Data breach at Spanish energy giant Endesa exposes full customer information, including sensitive details.
Published on: 2026-01-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Threat actor claims the theft of full customer data from Spanish energy firm Endesa
1. BLUF (Bottom Line Up Front)
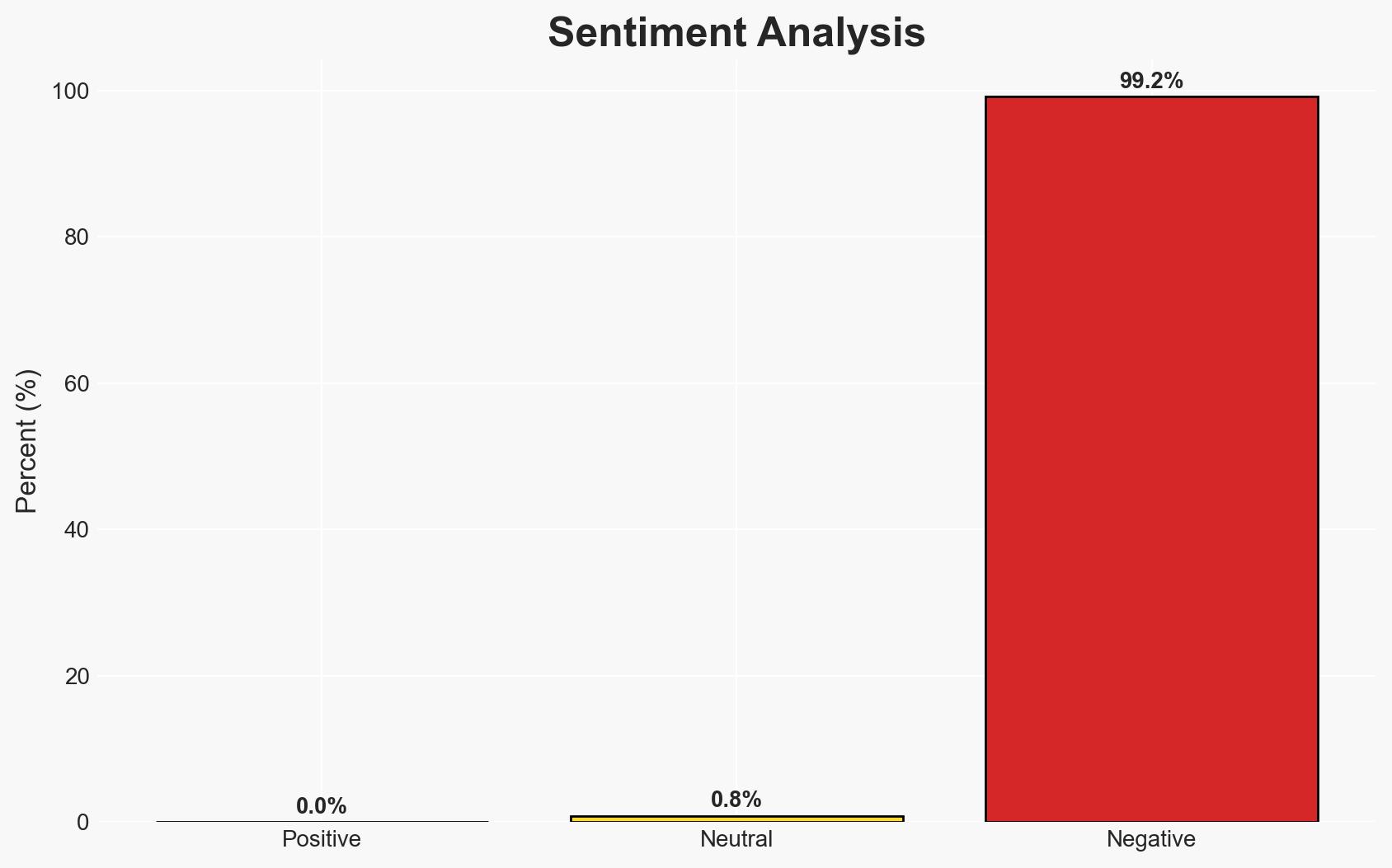
The data breach at Endesa, a major Spanish energy firm, has resulted in the unauthorized access and potential exfiltration of sensitive customer data. The most likely hypothesis is that the breach was conducted by a financially motivated cybercriminal group. The affected parties include Endesa’s customers and potentially the broader energy sector. Overall confidence in this assessment is moderate due to limited technical details about the breach.
2. Competing Hypotheses
- Hypothesis A: The breach was carried out by a financially motivated cybercriminal group aiming to sell the data on the black market. This is supported by the nature of the data accessed, which is valuable for identity theft and fraud. However, there is no direct evidence of data misuse yet.
- Hypothesis B: The breach was conducted by a state-sponsored actor aiming to gather intelligence on Spain’s energy sector. This is less supported due to the lack of evidence indicating a strategic motive beyond financial gain.
- Assessment: Hypothesis A is currently better supported given the type of data targeted and typical cybercriminal behavior. Indicators such as the appearance of data on dark web forums could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The breach was not an insider threat; Endesa’s security measures were standard for the industry; the attackers are external entities.
- Information Gaps: Specific technical details of how the breach occurred; identity and motives of the threat actors; any evidence of data misuse.
- Bias & Deception Risks: Potential bias in Endesa’s public statements aimed at minimizing perceived impact; lack of independent verification of breach details.
4. Implications and Strategic Risks
This data breach could have significant implications for Endesa and the broader energy sector, potentially affecting customer trust and regulatory scrutiny.
- Political / Geopolitical: Increased regulatory pressure on energy firms in Spain and the EU to enhance cybersecurity measures.
- Security / Counter-Terrorism: Potential for increased cyber threat activity targeting critical infrastructure in Spain.
- Cyber / Information Space: Heightened risk of phishing and identity theft targeting Endesa’s customers.
- Economic / Social: Possible financial losses for Endesa due to regulatory fines and loss of customer trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of dark web for signs of data sale; increase customer awareness and support for potential identity theft issues.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity infrastructure; engage in public-private partnerships to share threat intelligence.
- Scenario Outlook:
- Best: No misuse of data occurs, and Endesa strengthens its cybersecurity posture.
- Worst: Data is sold and used for widespread fraud, leading to significant financial and reputational damage.
- Most-Likely: Some data misuse occurs, prompting regulatory action and increased cybersecurity measures.
6. Key Individuals and Entities
- Endesa
- Enel
- Spanish Data Protection Agency
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, energy sector, identity theft, regulatory compliance, cybercrime, critical infrastructure
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us