FBI Alerts on North Korean QR Code Phishing Attacks Targeting U.S. Government and Institutions
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: North Korean hackers using malicious QR codes in spear phishing FBI warns
1. BLUF (Bottom Line Up Front)
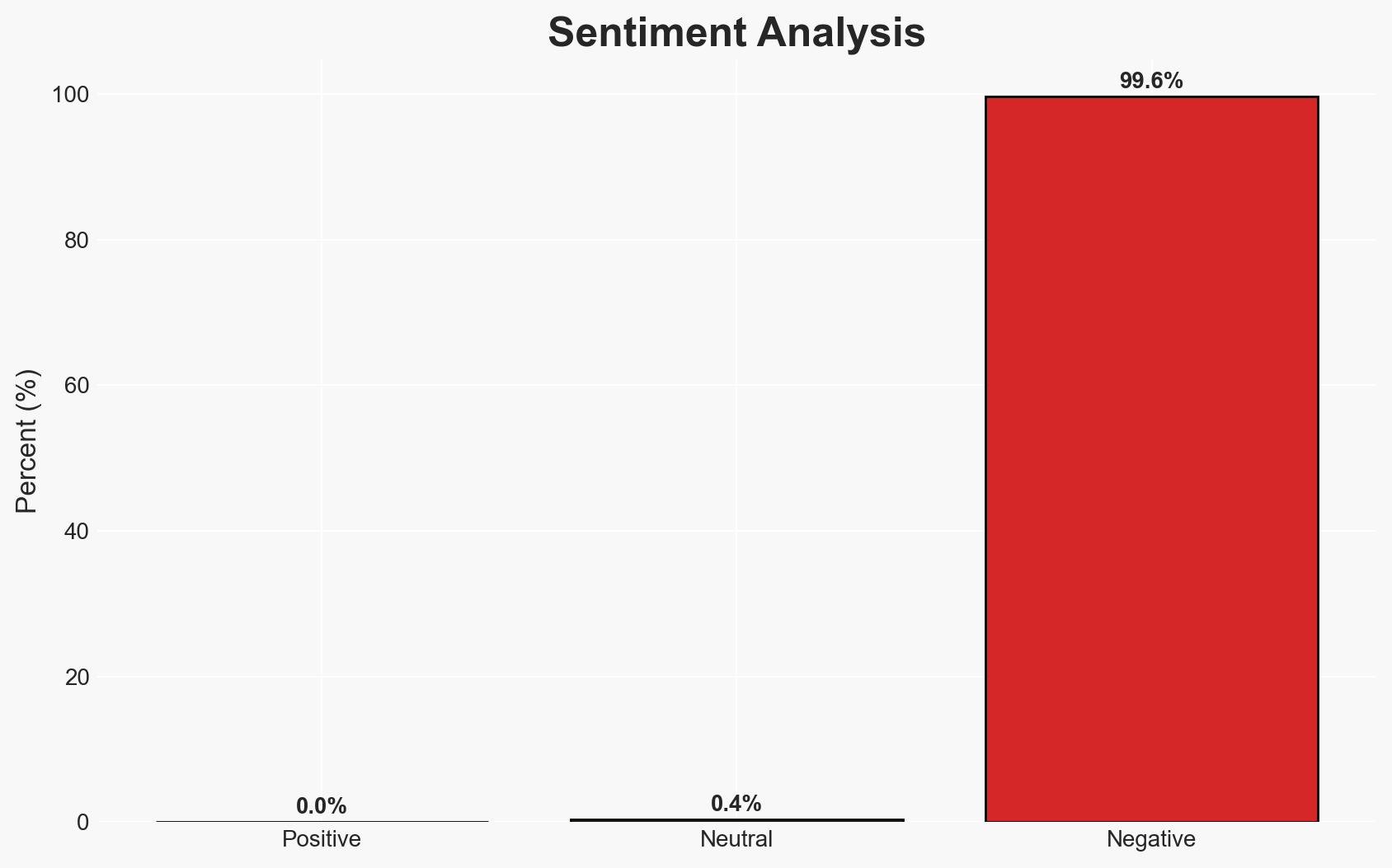
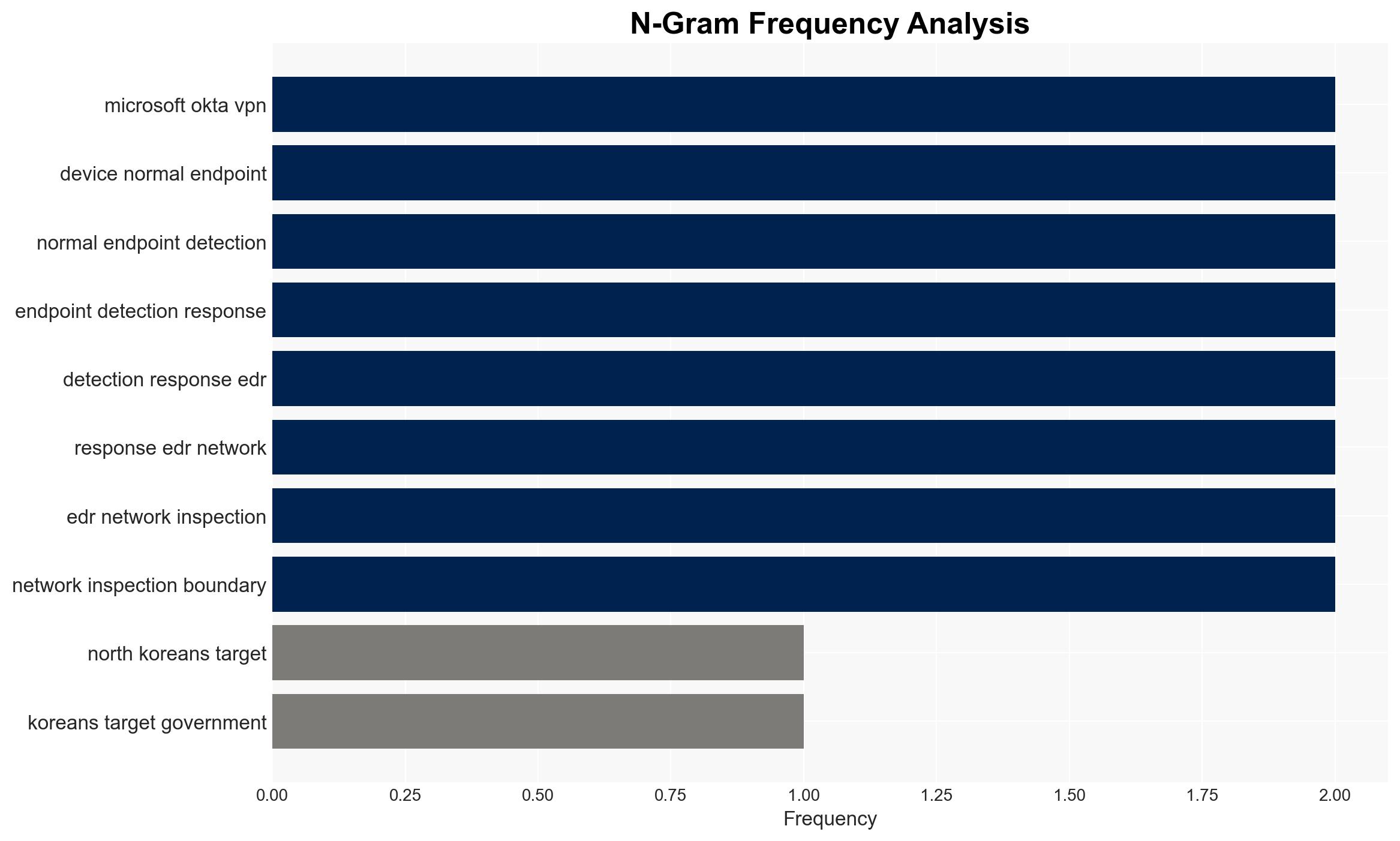
North Korean threat actor Kimsuky is conducting sophisticated QR code phishing attacks targeting U.S. government institutions, think tanks, and academia to compromise credentials and bypass multi-factor authentication. The attacks exploit vulnerabilities in mobile device security, posing a significant threat to enterprise environments. Overall confidence in this assessment is moderate, given the reliance on FBI reporting and the evolving nature of cyber threats.
2. Competing Hypotheses
- Hypothesis A: Kimsuky is primarily targeting U.S. entities to gather intelligence and disrupt operations. This is supported by the specificity of targets and the sophistication of the attack method. However, the exact scale and success rate of these attacks remain uncertain.
- Hypothesis B: The attacks are part of a broader campaign aimed at testing and refining cyber capabilities for future operations. This is plausible given North Korea’s history of using cyber operations for multiple strategic objectives, though direct evidence linking this campaign to broader strategic goals is limited.
- Assessment: Hypothesis A is currently better supported due to the targeted nature of the attacks and the immediate operational objectives. Indicators such as increased targeting of similar sectors or shifts in attack methodology could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Kimsuky has the technical capability to execute these attacks; U.S. entities remain primary targets; mobile device security is a critical vulnerability.
- Information Gaps: Detailed metrics on the success rate of these attacks; comprehensive understanding of North Korea’s strategic objectives related to this campaign.
- Bias & Deception Risks: Potential over-reliance on FBI reporting; possibility of misattribution or exaggeration of threat actor capabilities.
4. Implications and Strategic Risks
This development could lead to increased sophistication in phishing techniques and broader adoption of similar tactics by other threat actors. It may also prompt a reevaluation of mobile device security policies and practices.
- Political / Geopolitical: Potential escalation in cyber tensions between the U.S. and North Korea, influencing diplomatic relations.
- Security / Counter-Terrorism: Increased threat to critical infrastructure and sensitive information, necessitating enhanced defensive measures.
- Cyber / Information Space: Evolution of phishing tactics, highlighting the need for adaptive cybersecurity strategies and awareness.
- Economic / Social: Potential economic impact on targeted sectors, with possible disruptions to operations and increased cybersecurity costs.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of QR code-related activities; increase employee training on phishing awareness; implement mobile device management solutions.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing on cyber threats; invest in advanced threat detection and response capabilities; review and update security protocols.
- Scenario Outlook:
- Best: Successful mitigation of current threats with no significant breaches.
- Worst: Major breach leading to significant data loss and operational disruption.
- Most-Likely: Continued attempts with incremental improvements in defense and detection capabilities.
6. Key Individuals and Entities
- Kimsuky (North Korean threat actor group)
- Federal Bureau of Investigation (FBI)
- U.S. government institutions, think tanks, academia (targets)
7. Thematic Tags
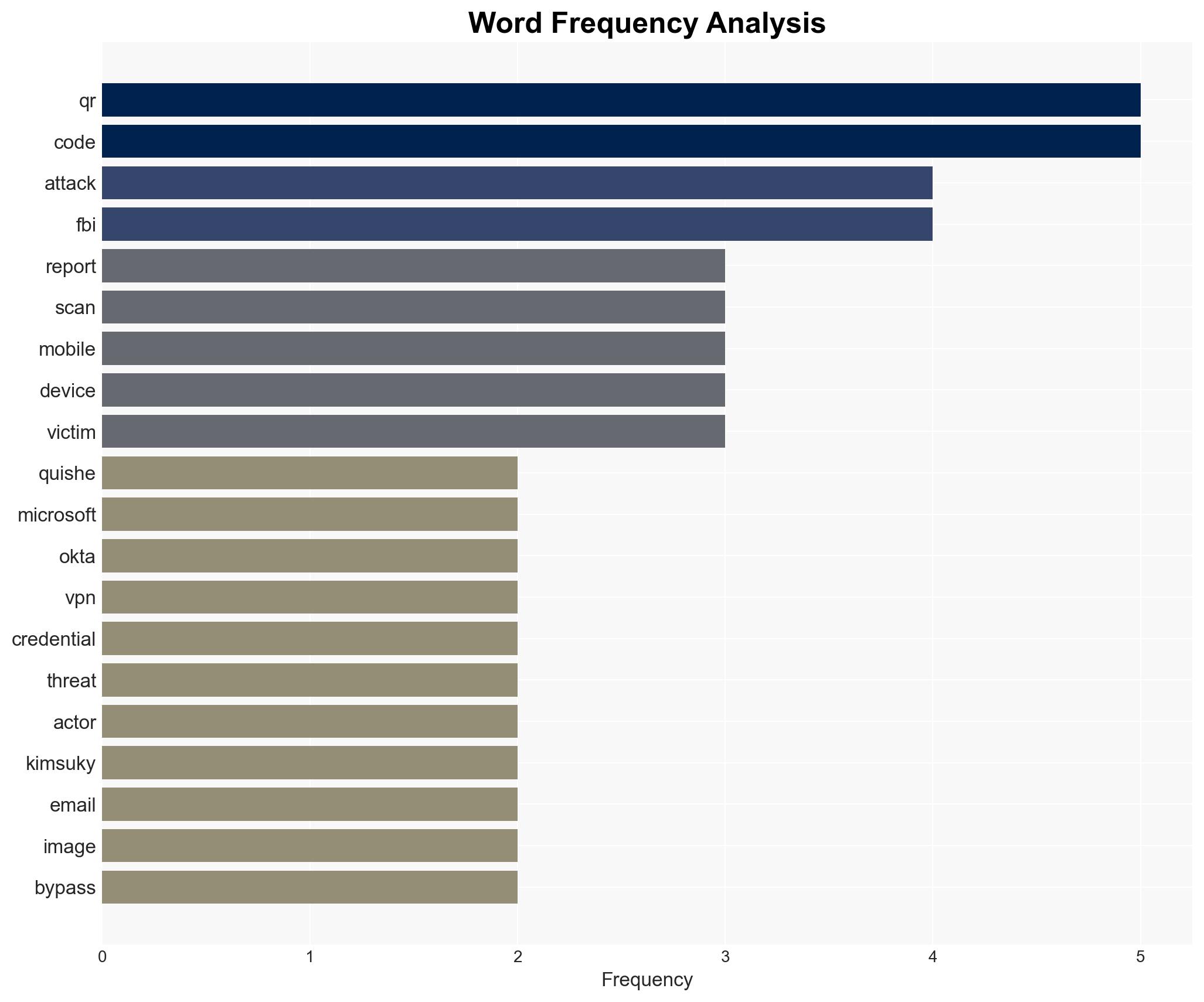
cybersecurity, cyber-espionage, phishing, North Korea, mobile security, credential theft, multi-factor authentication, cybersecurity strategy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us