Microsoft January 2026 Patch Tuesday Addresses 113 Vulnerabilities, Including Active Exploit for Zero-Day Flaw
Published on: 2026-01-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Patch Tuesday January 2026 Edition
1. BLUF (Bottom Line Up Front)
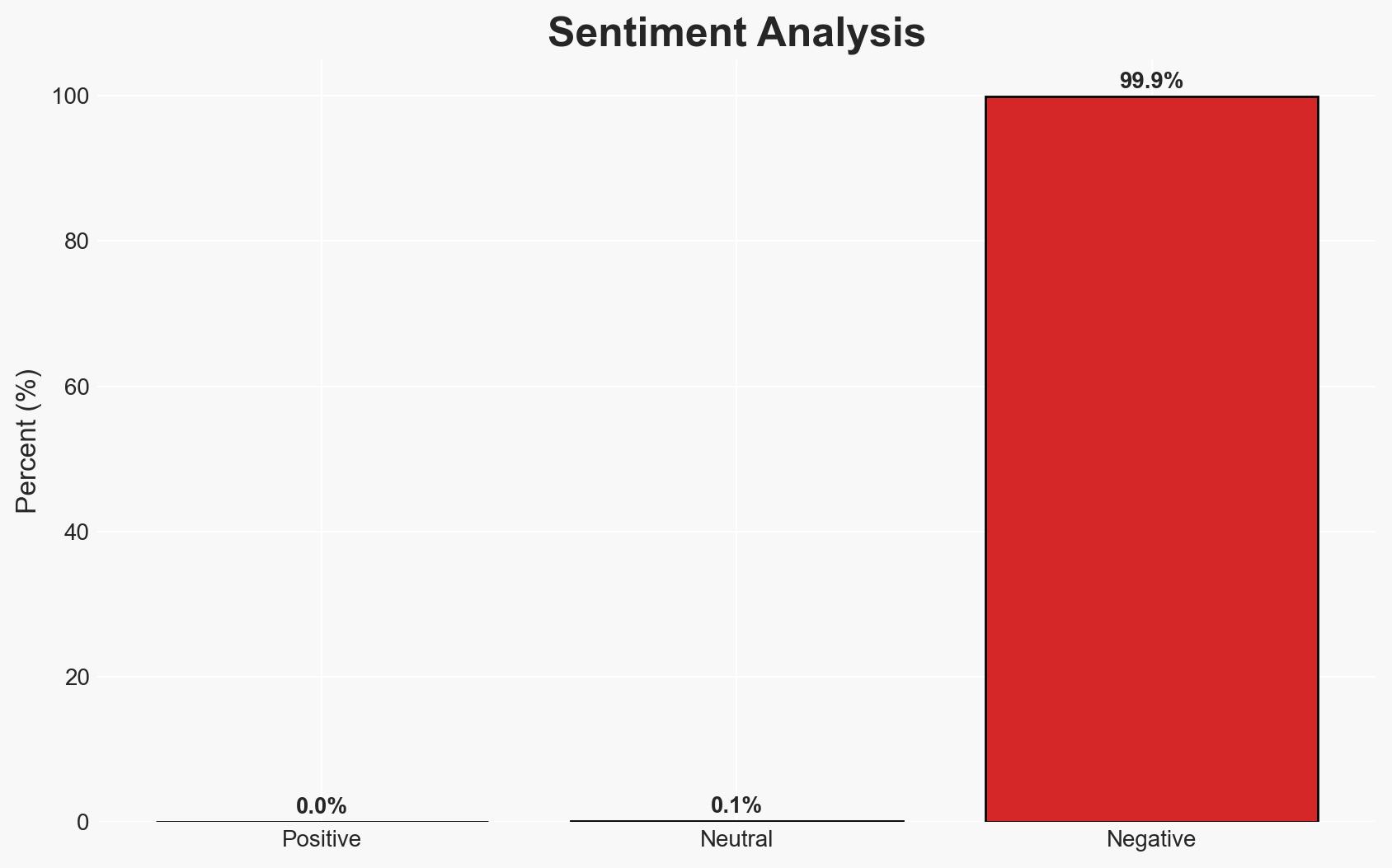
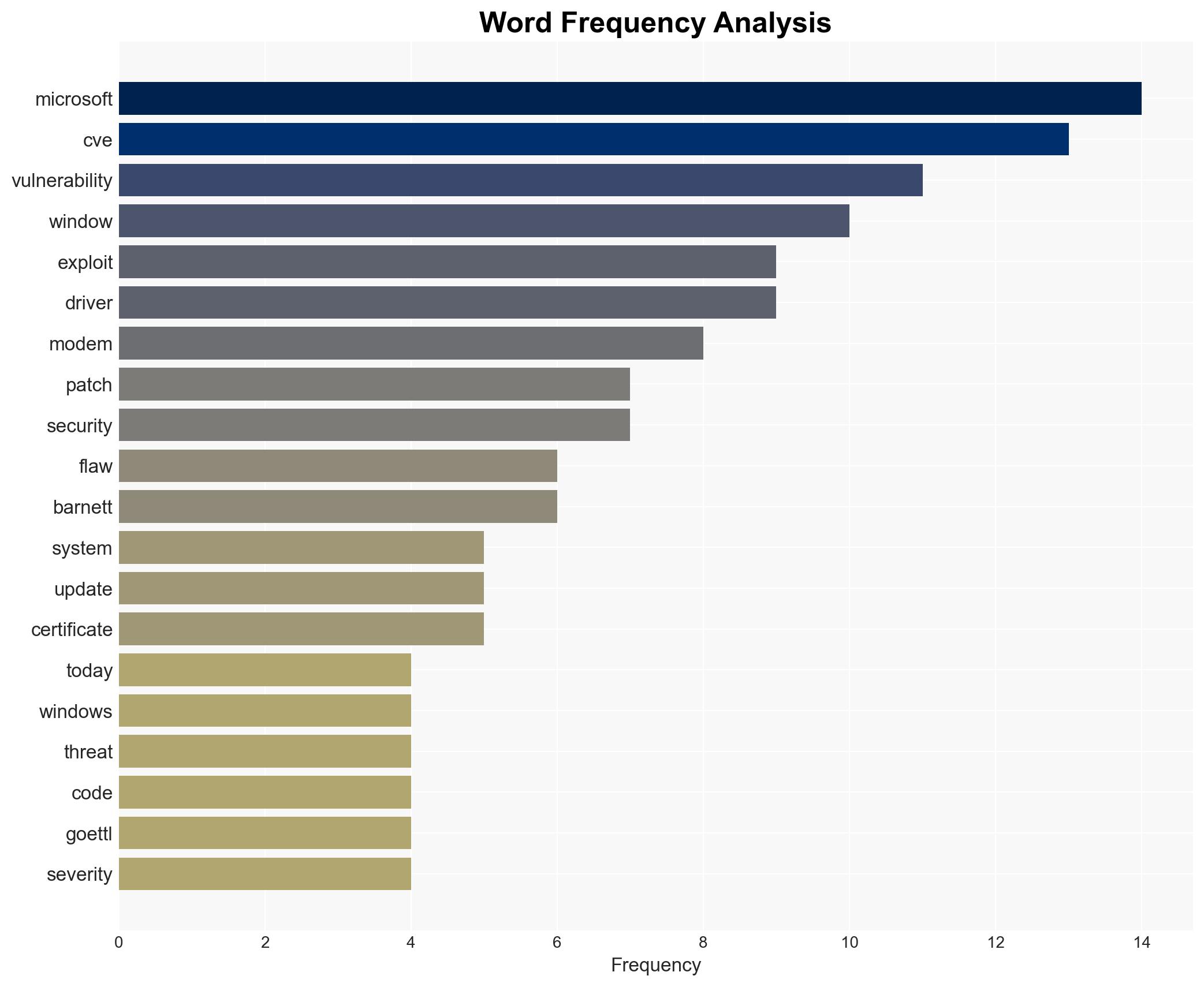
Microsoft’s January 2026 Patch Tuesday addresses significant vulnerabilities, including a zero-day flaw actively exploited in the wild. The critical nature of these vulnerabilities, particularly CVE-2026-20805, necessitates immediate attention from organizations using Windows OS. The overall confidence in this assessment is moderate, given the active exploitation and the potential for further exploitation chains.
2. Competing Hypotheses
- Hypothesis A: The active exploitation of CVE-2026-20805 and other vulnerabilities will lead to widespread attacks on organizations using Windows OS. This is supported by the confirmed active exploitation and the potential for chaining with other vulnerabilities. Uncertainties include the extent of exploitation and the specific threat actors involved.
- Hypothesis B: The vulnerabilities will be contained through rapid patching and mitigation efforts, limiting the impact. This is supported by the availability of patches and the emphasis on rapid patching as an effective mitigation strategy. However, the lack of detailed information on potential exploit chains could undermine this containment.
- Assessment: Hypothesis A is currently better supported due to the confirmed active exploitation and the potential for exploitation chains. Indicators that could shift this judgment include evidence of successful widespread patching or new information on exploit chains.
3. Key Assumptions and Red Flags
- Assumptions: Organizations will prioritize patching these vulnerabilities; threat actors will continue to exploit known vulnerabilities; Microsoft will provide timely updates and guidance.
- Information Gaps: Specific details on additional components involved in exploit chains; identification of threat actors exploiting these vulnerabilities.
- Bias & Deception Risks: Potential bias in vendor ratings and CVSS scores; risk of underestimating the severity due to lack of detailed exploit chain information.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities could lead to significant operational disruptions and data breaches, impacting organizational security and trust in Microsoft products. Over time, this could affect Microsoft’s market position and customer confidence.
- Political / Geopolitical: Potential for state-sponsored actors to exploit these vulnerabilities for espionage or sabotage.
- Security / Counter-Terrorism: Increased risk of cyber-attacks targeting critical infrastructure and sensitive data.
- Cyber / Information Space: Heightened threat landscape with potential for increased cyber-espionage and data theft.
- Economic / Social: Potential economic impact on affected organizations due to data breaches and operational disruptions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Prioritize patching of all affected systems, particularly addressing CVE-2026-20805; enhance monitoring for signs of exploitation.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular vulnerability assessments and incident response planning; strengthen partnerships with cybersecurity vendors.
- Scenario Outlook:
- Best: Rapid patching limits impact, and no further exploitation occurs.
- Worst: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Some exploitation occurs, but effective patching and mitigation limit the overall impact.
6. Key Individuals and Entities
- Microsoft
- Kev Breen, Senior Director of Cyber Threat Research at Immersive
- Chris Goettl, Vice President of Product Management at Ivanti
- Adam Barnett, Rapid7
7. Thematic Tags
cybersecurity, vulnerability management, zero-day exploit, Microsoft, patch management, cyber threat, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us