Trend Micro Apex Central RCE PoC Released Amid Patch Tuesday Insights and Cybersecurity Trends
Published on: 2026-01-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Week in review PoC for Trend Micro Apex Central RCE released Patch Tuesday forecast
1. BLUF (Bottom Line Up Front)
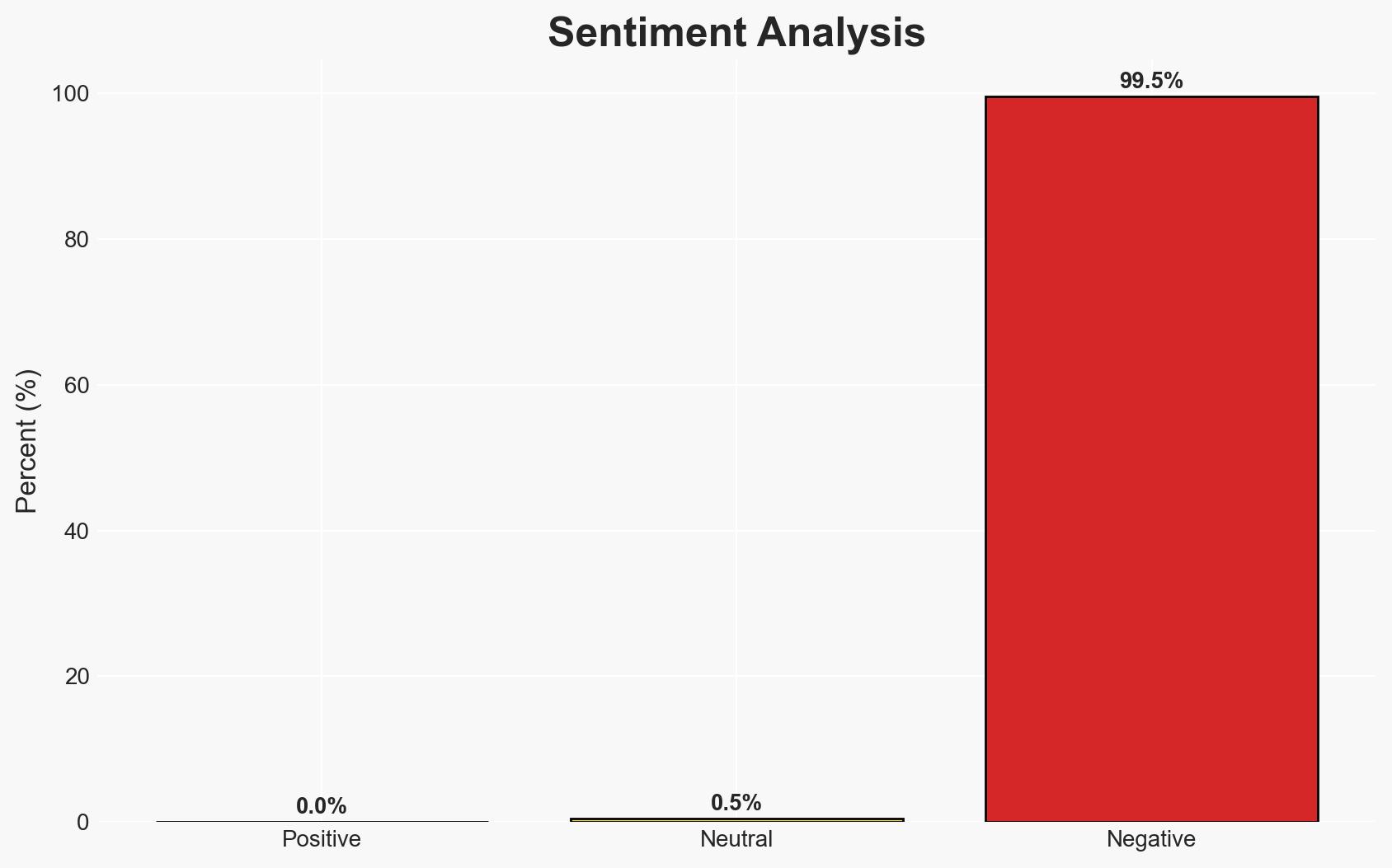
The release of a proof of concept (PoC) for an unauthenticated remote code execution (RCE) vulnerability in Trend Micro Apex Central poses a significant cyber risk, particularly for organizations using on-premise solutions. The vulnerability, if exploited, could lead to unauthorized access and control over affected systems. This development, alongside other cyber threats such as targeted malware campaigns, underscores the need for enhanced cybersecurity measures. Overall confidence in this assessment is moderate, given the available information and potential for exploitation.
2. Competing Hypotheses
- Hypothesis A: The PoC release for the Trend Micro Apex Central RCE will lead to widespread exploitation by cybercriminals, resulting in significant breaches. This is supported by the critical nature of the vulnerability and the historical pattern of rapid exploitation following PoC releases. However, the extent of exploitation depends on the speed and effectiveness of patch deployment by affected organizations.
- Hypothesis B: Organizations will quickly apply the patch, minimizing the impact of the vulnerability. This hypothesis is supported by the proactive release of the patch by Trend Micro and the heightened awareness of cybersecurity risks. Contradicting this is the potential delay in patch application due to resource constraints or lack of awareness.
- Assessment: Hypothesis A is currently better supported due to the critical nature of the vulnerability and the typical lag in patch application across organizations. Key indicators that could shift this judgment include reports of successful patch deployment and reduced incident reports related to this vulnerability.
3. Key Assumptions and Red Flags
- Assumptions: Organizations are aware of the vulnerability and have the capability to apply patches promptly. Cybercriminals have the intent and capability to exploit the PoC.
- Information Gaps: The exact number of systems affected by the vulnerability and the speed of patch deployment across different sectors.
- Bias & Deception Risks: Potential underreporting of successful exploitations due to reputational concerns. Overreliance on vendor communications without independent verification.
4. Implications and Strategic Risks
The exploitation of the Trend Micro vulnerability could lead to significant data breaches and operational disruptions, particularly in sectors with critical infrastructure. The convergence of cybersecurity and compliance pressures may drive organizations to adopt more robust real-time governance frameworks.
- Political / Geopolitical: Increased cyber incidents could strain diplomatic relations, especially if state-sponsored actors are implicated.
- Security / Counter-Terrorism: Enhanced cyber threats may necessitate increased collaboration between intelligence agencies and private sector cybersecurity firms.
- Cyber / Information Space: The vulnerability highlights the persistent threat landscape and the need for continuous monitoring and rapid response capabilities.
- Economic / Social: Potential economic impacts from breaches, including financial losses and damage to organizational reputation, could affect market stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Organizations should prioritize patching affected systems, enhance monitoring for signs of exploitation, and review incident response plans.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing and invest in real-time governance tools to improve compliance and security posture.
- Scenario Outlook:
- Best: Rapid patch deployment mitigates the threat with minimal incidents.
- Worst: Widespread exploitation leads to significant breaches and operational disruptions.
- Most-Likely: Mixed outcomes with some sectors effectively mitigating the threat while others experience targeted attacks.
6. Key Individuals and Entities
- Trend Micro, CISA, Chirag Shah (Global Information Security Officer & DPO at Model N), Greg Pollock (Head of Research and Insights at UpGuard)
7. Thematic Tags
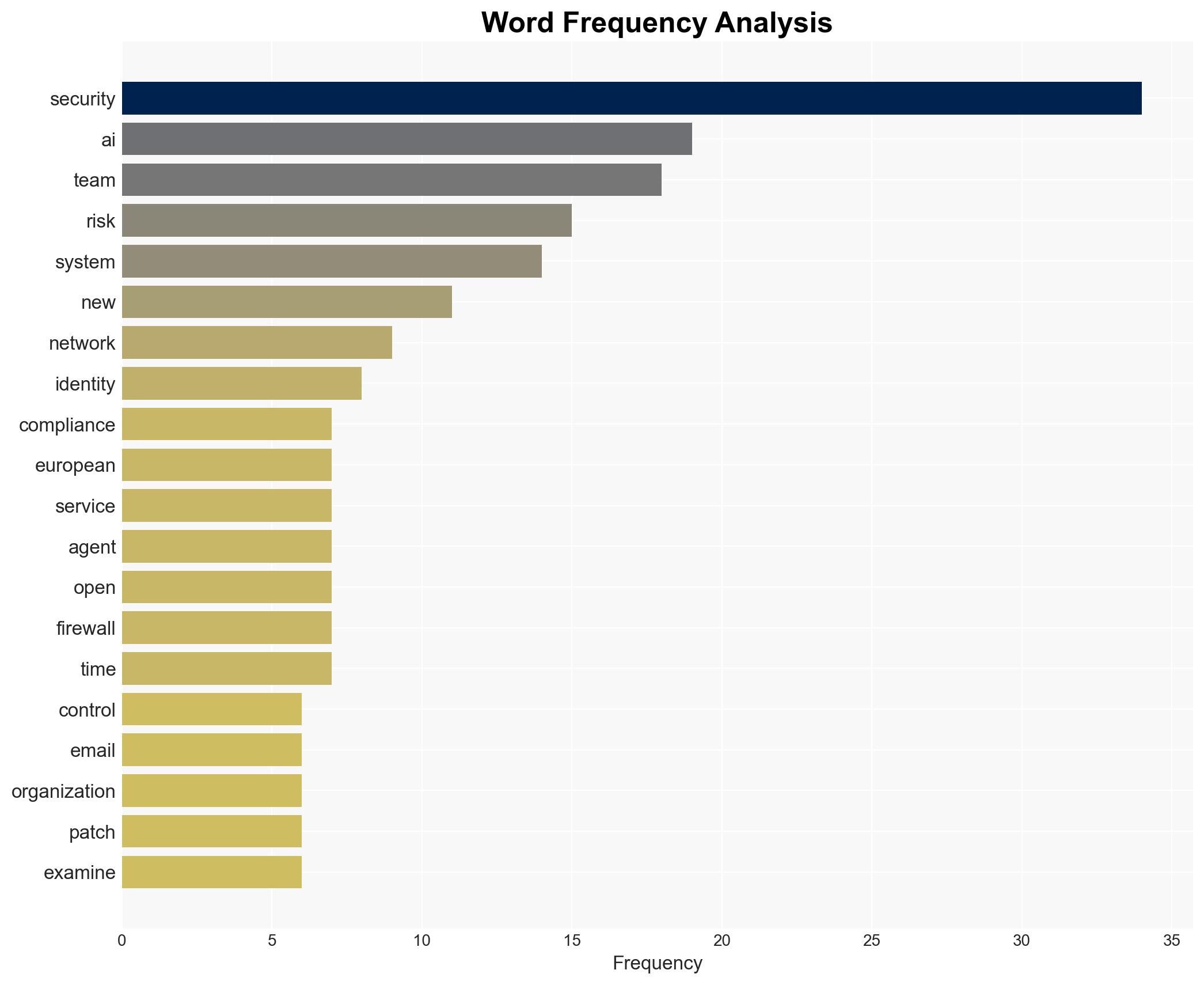
cybersecurity, remote code execution, vulnerability management, patch deployment, cyber threat intelligence, compliance risk, real-time governance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
- Cross-Impact Simulation: Simulate cascading interdependencies and system risks.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us