Cybersecurity Predictions for 2026: Anticipating Subtle Attacks and Evolving Threat Landscapes
Published on: 2025-12-30
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cyber experts pinpoint what to look out for in 2026
1. BLUF (Bottom Line Up Front)
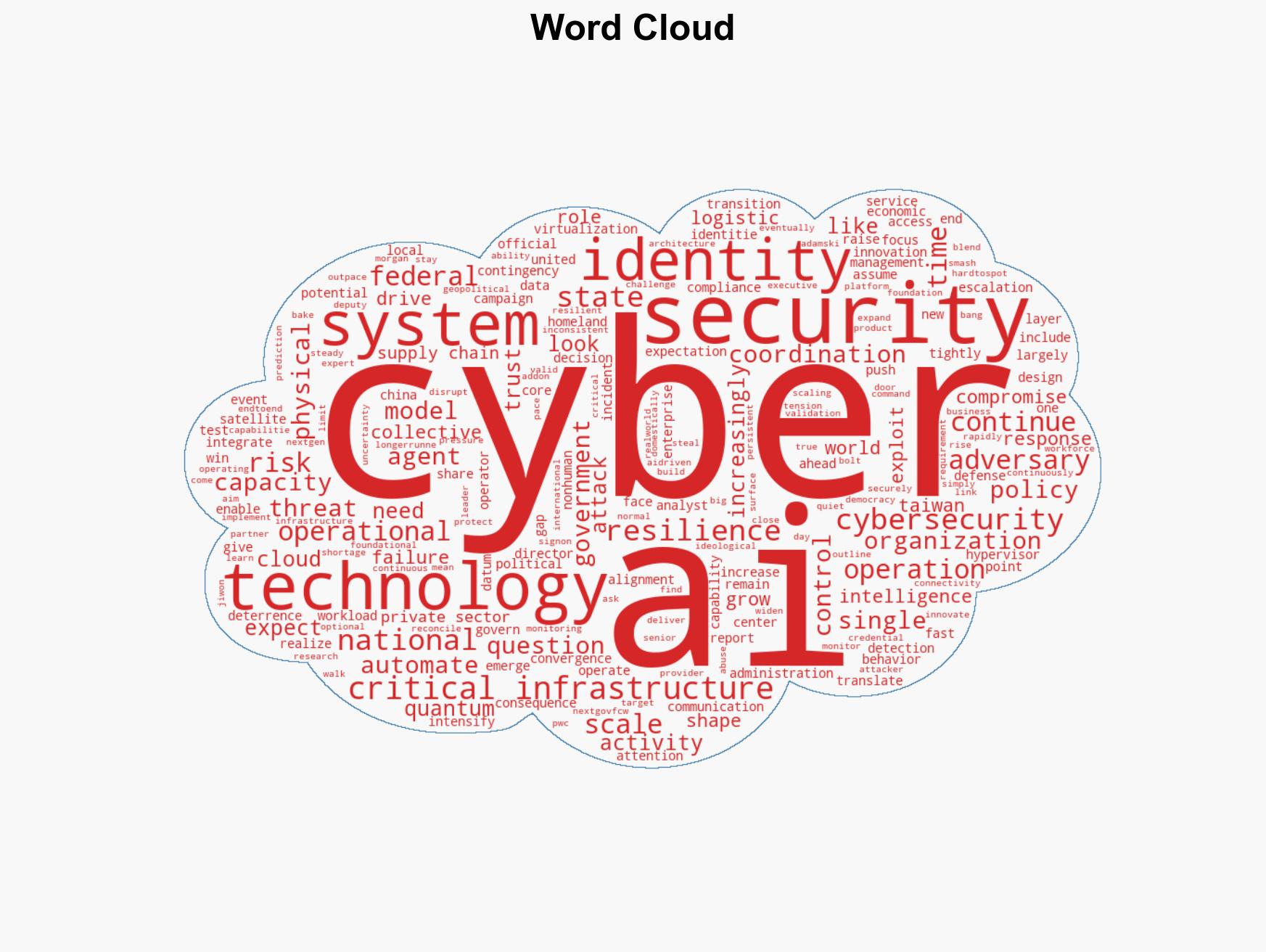
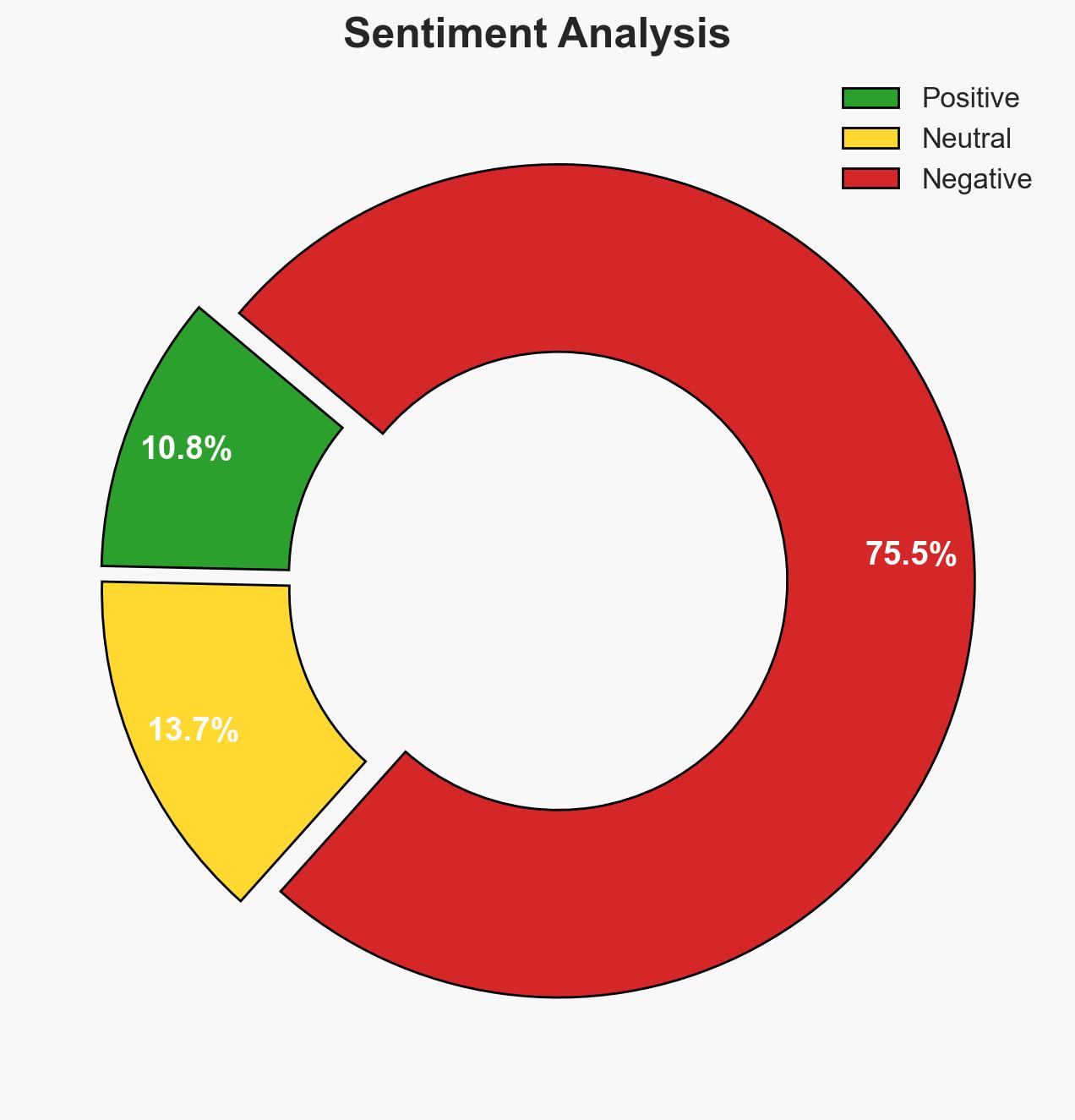
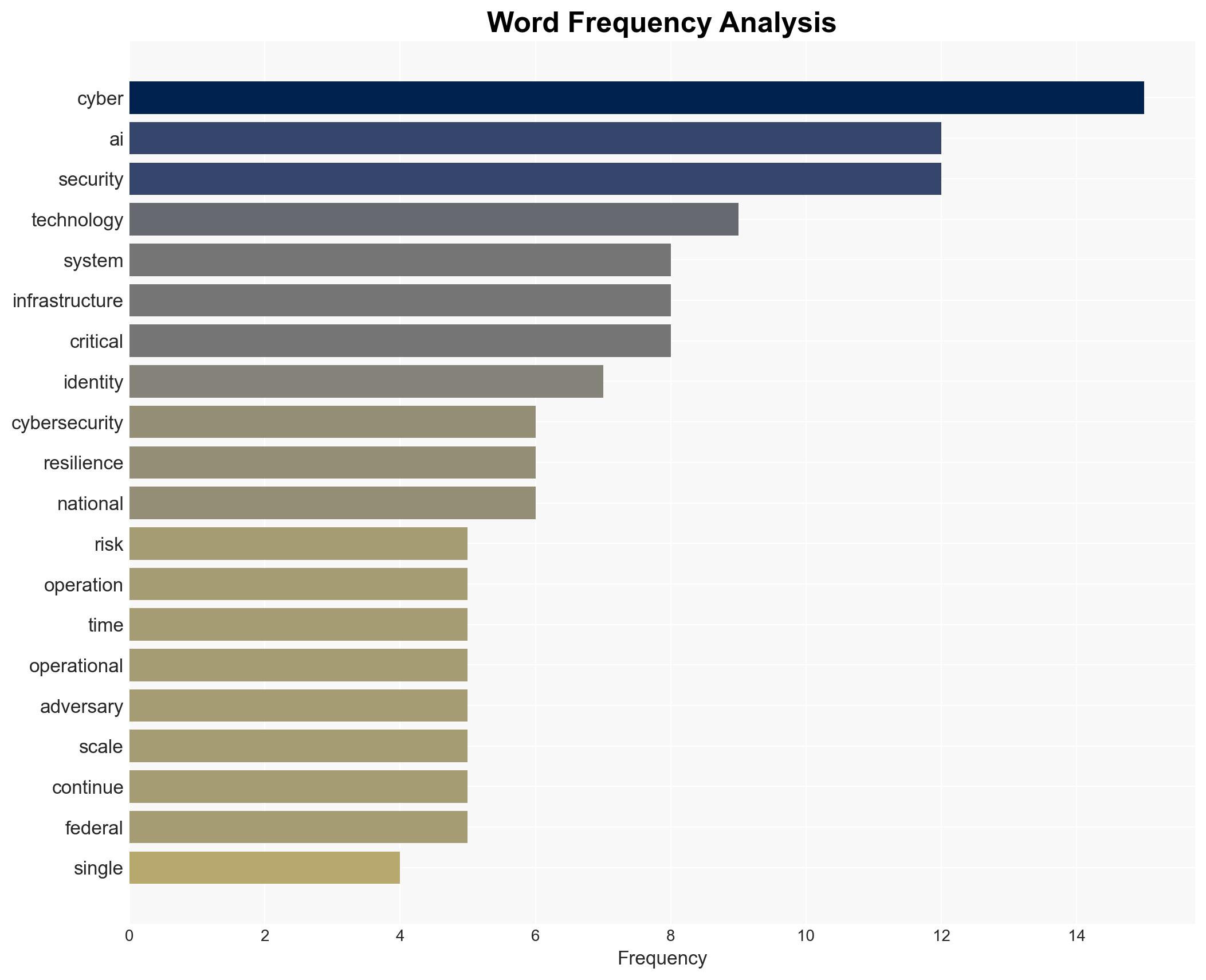
In 2026, cyber threats are expected to evolve into more subtle and prolonged campaigns leveraging valid credentials and identity systems, with a significant focus on disrupting real-world services. The expansion of technological infrastructure will increase the attack surface, challenging organizations to integrate security into their core operations. The United States faces challenges in aligning domestic cyber resilience efforts with international partners. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Cyber threats in 2026 will primarily involve subtle, long-term campaigns exploiting identity systems and technological convergence. This is supported by expert predictions of increased use of valid credentials and the growing attack surface. However, the exact nature and scale of these threats remain uncertain.
- Hypothesis B: Cyber threats will continue to focus on high-impact, short-term attacks targeting critical infrastructure. This hypothesis is less supported due to the lack of specific evidence indicating a shift away from the predicted subtle, long-term campaigns.
- Assessment: Hypothesis A is currently better supported due to expert insights on the evolving nature of cyber threats and the expanding technological landscape. Indicators such as increased geopolitical tensions and technological advancements could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Cyber adversaries will continue to innovate and exploit identity systems; technological advancements will outpace security measures; geopolitical tensions will influence cyber operations.
- Information Gaps: Specific details on adversaries’ capabilities and intentions; effectiveness of current security measures; potential technological breakthroughs in security.
- Bias & Deception Risks: Potential bias in expert predictions; reliance on open-source information; adversaries may engage in deception to mask true capabilities or intentions.
4. Implications and Strategic Risks
The evolution of cyber threats in 2026 could significantly impact global security dynamics and economic stability. The integration of security into technological development is crucial to mitigate risks.
- Political / Geopolitical: Increased cyber operations could escalate geopolitical tensions, particularly among major powers.
- Security / Counter-Terrorism: The threat landscape may become more complex, requiring enhanced coordination among security agencies.
- Cyber / Information Space: Greater emphasis on identity systems and AI-driven detection will be necessary to counter sophisticated threats.
- Economic / Social: Disruptions to critical infrastructure could have widespread economic and social consequences, affecting public trust and stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of identity systems; initiate cross-sector collaboration to share threat intelligence.
- Medium-Term Posture (1–12 months): Develop integrated security frameworks; invest in workforce training and technological innovation.
- Scenario Outlook:
- Best: Effective international cooperation leads to robust cyber defenses.
- Worst: Major cyber incidents cause significant disruptions to critical infrastructure.
- Most-Likely: Continued evolution of cyber threats with incremental improvements in security resilience.
6. Key Individuals and Entities
- Morgan Adamski, former executive director at U.S. Cyber Command
- Jiwon Ma, senior policy analyst at the Foundation for Defense of Democracies’ Center on Cyber and Technology Innovation
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, identity systems, geopolitical tensions, critical infrastructure, technological convergence, cyber resilience, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us