Hackers Utilize MAESTRO Toolkit to Exploit VMware Vulnerabilities and Escape Virtual Machines
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: MAESTRO Toolkit Exploiting VMware VM Escape Vulnerabilities
1. BLUF (Bottom Line Up Front)
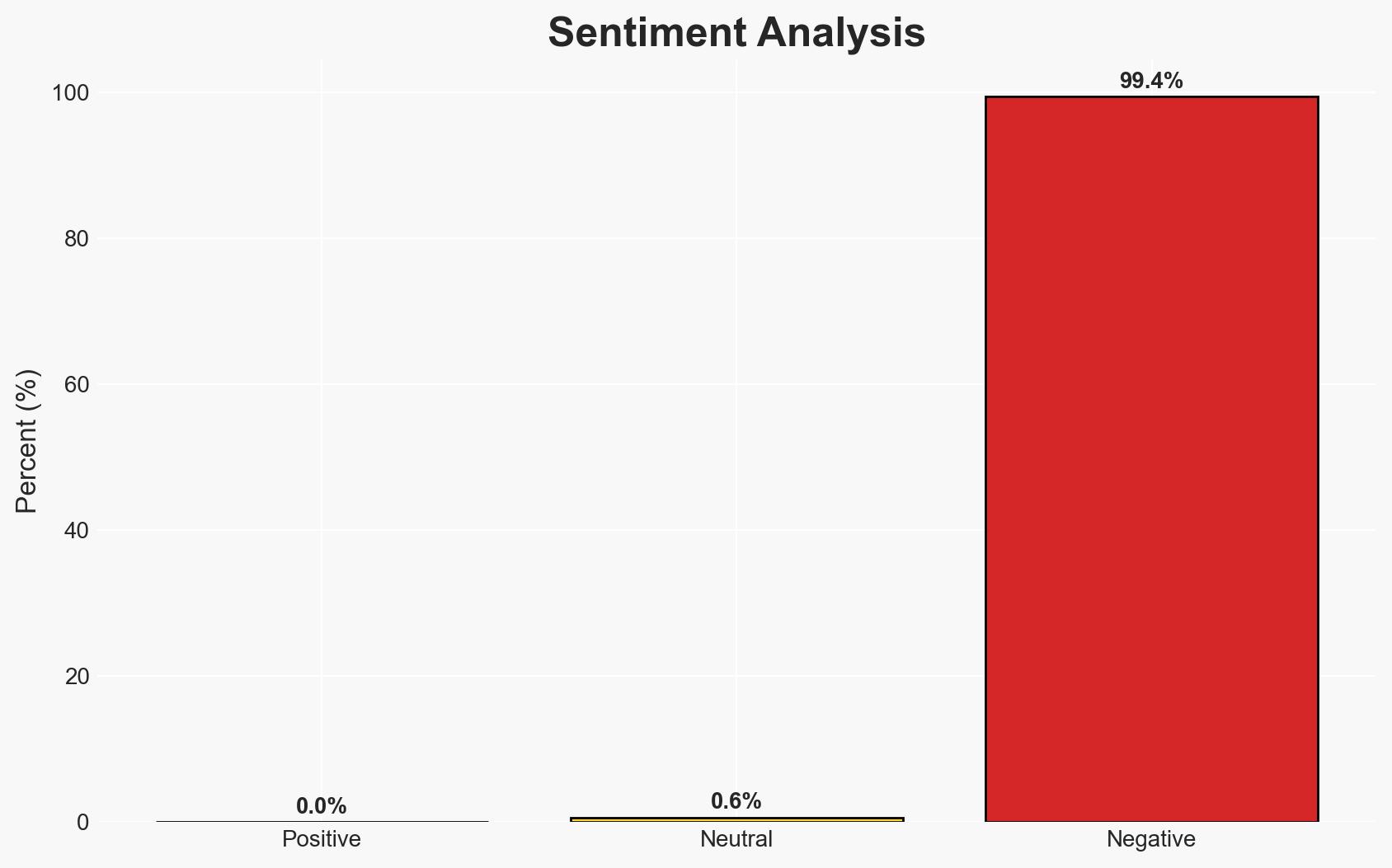
The MAESTRO toolkit represents a significant cyber threat, exploiting VMware VM escape vulnerabilities to gain control over host servers. The toolkit’s development and use suggest a sophisticated actor, likely originating from a Chinese-speaking region. This poses a critical risk to organizations using affected VMware versions. Overall confidence in this assessment is moderate due to the limited direct attribution evidence.
2. Competing Hypotheses
- Hypothesis A: The MAESTRO toolkit was developed and deployed by a state-sponsored actor from a Chinese-speaking region. This is supported by the presence of simplified Chinese notes in the code and the sophisticated nature of the attack. However, there is uncertainty due to the lack of direct attribution evidence.
- Hypothesis B: The toolkit was developed by an independent cybercriminal group with no state affiliation, using Chinese language as a deception tactic. This is plausible given the common use of false flags in cyber operations, but contradicts the toolkit’s complexity and resource requirements.
- Assessment: Hypothesis A is currently better supported due to the sophistication of the attack and linguistic indicators, though further evidence is needed to confirm state sponsorship. Indicators such as additional linguistic analysis or financial links could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The toolkit’s complexity implies significant resources; the use of simplified Chinese suggests a Chinese-speaking origin; the vulnerabilities were unknown to VMware until 2025.
- Information Gaps: Direct evidence linking the toolkit to a specific actor; detailed timeline of the toolkit’s deployment across different targets.
- Bias & Deception Risks: Potential confirmation bias in attributing the attack to a state actor based on language; risk of deception through false flag operations.
4. Implications and Strategic Risks
This development highlights vulnerabilities in virtualized environments, potentially encouraging similar attacks. The geopolitical implications could strain relations if state involvement is confirmed.
- Political / Geopolitical: Potential diplomatic tensions if state sponsorship is established, particularly involving China.
- Security / Counter-Terrorism: Increased threat to critical infrastructure and sensitive data across sectors reliant on VMware.
- Cyber / Information Space: Escalation in cyber capabilities and tactics, prompting a reevaluation of cybersecurity protocols.
- Economic / Social: Potential economic impact on organizations due to data breaches and system downtimes.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch affected VMware systems; enhance monitoring for unusual activity; conduct forensic analysis on compromised systems.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing; invest in advanced cybersecurity training and tools; review and update incident response plans.
- Scenario Outlook: Best: Rapid patching and collaboration mitigate further attacks. Worst: Attribution leads to geopolitical conflict. Most-Likely: Continued cyber threats necessitate ongoing vigilance and adaptation.
6. Key Individuals and Entities
- Anna Pham, Researcher, Huntress
- Matt Anderson, Researcher, Huntress
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, state-sponsored threats, VMware vulnerabilities, virtual machine escape, zero-day exploits, Chinese-speaking regions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us