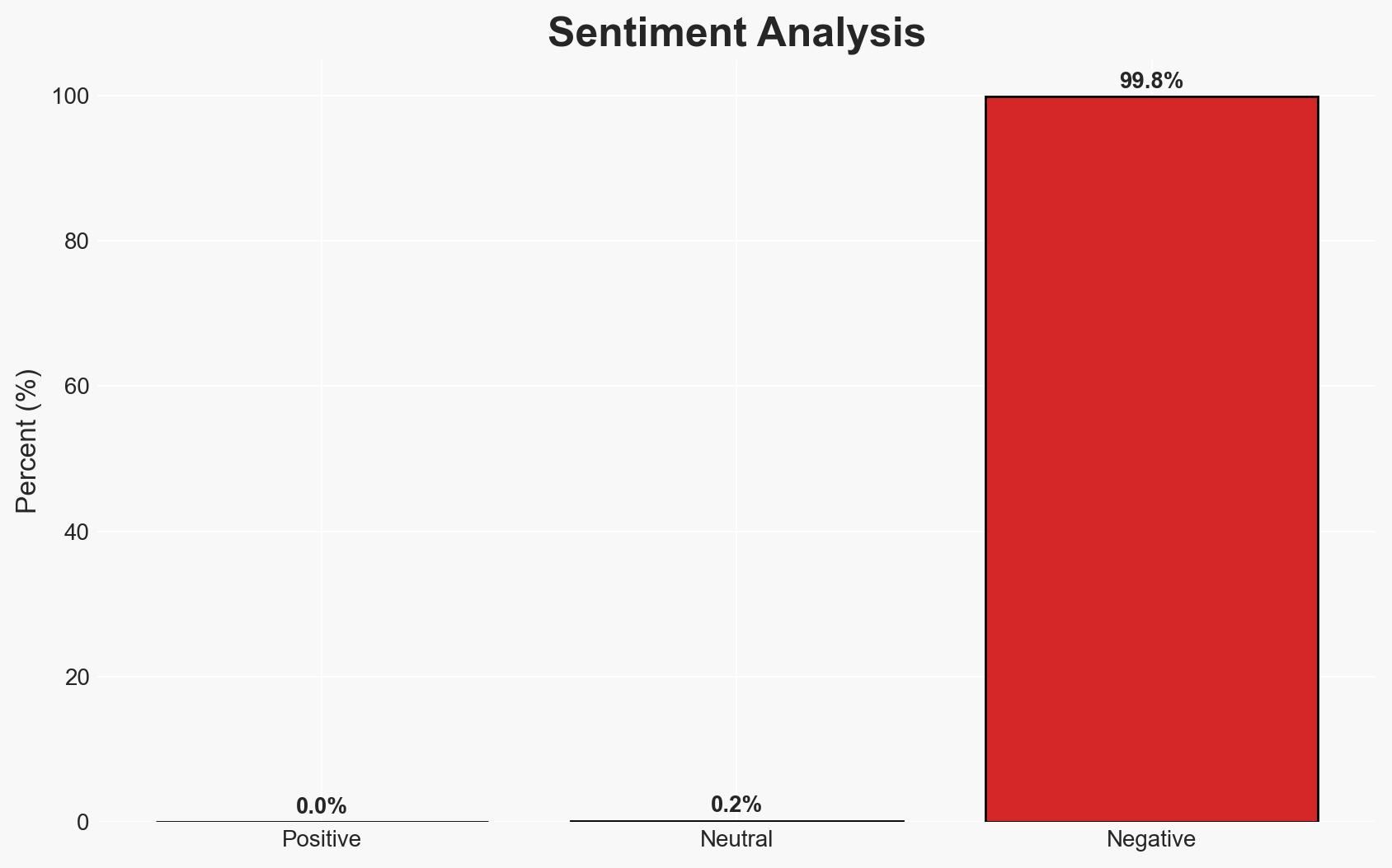
- Bias & Deception Risks: Potential bias in reporting from pwn.ai due to vested interests; lack of independent verification of the vulnerability’s impact.
4. Implications and Strategic Risks
The unpatched vulnerability in XSpeeder devices could lead to significant security breaches, affecting industrial operations and data integrity. Over time, this could escalate into broader geopolitical tensions if linked to state-sponsored activities.
- Political / Geopolitical: Potential for increased scrutiny on Chinese technology vendors; risk of diplomatic tensions if exploited by state actors.
- Security / Counter-Terrorism: Increased vulnerability of critical infrastructure; potential exploitation by terrorist groups for disruptive purposes.
- Cyber / Information Space: Heightened risk of cyber espionage and data breaches; possible increase in AI-driven vulnerability discovery and exploitation.
- Economic / Social: Potential economic impact on businesses relying on XSpeeder devices; erosion of trust in technology vendors.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage organizations using XSpeeder devices to implement network segmentation and monitoring; engage with cybersecurity firms for threat assessments.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity researchers for early vulnerability detection; invest in resilience measures for critical infrastructure.
- Scenario Outlook:
- Best: XSpeeder releases a patch, mitigating the threat.
- Worst: Widespread exploitation leads to significant industrial disruptions.
- Most-Likely: Continued exposure with sporadic exploitation incidents, prompting gradual vendor response.
6. Key Individuals and Entities
- XSpeeder (Chinese vendor)
- pwn.ai (Research firm)
7. Thematic Tags
cybersecurity, zero-day vulnerability, industrial security, AI in cybersecurity, vendor response, Chinese technology, critical infrastructure
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us