Police find no links to larger terrorist organization in Bondi Beach mass shooting investigation
Published on: 2025-12-30
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: No sign of broader terrorist cell behind Bondi Beach attack police say
1. BLUF (Bottom Line Up Front)
The investigation into the Bondi Beach attack suggests that the accused individuals acted independently, with no evidence of a broader terrorist cell involvement. The primary hypothesis is that the attack was inspired by ISIS but not directed by them. This assessment affects national security and counter-terrorism strategies, with a moderate confidence level due to limited information on the suspects’ motivations and activities.
2. Competing Hypotheses
- Hypothesis A: The accused acted independently, inspired by ISIS ideology but without direct operational support. This is supported by the lack of evidence of training or logistical preparation in the Philippines and the absence of connections to a broader cell.
- Hypothesis B: The accused were part of a covert terrorist network that remains undetected. This is contradicted by the police findings and the logistical challenges foreigners face in receiving training in the region.
- Assessment: Hypothesis A is currently better supported due to the absence of evidence linking the accused to a broader network and the logistical improbability of covert training. Indicators such as new intelligence on connections or communications could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The police investigation is thorough and unbiased; the accused did not receive covert training; the lack of evidence is indicative of reality rather than investigative limitations.
- Information Gaps: Detailed motives for the Philippines visit, potential undisclosed communications or financial transactions, and the full extent of their interactions in the region.
- Bias & Deception Risks: Potential confirmation bias in interpreting the absence of evidence as evidence of absence; possible deception by the accused regarding their activities and intentions.
4. Implications and Strategic Risks
This development may influence national security policies and counter-terrorism strategies, emphasizing the need for vigilance against lone-wolf actors. It could also affect international cooperation on counter-terrorism efforts.
- Political / Geopolitical: Potential strain on Australia-Philippines relations if further evidence emerges, affecting diplomatic and security cooperation.
- Security / Counter-Terrorism: Increased focus on monitoring individuals inspired by extremist ideologies without direct group affiliations.
- Cyber / Information Space: Potential for increased online radicalization efforts targeting vulnerable individuals.
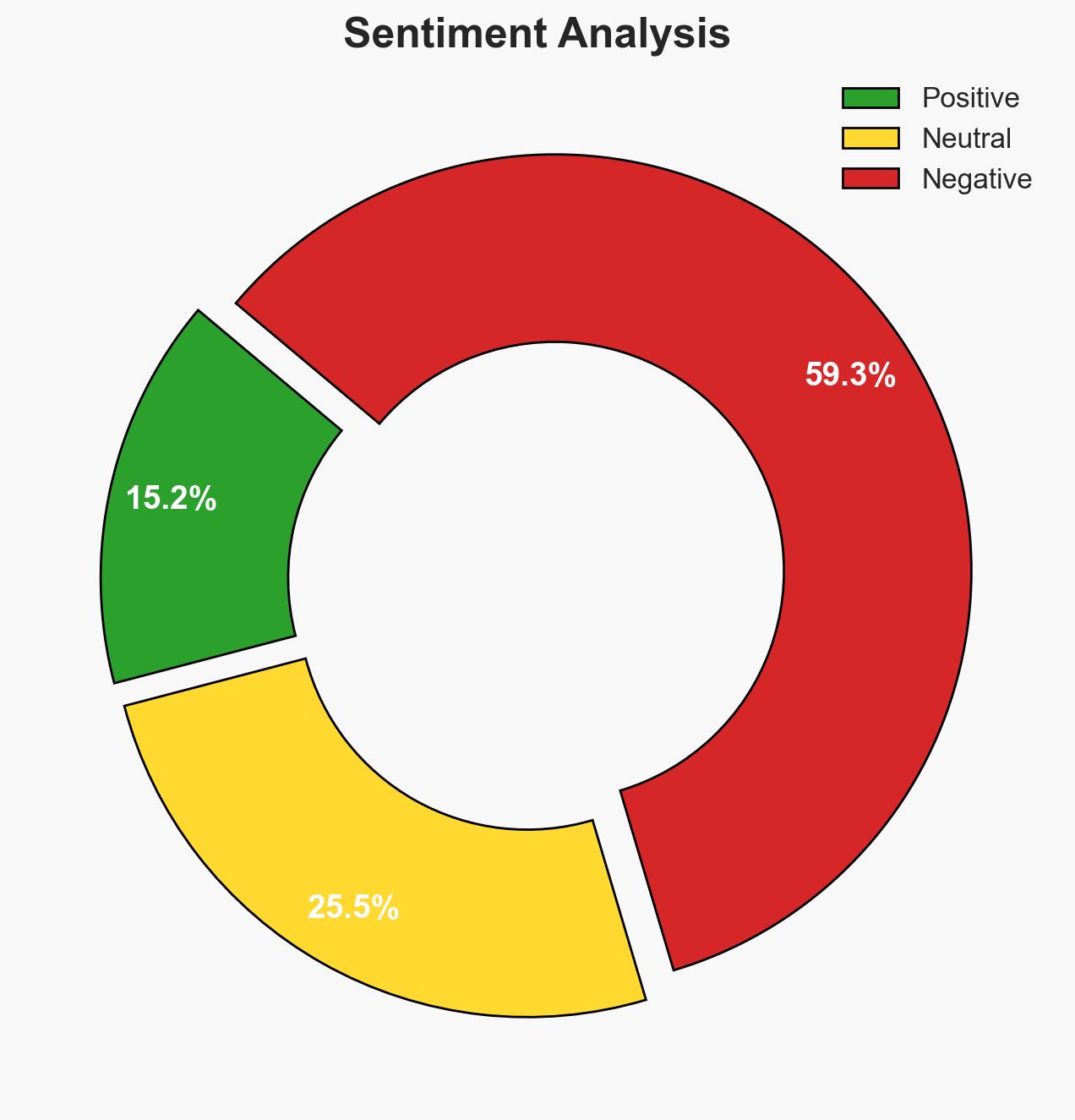
- Economic / Social: Possible impacts on community cohesion and public perception of security, particularly within Jewish and Muslim communities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of individuals with potential extremist sympathies; strengthen community engagement to counter radicalization.
- Medium-Term Posture (1–12 months): Develop partnerships with regional allies to improve intelligence sharing; invest in counter-radicalization programs.
- Scenario Outlook: Best: No further incidents and improved security measures. Worst: Emergence of new evidence indicating broader network involvement. Most-Likely: Continued lone-wolf threats with sporadic incidents.
6. Key Individuals and Entities
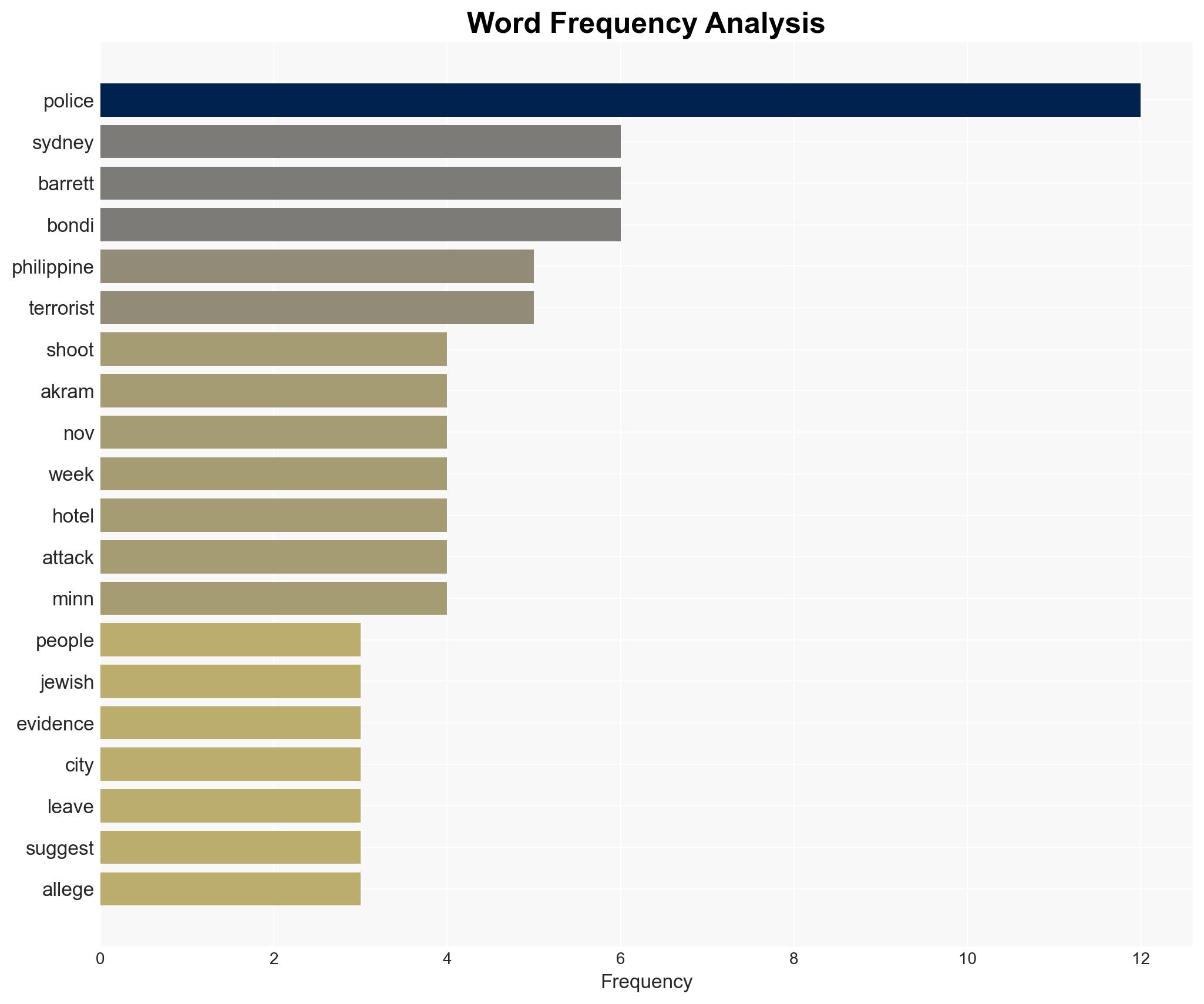
- Sajid Akram
- Naveed Akram
- Australian Federal Police Commissioner Krissy Barrett
- Tom Smith, academic director of the Royal Air Force College
- GV Hotel, Davao City
7. Thematic Tags
Counter-Terrorism, lone-wolf attacks, ISIS influence, international security cooperation, radicalization prevention, Australia-Philippines relations
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us