Spyware Company Founder Admits Guilt in Uncommon Stalkerware Case, Facing Charges of Hacking and Conspiracy
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
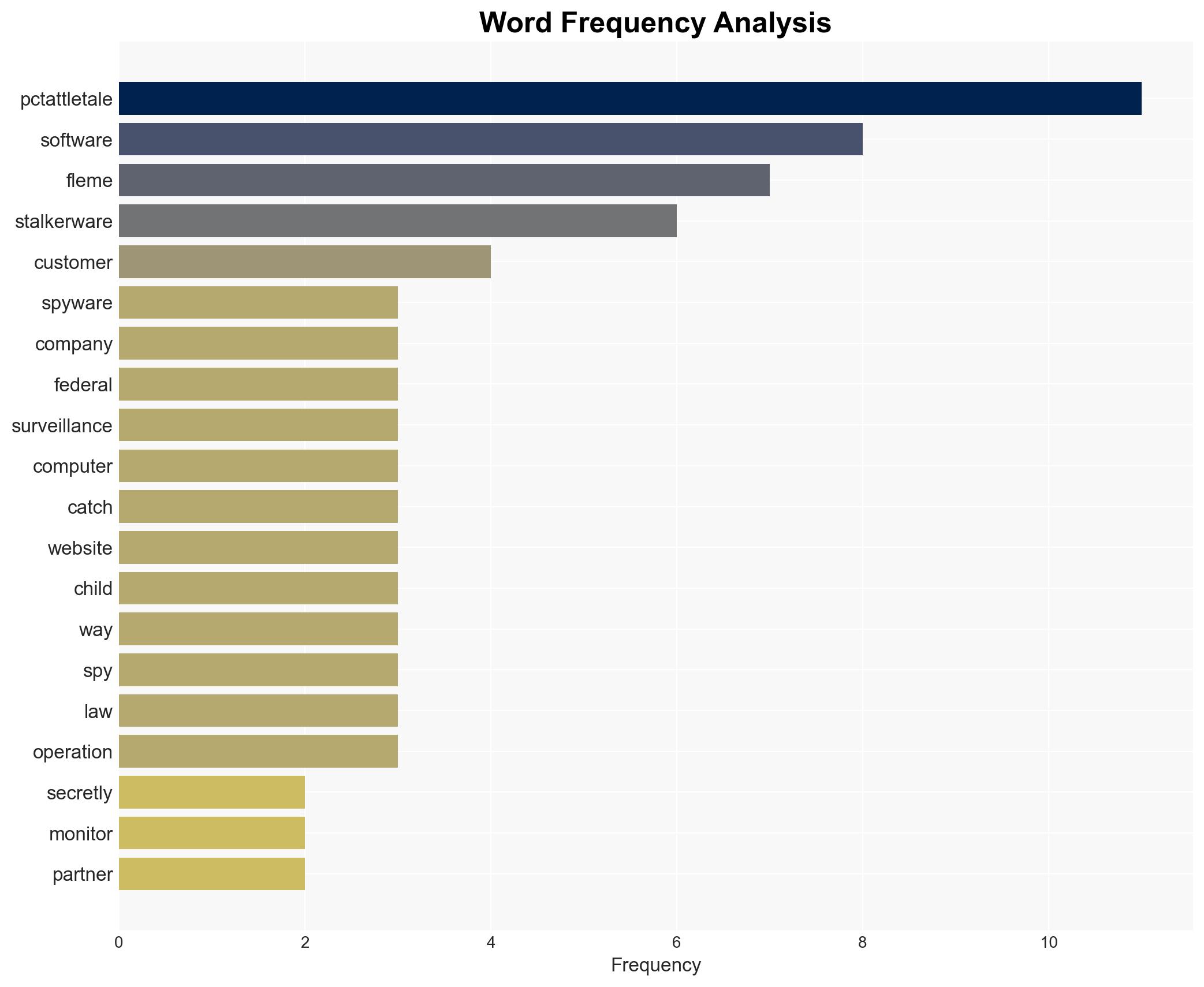
Intelligence Report: pcTattletale founder pleads guilty in rare stalkerware prosecution
1. BLUF (Bottom Line Up Front)
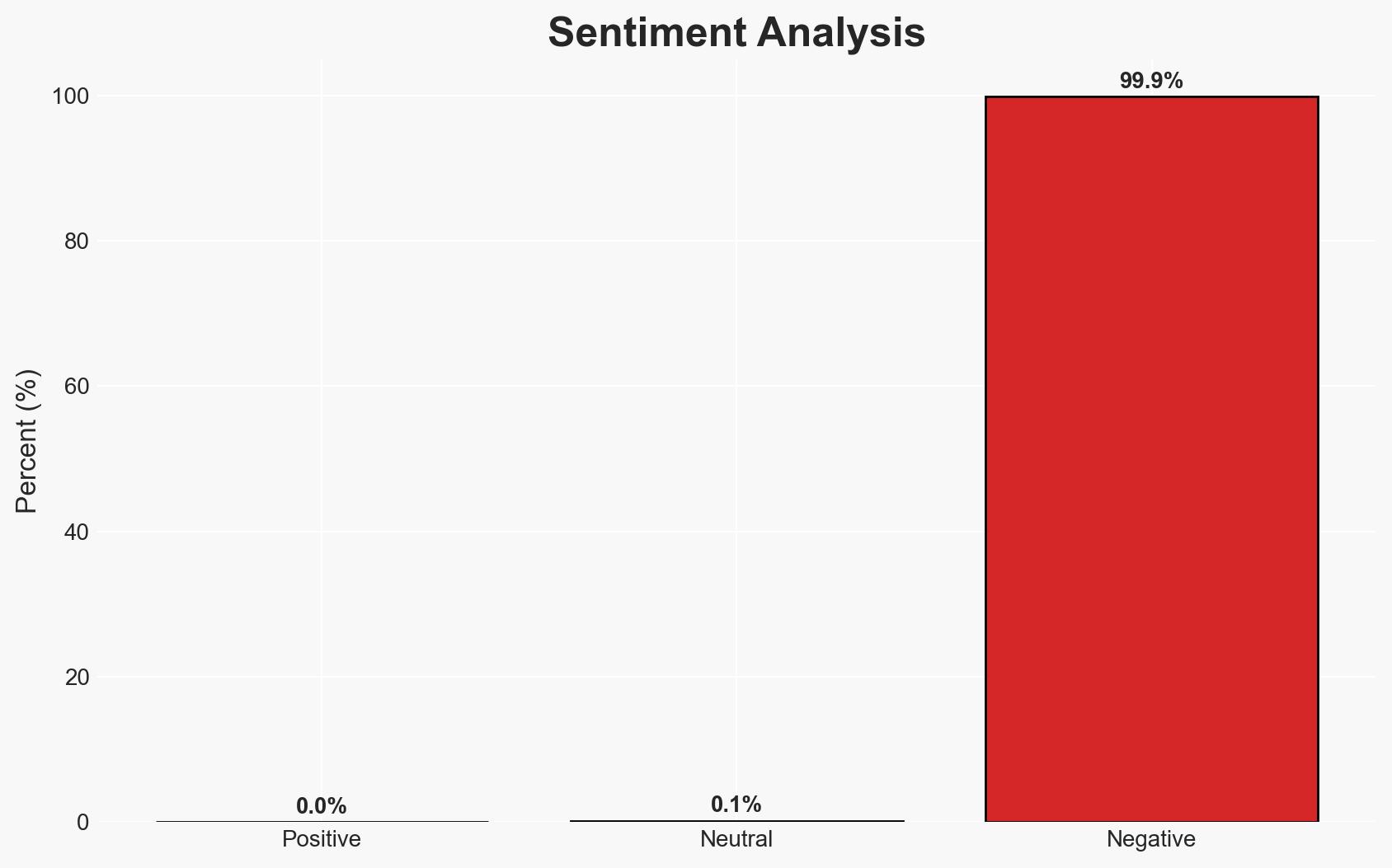
The guilty plea of Bryan Fleming, founder of pcTattletale, marks a significant legal precedent in the prosecution of stalkerware operators. This development highlights the challenges in regulating and prosecuting digital surveillance tools marketed for illicit purposes. The case may influence future legal frameworks and enforcement strategies against similar software providers. Overall confidence in this assessment is moderate, given the limited scope of available data.
2. Competing Hypotheses
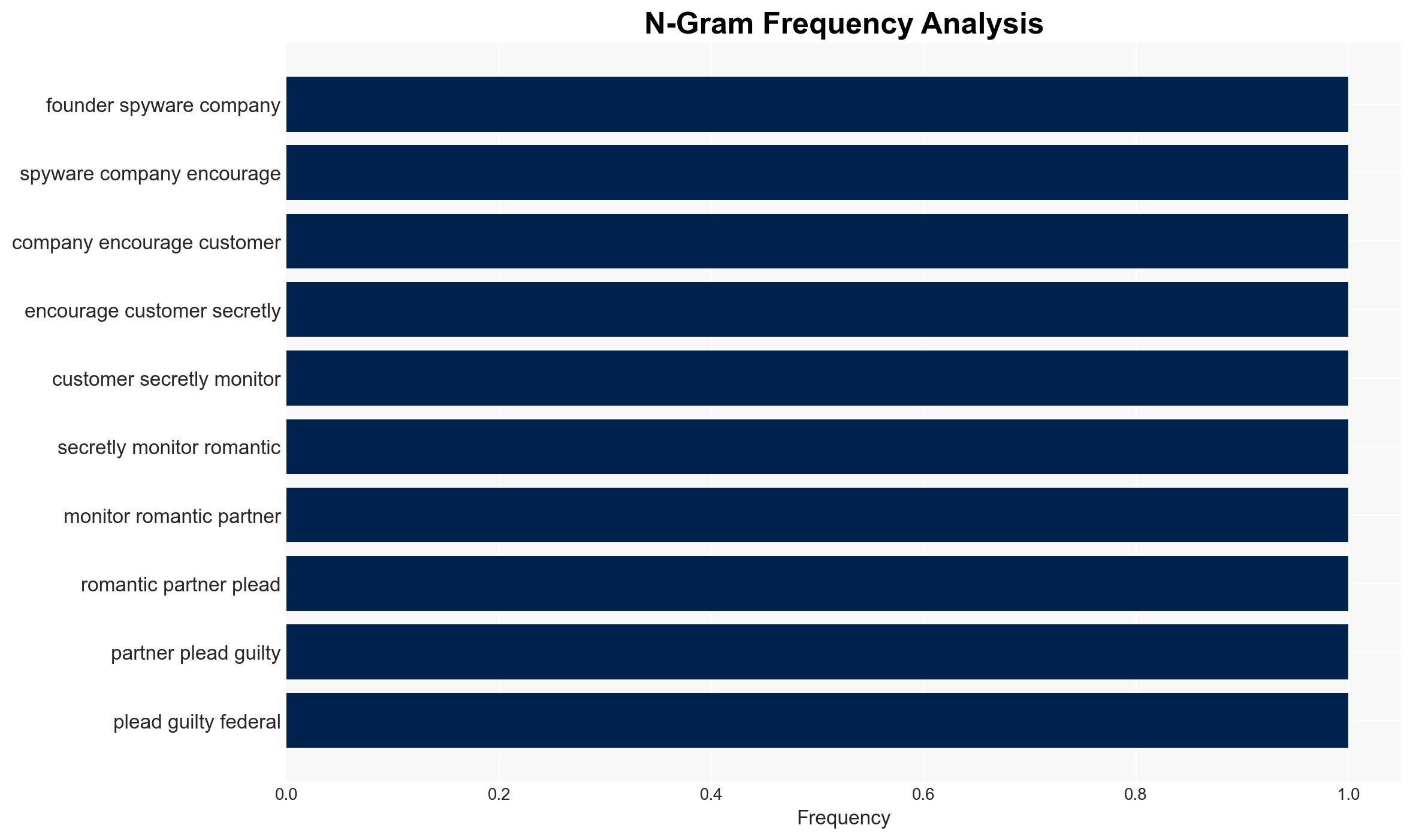
- Hypothesis A: Fleming was aware of the illegal uses of pcTattletale and deliberately marketed it for such purposes. This is supported by his promotional strategies and reassurances to customers about concealing purchases. However, his claim of ignorance raises questions about his intent.
- Hypothesis B: Fleming genuinely believed pcTattletale was legal and primarily intended for legitimate monitoring purposes. This is contradicted by the software’s marketing as undetectable and its use in spying on partners without consent.
- Assessment: Hypothesis A is currently better supported due to the explicit marketing strategies and customer interactions that indicate awareness of illegal applications. Key indicators that could shift this judgment include new evidence of Fleming’s internal communications or legal advice received.
3. Key Assumptions and Red Flags
- Assumptions: Fleming had control over marketing strategies; customers primarily used the software for illicit surveillance; legal frameworks are insufficiently clear on stalkerware.
- Information Gaps: Details on Fleming’s internal communications and any legal counsel he received; comprehensive data on how customers used the software.
- Bias & Deception Risks: Potential bias in law enforcement’s portrayal of Fleming’s intent; Fleming’s public statements may be self-serving and deceptive.
4. Implications and Strategic Risks
This case could set a legal precedent affecting future prosecutions of digital surveillance tools and influence regulatory approaches globally.
- Political / Geopolitical: Potential for increased international cooperation on digital privacy laws and enforcement.
- Security / Counter-Terrorism: Enhanced scrutiny on software that could be repurposed for espionage or terrorism-related surveillance.
- Cyber / Information Space: Increased focus on cybersecurity measures to protect against unauthorized surveillance software.
- Economic / Social: Possible impacts on the software industry, particularly companies developing monitoring tools, and public awareness of digital privacy rights.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor legal developments in similar cases; assess current software regulations and enforcement capabilities.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies to enhance digital privacy protections; invest in public awareness campaigns on legal surveillance tools.
- Scenario Outlook: Best: Strengthened legal frameworks deter illegal surveillance software. Worst: Proliferation of undetectable surveillance tools. Most-Likely: Gradual improvements in legal and regulatory measures with ongoing challenges in enforcement.
6. Key Individuals and Entities
- Bryan Fleming – Founder of pcTattletale
- pcTattletale – Surveillance software company
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, digital privacy, legal frameworks, surveillance software, law enforcement, regulatory challenges, stalkerware
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us