Chinese Salt Typhoon Cyberattack Expands as US Telecoms Face Erosion of Cybersecurity Measures
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
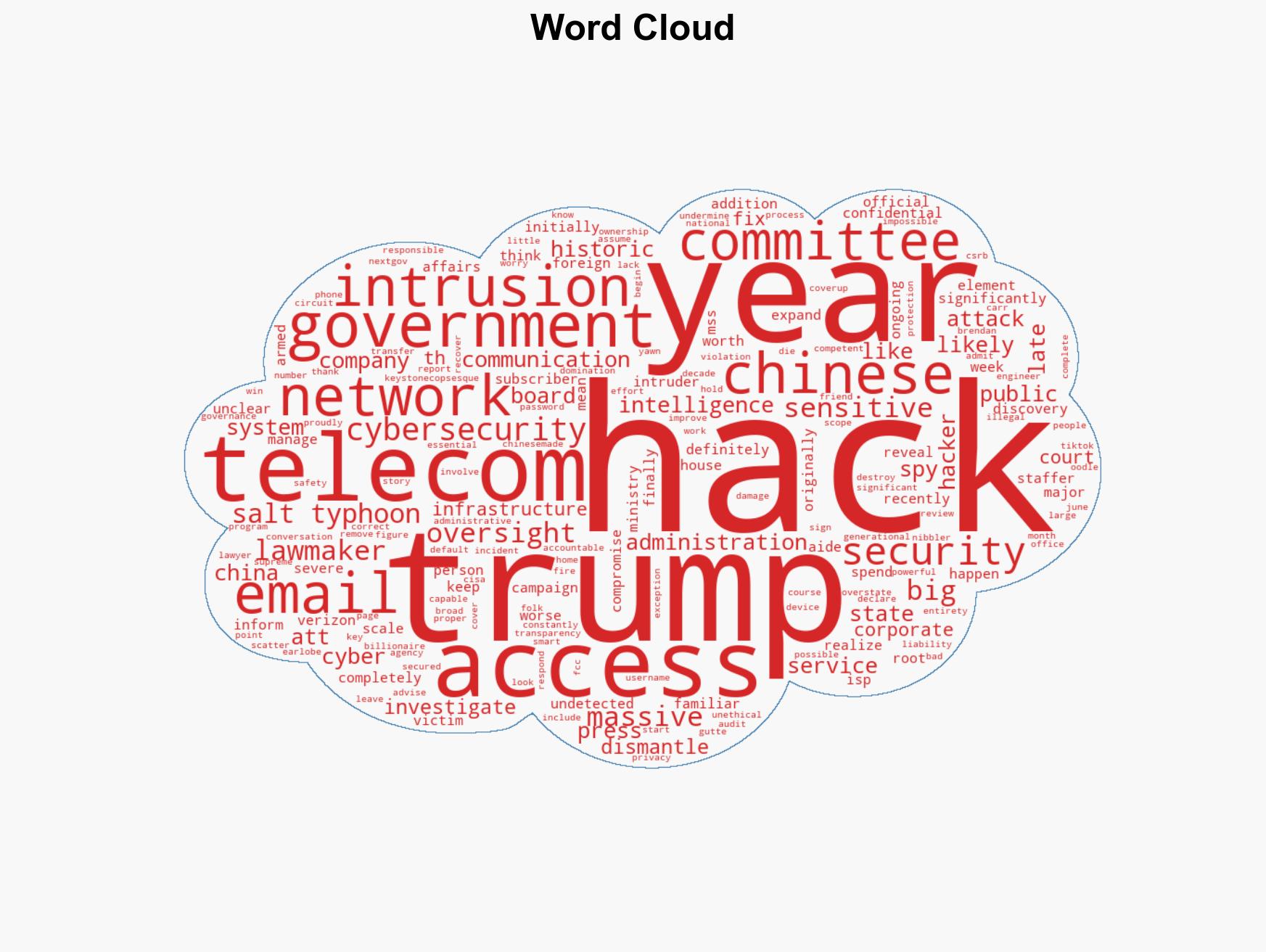
Intelligence Report: Scope Of Chinese Salt Typhoon Hack Keeps Getting Worse As Trump Dismantles US Cybersecurity Defenses
1. BLUF (Bottom Line Up Front)
The “Salt Typhoon” hack represents a significant breach of U.S. telecommunications and government communications networks by Chinese state actors, with ongoing implications for national security. The breach was facilitated by inadequate cybersecurity measures and compounded by policy decisions that weakened U.S. cyber defenses. The most likely hypothesis is that the Chinese Ministry of State Security (MSS) continues to exploit these vulnerabilities for intelligence gathering. Confidence in this assessment is moderate due to incomplete information about the full scope of the intrusion.
2. Competing Hypotheses
- Hypothesis A: The Chinese MSS conducted the Salt Typhoon hack to gather intelligence on U.S. government and public officials, exploiting weak cybersecurity practices in U.S. telecoms. Supporting evidence includes the reported access to sensitive communications and the pattern of Chinese cyber-espionage activities. Key uncertainties include the full extent of data accessed and the specific objectives of the MSS.
- Hypothesis B: The intrusion was part of a broader cyber campaign aimed at disrupting U.S. telecommunications infrastructure, with intelligence gathering as a secondary objective. This is supported by the scale and persistence of the intrusion. However, there is less direct evidence of intent to disrupt infrastructure beyond espionage.
- Assessment: Hypothesis A is currently better supported due to the direct evidence of intelligence gathering activities and the historical context of Chinese cyber-espionage. Indicators that could shift this judgment include evidence of infrastructure disruption or new information on MSS objectives.
3. Key Assumptions and Red Flags
- Assumptions: The MSS is the primary actor behind the hack; U.S. telecoms’ cybersecurity practices were inadequate; U.S. policy decisions have weakened cyber defenses.
- Information Gaps: Full scope of data accessed by the MSS; specific MSS objectives; potential for ongoing access or additional vulnerabilities.
- Bias & Deception Risks: Potential bias in underestimating the MSS’s capabilities or objectives; risk of deception by U.S. entities minimizing breach impact for liability reasons.
4. Implications and Strategic Risks
The Salt Typhoon hack could lead to long-term strategic vulnerabilities for the U.S., impacting political, security, and economic stability. The breach may embolden further cyber operations by state actors.
- Political / Geopolitical: Increased tensions between the U.S. and China; potential for retaliatory measures or diplomatic fallout.
- Security / Counter-Terrorism: Heightened risk of further cyber-espionage and potential exploitation of compromised data by adversaries.
- Cyber / Information Space: Erosion of trust in U.S. telecoms; potential for increased regulatory scrutiny and cybersecurity reforms.
- Economic / Social: Possible economic repercussions for telecoms; public concern over privacy and data security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of telecom cybersecurity practices; increase monitoring of MSS activities; enhance incident response capabilities.
- Medium-Term Posture (1–12 months): Strengthen public-private cybersecurity partnerships; invest in cybersecurity infrastructure; review and reform regulatory frameworks.
- Scenario Outlook:
- Best: Comprehensive reforms lead to enhanced cybersecurity and deterrence of future breaches.
- Worst: Continued vulnerabilities result in further significant breaches and geopolitical escalation.
- Most-Likely: Incremental improvements in cybersecurity with ongoing risks from state actors.
6. Key Individuals and Entities
- Ministry of State Security (MSS)
- AT&T
- Verizon
- Cybersecurity and Infrastructure Security Agency (CISA)
- Federal Communications Commission (FCC)
- Brendan Carr
7. Thematic Tags
cybersecurity, cyber-espionage, telecommunications, national security, U.S.-China relations, cybersecurity policy, intelligence gathering, regulatory oversight
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us