Patients struggle to obtain information following Manage My Health ransomware attack as systems remain unresp…
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Manage My Health patients draw blanks in quest for information on cybersecurity breach
1. BLUF (Bottom Line Up Front)
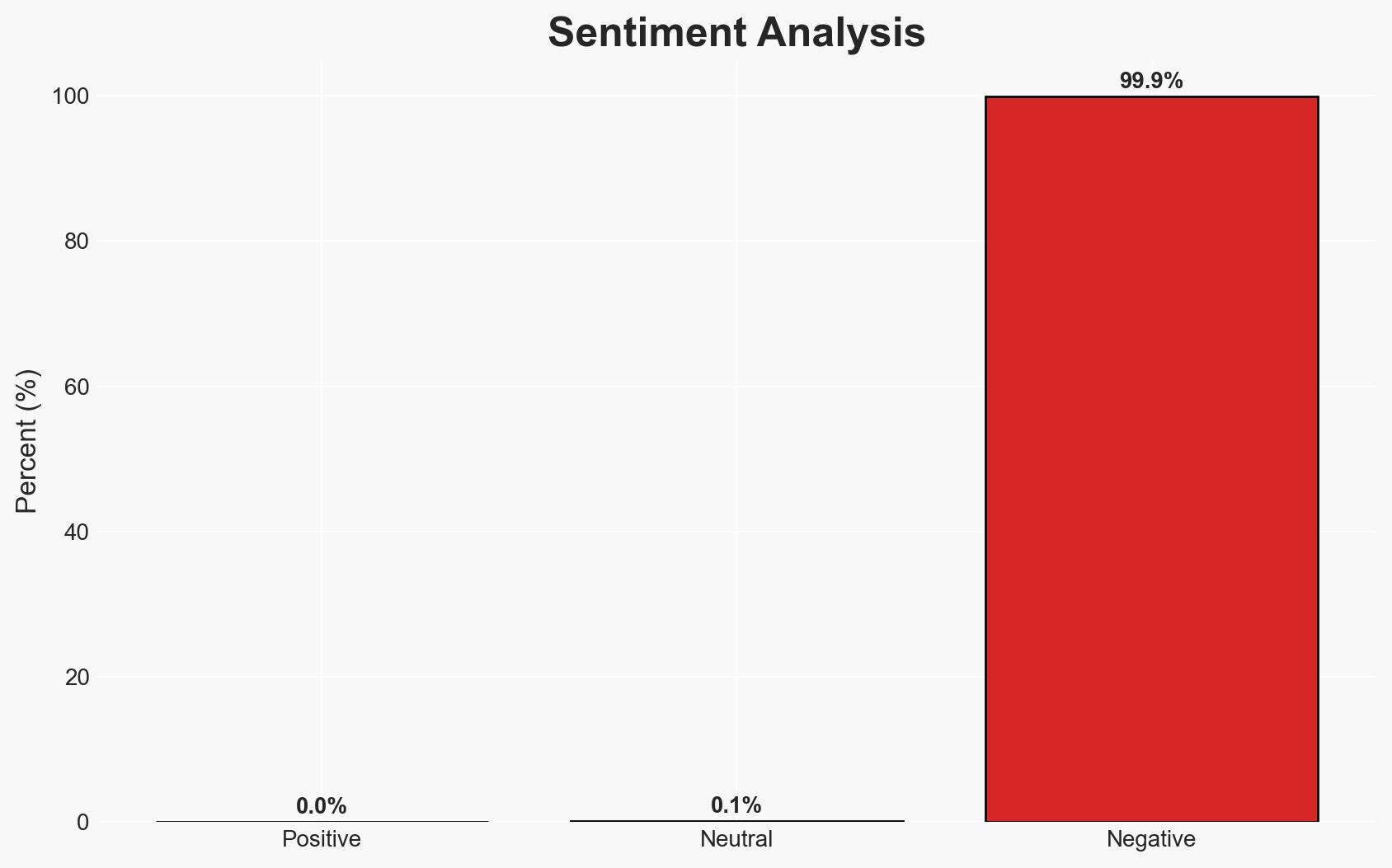
The Manage My Health platform has experienced a ransomware attack, resulting in compromised patient health records and inadequate communication with affected individuals. The situation is exacerbated by technical failures and overloaded support systems, leading to a loss of trust among users. The most likely hypothesis is that the breach was due to inadequate cybersecurity measures, with moderate confidence in this assessment.
2. Competing Hypotheses
- Hypothesis A: The ransomware attack on Manage My Health was facilitated by inadequate cybersecurity measures. Supporting evidence includes the company’s inability to promptly notify affected users and the technical failures experienced. However, specific details on the security posture prior to the attack are unclear.
- Hypothesis B: The attack was a sophisticated operation by a well-resourced threat actor, overwhelming even robust defenses. This is contradicted by the apparent lack of preparedness in communication and response, suggesting systemic vulnerabilities.
- Assessment: Hypothesis A is currently better supported due to the evident communication breakdowns and technical issues, indicating potential pre-existing weaknesses. Indicators that could shift this judgment include evidence of advanced persistent threat involvement or insider complicity.
3. Key Assumptions and Red Flags
- Assumptions: The breach was primarily due to external cyber threats; Manage My Health’s communication failures are not intentional; affected patients represent a diverse demographic.
- Information Gaps: Specific details on the nature of the ransomware, the extent of data compromised, and the timeline of the breach remain unknown.
- Bias & Deception Risks: Potential underreporting by Manage My Health to minimize reputational damage; confirmation bias in assuming external threats without considering internal vulnerabilities.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on healthcare cybersecurity practices and regulatory pressures. The breach may also serve as a case study for future cyber defense strategies.
- Political / Geopolitical: Potential for increased regulatory oversight and policy changes in data protection laws.
- Security / Counter-Terrorism: Heightened awareness and preparedness against similar attacks in the healthcare sector.
- Cyber / Information Space: Increased focus on cybersecurity infrastructure and incident response capabilities.
- Economic / Social: Potential loss of consumer trust in digital health services, impacting user engagement and service adoption.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance communication channels with affected users, conduct a comprehensive security audit, and engage with cybersecurity experts for immediate risk mitigation.
- Medium-Term Posture (1–12 months): Develop robust incident response plans, invest in cybersecurity infrastructure, and establish partnerships with cybersecurity firms for ongoing support.
- Scenario Outlook:
- Best: Rapid recovery and improved security measures restore user trust.
- Worst: Continued technical failures and inadequate responses lead to significant reputational damage and regulatory penalties.
- Most-Likely: Gradual improvement in communication and security, with moderate impact on user trust and regulatory scrutiny.
6. Key Individuals and Entities
- Manage My Health (entity)
- Andrea (affected individual, Wellington)
- Nel (affected individual)
- Lou (affected individual)
- Privacy Commissioner (potential regulatory entity)
7. Thematic Tags
cybersecurity, ransomware, data breach, healthcare, information security, regulatory compliance, user trust
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us