Generative AI Enhances Speed and Efficiency of Identity Attacks on Active Directory Systems
Published on: 2026-01-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: How generative AI accelerates identity attacks against Active Directory
1. BLUF (Bottom Line Up Front)
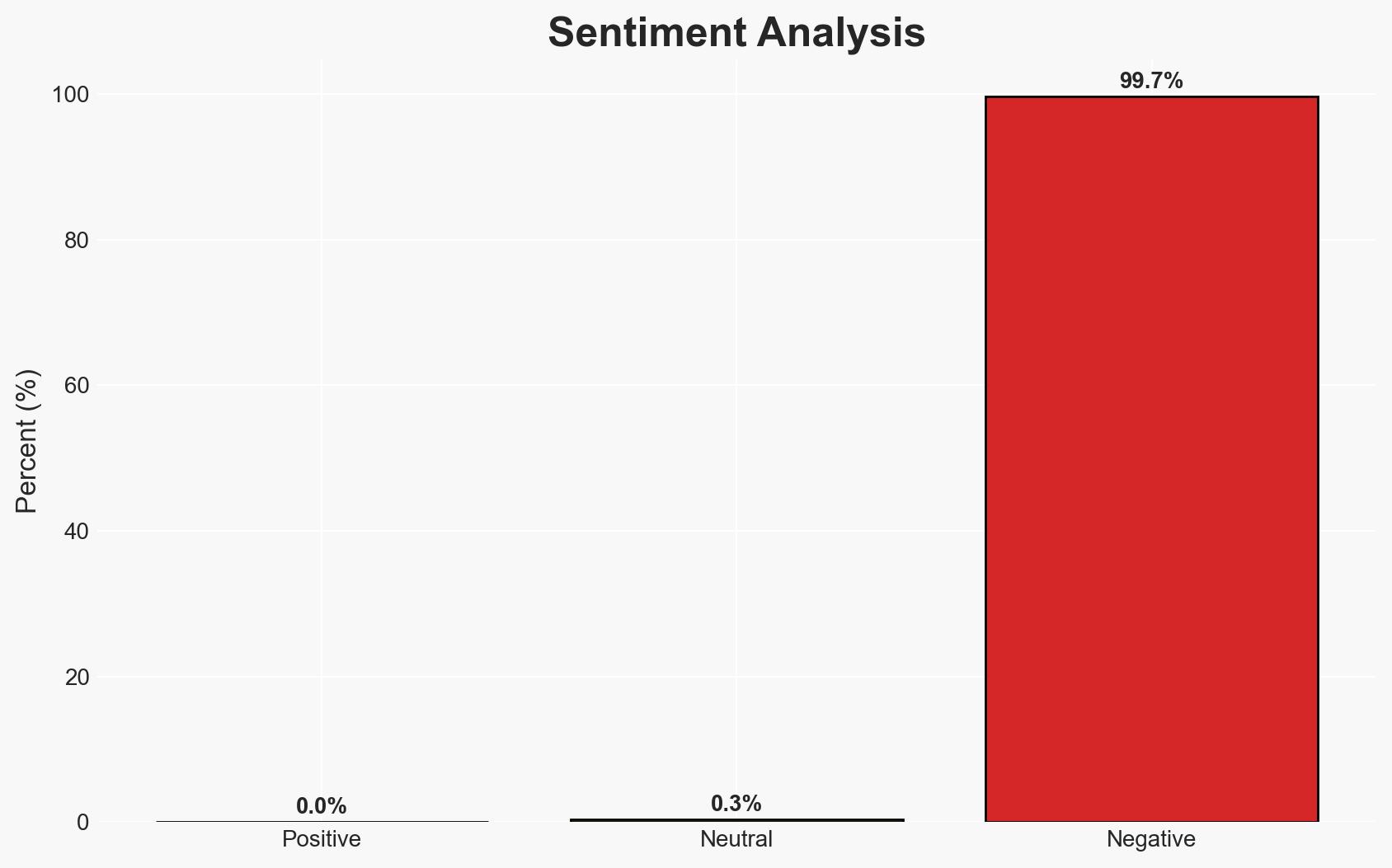
Generative AI is significantly enhancing the speed and effectiveness of identity attacks against Active Directory systems, lowering the technical barriers for attackers and increasing the threat landscape for organizations. This development poses a substantial risk to cybersecurity, with moderate confidence that AI-driven attacks will become more prevalent and sophisticated. Organizations relying on Active Directory are particularly vulnerable.
2. Competing Hypotheses
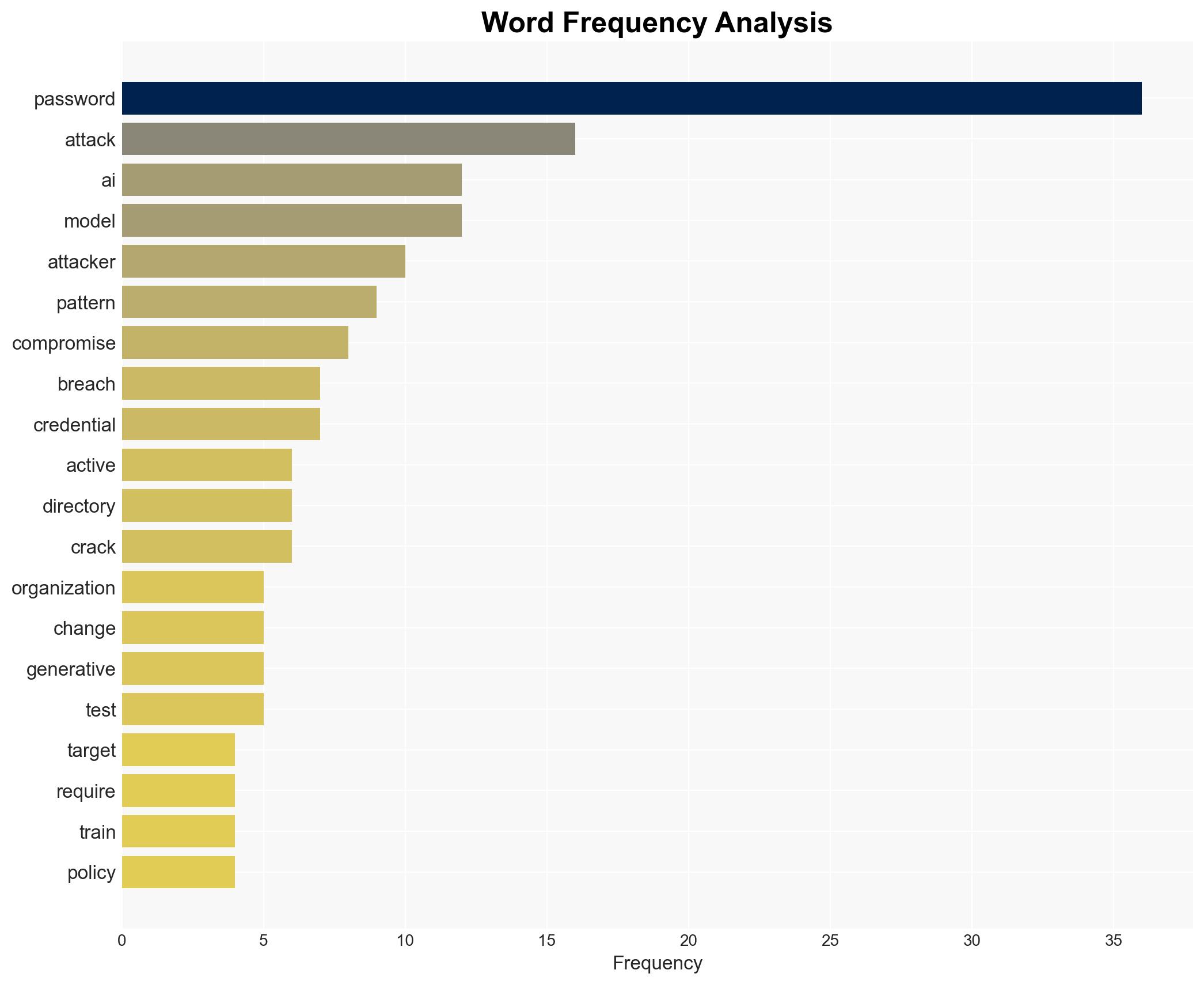
- Hypothesis A: Generative AI is the primary driver of increased efficiency in identity attacks against Active Directory, as evidenced by tools like PassGAN that leverage AI to predict passwords with high accuracy. However, the extent of AI’s role relative to other technological advancements remains uncertain.
- Hypothesis B: The increased efficiency of identity attacks is primarily due to broader access to high-performance computing and not solely due to generative AI. While AI contributes, the democratization of powerful hardware plays a critical role.
- Assessment: Hypothesis A is currently better supported due to the specific capabilities of generative AI in pattern recognition and targeted attacks, as demonstrated by PassGAN’s performance. Indicators such as the rapid evolution of AI models and their application in real-world attacks could further validate this hypothesis.
3. Key Assumptions and Red Flags
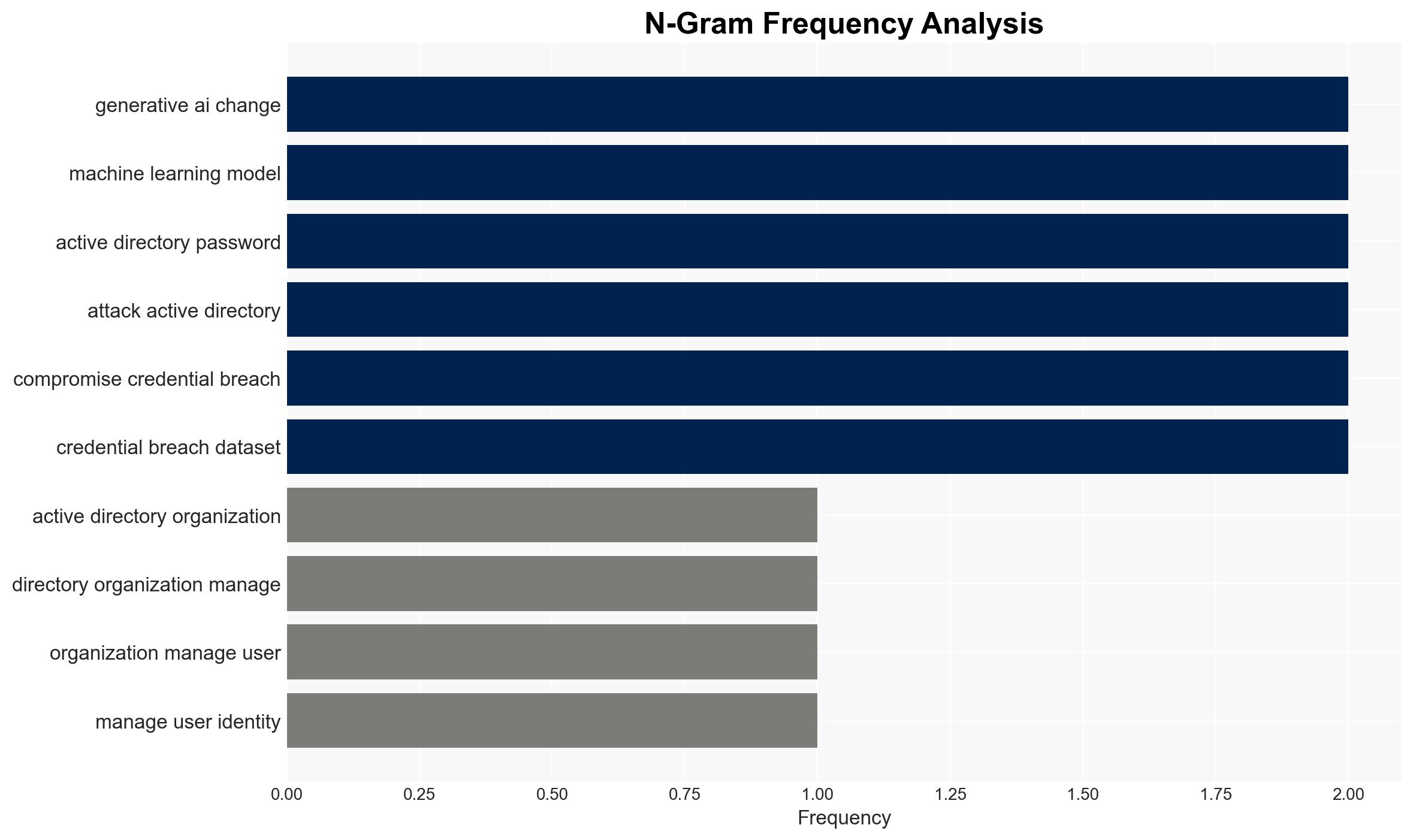
- Assumptions: Organizations continue to rely on Active Directory; AI models will continue to improve in sophistication; attackers have access to necessary computational resources; security measures remain static.
- Information Gaps: Lack of comprehensive data on the prevalence of AI-driven attacks across different sectors; insufficient understanding of defensive measures’ effectiveness against AI-enhanced attacks.
- Bias & Deception Risks: Potential over-reliance on AI capabilities in assessments; source bias from cybersecurity firms promoting AI-related threats; possible exaggeration of AI’s role by adversaries to instill fear.
4. Implications and Strategic Risks
The integration of generative AI into cyberattack methodologies could lead to a paradigm shift in cybersecurity, necessitating new defense strategies and policies. The evolution of these attacks could influence various domains.
- Political / Geopolitical: Increased cyber threats could strain international relations and lead to calls for new cybersecurity treaties or regulations.
- Security / Counter-Terrorism: Enhanced attack capabilities could be exploited by state and non-state actors, complicating defense and response strategies.
- Cyber / Information Space: The sophistication of AI-driven attacks may outpace current cybersecurity measures, leading to increased breaches and data theft.
- Economic / Social: Successful attacks could result in significant financial losses and erode trust in digital systems, impacting economic stability and social cohesion.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of AI-driven attack indicators; update password policies and authentication methods; conduct awareness training for employees.
- Medium-Term Posture (1–12 months): Invest in AI-based defensive technologies; foster partnerships with cybersecurity firms for threat intelligence sharing; enhance incident response capabilities.
- Scenario Outlook:
- Best Case: Organizations adapt quickly, reducing the impact of AI-driven attacks through robust defenses and policies.
- Worst Case: AI-driven attacks become widespread, leading to frequent and severe data breaches.
- Most-Likely: A gradual increase in AI-driven attacks with varying degrees of success, prompting ongoing adaptation in cybersecurity practices.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, generative AI, identity attacks, Active Directory, password cracking, AI-driven threats, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us