pcTattletale founder admits guilt as US intensifies efforts against stalkerware operations
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: pcTattletale founder pleads guilty as US cracks down on stalkerware
1. BLUF (Bottom Line Up Front)
The guilty plea of pcTattletale founder Bryan Fleming marks a significant step in U.S. efforts to combat stalkerware, potentially setting a precedent for future legal actions against similar entities. This development highlights vulnerabilities in digital privacy and security, affecting individuals targeted by such software. Overall, there is moderate confidence that this case will catalyze further scrutiny and regulation of spyware applications.
2. Competing Hypotheses
- Hypothesis A: The prosecution of Bryan Fleming will lead to increased legal actions against stalkerware developers, resulting in a decline in the availability and use of such software. Supporting evidence includes the rarity of such prosecutions and the explicit illegal use of pcTattletale. However, uncertainties remain about the legal system’s capacity to handle similar cases efficiently.
- Hypothesis B: Despite the prosecution, stalkerware will continue to proliferate due to the ease of developing and distributing such software globally. This is supported by the historical resilience of cybercrime and the use of overseas shell companies by developers. Contradicting evidence includes the increased focus on digital privacy and security by law enforcement.
- Assessment: Hypothesis A is currently better supported due to the legal precedent set and the explicit nature of pcTattletale’s marketing, which may deter other developers. Key indicators that could shift this judgment include changes in legislation, international cooperation, and technological advancements in spyware detection.
3. Key Assumptions and Red Flags
- Assumptions: The legal system will continue to prioritize stalkerware cases; international cooperation will improve; technological solutions will keep pace with spyware development.
- Information Gaps: Detailed data on the prevalence of stalkerware and the effectiveness of current legal frameworks in different jurisdictions.
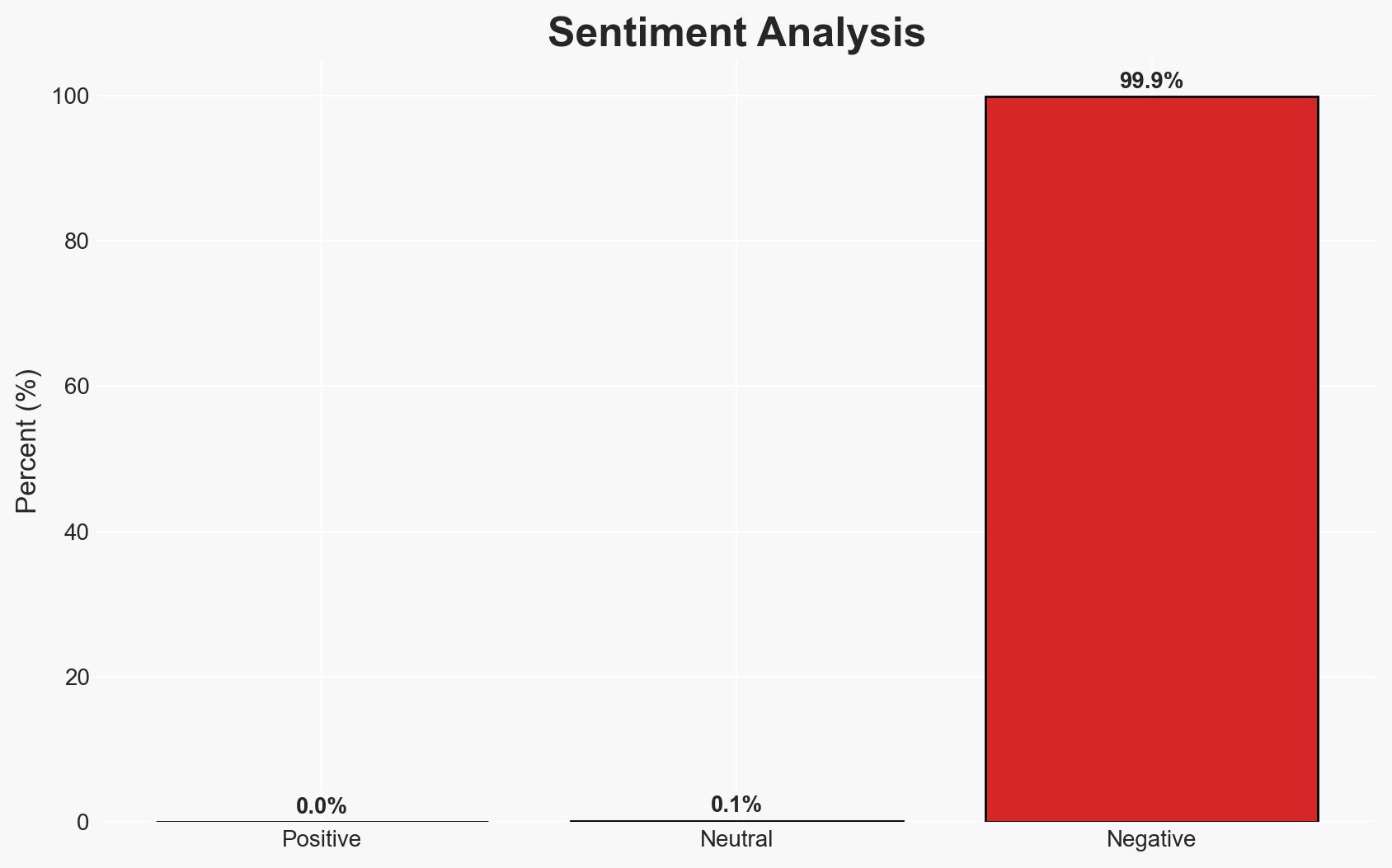
- Bias & Deception Risks: Potential bias in reporting due to the negative perception of stalkerware; risk of deception by developers using legal loopholes or rebranding tactics.
4. Implications and Strategic Risks
This development could lead to increased regulatory scrutiny and a push for stronger privacy laws, impacting the digital surveillance landscape. Over time, it may influence international norms and cooperation in cybercrime prevention.
- Political / Geopolitical: Potential for increased international collaboration on cybercrime legislation and enforcement.
- Security / Counter-Terrorism: Enhanced focus on digital privacy could improve overall cybersecurity but may also drive stalkerware underground.
- Cyber / Information Space: Possible increase in cybersecurity measures and public awareness campaigns regarding digital privacy threats.
- Economic / Social: Legal actions could deter investment in spyware development, impacting the market for such tools; increased public awareness may lead to greater demand for privacy-focused technologies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor legal proceedings and public reactions; enhance public awareness campaigns on digital privacy and security.
- Medium-Term Posture (1–12 months): Develop partnerships with international law enforcement to address cross-border cybercrime; invest in research and development of anti-stalkerware technologies.
- Scenario Outlook:
- Best: Significant reduction in stalkerware use due to effective legal deterrents and technological advancements.
- Worst: Stalkerware developers adapt to legal pressures, leading to more sophisticated and harder-to-detect tools.
- Most-Likely: Gradual decline in stalkerware prevalence as legal and technological measures improve, though some underground activity persists.
6. Key Individuals and Entities
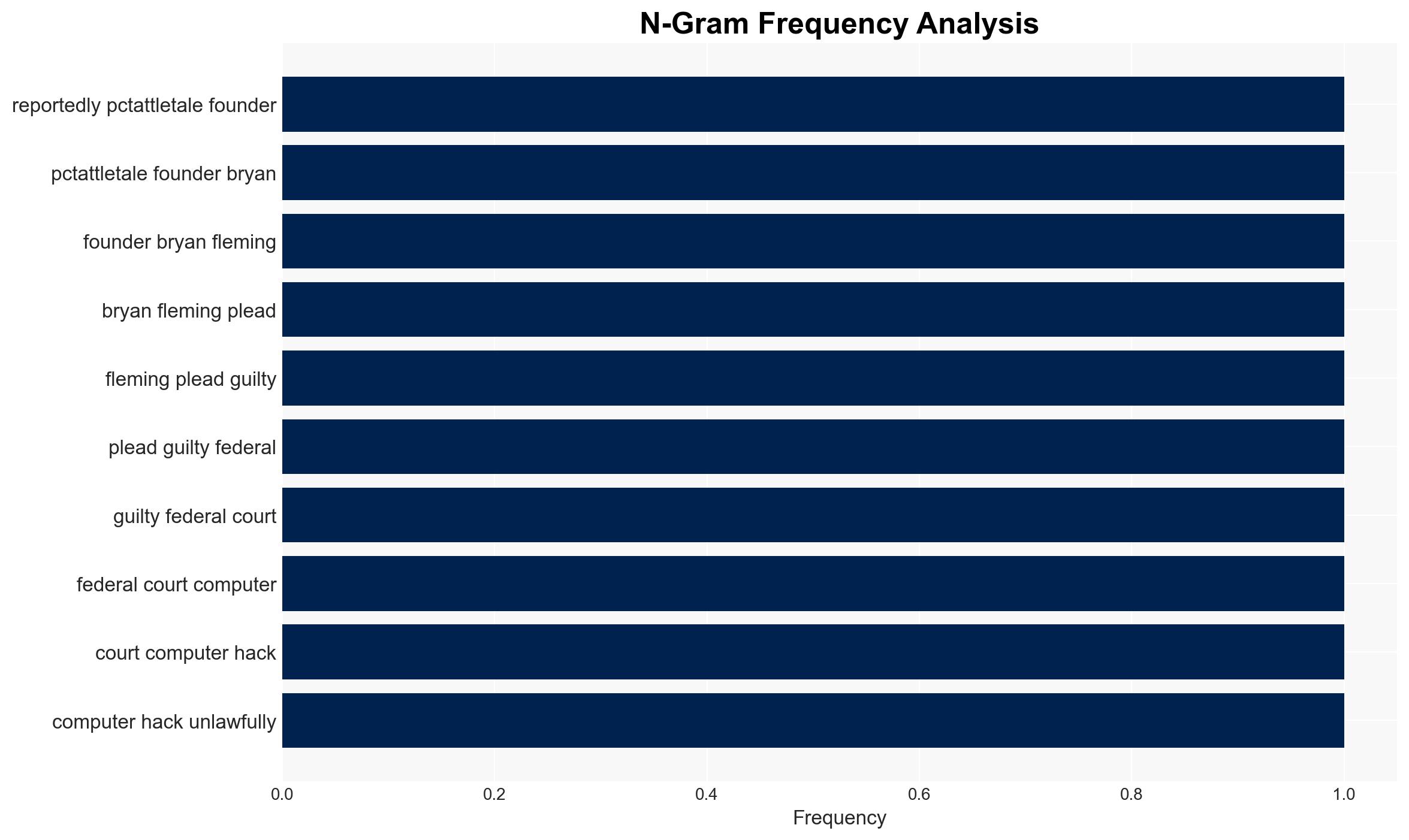
- Bryan Fleming – Founder of pcTattletale
- Homeland Security Investigations – Investigating agency
- Amazon – Provider of cloud infrastructure used by pcTattletale
- Coalition Against Stalkerware – Advocacy group against stalkerware
7. Thematic Tags
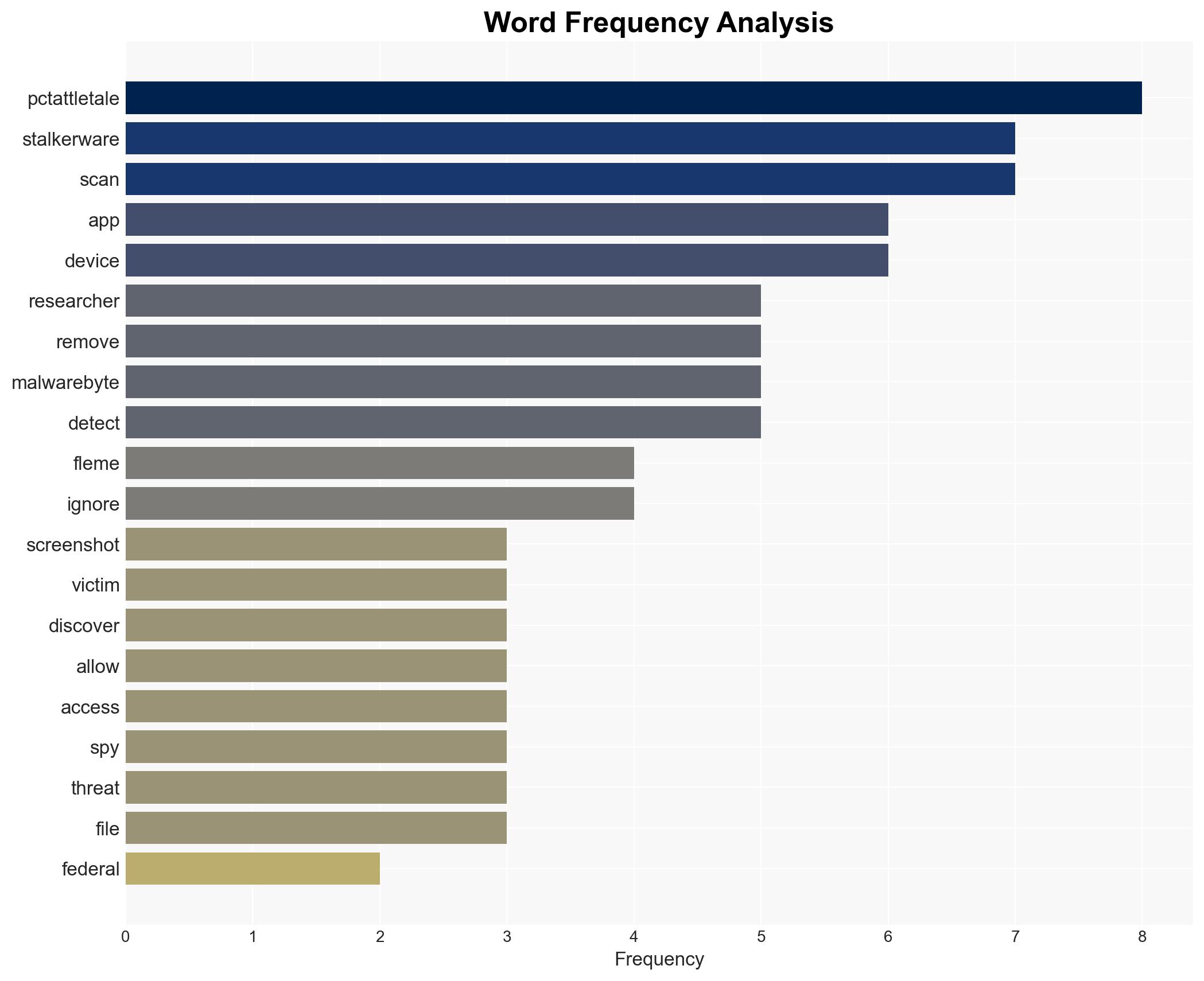
cybersecurity, digital privacy, legal precedent, stalkerware, cybercrime, law enforcement, spyware
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us