AFP reports Bondi attack suspects acted independently, with no links to larger terrorist networks.
Published on: 2025-12-30
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: AFP believes Bondi attack gunmen operated alone
1. BLUF (Bottom Line Up Front)
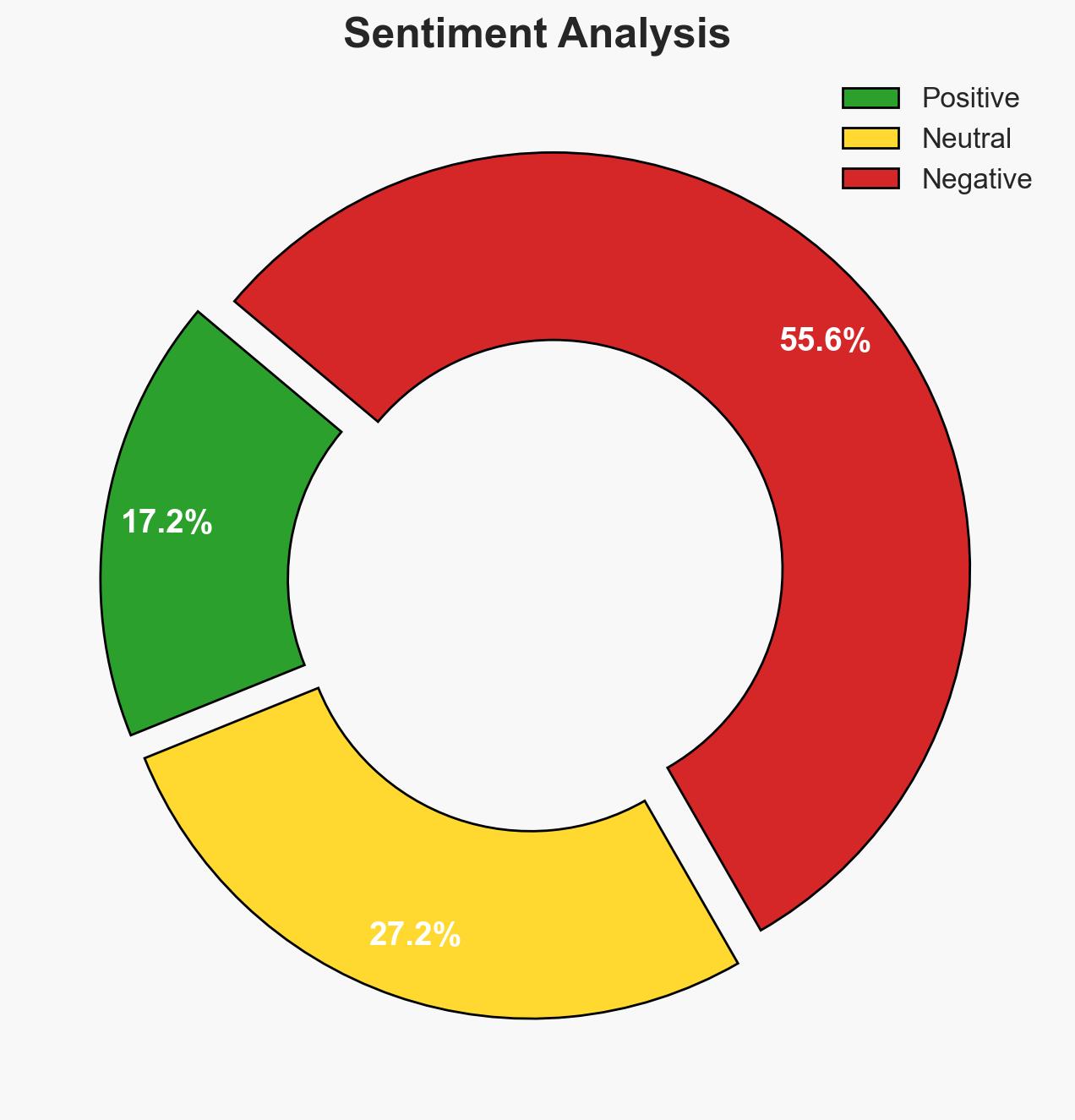
The Australian Federal Police (AFP) assesses that the Bondi attack gunmen acted independently, without evidence of broader terrorist cell involvement. The investigation is ongoing, with a focus on potential influences from hate preachers. This assessment is made with moderate confidence due to limited available evidence and ongoing investigations.
2. Competing Hypotheses
- Hypothesis A: The gunmen acted alone without external direction or support. This is supported by the lack of evidence of cell involvement or training during their time in the Philippines. However, uncertainties remain regarding their motivations and potential influences.
- Hypothesis B: The gunmen were influenced or directed by external entities, possibly through ideological indoctrination by hate preachers. This is contradicted by the AFP’s current findings but remains plausible given the investigation into hate preachers.
- Assessment: Hypothesis A is currently better supported due to the AFP’s lack of evidence for external direction. Key indicators that could shift this judgment include new evidence of communication with extremist networks or financial/logistical support.
3. Key Assumptions and Red Flags
- Assumptions: The AFP’s intelligence and investigative processes are thorough and unbiased; the gunmen’s actions were ideologically motivated; hate preachers have a measurable influence on potential attackers.
- Information Gaps: Details on the gunmen’s activities and contacts during their time in the Philippines; potential communications with extremist networks; comprehensive analysis of hate preachers’ influence.
- Bias & Deception Risks: Potential cognitive bias in focusing on lone-actor hypothesis; source bias from relying on limited intelligence; risk of deception by the gunmen or their associates to obscure external influences.
4. Implications and Strategic Risks
The development could influence national security policies and community relations, particularly regarding hate speech and counter-terrorism strategies.
- Political / Geopolitical: Potential for increased legislative measures against hate speech; diplomatic considerations with the Philippines regarding counter-terrorism cooperation.
- Security / Counter-Terrorism: Heightened focus on lone-actor threats and hate speech as a radicalization vector; potential for copycat attacks.
- Cyber / Information Space: Monitoring of online hate speech and extremist content may increase; potential for cyber operations targeting hate networks.
- Economic / Social: Community tensions may rise, impacting social cohesion; economic impacts from increased security measures and potential tourism decline.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of hate speech and extremist content; strengthen community engagement to mitigate tensions; continue intelligence sharing with international partners.
- Medium-Term Posture (1–12 months): Develop resilience measures against lone-actor threats; expand partnerships with community leaders to counter radicalization; invest in capability development for hate speech detection.
- Scenario Outlook:
- Best: Successful prosecution and prevention of further attacks, leading to improved community relations.
- Worst: Failure to address root causes, resulting in further attacks and societal division.
- Most-Likely: Continued focus on lone-actor threats with incremental improvements in counter-terrorism strategies.
6. Key Individuals and Entities
- Naveed Akram – Alleged attacker
- Sajid Akram – Deceased alleged attacker
- Australian Federal Police (AFP)
- Hate preachers – Under investigation
- Prime Minister Anthony Albanese – Announced hate speech reforms
7. Thematic Tags
Counter-Terrorism, lone-actor threats, hate speech, radicalization, law enforcement, community relations, intelligence analysis
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us