$35 Million in Stolen Cryptocurrency Linked to 2022 LastPass Data Breach, Traced to Russian Cybercriminals
Published on: 2026-01-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Experts Trace 35m in Stolen Crypto to LastPass Breach
1. BLUF (Bottom Line Up Front)
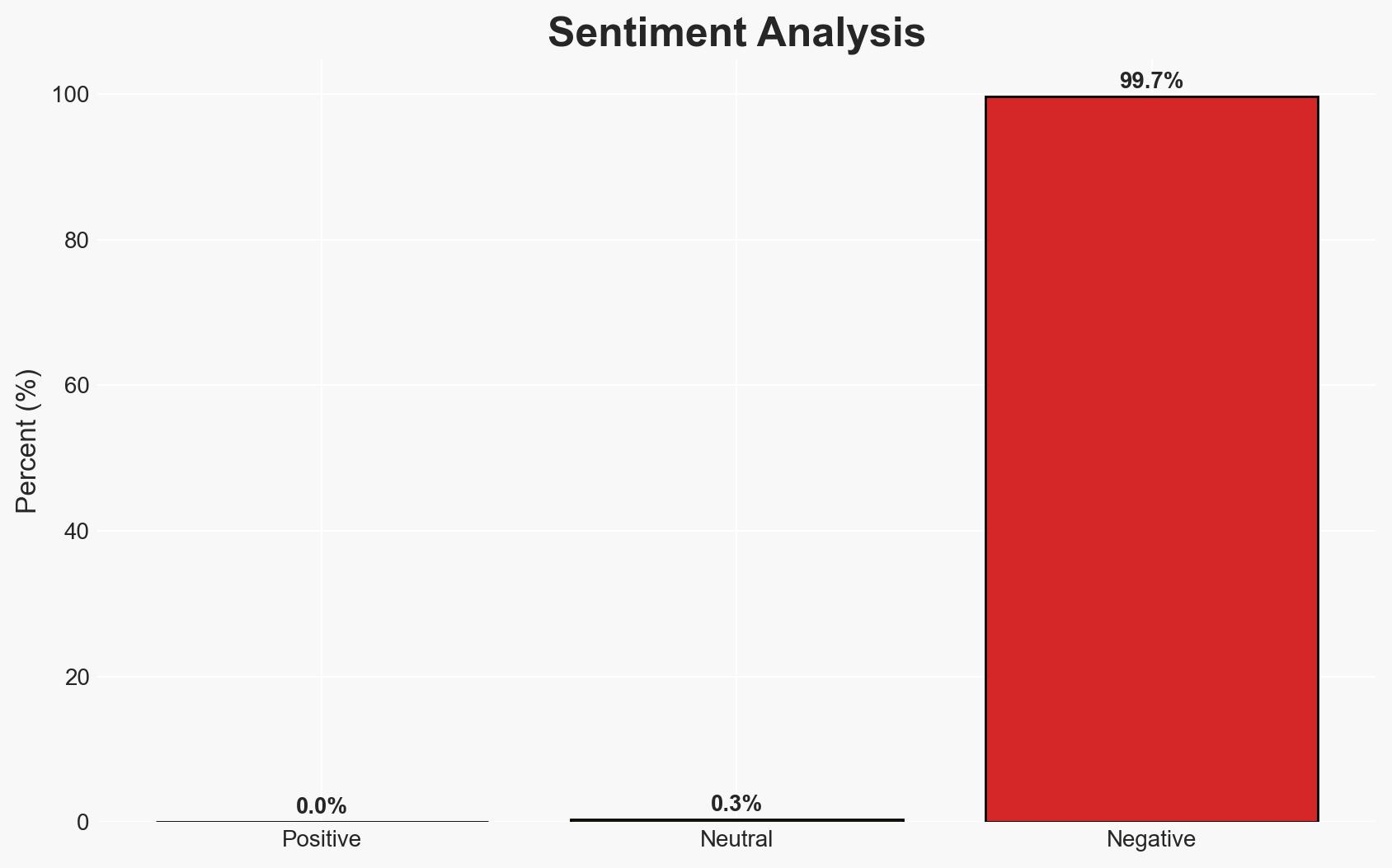
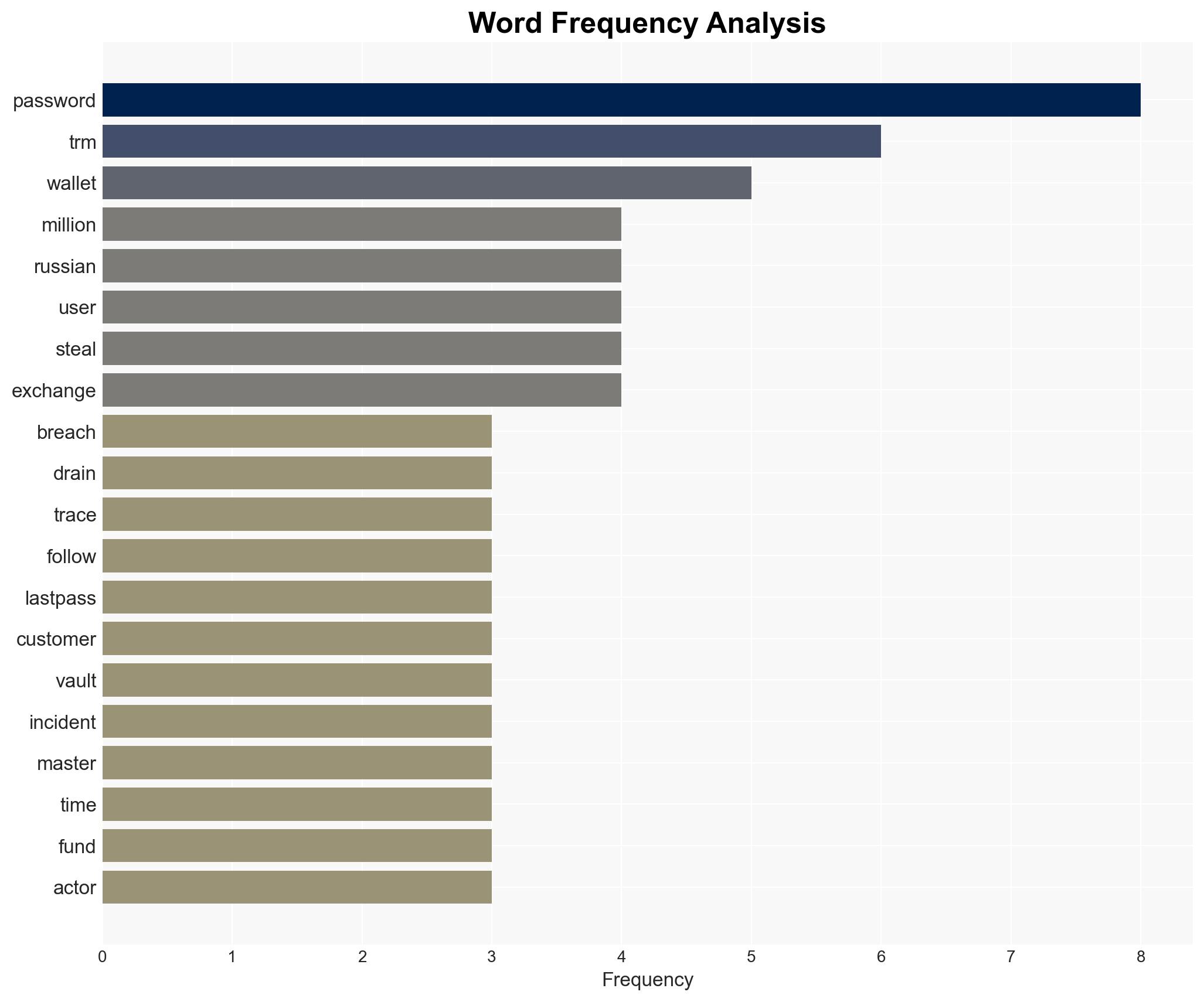
The LastPass data breach has resulted in the theft of $35 million in cryptocurrency, with evidence suggesting Russian cybercriminal involvement. The breach exposed password vaults, leading to long-term vulnerabilities. The most likely hypothesis is that Russian actors exploited these vulnerabilities over several years. Overall confidence in this assessment is moderate, given the reliance on blockchain analysis and the potential for obfuscation techniques.
2. Competing Hypotheses
- Hypothesis A: Russian cybercriminals exploited the LastPass breach to systematically drain cryptocurrency wallets over several years. This is supported by the tracing of stolen funds to Russian exchanges and infrastructure. Key uncertainties include the full extent of the breach and the potential involvement of other actors.
- Hypothesis B: The breach was opportunistically exploited by multiple independent groups, not exclusively Russian, using similar techniques. While Russian exchanges were involved, this does not preclude other actors from participating. Evidence contradicting this includes the consistent tracing to Russian-controlled infrastructure.
- Assessment: Hypothesis A is currently better supported due to the consistent tracing of funds to Russian exchanges and infrastructure. Key indicators that could shift this judgment include evidence of non-Russian actors or alternative financial routes.
3. Key Assumptions and Red Flags
- Assumptions: The breach primarily involved Russian actors; blockchain analysis accurately reflects the flow of funds; LastPass users did not change weak passwords post-breach.
- Information Gaps: Full scope of the breach impact; potential involvement of non-Russian actors; detailed operational methods used by the attackers.
- Bias & Deception Risks: Potential confirmation bias in attributing actions to Russian actors; reliance on proprietary demixing techniques that may not be independently verifiable.
4. Implications and Strategic Risks
The breach highlights ongoing vulnerabilities in digital security and the potential for long-term exploitation by cybercriminals. This could lead to increased scrutiny of password management services and regulatory actions.
- Political / Geopolitical: Potential for increased tensions between Western countries and Russia over cybercrime allegations.
- Security / Counter-Terrorism: Heightened awareness of cyber threats and the need for improved cybersecurity measures.
- Cyber / Information Space: Increased focus on securing digital assets and the role of anonymization services in cybercrime.
- Economic / Social: Potential loss of trust in digital financial systems and increased demand for regulatory oversight.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Russian exchanges; promote user education on password security; collaborate with international partners for intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures for digital asset protection; strengthen partnerships with cybersecurity firms; invest in advanced blockchain analysis capabilities.
- Scenario Outlook:
- Best: Enhanced security measures prevent further breaches, restoring trust in digital platforms.
- Worst: Continued exploitation leads to significant financial losses and geopolitical tensions.
- Most-Likely: Incremental improvements in security with ongoing low-level cybercrime activity.
6. Key Individuals and Entities
- TRM Labs (Blockchain analytics company)
- LastPass (Password management provider)
- Cryptex (Russia-based exchange)
- Audi6 (Russian exchange)
- CoinJoin (Anonymization service)
- Wasabi Wallet (Cryptocurrency wallet service)
7. Thematic Tags
cybersecurity, cryptocurrency theft, Russian cybercrime, blockchain analysis, data breach, digital asset protection, international cooperation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us