CISA Retires Ten Emergency Directives Following Successful Cyber Risk Mitigation Reviews
Published on: 2026-01-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA Closes Ten Emergency Directives After Federal Cyber Reviews
1. BLUF (Bottom Line Up Front)
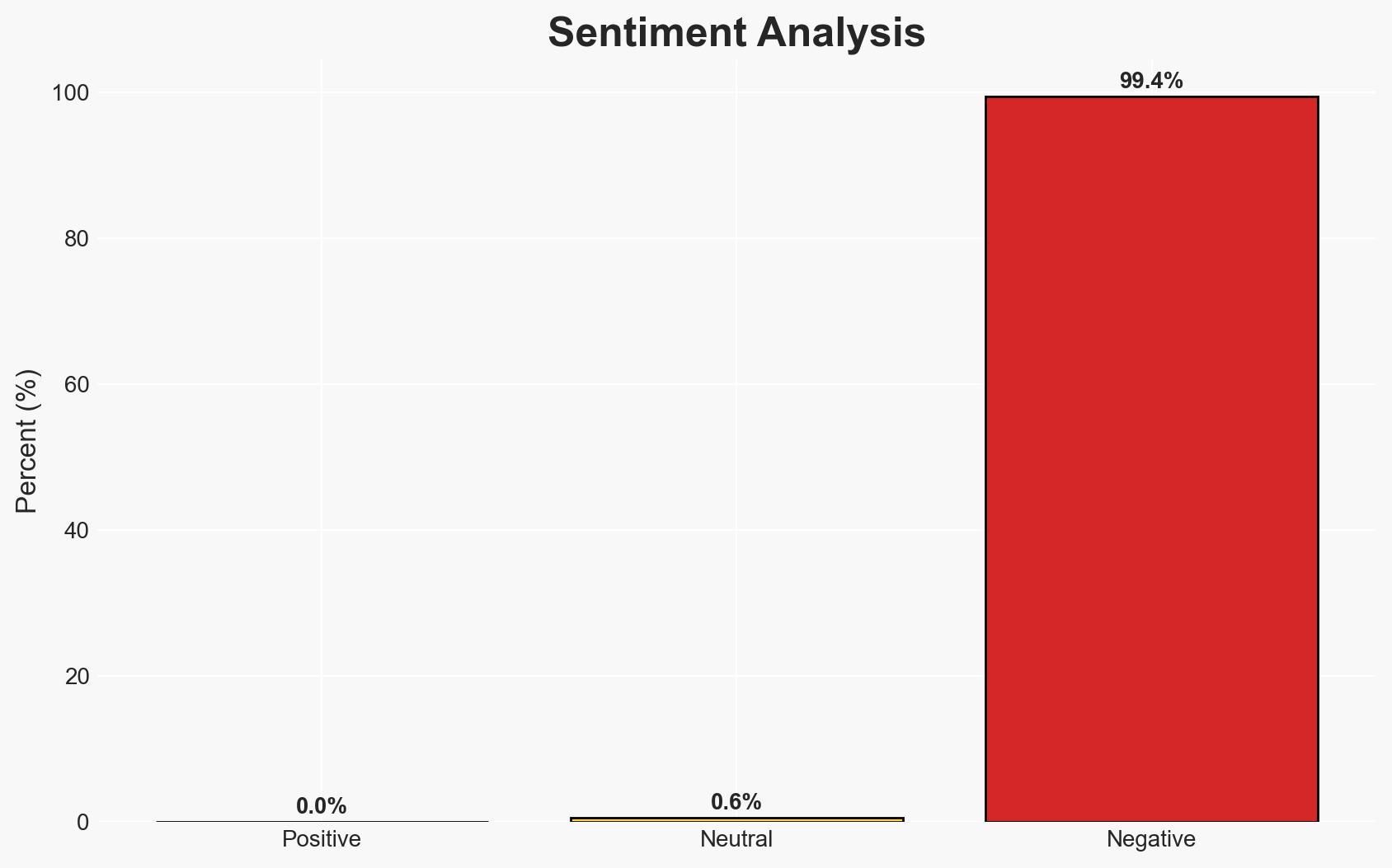
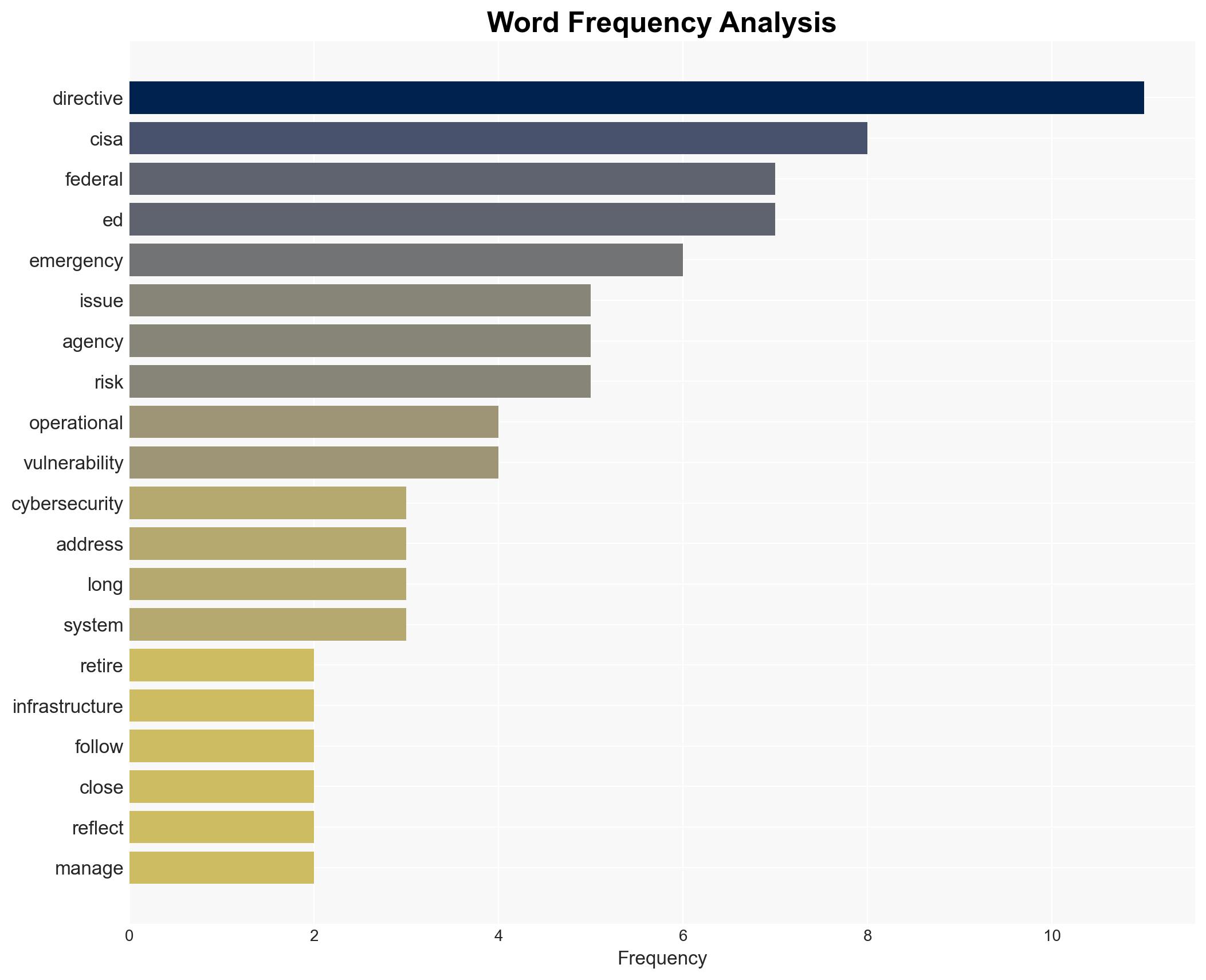
The US Cybersecurity and Infrastructure Security Agency (CISA) has retired ten Emergency Directives, indicating a shift towards standardized cybersecurity practices across federal agencies. This development suggests an improved federal cyber-risk management posture, though it may also expose gaps in addressing emerging threats. Overall, this assessment is made with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: The retirement of the directives reflects a genuine improvement in federal cybersecurity capabilities and risk management, supported by the integration of best practices and the transition to standardized directives. However, uncertainty exists regarding the adaptability of these measures to new threats.
- Hypothesis B: The closure of the directives may be premature, potentially leaving federal systems vulnerable to emerging threats not covered by existing measures. This hypothesis is less supported due to the reported full implementation of remediation actions.
- Assessment: Hypothesis A is currently better supported, as CISA’s actions align with reported improvements in cyber-risk management. Key indicators that could shift this judgment include the emergence of new vulnerabilities or a significant cyber incident affecting federal systems.
3. Key Assumptions and Red Flags
- Assumptions: Federal agencies have effectively implemented the required cybersecurity measures; CISA’s KEV catalog is comprehensive and up-to-date; the current risk posture accurately reflects the threat landscape.
- Information Gaps: Specific details on the implementation status of each directive across all agencies; metrics on the effectiveness of the KEV catalog in preventing incidents.
- Bias & Deception Risks: Potential over-reliance on self-reported compliance by agencies; confirmation bias in evaluating the effectiveness of standardized directives.
4. Implications and Strategic Risks
This development could lead to a more resilient federal cybersecurity posture but may also create overconfidence in existing measures, potentially overlooking emerging threats.
- Political / Geopolitical: Strengthened cybersecurity could enhance US diplomatic leverage in international cyber policy discussions.
- Security / Counter-Terrorism: Improved federal cybersecurity may reduce the risk of cyber-enabled terrorism targeting government infrastructure.
- Cyber / Information Space: The shift to standardized directives may streamline threat response but could also delay adaptation to novel threats.
- Economic / Social: Enhanced cybersecurity could bolster public trust in federal systems, indirectly supporting economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive review of the KEV catalog’s coverage and update it as necessary; enhance monitoring for new vulnerabilities.
- Medium-Term Posture (1–12 months): Develop partnerships with private sector cybersecurity firms to enhance threat intelligence sharing; invest in cybersecurity training for federal employees.
- Scenario Outlook:
- Best: Federal systems remain secure with no significant breaches, supported by proactive threat management.
- Worst: A major cyber incident occurs due to overlooked vulnerabilities, undermining confidence in federal cybersecurity.
- Most-Likely: Incremental improvements in cybersecurity posture continue, with occasional minor incidents prompting further refinement of directives.
6. Key Individuals and Entities
- Madhu Gottumukkala (Acting Director, CISA)
- US Cybersecurity and Infrastructure Security Agency (CISA)
- Federal Civilian Executive Branch Agencies
7. Thematic Tags
cybersecurity, federal agencies, risk management, emergency directives, CISA, vulnerabilities, cyber policy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us