Data Breach at Manage My Health Sparks Enhanced Security Measures Across Medical Platforms
Published on: 2026-01-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Manage My Health fallout Will other medical platforms boost security
1. BLUF (Bottom Line Up Front)
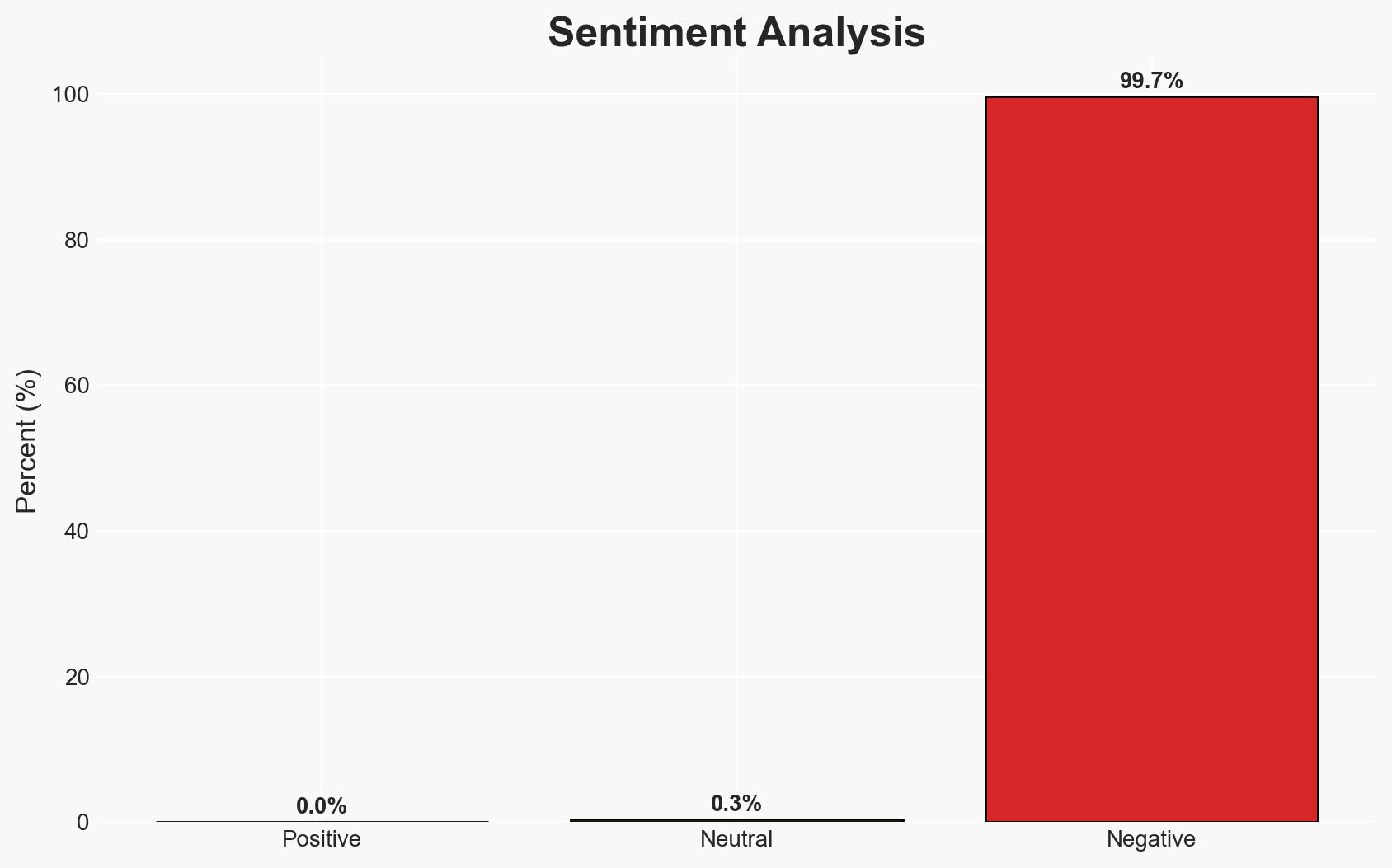
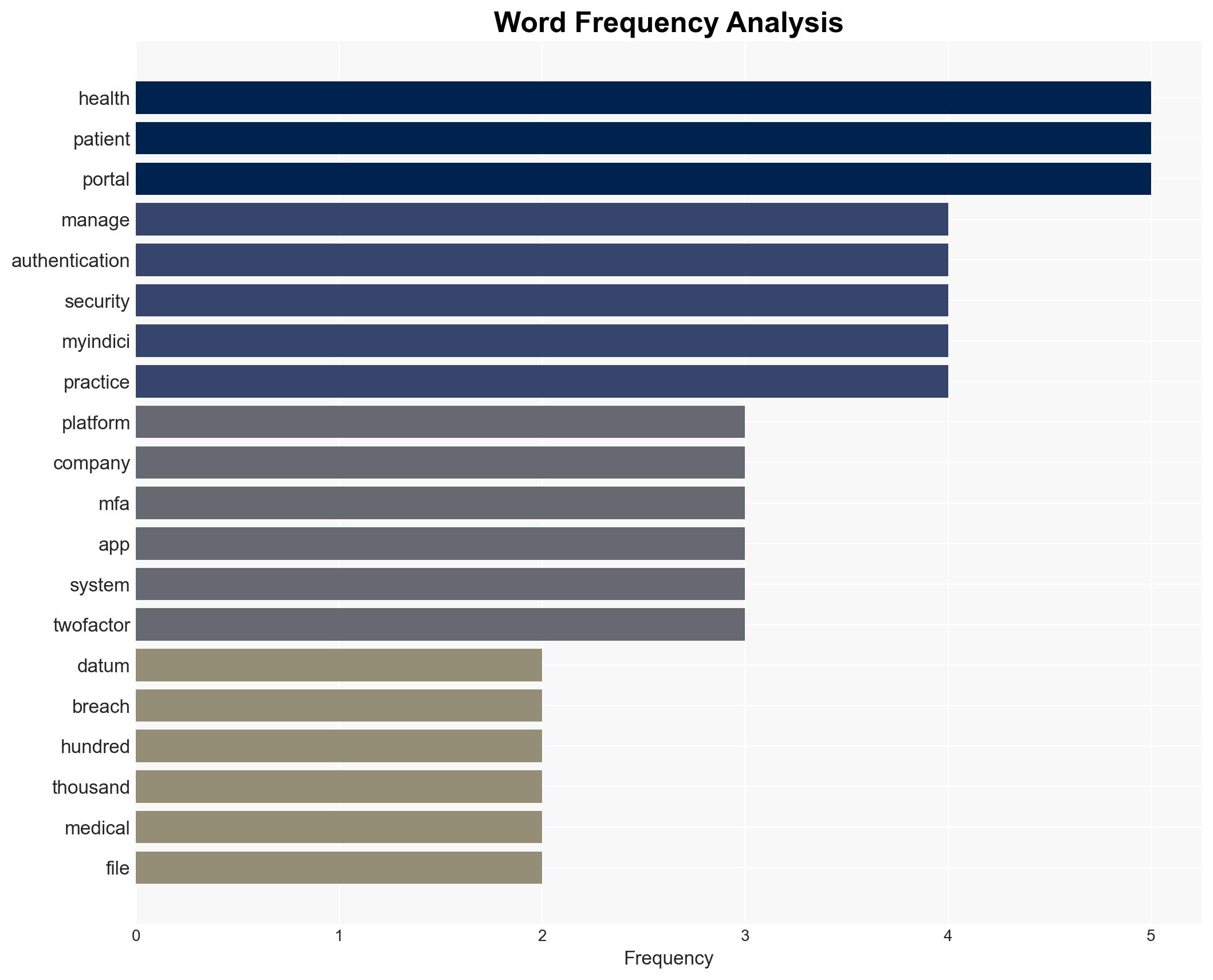
The recent data breach of Manage My Health, affecting 125,000 patients, underscores vulnerabilities in medical data platforms. Competing platforms are enhancing security through multi-factor authentication (MFA). Hypothesis A, that increased security measures will mitigate future breaches, is currently better supported. This affects healthcare providers and patients, with moderate confidence in this assessment.
2. Competing Hypotheses
- Hypothesis A: Enhanced security measures, such as MFA, will effectively mitigate future data breaches in medical platforms. Supporting evidence includes the adoption of MFA by platforms like MyIndici and The Doctors’ portal. Key uncertainty remains around the full implementation and user compliance with these measures.
- Hypothesis B: Despite enhanced security measures, medical platforms will continue to face significant cybersecurity threats due to evolving tactics by cybercriminals. Contradicting evidence includes the recent breach of Canopy Health, indicating persistent vulnerabilities.
- Assessment: Hypothesis A is currently better supported due to proactive security enhancements by multiple platforms. Indicators that could shift this judgment include new breaches despite MFA or evidence of sophisticated attacks bypassing current security measures.
3. Key Assumptions and Red Flags
- Assumptions: Medical platforms will continue to prioritize security; MFA adoption will be widespread and enforced; cyber threats will not outpace current security advancements.
- Information Gaps: Detailed security protocols of affected and unaffected platforms; user compliance rates with MFA; specifics of the Canopy Health breach.
- Bias & Deception Risks: Potential over-reliance on MFA as a panacea; source bias from platform spokespersons emphasizing security without independent verification.
4. Implications and Strategic Risks
The development of enhanced security measures in response to breaches could lead to a more secure healthcare information environment, but also highlights the ongoing cyber threat landscape.
- Political / Geopolitical: Increased scrutiny and potential regulation of healthcare data security practices.
- Security / Counter-Terrorism: Potential targeting of healthcare data by cybercriminals or state actors for espionage or disruption.
- Cyber / Information Space: Rising importance of cybersecurity in healthcare, with possible shifts towards more robust digital defenses.
- Economic / Social: Potential financial impacts on healthcare providers from breaches and subsequent security investments; erosion of patient trust in digital health solutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct comprehensive security audits of medical platforms; mandate MFA for all users; increase user education on cybersecurity practices.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for continuous monitoring; invest in advanced threat detection technologies; enhance regulatory frameworks for data protection.
- Scenario Outlook:
- Best: Full adoption of security measures leads to a significant reduction in breaches.
- Worst: New vulnerabilities are exploited, leading to major data breaches despite enhanced measures.
- Most-Likely: Incremental improvements in security reduce breach frequency but do not eliminate risk entirely.
6. Key Individuals and Entities
- Manage My Health
- Canopy Health
- MyIndici (Valentia Technologies)
- The Doctors (Webtools)
- Angus Chambers, General Practice Owners Association
- Callum McMenamin, web standards consultant
7. Thematic Tags
cybersecurity, healthcare data, multi-factor authentication, data breach, medical platforms, patient privacy, cyber threats
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us