Cybercriminals Exposed: BreachForums User Database Leaked Online
Published on: 2026-01-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers get hacked as BreachForums database is leaked
1. BLUF (Bottom Line Up Front)
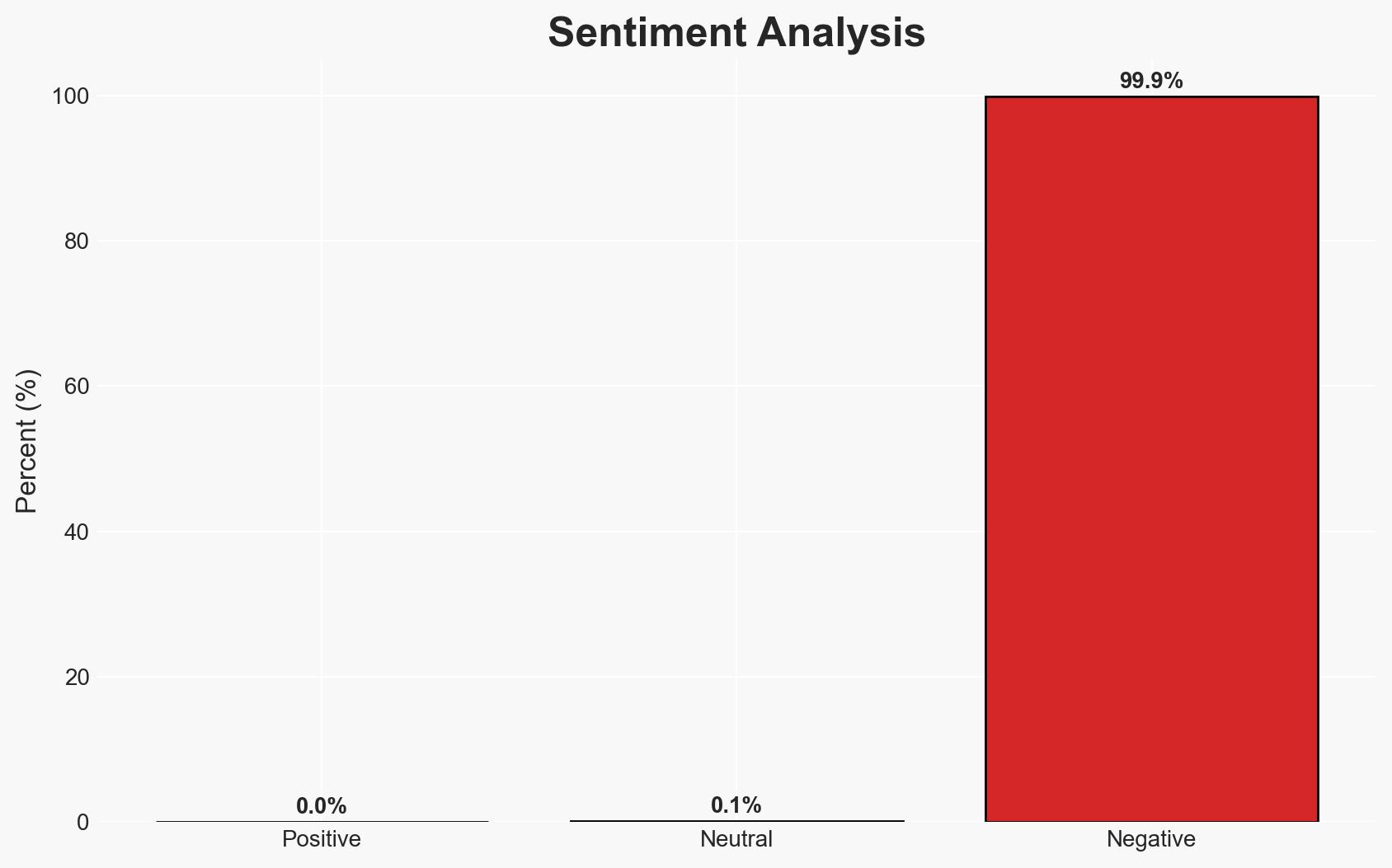
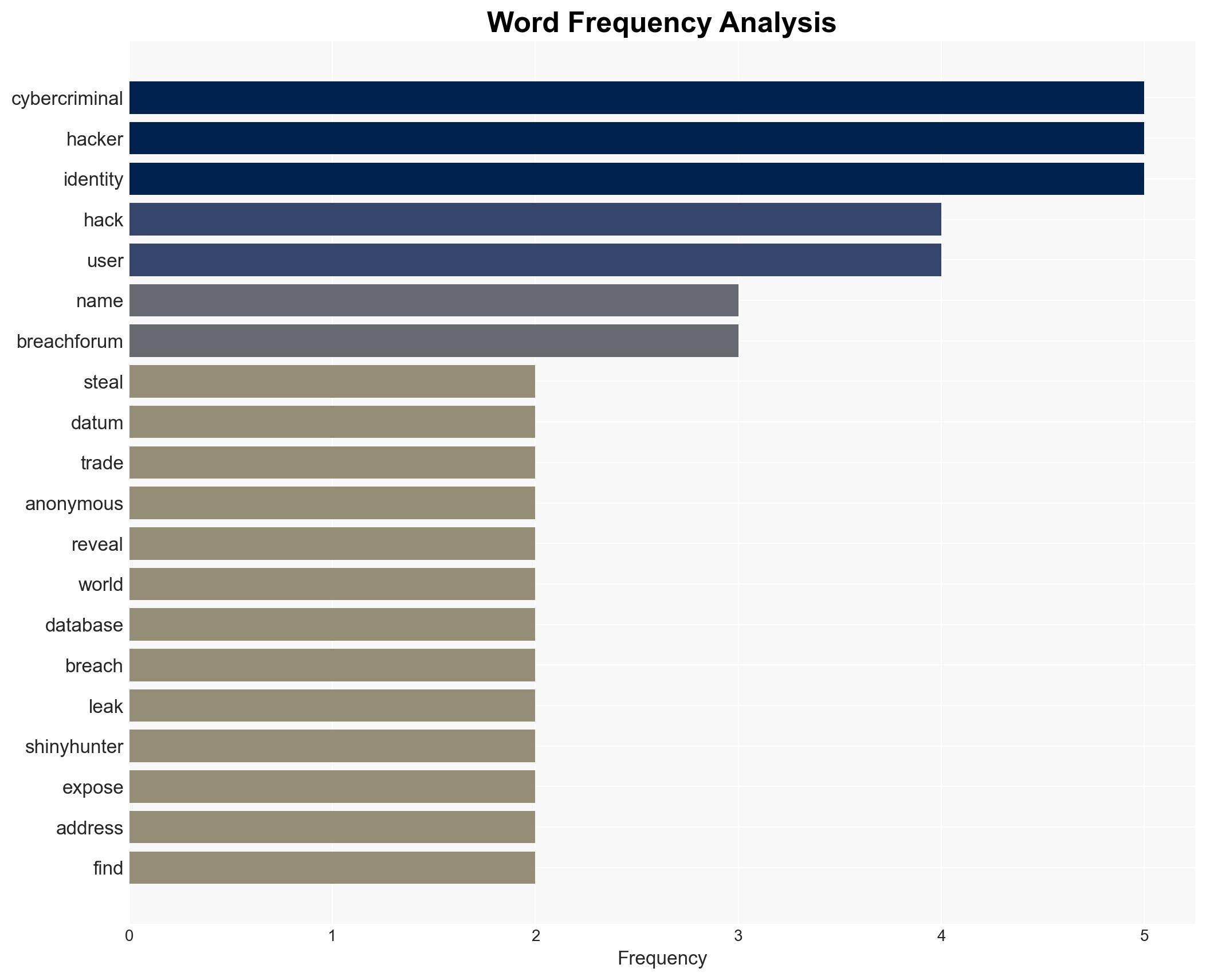
The breach of BreachForums’ user database represents a significant counter-cybercriminal event, potentially exposing numerous cybercriminals to law enforcement scrutiny. The most likely hypothesis is that this breach was orchestrated by a rival hacker or group with motivations to disrupt or retaliate against BreachForums users. This development affects cybercriminals globally and may lead to increased law enforcement actions. Overall confidence in this assessment is moderate due to uncertainties regarding the identity and motivations of the perpetrator.
2. Competing Hypotheses
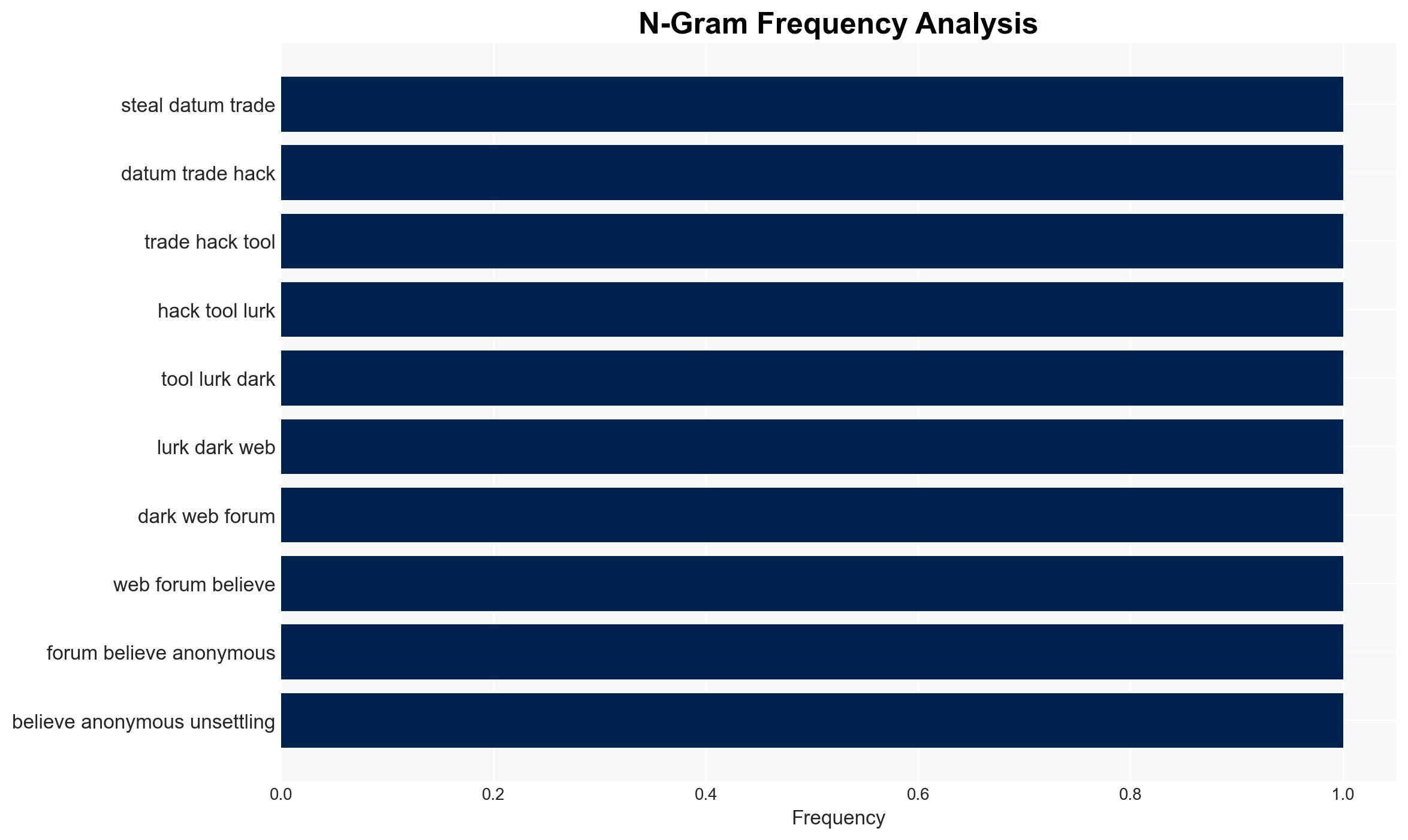
- Hypothesis A: The breach was conducted by a rival hacker or group aiming to undermine BreachForums and its users. Supporting evidence includes the leak’s publication on a site associated with known hacking groups and the manifesto’s tone, suggesting rivalry or retaliation. Key uncertainties include the true identity and motivations of “James.”
- Hypothesis B: The breach was an insider attack by a disgruntled former member of BreachForums. This is supported by the detailed knowledge and personal tone of the manifesto. Contradicting evidence includes the lack of clear insider indicators and the public nature of the leak.
- Assessment: Hypothesis A is currently better supported due to the external publication of the leak and the association with known hacking groups. Indicators that could shift this judgment include new evidence of insider involvement or further communications from “James.”
3. Key Assumptions and Red Flags
- Assumptions: The database leak is authentic; “James” is the sole actor behind the breach; law enforcement will act on the leaked data.
- Information Gaps: The true identity and motivations of “James”; the extent of law enforcement’s ability to leverage the leaked data.
- Bias & Deception Risks: Potential bias in interpreting “James’s” manifesto; risk of deception by the leaker to mislead about their identity or intentions.
4. Implications and Strategic Risks
This breach could lead to increased law enforcement actions against cybercriminals and disrupt the operations of BreachForums. It may also trigger retaliatory actions within the cybercriminal community.
- Political / Geopolitical: Potential for international cooperation in cybercrime investigations, but also risk of diplomatic tensions if state actors are implicated.
- Security / Counter-Terrorism: Enhanced law enforcement capabilities to track and arrest cybercriminals; potential for increased cybercriminal activity in response.
- Cyber / Information Space: Possible shifts in cybercriminal tactics to avoid detection; increased scrutiny of dark web forums.
- Economic / Social: Potential destabilization of cybercriminal markets; increased public awareness of cyber risks.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor dark web forums for retaliatory actions; enhance law enforcement collaboration to exploit the leaked data.
- Medium-Term Posture (1–12 months): Develop resilience measures against potential cybercriminal retaliation; strengthen partnerships with international cybercrime units.
- Scenario Outlook: Best: Significant arrests and disruption of cybercriminal networks; Worst: Escalation of cybercriminal activities; Most-Likely: Incremental law enforcement successes with ongoing cybercriminal adaptations.
6. Key Individuals and Entities
- James (alleged hacker and manifesto author)
- ShinyHunters (hacking group)
- GnosticPlayers (hacking group)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cybercrime, dark web, law enforcement, hacking groups, data breach, cyber investigations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us