FBI Alerts on Kimsuky APT’s Quishing Attacks Targeting Governments and Institutions
Published on: 2026-01-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
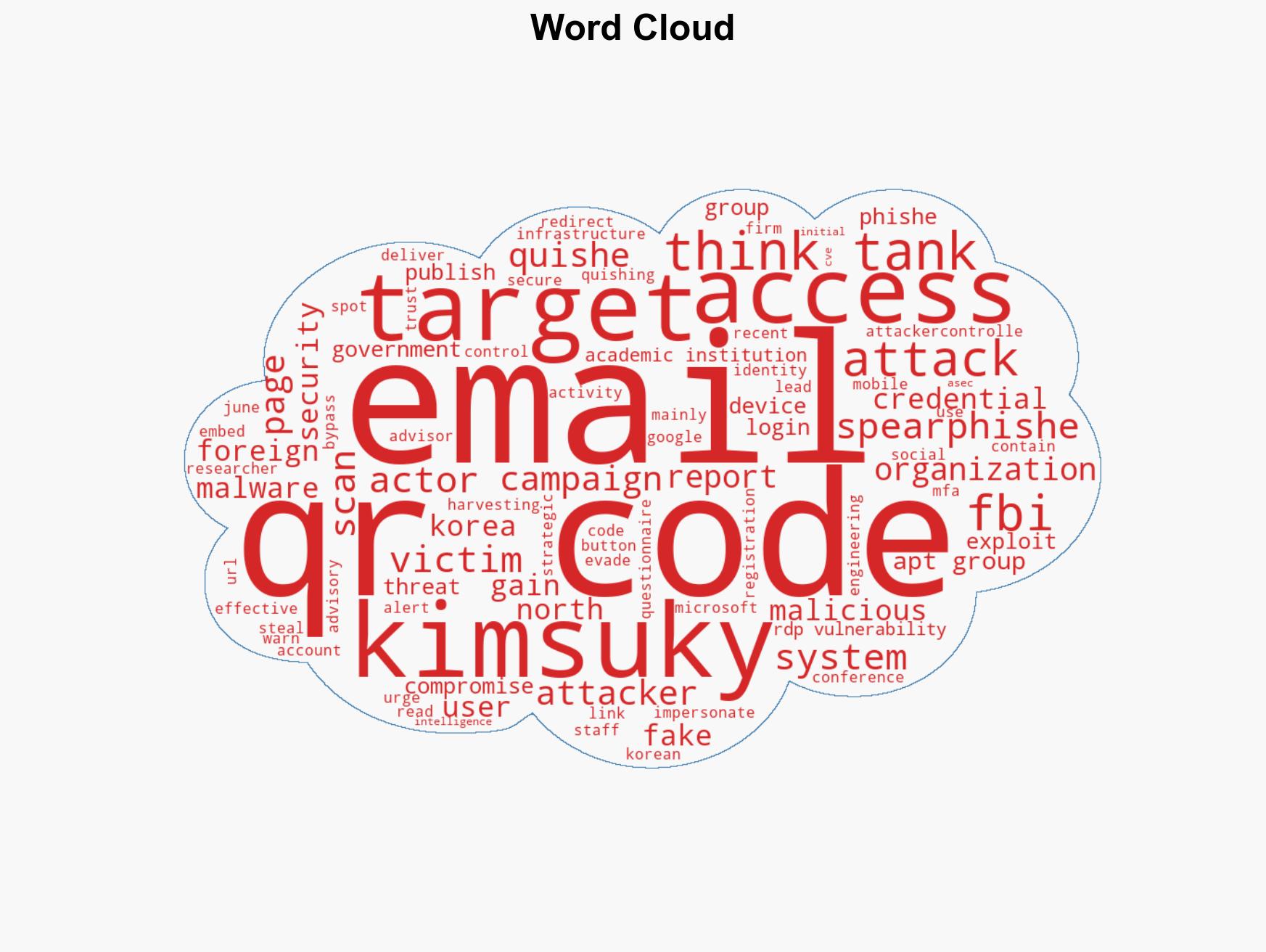
Intelligence Report: North Korealinked APT Kimsuky behind quishing attacks FBI warns
1. BLUF (Bottom Line Up Front)
The FBI has identified the North Korean APT group Kimsuky as responsible for sophisticated quishing attacks targeting government, academic, and think tank sectors. These attacks exploit QR codes to bypass traditional security measures, posing a significant threat to credential security and organizational integrity. The most likely hypothesis is that these attacks are part of a broader North Korean cyber-espionage campaign. Overall confidence in this assessment is moderate due to limited direct evidence of state sponsorship.
2. Competing Hypotheses
- Hypothesis A: Kimsuky is conducting quishing attacks as part of a state-sponsored cyber-espionage campaign aimed at gathering intelligence from strategic sectors. This is supported by the targeting of government and academic institutions and the sophistication of the attacks. However, direct evidence linking these activities to the North Korean state remains limited.
- Hypothesis B: Kimsuky is operating independently or as a proxy for non-state actors interested in financial gain or other non-political objectives. This hypothesis is less supported given the strategic nature of the targets and the complexity of the operations, which align more closely with state-level objectives.
- Assessment: Hypothesis A is currently better supported due to the alignment of targets and methods with known state-sponsored cyber-espionage objectives. Indicators that could shift this judgment include evidence of financial motivations or links to non-state actors.
3. Key Assumptions and Red Flags
- Assumptions: Kimsuky has the capability to conduct sophisticated cyber operations; the group’s activities are aligned with North Korean state interests; QR code vulnerabilities are not widely mitigated across targeted sectors.
- Information Gaps: Direct evidence of North Korean state sponsorship; comprehensive data on the full scope of affected entities; technical details of the QR code exploitation methods.
- Bias & Deception Risks: Confirmation bias in attributing cyber activities to state actors; potential misinformation from sources with vested interests in attributing attacks to North Korea.
4. Implications and Strategic Risks
The evolution of quishing attacks by Kimsuky could lead to increased sophistication in cyber-espionage tactics, potentially affecting global cyber security dynamics and prompting escalated cyber defenses.
- Political / Geopolitical: Potential escalation in cyber tensions between North Korea and targeted nations, influencing diplomatic relations.
- Security / Counter-Terrorism: Increased threat to national security infrastructure and potential for compromised sensitive information.
- Cyber / Information Space: Enhanced focus on QR code security measures and the development of countermeasures against quishing attacks.
- Economic / Social: Possible economic impacts due to compromised intellectual property and increased costs for cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement enhanced QR code scanning protocols; conduct awareness training on quishing risks; increase monitoring of suspicious email activities.
- Medium-Term Posture (1–12 months): Develop partnerships for intelligence sharing on cyber threats; invest in advanced threat detection technologies; enhance resilience against identity-based attacks.
- Scenario Outlook:
- Best: Successful mitigation of quishing threats leads to reduced impact on targeted sectors.
- Worst: Escalation of cyber-espionage activities results in significant breaches and geopolitical tensions.
- Most-Likely: Continued quishing attempts with incremental improvements in defensive measures.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, North Korea, quishing, APT groups, information security, state-sponsored attacks
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us