Urgent Update Recommended for iPhone Users to Address Critical WebKit Vulnerabilities and Enhance Security
Published on: 2026-01-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Why iPhone users should update and restart their devices now
1. BLUF (Bottom Line Up Front)
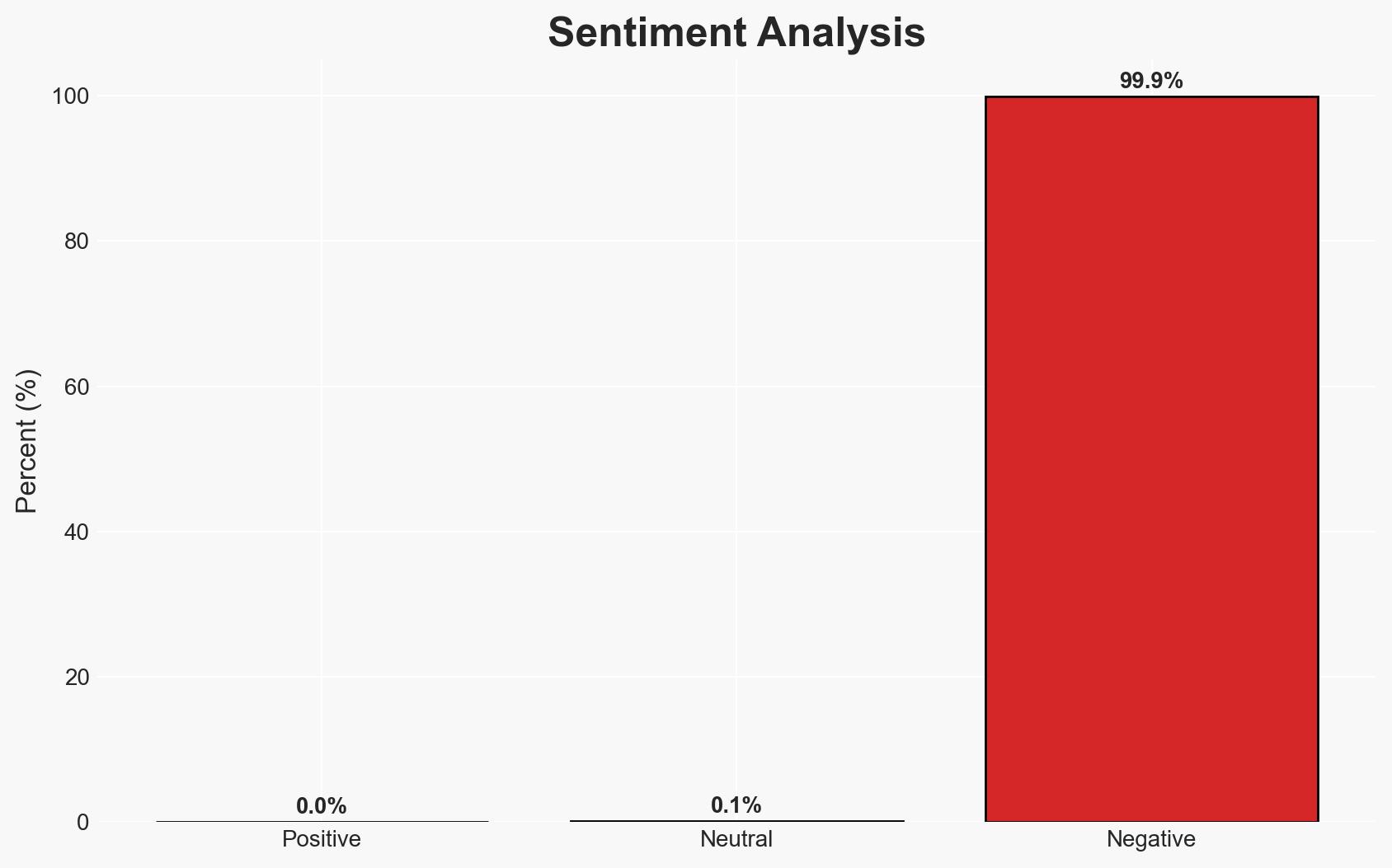
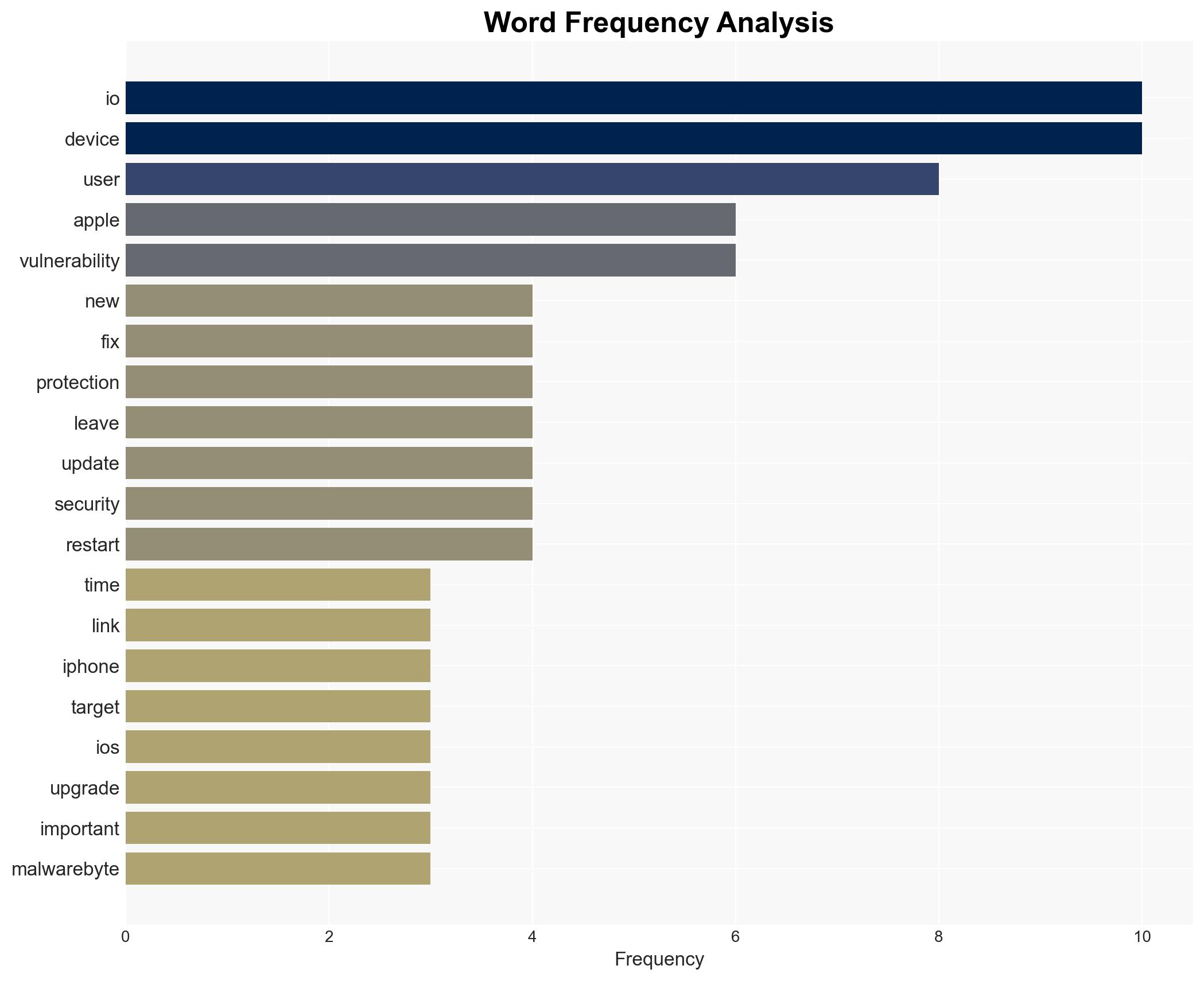
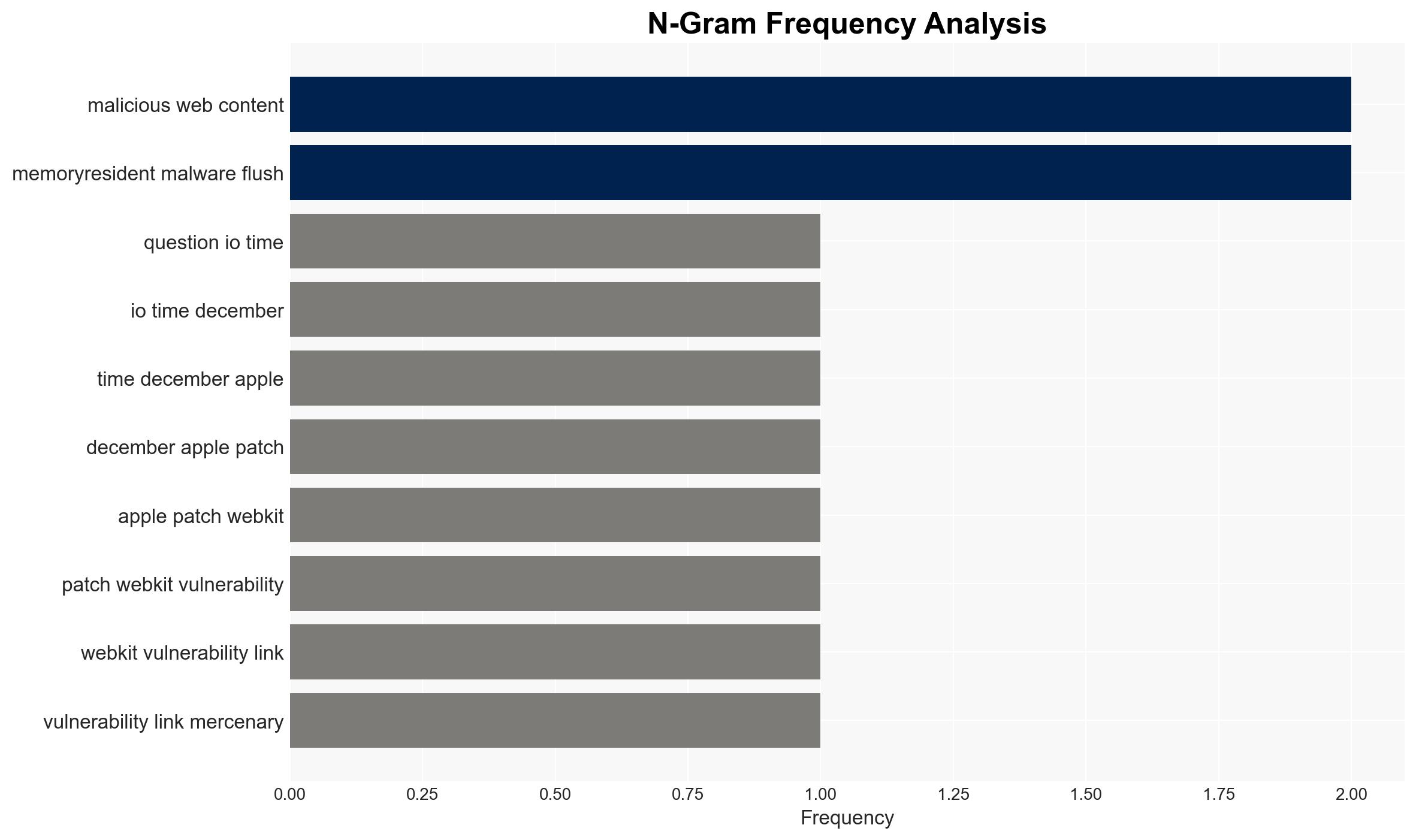
Apple has patched two critical WebKit zero-day vulnerabilities linked to mercenary spyware, urging users to upgrade to iOS 26+ for enhanced security. The vulnerabilities are actively exploited, posing a significant risk to users who delay updates. The situation affects all iPhone 11 and newer users, with moderate confidence in the assessment that failure to update increases exposure to cyber threats.
2. Competing Hypotheses
- Hypothesis A: The primary motivation for Apple’s push to iOS 26+ is to mitigate active exploitation of WebKit vulnerabilities. Supporting evidence includes the confirmed exploitation of these vulnerabilities and the introduction of new security features in iOS 26+. However, uncertainties remain regarding the potential for additional undisclosed vulnerabilities.
- Hypothesis B: Apple’s emphasis on upgrading to iOS 26+ is driven by a strategic business interest to increase adoption of new features, such as Liquid Glass, rather than solely security concerns. This is contradicted by the immediate security threat posed by the vulnerabilities, but supported by reports of slow adoption rates due to resistance to new features.
- Assessment: Hypothesis A is currently better supported due to the immediate and confirmed security threats posed by the vulnerabilities. Indicators such as increased reports of exploitation or new vulnerability disclosures could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Users will respond to security advisories by updating their devices; Apple will continue to release timely security patches; the vulnerabilities are limited to WebKit and not indicative of broader systemic issues.
- Information Gaps: Detailed technical analysis of the vulnerabilities and their exploitation methods; comprehensive data on the adoption rates of iOS 26+ post-advisory.
- Bias & Deception Risks: Potential bias in reporting adoption rates and user resistance; risk of underestimating the capabilities of adversaries exploiting the vulnerabilities.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities could lead to increased cyber espionage activities, affecting both individual and organizational security. The slow adoption of iOS 26+ may prolong exposure to these threats, impacting user trust and Apple’s reputation.
- Political / Geopolitical: Potential for increased tensions if state actors are implicated in exploiting these vulnerabilities.
- Security / Counter-Terrorism: Elevated risk of targeted attacks on high-profile individuals and organizations, potentially leading to data breaches.
- Cyber / Information Space: Expansion of attack vectors through repurposed exploits, increasing the overall threat landscape.
- Economic / Social: Potential economic impact on Apple due to decreased consumer confidence and increased support costs.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage rapid dissemination of update advisories; monitor for new exploit attempts; engage with Apple for detailed vulnerability assessments.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for enhanced threat intelligence; invest in user education programs to increase update compliance.
- Scenario Outlook:
- Best: Rapid adoption of iOS 26+ mitigates threats, with no significant breaches reported.
- Worst: Exploits lead to major data breaches, damaging trust in Apple’s security posture.
- Most-Likely: Gradual increase in iOS 26+ adoption reduces threat exposure, but sporadic exploitation continues.
6. Key Individuals and Entities
- Apple Inc.
- iPhone users (iPhone 11 and newer)
- Mercenary spyware developers
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, software updates, zero-day vulnerabilities, espionage, mobile security, Apple, spyware
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us