UAT-7290, a China-affiliated group, conducts telecom espionage in South Asia and Europe using advanced malware
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China-linked UAT-7290 spies on telco in South Asia and Europe using modular malware
1. BLUF (Bottom Line Up Front)
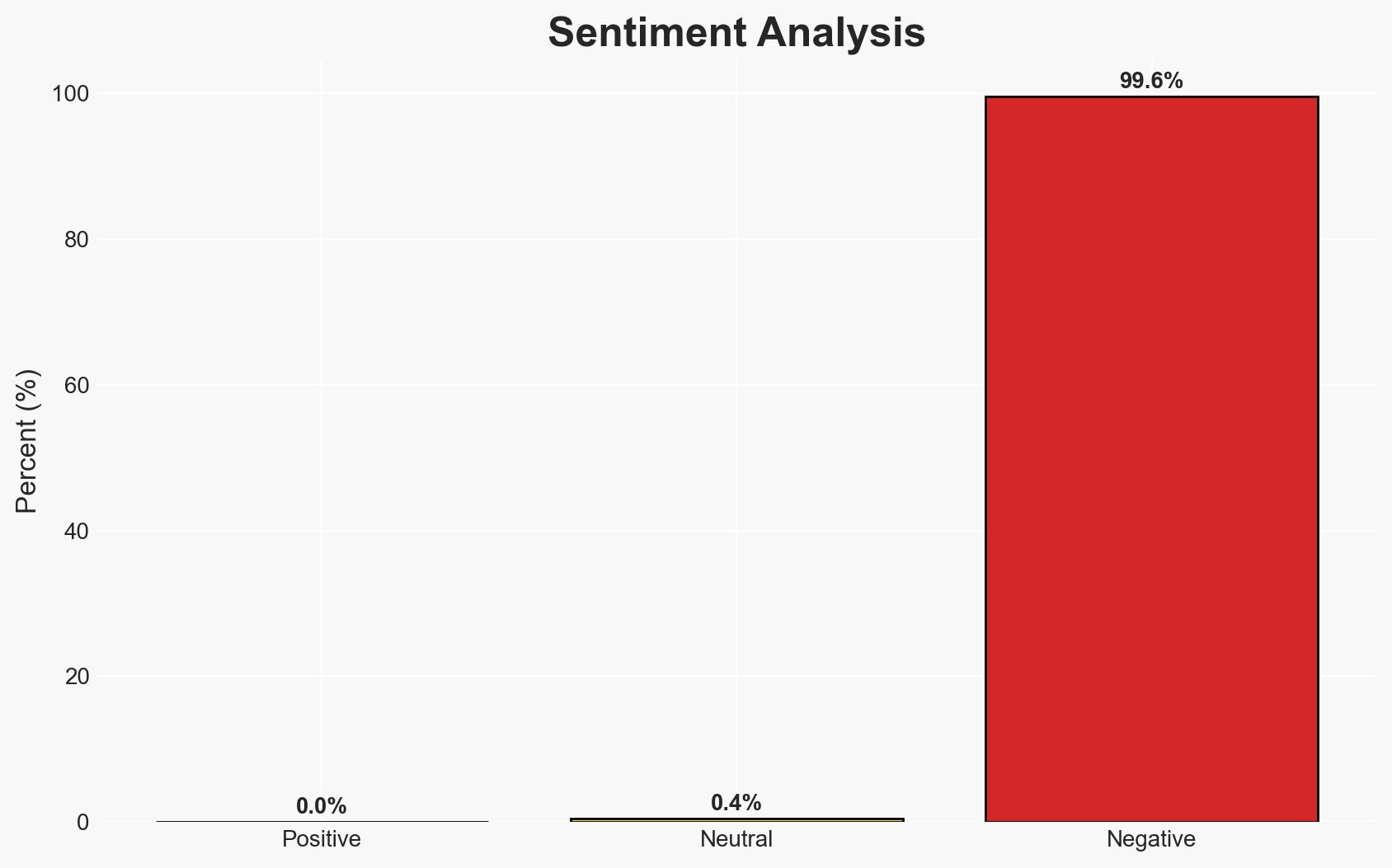
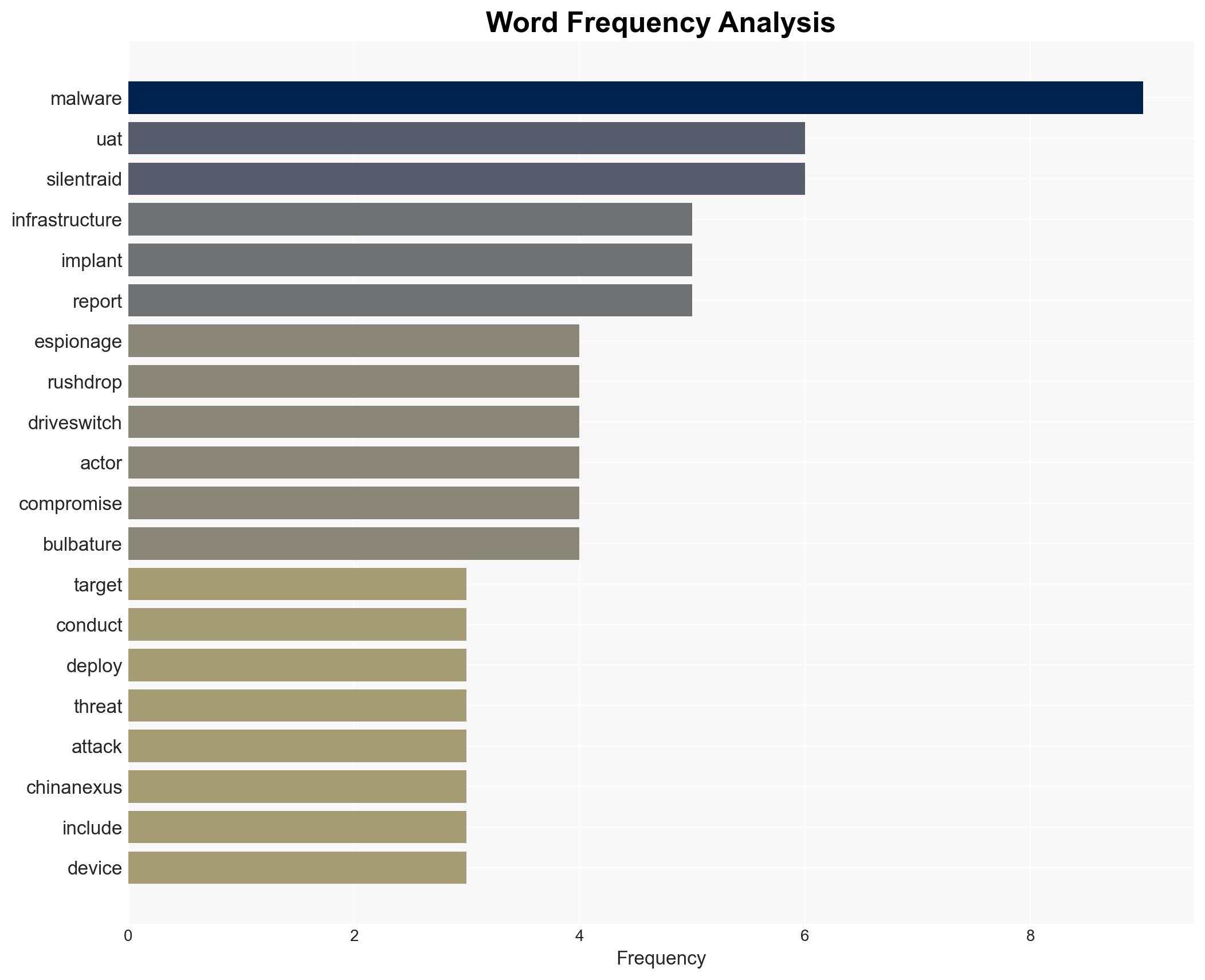
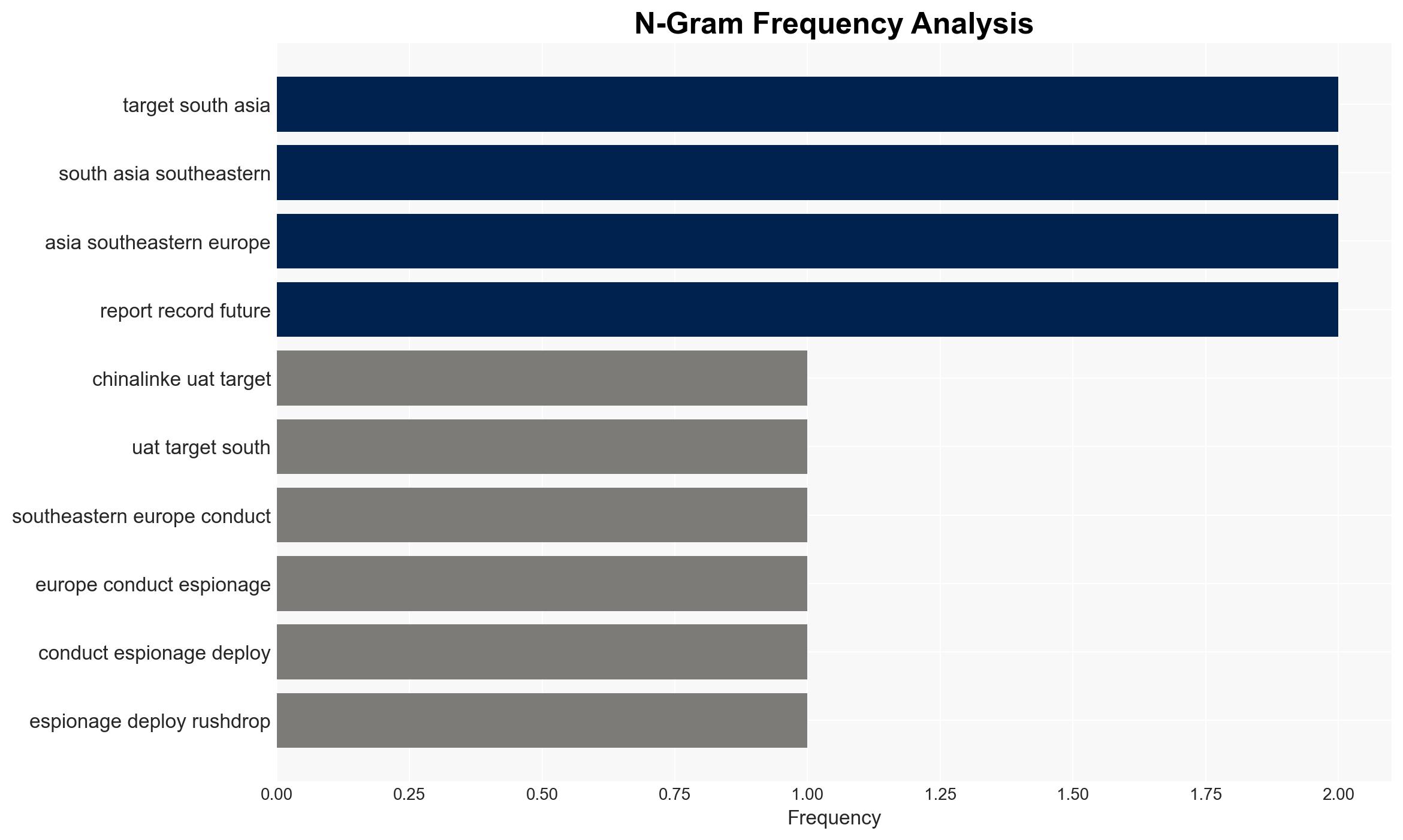
China-linked threat actor UAT-7290 is conducting espionage operations targeting telecommunications providers in South Asia and Southeastern Europe using sophisticated modular malware. The group’s activities are likely part of a broader Chinese cyber-espionage campaign. This assessment is made with moderate confidence due to overlapping indicators with known Chinese APT groups and the use of advanced malware techniques.
2. Competing Hypotheses
- Hypothesis A: UAT-7290 is a China-aligned cyber-espionage group targeting telecoms to gather intelligence and facilitate further cyber operations. This is supported by the use of modular malware, overlap with known Chinese APT tactics, and infrastructure linked to China. Uncertainties include the exact command structure and direct attribution to state actors.
- Hypothesis B: UAT-7290 is an independent cybercriminal group exploiting telecom networks for financial gain or selling access to state actors. While plausible, this is less supported due to the sophisticated nature of the tools and the strategic targeting of telecoms, which aligns more with state-sponsored objectives.
- Assessment: Hypothesis A is currently better supported due to the alignment of TTPs with known Chinese APTs and the strategic nature of the targets. Indicators such as further attribution evidence or shifts in targeting focus could alter this judgment.
3. Key Assumptions and Red Flags
- Assumptions: UAT-7290 is state-sponsored; the targeting of telecoms is strategic; China is the primary beneficiary of the intelligence gathered.
- Information Gaps: Direct evidence linking UAT-7290 to specific Chinese government entities; comprehensive understanding of the group’s full operational scope.
- Bias & Deception Risks: Attribution bias due to reliance on technical overlaps; potential for false flag operations by other actors mimicking Chinese TTPs.
4. Implications and Strategic Risks
The activities of UAT-7290 could exacerbate geopolitical tensions and lead to increased cyber defense measures by affected nations. The persistent threat to telecom infrastructure poses significant risks to national security and economic stability.
- Political / Geopolitical: Potential diplomatic strains between China and affected countries; possible sanctions or retaliatory cyber actions.
- Security / Counter-Terrorism: Increased vulnerability of critical infrastructure; potential for exploitation by other threat actors.
- Cyber / Information Space: Escalation in cyber espionage activities; heightened cybersecurity measures and information sharing among allies.
- Economic / Social: Disruption of telecom services could impact economic activities and public trust in digital infrastructure.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of telecom networks; deploy threat intelligence to identify and mitigate UAT-7290 activities; engage in diplomatic channels to address cyber threats.
- Medium-Term Posture (1–12 months): Strengthen international cybersecurity partnerships; invest in advanced detection and response capabilities; conduct joint exercises to improve resilience.
- Scenario Outlook: Best: Successful mitigation and diplomatic resolution; Worst: Escalation of cyber conflicts and economic disruptions; Most-Likely: Continued cyber espionage with incremental improvements in defenses.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, telecommunications, China, APT, malware, national security, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us