CISA Discontinues 10 Emergency Cybersecurity Directives from 2019 to 2024
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA Retires 10 Emergency Cybersecurity Directives Issued Between 2019 and 2024
1. BLUF (Bottom Line Up Front)
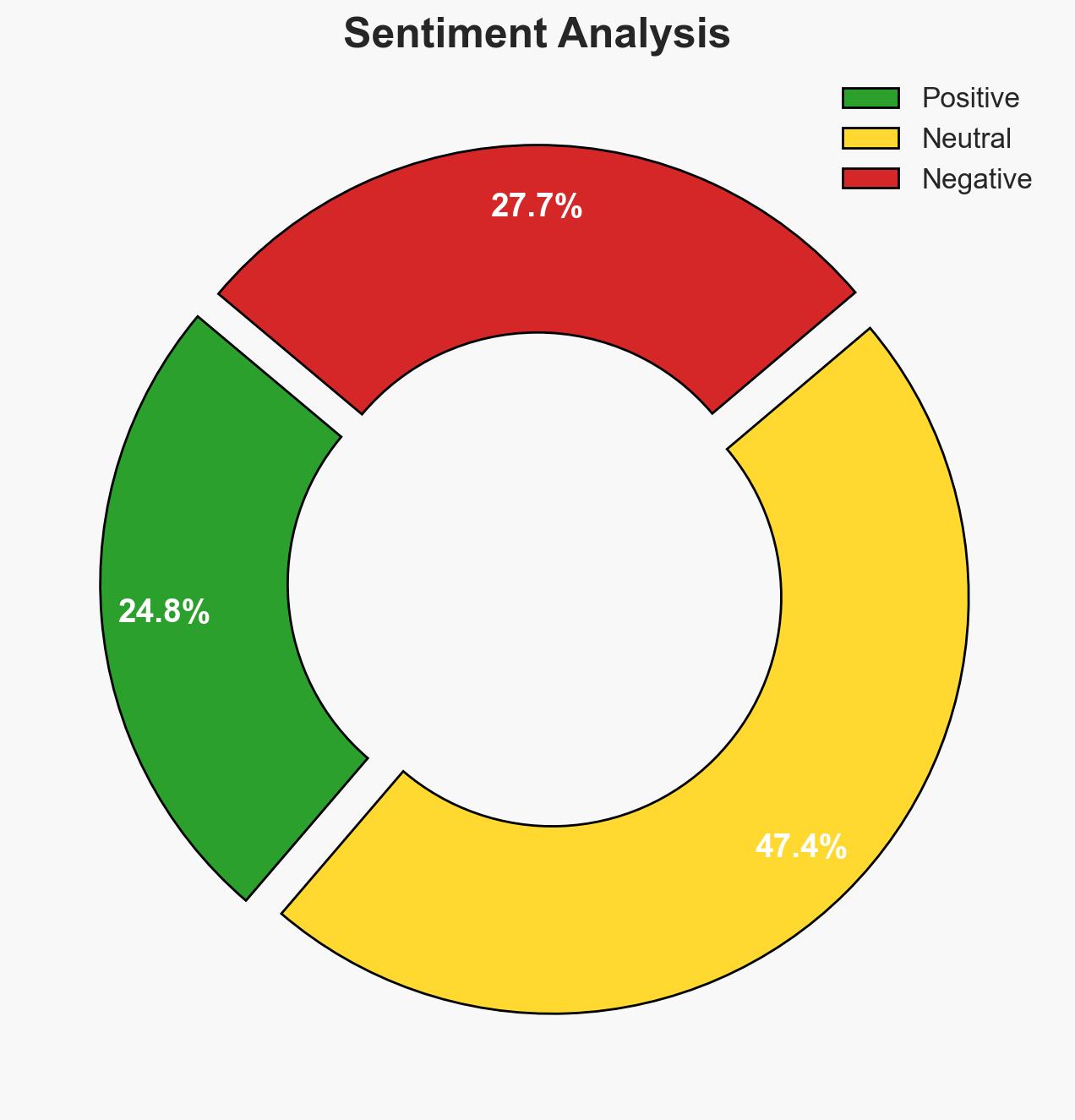
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has retired 10 emergency cybersecurity directives, indicating a shift towards more integrated and resilient cybersecurity measures across federal systems. This development primarily affects federal agencies and their cybersecurity posture. The most likely hypothesis is that CISA’s actions reflect successful mitigation of the vulnerabilities addressed by these directives. Overall confidence in this judgment is moderate, given the lack of detailed public reporting on the effectiveness of these mitigations.
2. Competing Hypotheses
- Hypothesis A: CISA’s retirement of the directives indicates that the vulnerabilities have been effectively mitigated and integrated into ongoing cybersecurity practices. This is supported by CISA’s statement on successful remediation and incorporation into Binding Operational Directive (BOD) 22-01. However, the lack of specific metrics on mitigation success introduces uncertainty.
- Hypothesis B: The retirement of directives could be a strategic move to streamline cybersecurity efforts and focus on new threats, rather than an indication of complete mitigation. This hypothesis is less supported due to CISA’s emphasis on collaboration and resilience-building, but it remains plausible given the evolving threat landscape.
- Assessment: Hypothesis A is currently better supported due to CISA’s explicit statements on remediation success and integration into broader directives. Indicators such as new threat reports or changes in federal cybersecurity posture could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities addressed by the directives are no longer a significant threat; CISA’s collaboration with federal agencies has been effective; Binding Operational Directive 22-01 adequately covers the risks.
- Information Gaps: Detailed metrics on the effectiveness of mitigations; specific feedback from federal agencies on the impact of these directives.
- Bias & Deception Risks: Potential for confirmation bias in assessing the success of mitigations; reliance on CISA’s public statements without independent verification.
4. Implications and Strategic Risks
This development could lead to a more streamlined and resilient federal cybersecurity posture, but also risks complacency if new threats are not adequately anticipated.
- Political / Geopolitical: May enhance U.S. credibility in cybersecurity leadership, but could also prompt adversaries to seek new vulnerabilities.
- Security / Counter-Terrorism: Improved federal cybersecurity could reduce the risk of cyber-terrorism, but new attack vectors may emerge.
- Cyber / Information Space: Enhanced resilience in federal systems could deter cyber-espionage but requires continuous adaptation to new threats.
- Economic / Social: Greater cybersecurity could protect economic interests and public trust, but requires sustained investment and vigilance.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for any emerging threats or vulnerabilities; verify the effectiveness of current cybersecurity measures through independent audits.
- Medium-Term Posture (1–12 months): Strengthen partnerships with private sector cybersecurity firms; invest in training and capacity-building for federal cybersecurity personnel.
- Scenario Outlook:
- Best: Federal systems remain secure with no major breaches, supported by continuous updates and collaboration.
- Worst: New vulnerabilities are exploited due to over-reliance on past directives, leading to significant breaches.
- Most-Likely: Federal cybersecurity posture improves incrementally, with occasional adjustments to address emerging threats.
6. Key Individuals and Entities
- CISA Acting Director Madhu Gottumukkala
- Federal Civilian Executive Branch (FCEB) agencies
7. Thematic Tags
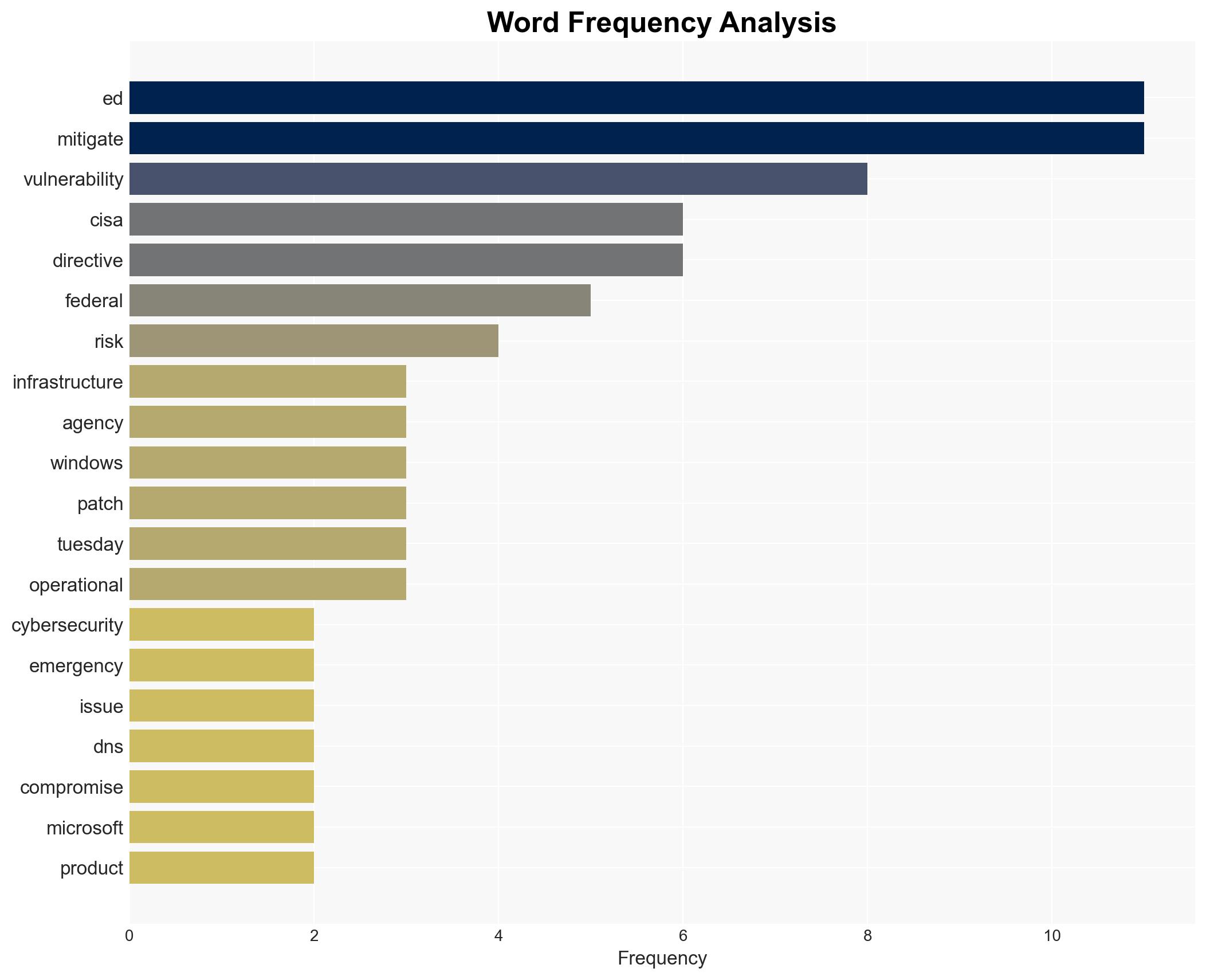
cybersecurity, federal agencies, vulnerability mitigation, CISA, national security, cyber threats, resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us