F5 Inc Faces Securities Class Action After Cybersecurity Incident Reveals Financial Impact on Investors
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: F5 Inc FFIV Cybersecurity Incident-Related Securities Class Action Pending As Adverse Financial Impact Clarified Hagens Berman
1. BLUF (Bottom Line Up Front)
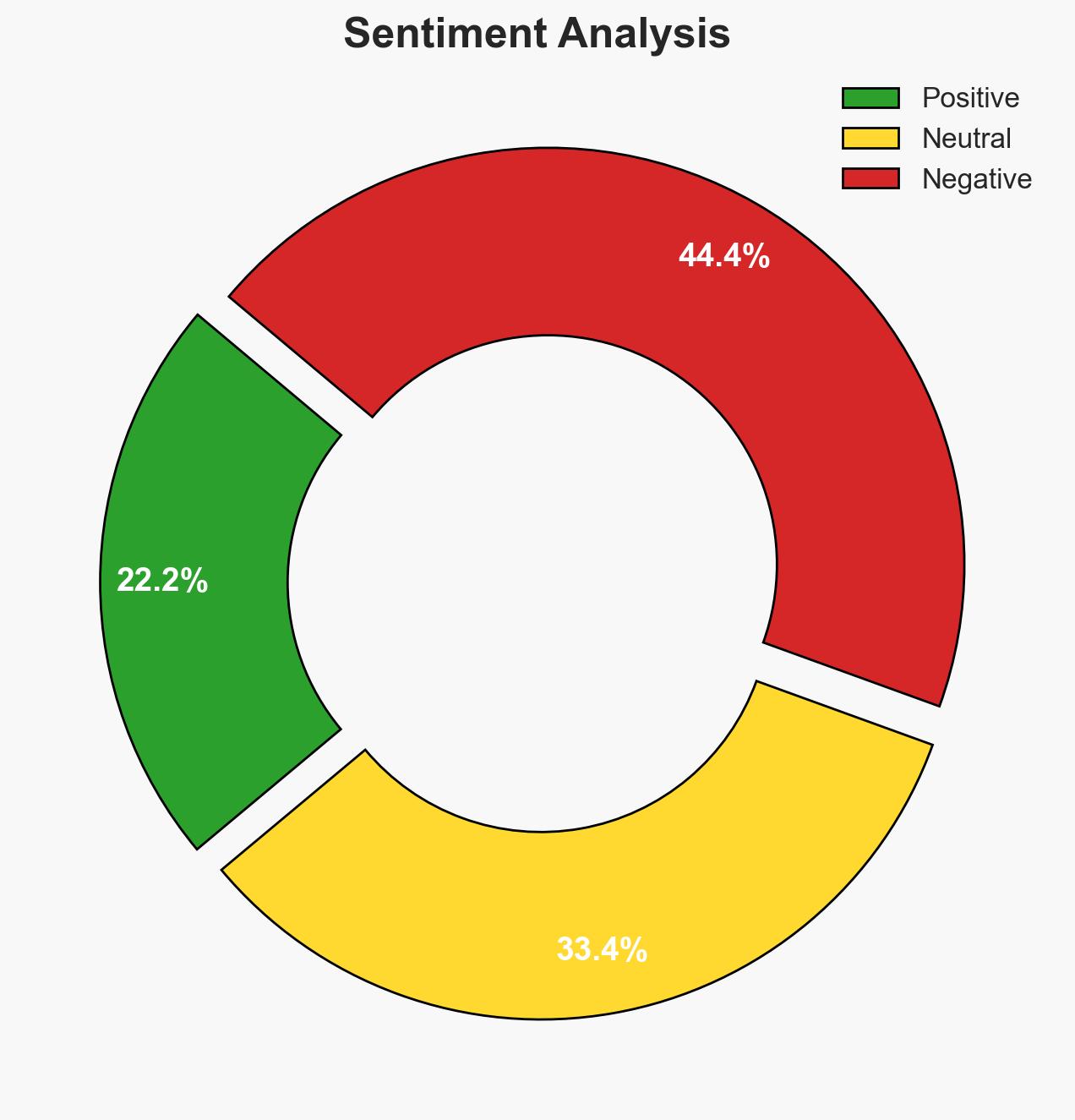
F5 Inc. is facing a securities class action lawsuit following a significant cybersecurity breach that impacted its financial projections and stock price. The breach, attributed to a nation-state actor, compromised the BIG-IP product’s source code. The primary hypothesis is that F5 management delayed disclosure of the breach, impacting investor trust and financial stability. Confidence in this judgment is moderate due to incomplete information on internal decision-making processes.
2. Competing Hypotheses
- Hypothesis A: F5 Inc. intentionally delayed disclosing the cybersecurity breach to mitigate immediate financial and reputational damage. Supporting evidence includes the timing of disclosures and subsequent stock price declines. Key uncertainties involve the internal decision-making timeline and motivations.
- Hypothesis B: F5 Inc. promptly disclosed the breach upon confirming its full impact, with delays attributed to the complexity of assessing the breach’s scope. This is supported by the sophisticated nature of the threat actor and the technical challenges in breach assessment.
- Assessment: Hypothesis A is currently better supported due to the significant gap between breach discovery and public disclosure, coupled with the financial impact on stock prices. Indicators such as internal communications or whistleblower accounts could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: F5’s internal security protocols were insufficient to detect the breach earlier; the breach’s financial impact was significant enough to warrant earlier disclosure; F5 management had full knowledge of the breach’s implications by October 2025.
- Information Gaps: Lack of detailed internal communications regarding the breach timeline; absence of third-party forensic analysis reports; unclear extent of the breach’s impact on F5’s product security.
- Bias & Deception Risks: Potential bias in F5’s public statements to minimize perceived impact; risk of deception by the threat actor regarding the breach’s scope and intent.
4. Implications and Strategic Risks
The cybersecurity incident at F5 Inc. could lead to long-term reputational damage, affecting customer trust and market position. The incident may also prompt regulatory scrutiny and impact investor confidence.
- Political / Geopolitical: Potential for increased scrutiny on nation-state cyber activities and calls for international cooperation on cybersecurity standards.
- Security / Counter-Terrorism: Heightened awareness of vulnerabilities in critical infrastructure products, possibly influencing national security policies.
- Cyber / Information Space: Increased focus on securing software development environments and source code integrity across the industry.
- Economic / Social: Potential for decreased investor confidence in tech firms’ cybersecurity capabilities, impacting stock markets and investment strategies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor F5’s public statements and legal proceedings; engage with cybersecurity experts to assess potential industry-wide impacts.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to enhance threat detection capabilities; advocate for industry-wide cybersecurity best practices.
- Scenario Outlook:
- Best Case: F5 resolves the lawsuit with minimal financial impact and strengthens its cybersecurity posture, restoring investor confidence.
- Worst Case: Ongoing legal and financial repercussions lead to significant market share loss and long-term reputational damage.
- Most Likely: F5 faces moderate financial penalties and implements improved security measures, with gradual recovery of investor trust.
6. Key Individuals and Entities
- F5 Inc. (FFIV)
- Hagens Berman (Shareholder rights firm)
- Reed Kathrein (Hagens Berman partner leading the investigation)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, nation-state threat, financial impact, investor confidence, legal proceedings, source code breach, corporate governance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us