Bandits Storm Kwara Palace, Kidnap Monarch’s Family Members During Festive Season Raid
Published on: 2026-01-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: How bandits walked into Kwara palace kidnapped monarchs seven family members Vigilante leader
1. BLUF (Bottom Line Up Front)
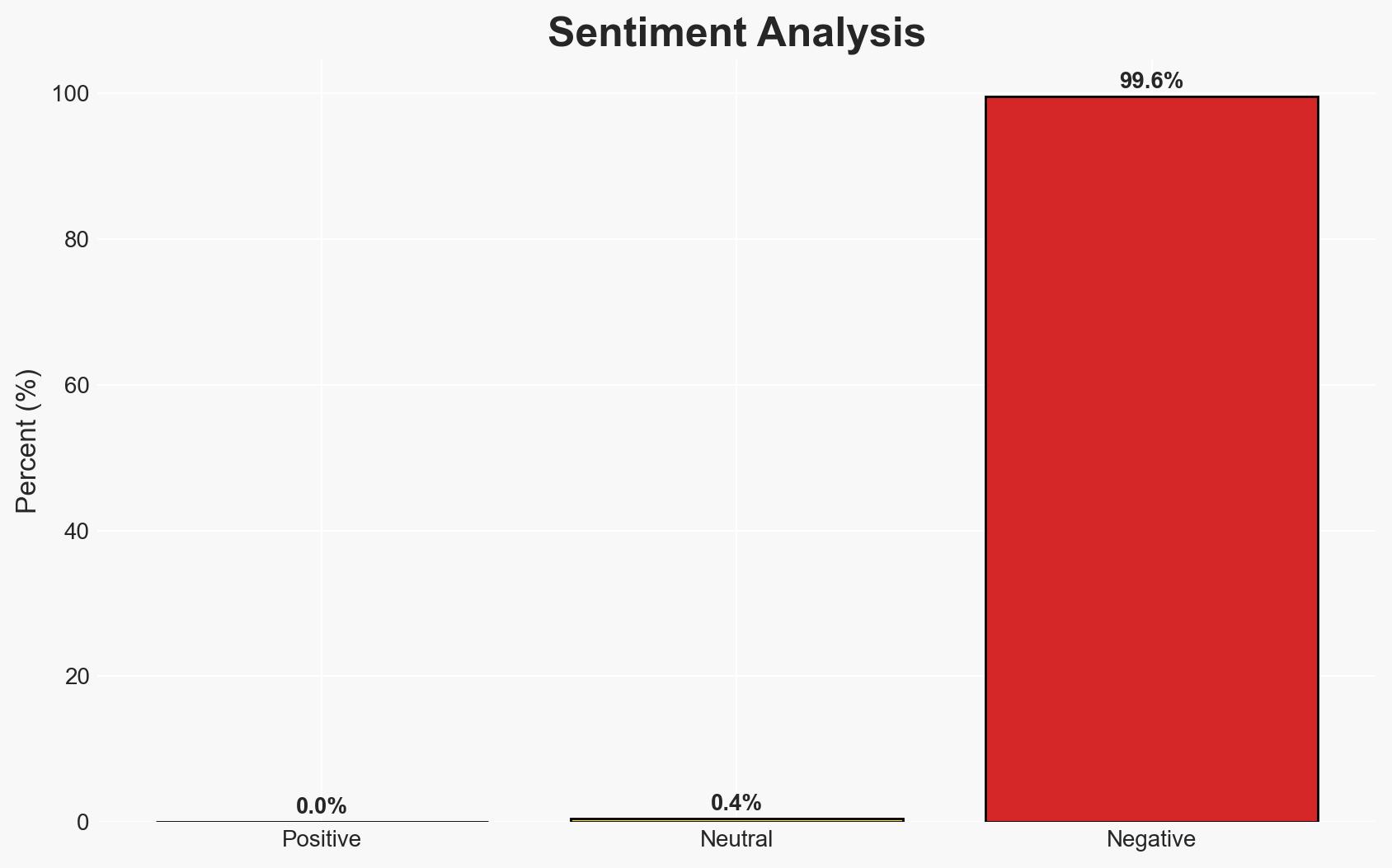
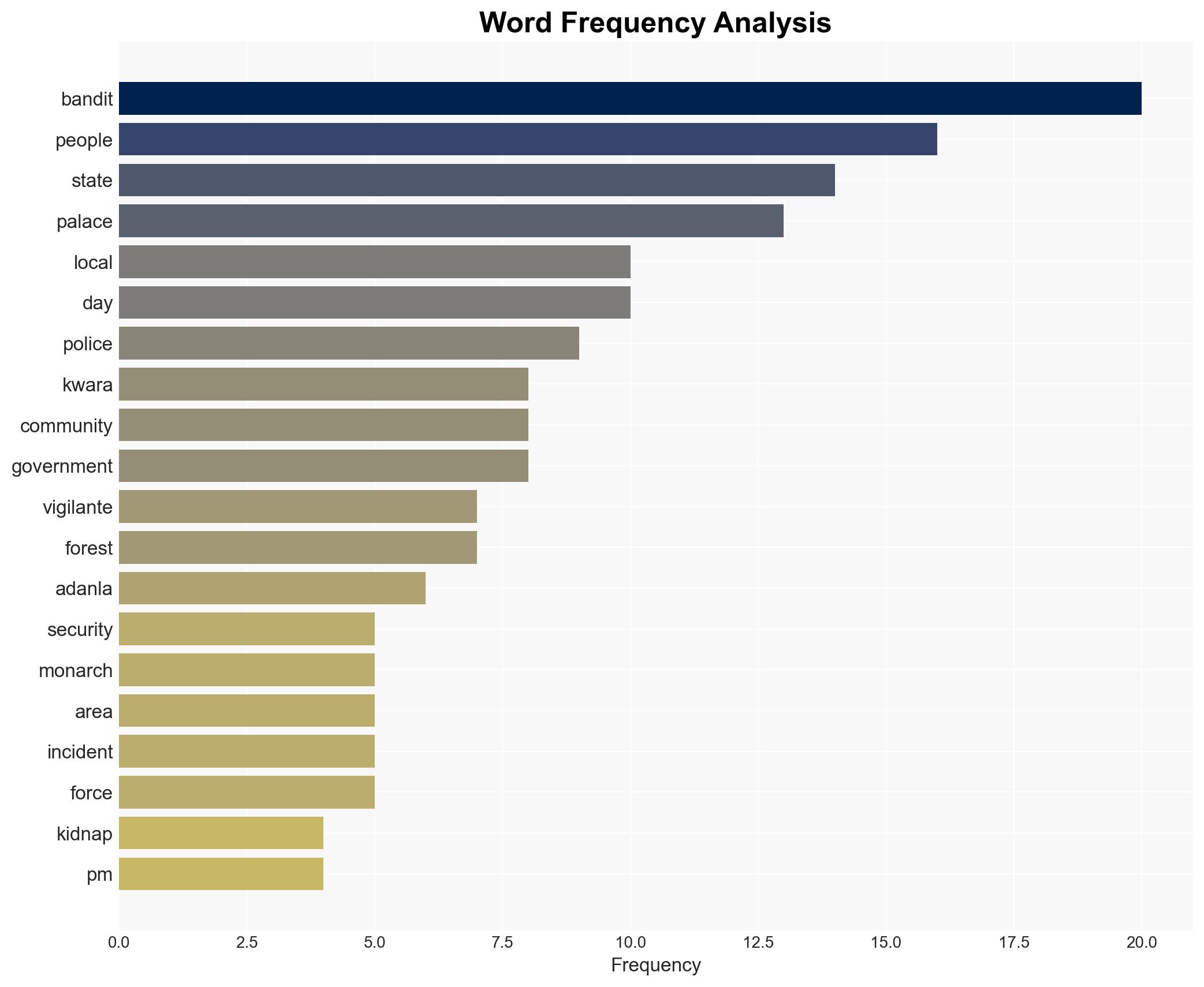
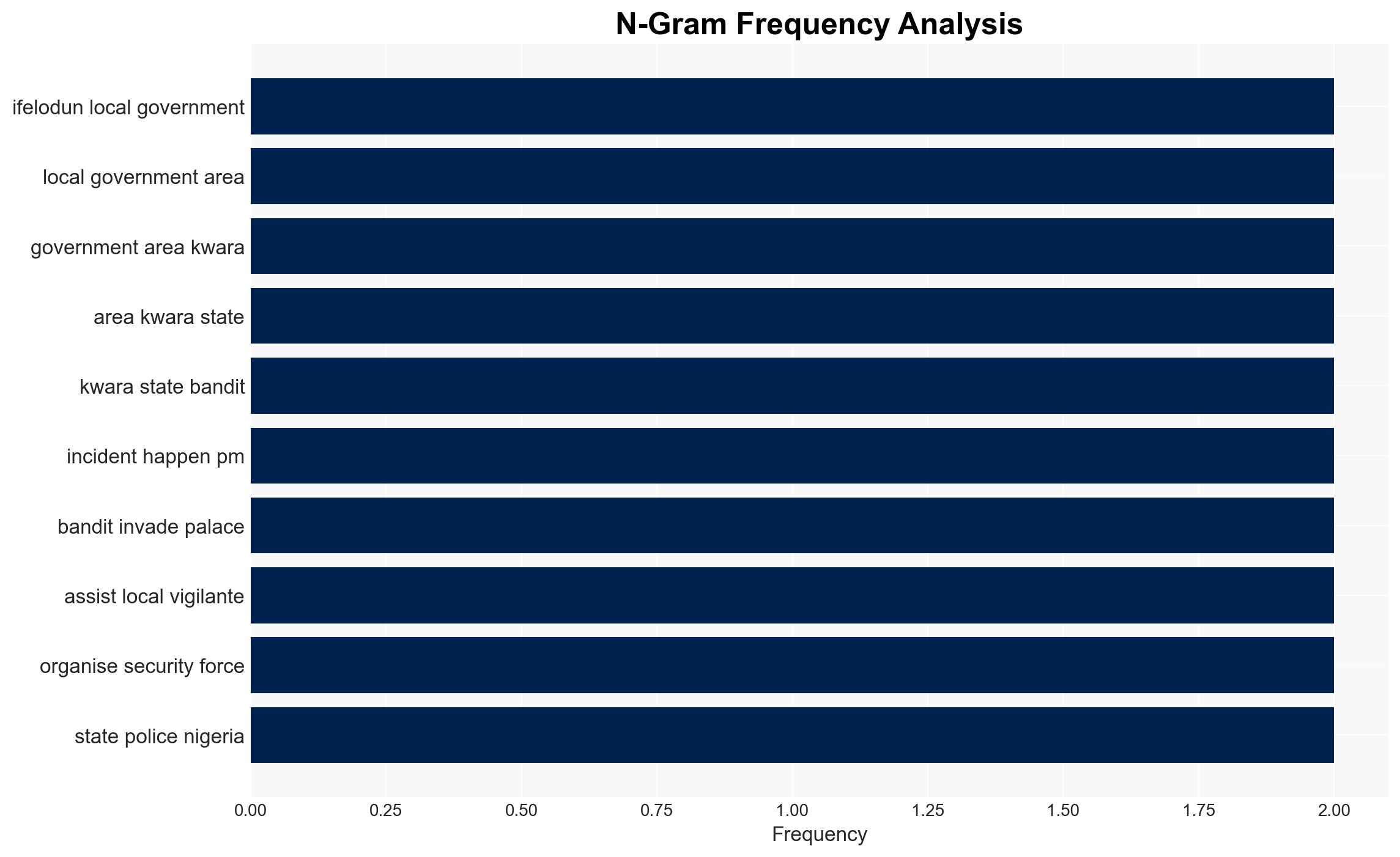
The abduction of seven royal family members from the Kwara State palace by bandits on December 26, 2025, highlights significant security vulnerabilities in the region. The incident suggests a potential increase in organized criminal activities targeting high-profile individuals. The most supported hypothesis is that the bandits are part of a local criminal group exploiting security gaps. Overall confidence in this judgment is moderate, given the lack of detailed intelligence on the perpetrators.
2. Competing Hypotheses
- Hypothesis A: The bandits are a local criminal group exploiting security lapses in the region. This is supported by the methodical nature of the attack and previous similar incidents in the area. However, the lack of immediate identification of the group introduces uncertainty.
- Hypothesis B: The attack was orchestrated by an external group with broader political motives, possibly to destabilize the region. This is less supported due to the absence of evidence linking the incident to political objectives.
- Assessment: Hypothesis A is currently better supported due to the pattern of local criminal activity and the absence of political demands. Key indicators that could shift this judgment include evidence of external funding or political statements from the perpetrators.
3. Key Assumptions and Red Flags
- Assumptions: The bandits had prior knowledge of the palace’s security weaknesses; the incident is primarily criminal rather than politically motivated; local security forces lack the capacity to prevent such attacks.
- Information Gaps: Detailed profiles of the bandits, their organizational structure, and potential external support remain unknown.
- Bias & Deception Risks: Potential bias in local reporting may underplay political motives; eyewitness accounts may be unreliable due to fear or coercion.
4. Implications and Strategic Risks
This development could lead to increased criminal activities and further destabilization of the region if not addressed. It may also embolden other groups to exploit similar vulnerabilities.
- Political / Geopolitical: Potential for increased pressure on local government to enhance security measures, risking political instability if perceived as ineffective.
- Security / Counter-Terrorism: Likely increase in security operations and community vigilance, but also potential for retaliatory violence by bandits.
- Cyber / Information Space: Possible misinformation campaigns to exploit the incident for political gain or to sow discord.
- Economic / Social: Economic strain due to ransom demands and potential decline in local business confidence; social unrest if security concerns persist.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance local intelligence gathering and community engagement to identify the bandits; increase visible security presence in vulnerable areas.
- Medium-Term Posture (1–12 months): Develop partnerships with regional security forces to improve response capabilities; invest in community-based security initiatives.
- Scenario Outlook:
- Best: Successful identification and apprehension of the bandits, leading to improved regional security.
- Worst: Escalation of criminal activities and potential spillover into neighboring regions.
- Most-Likely: Continued sporadic incidents with gradual improvements in security response.
6. Key Individuals and Entities
- His Royal Majesty Oba David Adedumoye, Elerin of Adanla Irese
- Mr. Olaitan Oyin-Zubair, Coordinator of the Kwara South Joint Community Security Watch Network
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
national security threats, organized crime, regional security, kidnapping, local governance, community policing, ransom demands, Nigeria
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us